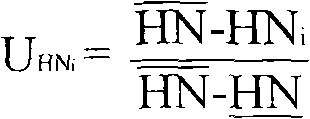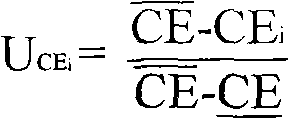Safety start method of tree topology in IPv6 over low power wireless personal area network (6LoWPAN)
A secure startup and tree topology technology, applied in the field of computer networks, can solve problems such as waste, computational complexity, and energy consumption of nodes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
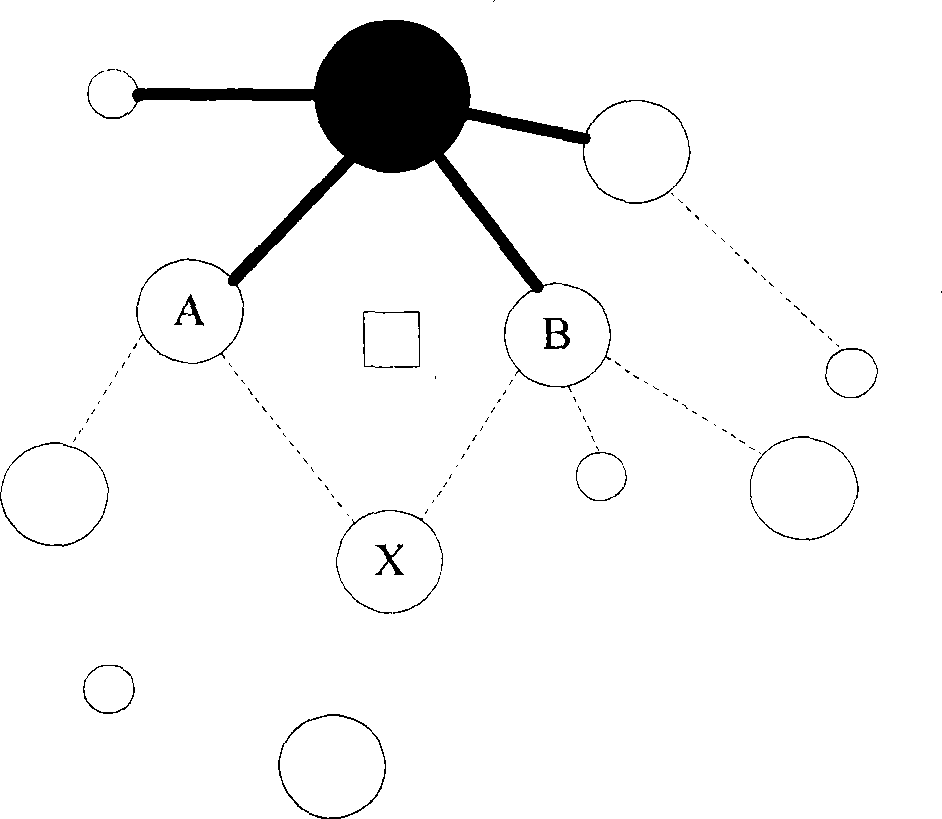
[0035] Specific implementation examples such as figure 1 As shown, it has the following characteristics:
[0036] The entire 6LoWPAN establishes a multi-hop tree topology with a base station and several FFD and RFD nodes. The communication range of each FFD node is d R , the communication range of each RFD node is d r , each node always sends data at an energy level corresponding to its own communication range. Each node senses and collects data and aggregates it to the base station.
[0037] 1. Node pre-allocation
[0038] Before node deployment, the deployer of the network completes the following specific steps:
[0039] 1.1 Generate two point groups G with order q 1 and G 2 , G 1 is the additive group, G 2 is a multiplicative group, and q is a large prime number. generate a bilinear map Generate 3 one-way collision-resistant hash functions H 1 、H 2 and H 3 . Among them, H 1 : {0, 1} * →G 1 , converting a string of arbitrary length to G 1 a point in H 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com