Method, device and electronic equipment for structuring data fingerprint
A data fingerprint and electronic device technology, applied in the information field, can solve problems such as complexity and heavy system workload, and achieve the effect of small amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
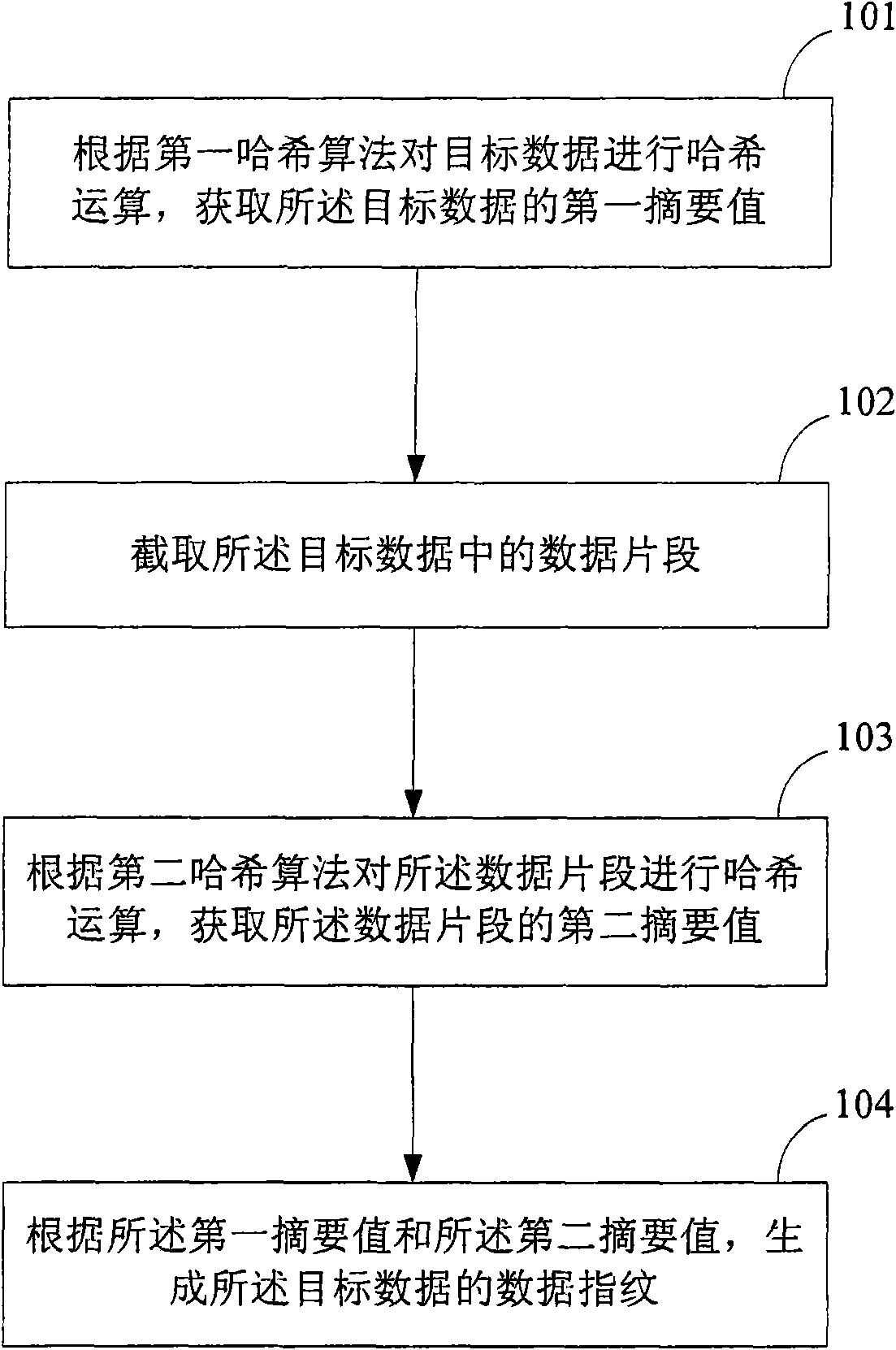
[0029] like figure 1 as shown, figure 1 It is a schematic flowchart of a method for constructing a data fingerprint of target data in this embodiment, and the process includes the following steps:
[0030] 101. Perform a hash operation on the target data according to a first hash algorithm to obtain a first digest value of the target data;
[0031] 102. Intercepting a data segment in the target data;
[0032] 103. Perform a hash operation on the data segment according to a second hash algorithm to obtain a second digest value of the data segment;
[0033] 104. Generate a data fingerprint of the target data according to the first digest value and the second digest value.
[0034] The first hash algorithm and the second hash algorithm in the embodiment of the present invention may be the same hash algorithm, or may be different hash algorithms. However, whether the same hash algorithm or different hash algorithms are used, the obtained first digest value and the second diges...
