Biometric security device
A security device and biometric data technology, applied in the field of security devices, can solve the problems of being unsuitable or only conditionally suitable for mobile use, high cost, and damage to biometric sensors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
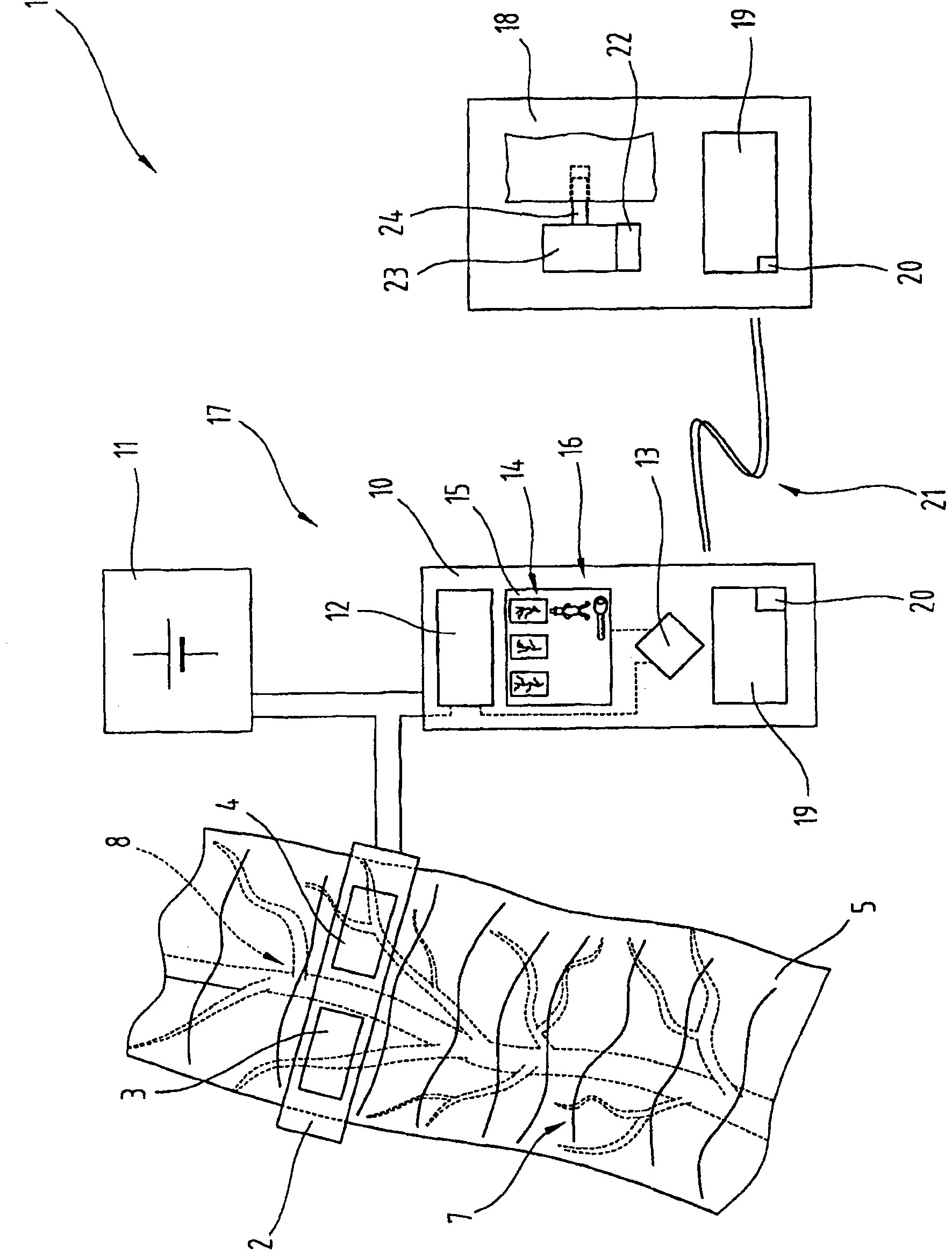
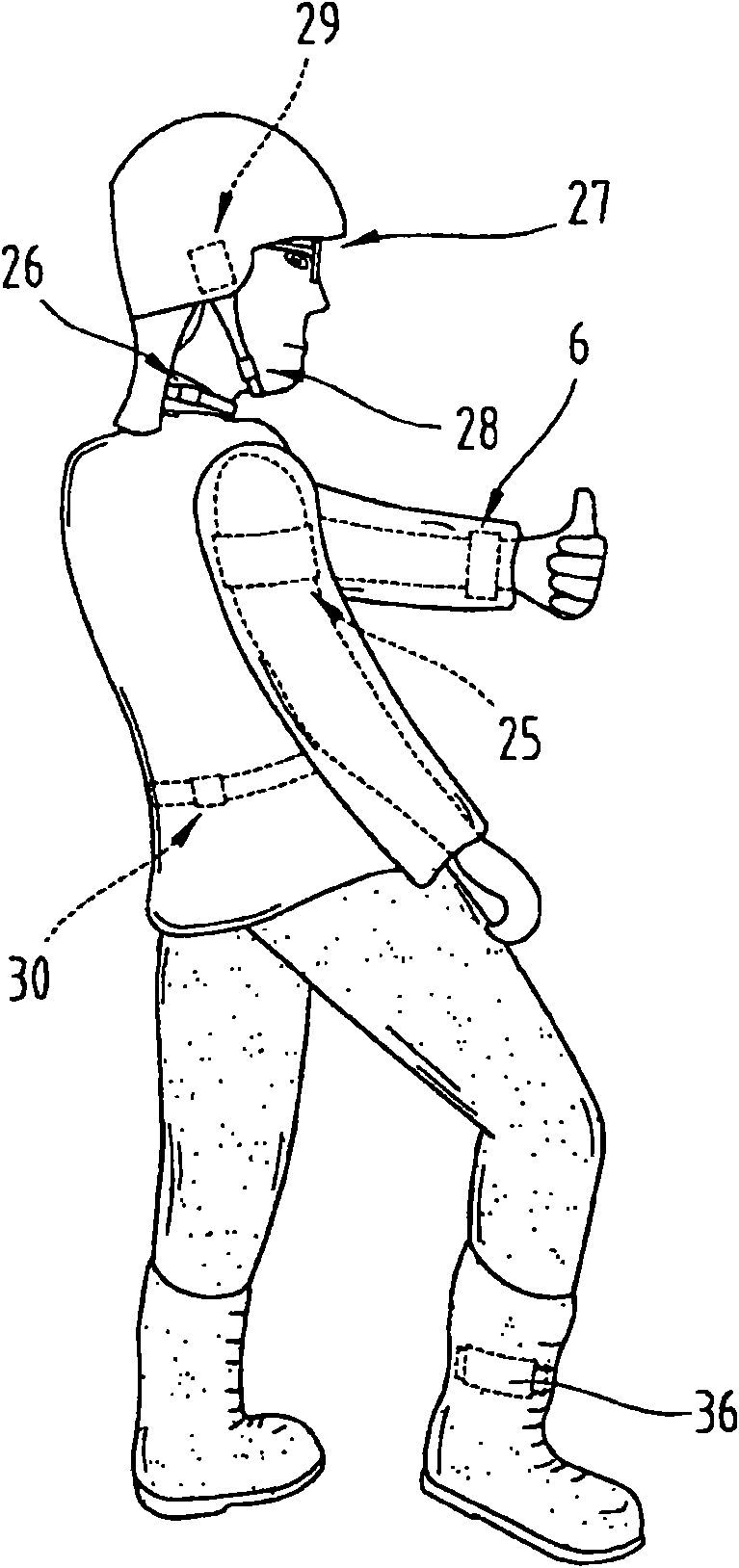
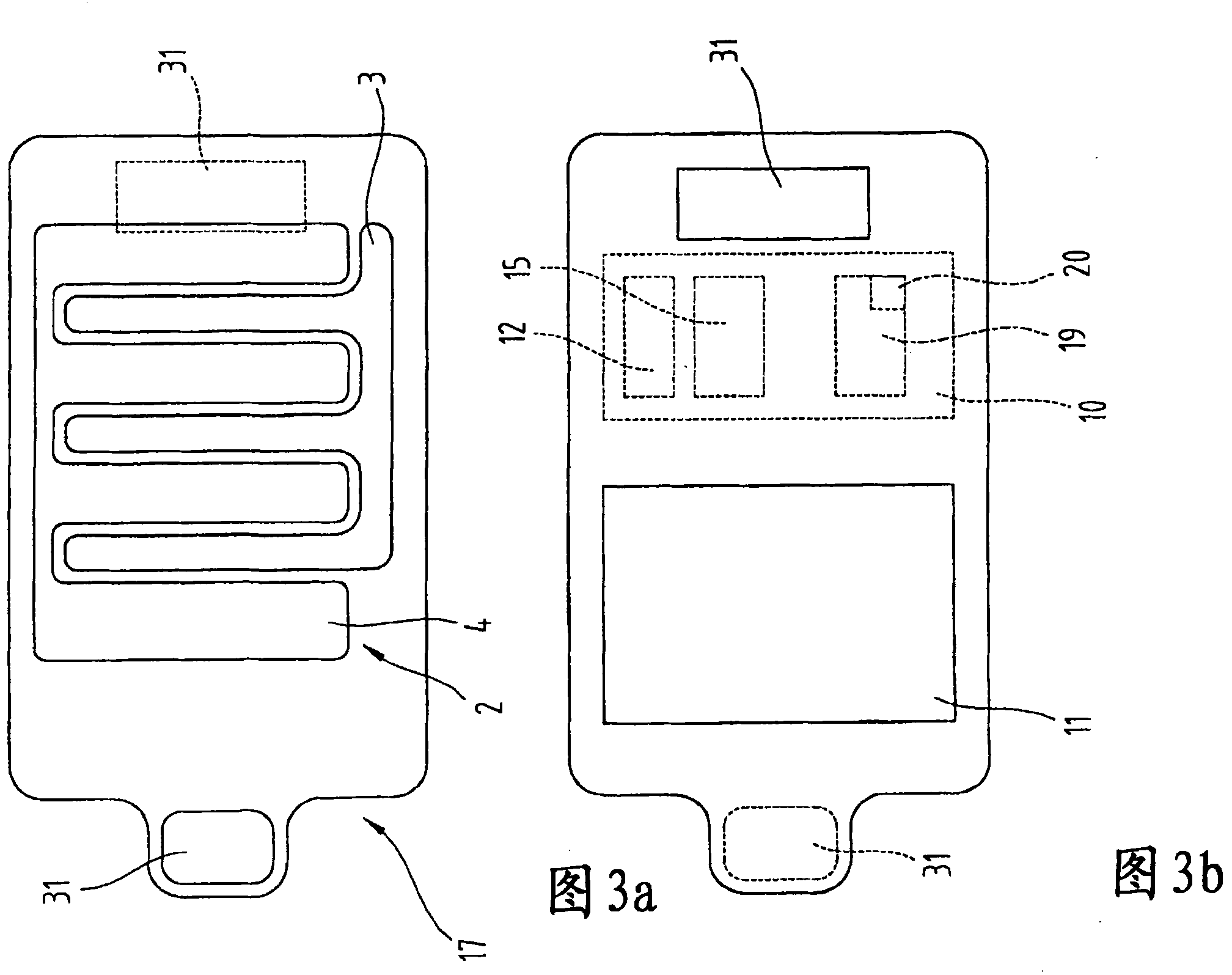
[0091] First of all, it should be pointed out that the same parts in the different embodiments described have the same reference signs or the same part numbers, and the disclosure contained in the entire specification can be transferred to the same reference signs or the same parts according to the meaning. Identical parts labeled. Moreover, the position descriptions selected in this specification, such as upper, lower, side, etc., all involve direct description and displayed drawings. These position descriptions can be transferred to a new position according to their meaning when the position changes. In addition, individual features or combinations of features from the shown and described different embodiments for independent, inventive or solutions according to the invention may also be shown.
[0092] All descriptions of the numerical range in the detailed description should be understood as these numerical ranges also include any and all of its sub-regions. For example, the ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap