Digital content protecting system
A technology for protecting systems and digital content, applied in the field of information technology, can solve the problems of not considering the security of the equipment itself, and achieve the effect of strengthening protection and facilitating users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
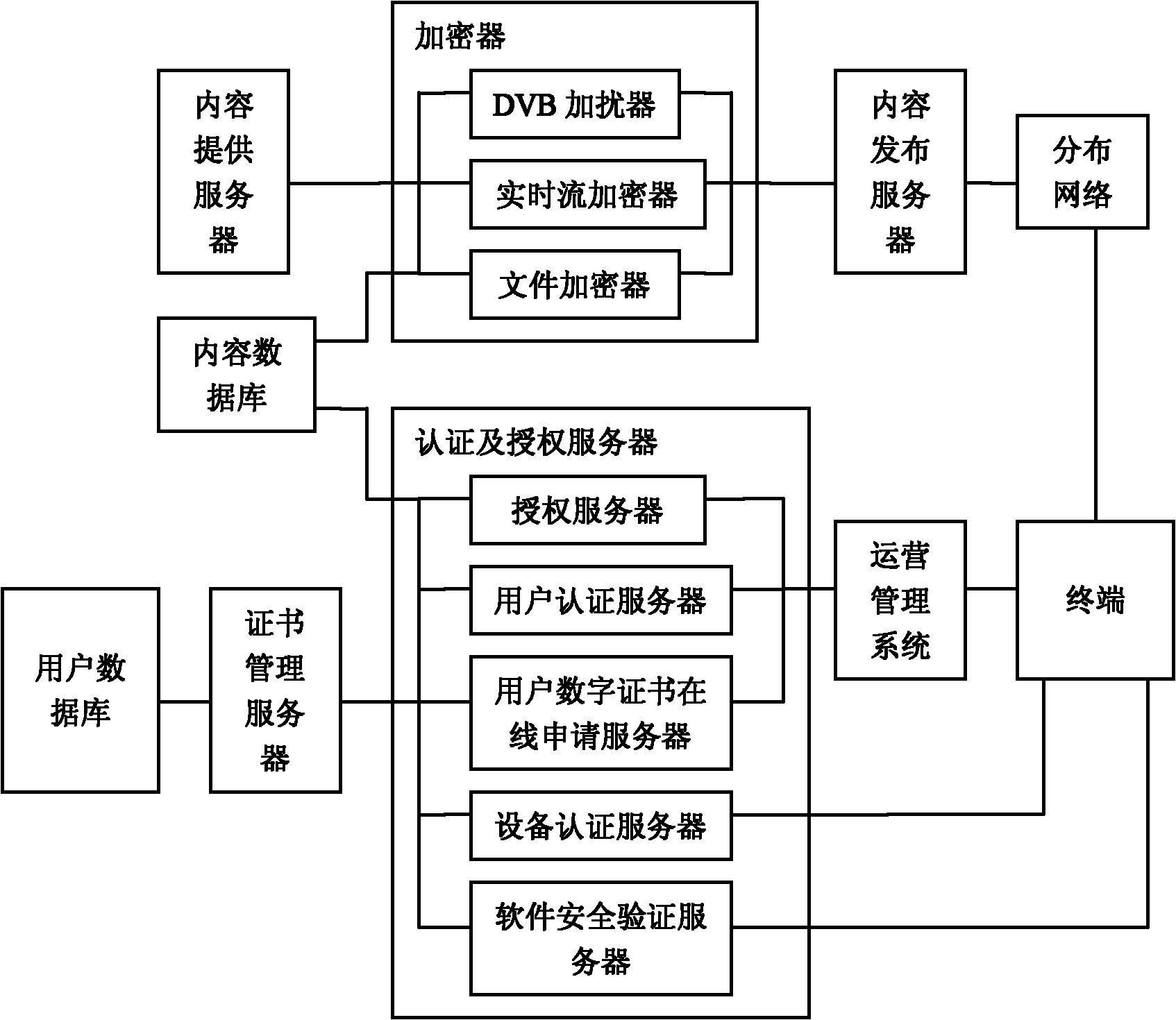
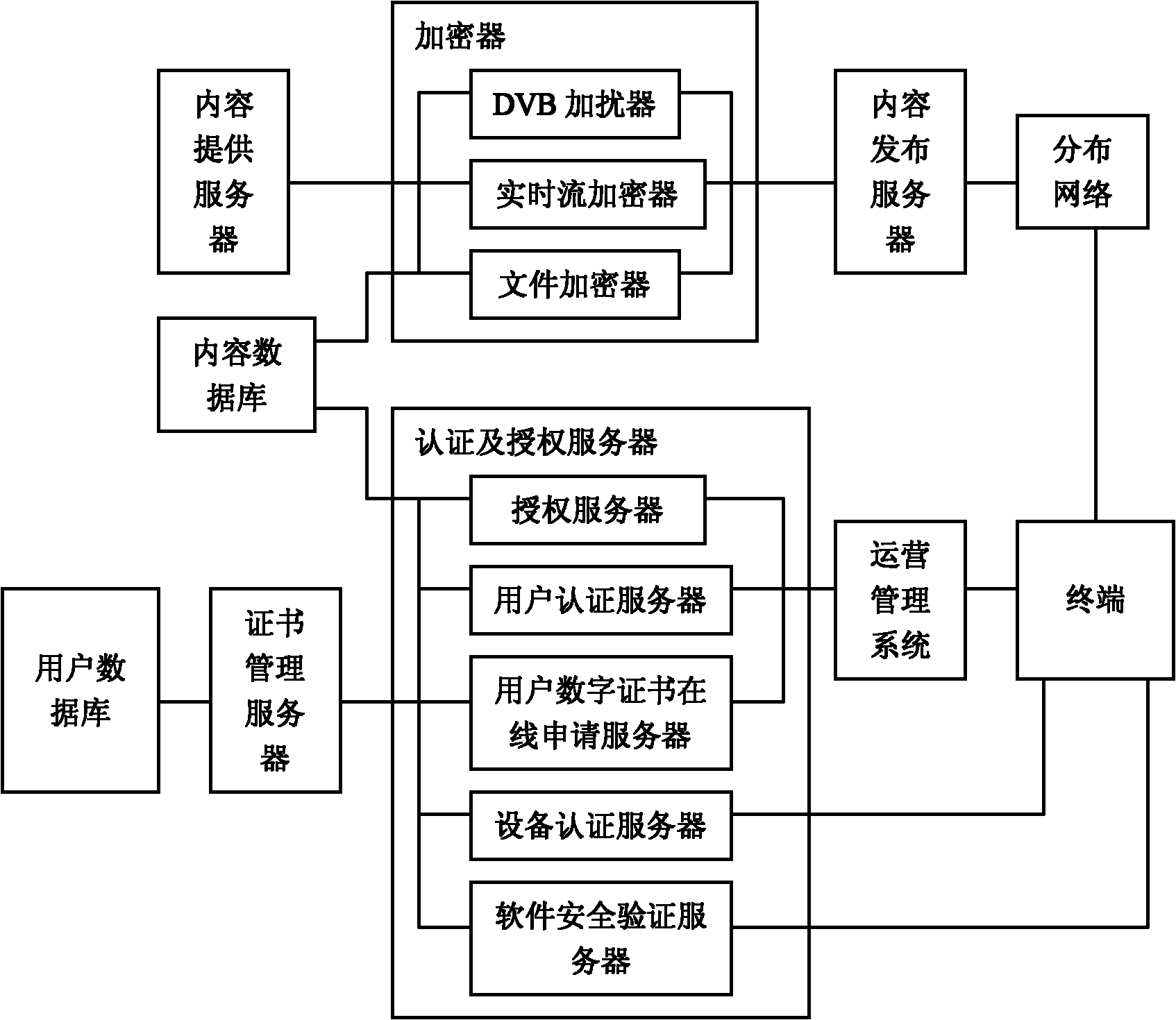
[0030] The authentication and authorization server in this example consists of an authorization server, a user authentication server, a user digital certificate online application server, a device authentication server, and a software security verification server. The encryptor is composed of a DVB scrambler, a real-time stream encryptor, and a file encryptor. The system block diagram is as figure 1 .
[0031] First, the DVB scrambler is connected to the content providing server, and connected to the content database, and connected to the content publishing server, and the real-time streaming encryptor is connected to the content providing server, and connected to the content database, and connected to the content publishing server, file encryptor Connect with the content providing server, and with the content database, and with the content publishing server, the content publishing server with the distribution network, the authorization server with the content database, the autho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com