Method, device and system for defending malicious program for terminal
A malicious program and malicious technology are applied in the field of a method, device and system for terminal defense against malicious programs, which can solve the problems of poor security of anti-virus solutions and inability to timely prevent the harm of malicious programs, so as to improve the ability to defend against malicious programs, The effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
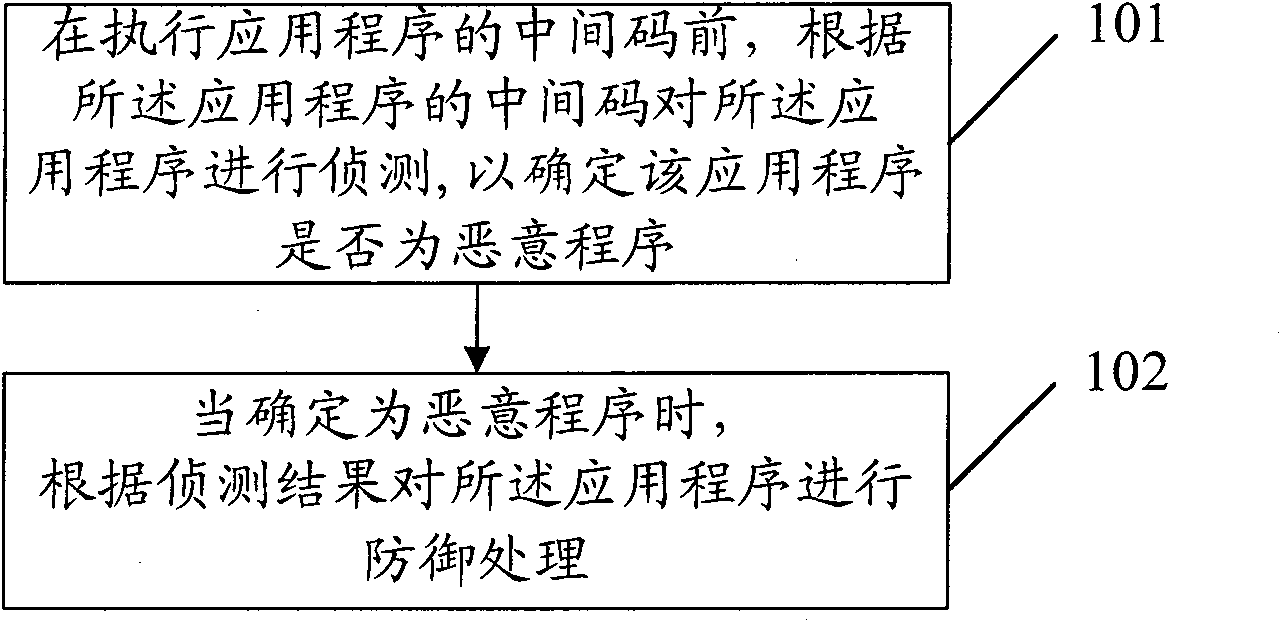
[0030] This embodiment provides a method for defending against malicious programs, such as figure 2 As shown, the method includes:
[0031] Step 101, before executing the intermediate code of the application, detect the application according to the intermediate code of the application to determine whether the application is a malicious program;
[0032] The intermediate code here refers to the intermediate code that the program generates during the compilation process and is not the binary code that can finally be executed by the machine. It is usually some middleware such as virtual machine instructions, such as Java bytecode, Microsoft .NET, etc. The common intermediate language (Common Intermediate Language, CIL) of the framework, etc. The malicious programs mentioned here refer to programs that damage the system, such as viruses and Trojan horses.
[0033] Step 102, when it is determined that the application program is a malicious program, perform defense processing on ...
Embodiment 2
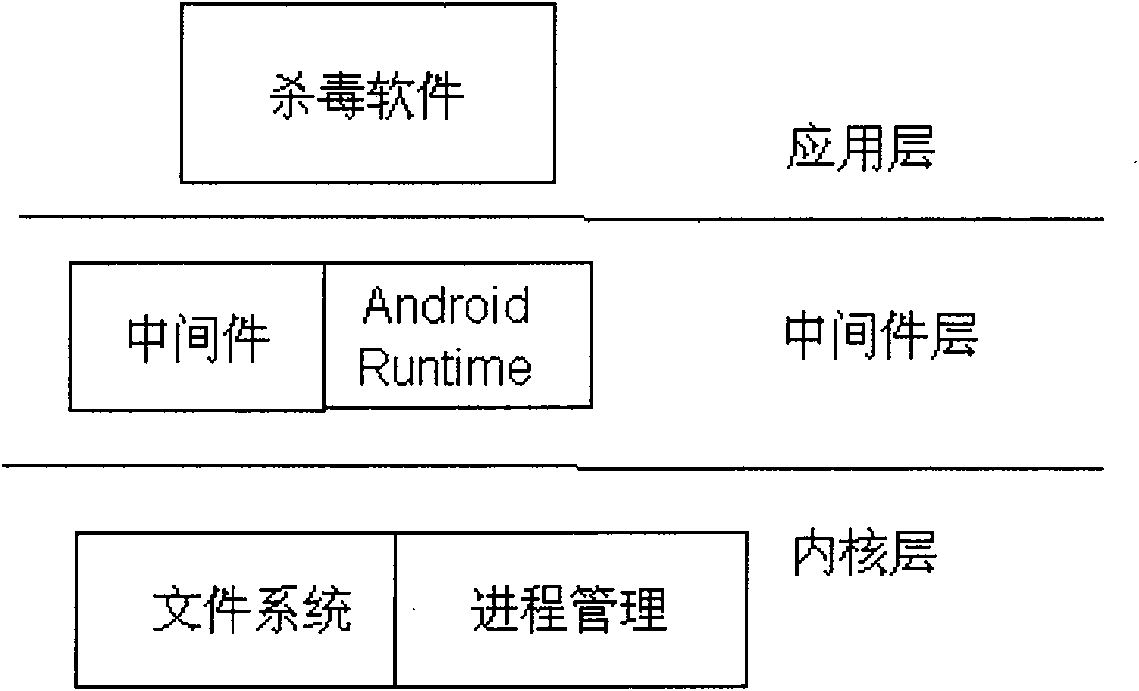
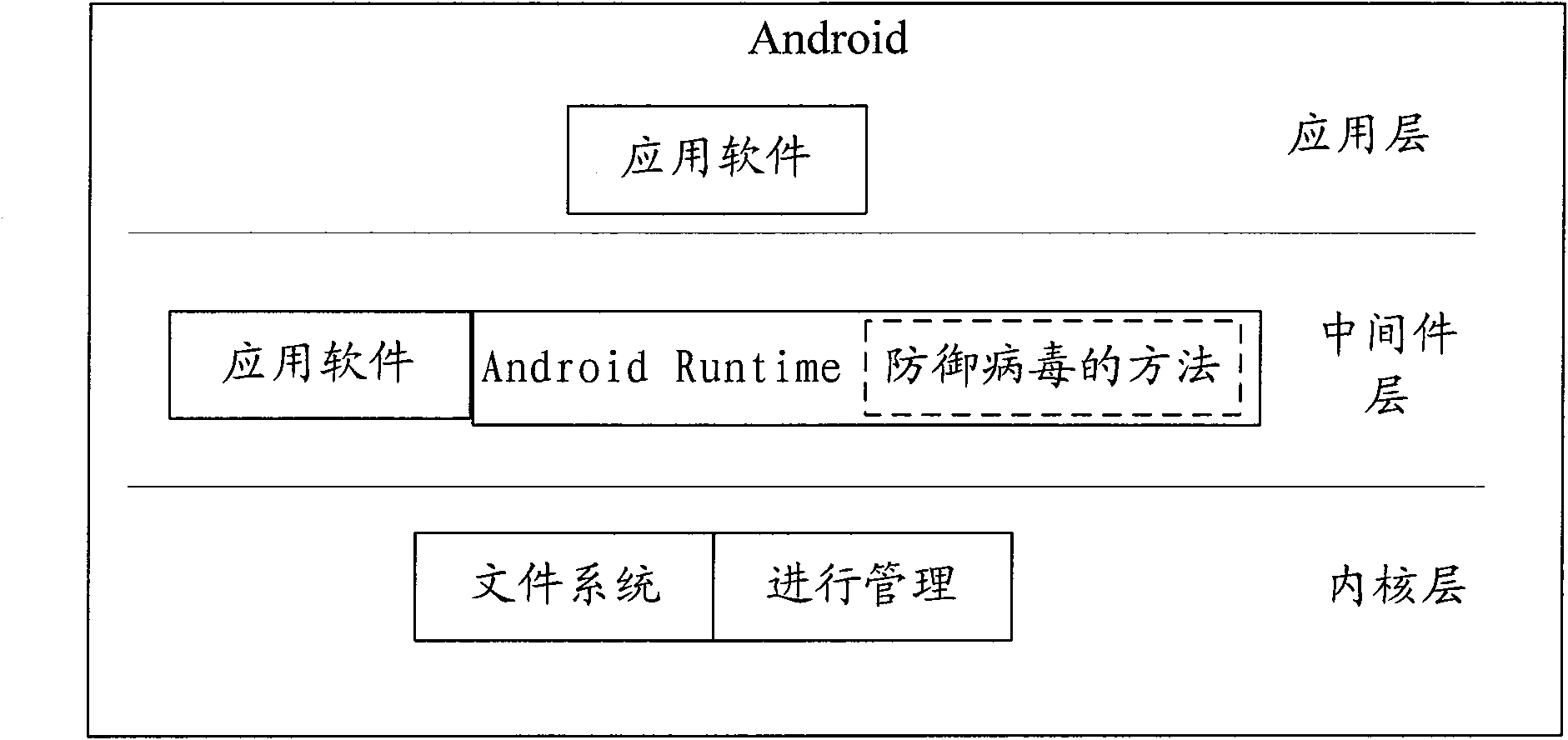
