U disk information safety system based on information hiding and digital watermarking technology
An information security system and digital watermarking technology, applied in the field of computer applications, can solve problems such as poor security and insecure encrypted files, and achieve the effects of strong compatibility, low cost, and simple operation methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
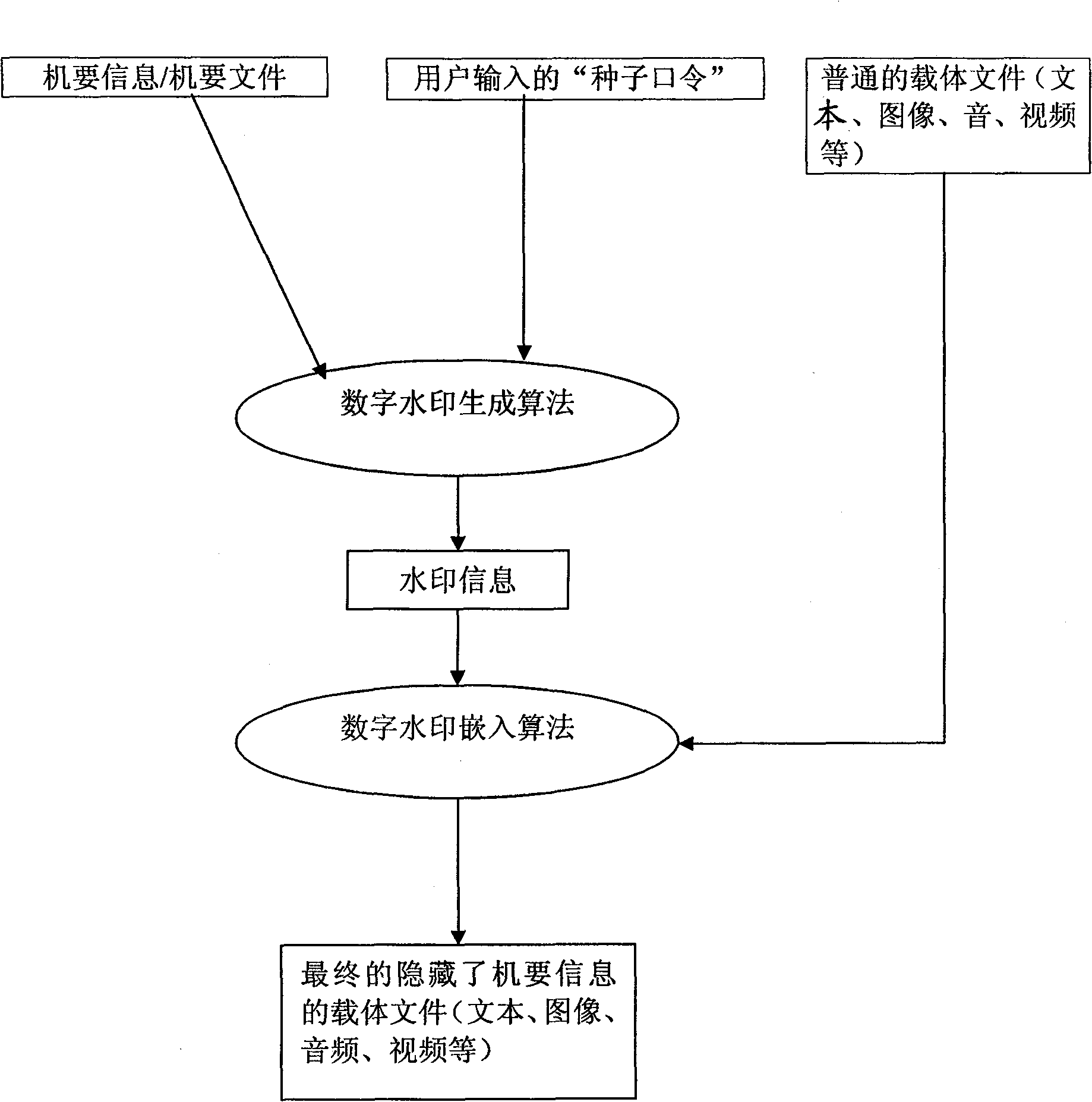
[0035] see figure 1 , this example illustrates the method in which confidential information is loaded and hidden into the carrier.
[0036] First, use the digital watermark generation algorithm to associate the confidential information / confidential files, the "seed" input by the user, and the serial number of the control chip or the wafer number of the storage device or the serial number of the U disk, and combine them as the input parameters of the algorithm. Encoding, generate the intermediate digital watermark information and hidden position, and then use the digital watermark embedding algorithm to load the digital watermark information into the hidden position in the ordinary carrier file to generate a visually indistinguishable carrier file that hides important information / The final carrier file of confidential documents, and does not affect the normal use of the final carrier file. The common carrier files used can be text files, picture files, audio carrier files, v...