Embodiment 2
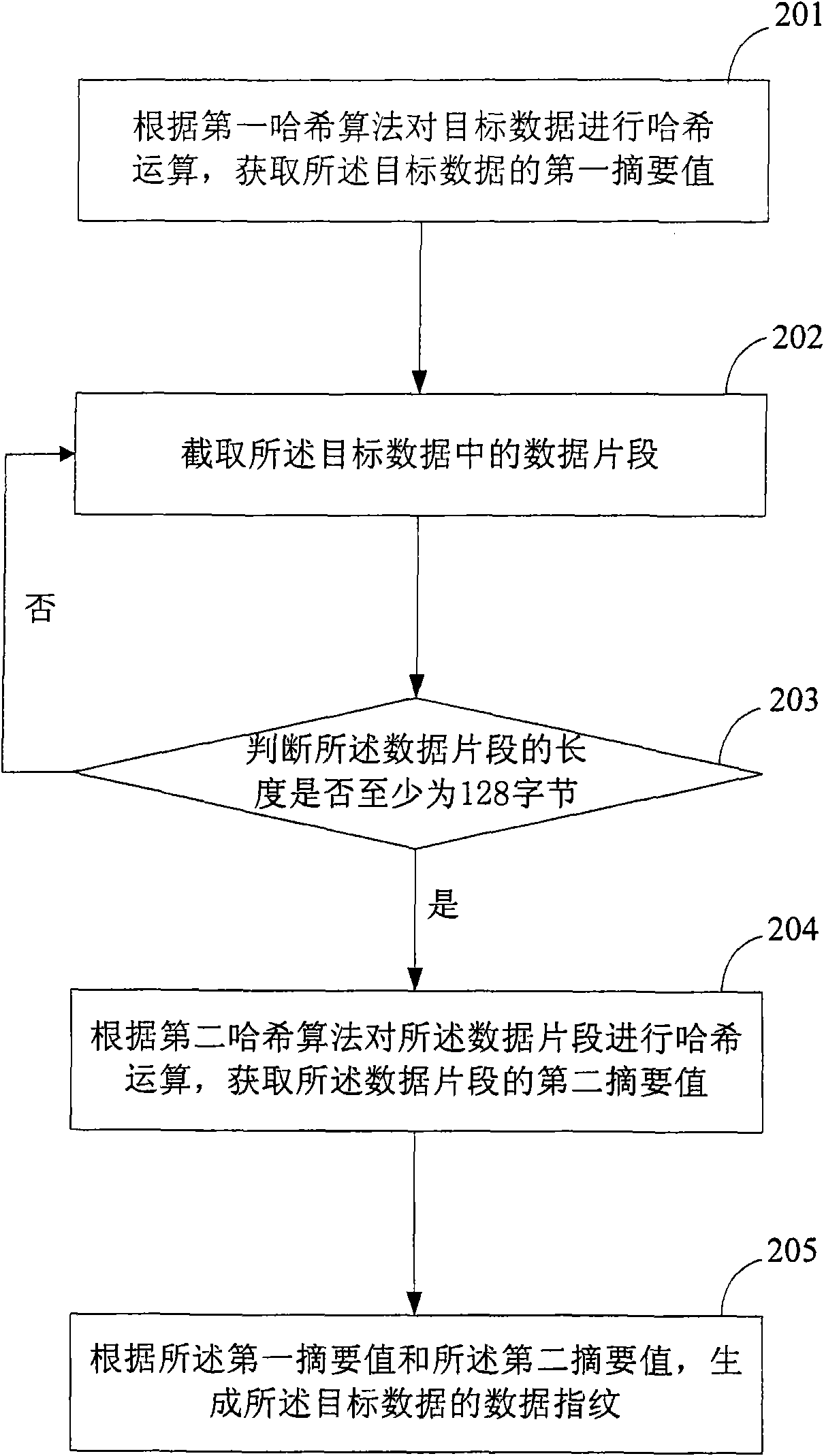
[0038] like figure 2 as shown, figure 2 It is a schematic flowchart of a method for constructing a data fingerprint of target data in this embodiment, and the process includes the following steps:
[0039] 201. Perform a hash operation on the target data according to a first hash algorithm to obtain a first digest value of the target data;
[0040] 202. Intercepting a data segment in the target data;
[0041] 203. Determine whether the length of the data segment is at least 128 bytes; if the length of the data segment is at least 128 bytes, then perform step 204; if the length of the data segment is less than 128 bytes, then perform step 202 .
[0042] 204. Perform a hash operation on the data segment according to a second hash algorithm to obtain a second digest value of the data segment;
[0043] 205. Generate a data fingerprint of the target data according to the first digest value and the second digest value.
[0044] In the embodiment of the present invention, afte...
