Node trust management system in wireless sensor network
A wireless sensor and trust management technology, applied in wireless communication, network topology, electrical components, etc., can solve problems such as network paralysis, low trust value, and packet forwarding failure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
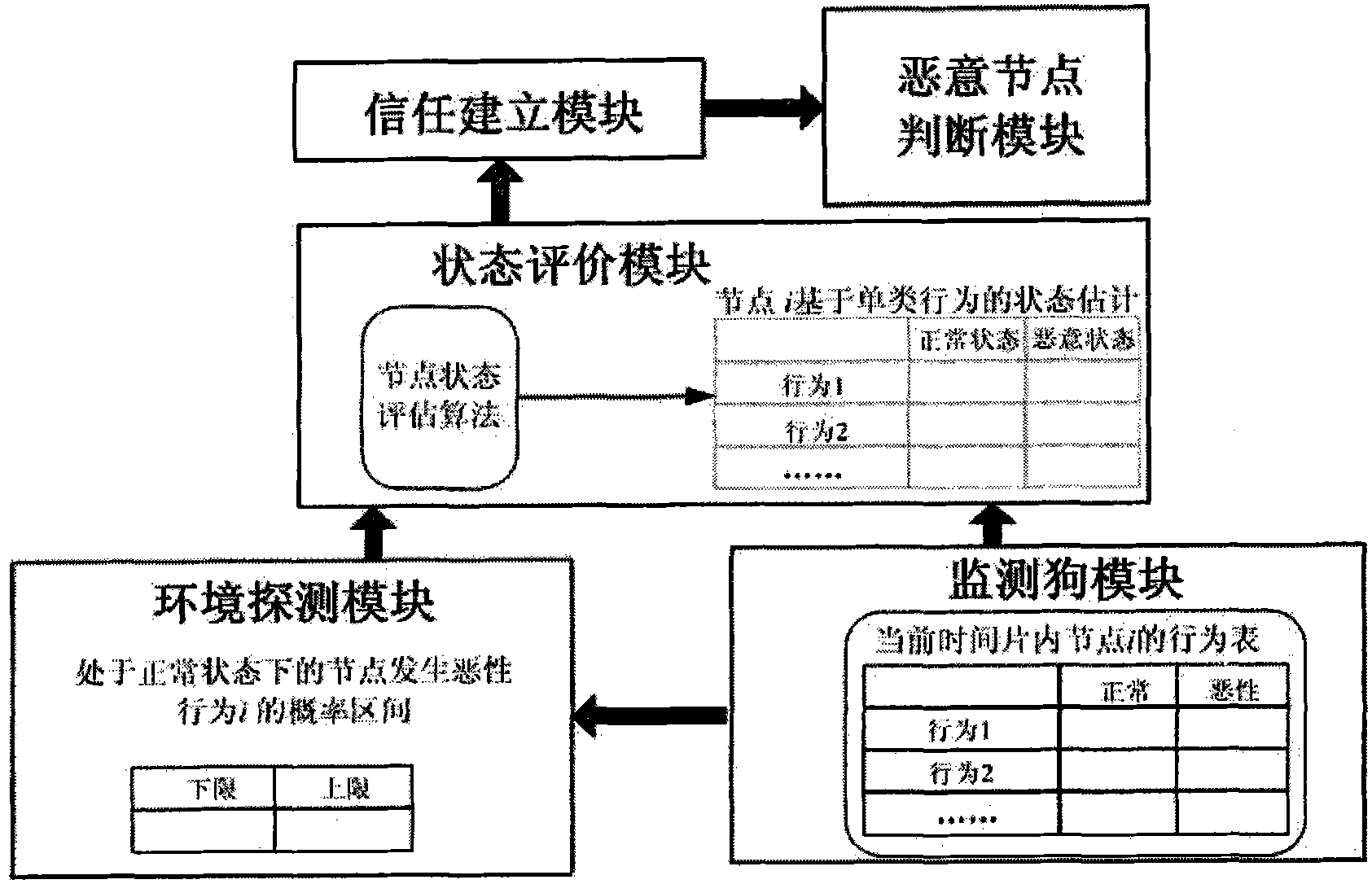
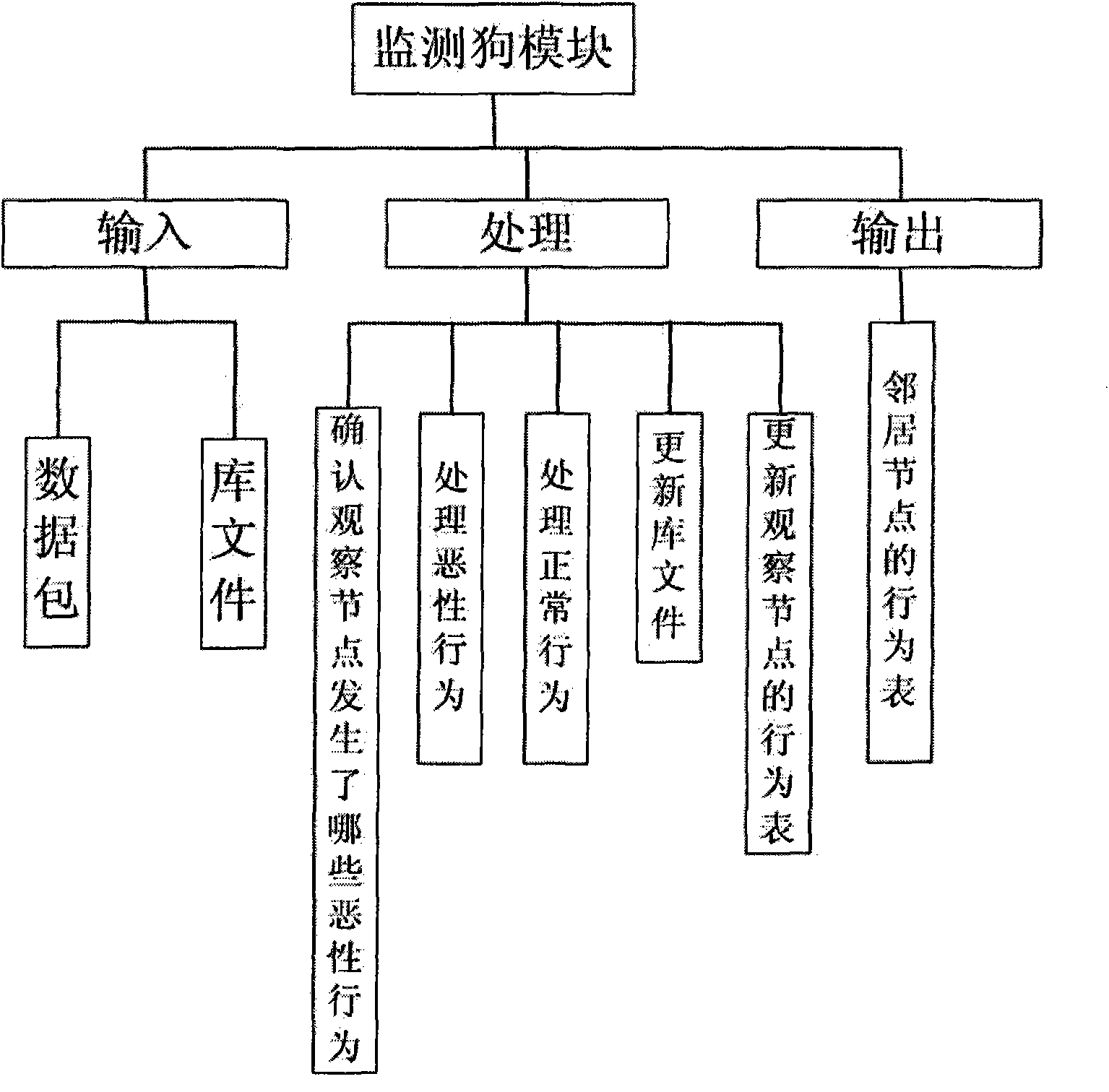
[0099] The technical solution adopted by the present invention is that in the system, the monitoring dog module is connected with the environment detection module and the state evaluation module, and the environment detection module is connected with the state evaluation module, the trust establishment module and the malicious node judgment module in sequence, such as figure 1 .