Embodiment 2
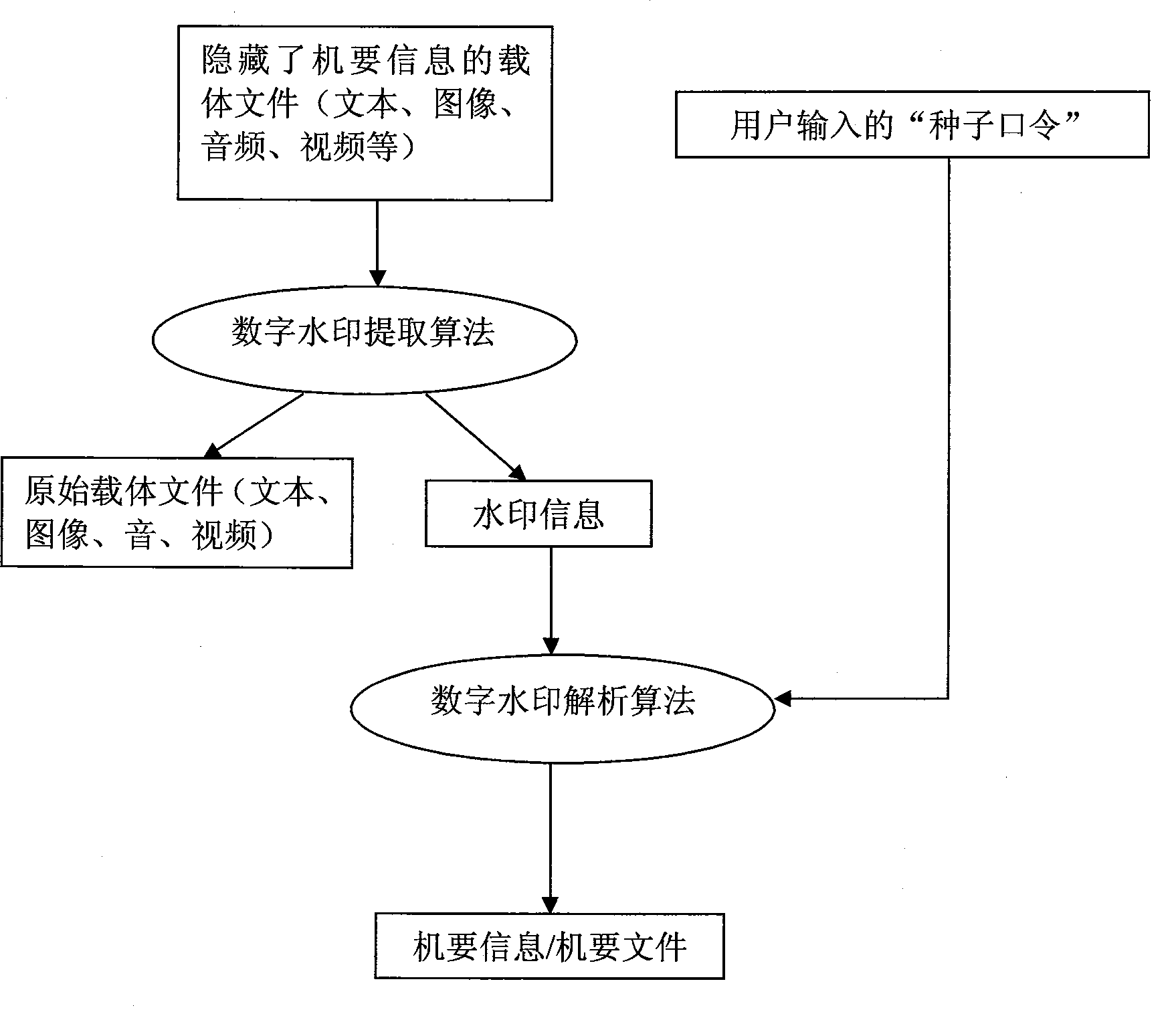
[0038] see figure 2 , this example illustrates how the confidential information hidden in the carrier file is extracted.
[0039] First, use the digital watermark extraction algorithm to extract the digital watermark information from the hidden position in the final carrier file, and at the same time obtain the most original carrier file. For the digital watermark information, use the digital watermark analysis algorithm to extract the user The input "seed" is used as an input parameter to be operated together, and finally the hidden confidential information / confidential file is obtained.
[0040]It should be noted that: regardless of whether the "seed" input by the user when extracting confidential information matches or not the "seed" input when making the watermark, this algorithm will use it as an input parameter for operation. The difference is: the wrong "seed", the final result can only be a garbled output.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com