[0038] This embodiment specifically provides a method for defending against malicious programs. In a specific embodiment, the application program described in Embodiment 1 is a program written in JAVA language, and the method runs on a mobile terminal loaded with an Android operating system, and the method is applied to image 3 As shown in the Android middleware layer, the runtime software is Android Runtime. Of course, those skilled in the art can understand that the JAVA language and the Android operating system are only specific examples, which does not mean that this embodiment is only applicable to the JAVA language and the Android operating system. Such as Figure 4 As shown, the method includes:
[0039] Step 201, before executing the intermediate code of the application, detect the application according to the intermediate code of the application to determine whether the application is a malicious program;
[0040] Specifically, step 201 can be implemented in the f...
Embodiment 3
[0053] This embodiment provides an apparatus 300 for defending against malicious programs. The apparatus can be installed in a mobile terminal such as a mobile phone, and specifically can be located in a middleware layer of an operating system. Such as Figure 5 As shown, it includes: a detection module 31 and a processing module 32 .
[0054] The detection module 31 is used to detect the application program according to the intermediate code of the application program before executing the intermediate code of the application program, and determine whether the application program is a malicious program; the processing module 32 is used to When the detection module 31 determines that the application program is a malicious program, defense processing is performed on the application program.
[0055] Wherein, the detection module 31 includes: a detection manager 311 and at least one detection unit 312 .
[0056] The detection manager 311 is configured to manage the detection un...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com