[0100] The specific steps of the system work are as follows:
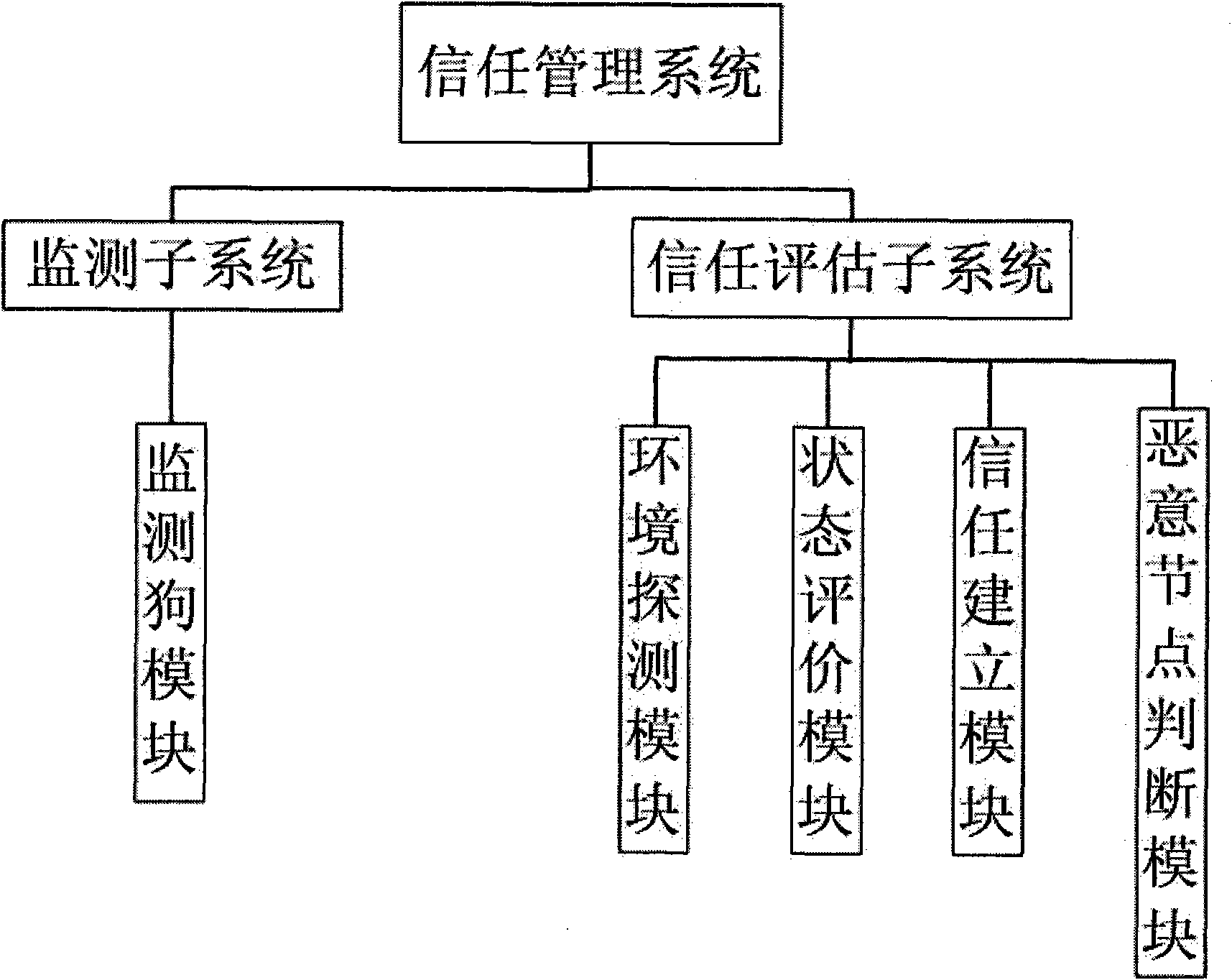
[0101] The first step is initialization. First preset system parameters ξ 0 , R 0 , R 1 , β 1,1-J , β 2,1-J , β 3,1-J , β 4,1-J ,P thr 、C thr 、r 0 . Divide each time slice cycle into a supervision phase and a trust evaluation phase. Such as figure 2As shown, in the monitoring phase, the monitoring subsystem is run, that is, its component module—the monitoring dog module is run. In the stage of trust evaluation, run the trust evaluation subsystem, that is, run its component modules—environment detection module, state eval...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com