Embodiment 3
[0050] According to the method described in Embodiment 1 or Embodiment 2, here, three independent embodiments are respectively used to illustrate the technical solutions of the embodiments of the present invention.
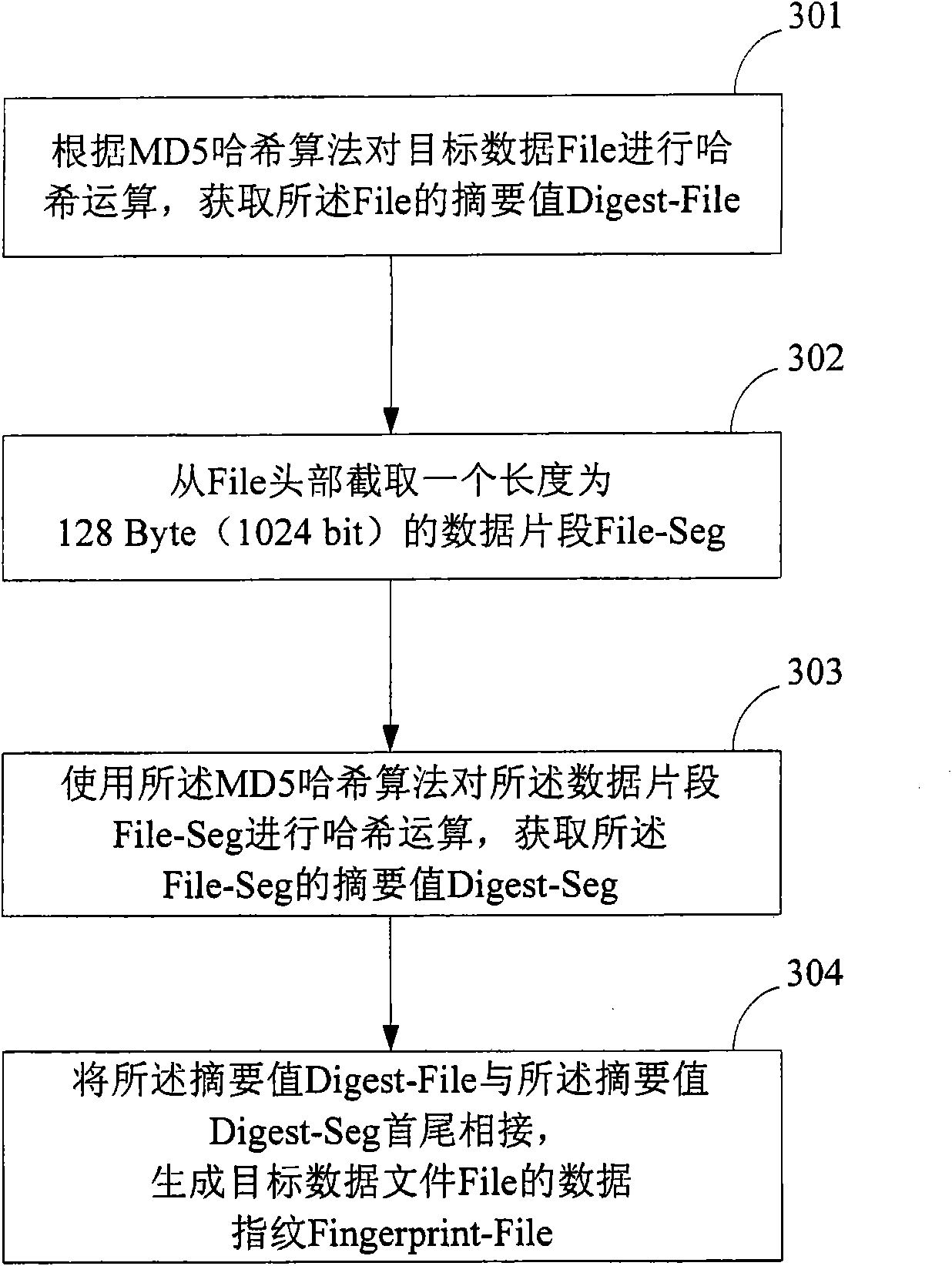
[0051] like image 3 as shown, image 3 It is a schematic flowchart of the first method for constructing data fingerprints of target data in an embodiment of the present invention, and the process includes the following steps:
[0052] 301. Perform a hash operation on the target data File according to the MD5 (Message-Digest Algorithm 5, data digest algorithm 5) hash algorithm, and obtain the digest value Digest-File of the File;
[0053] 302. Intercepting a data segment File-Seg with a length of 128Byte (1024bit) from the File header;
[0054] 303. Use the MD5 hash algorithm to perform a hash operation on the data segment File-Seg to obtain a digest value Digest-Seg of the File-Seg;
[0055] 304. Concatenate the digest value Digest-File and the digest value Di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com