Secret key management method and system
A key management and key technology, which is applied in the field of information security, can solve problems such as easy readout, fraudulent use of signatures, and insecure key generation mechanisms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
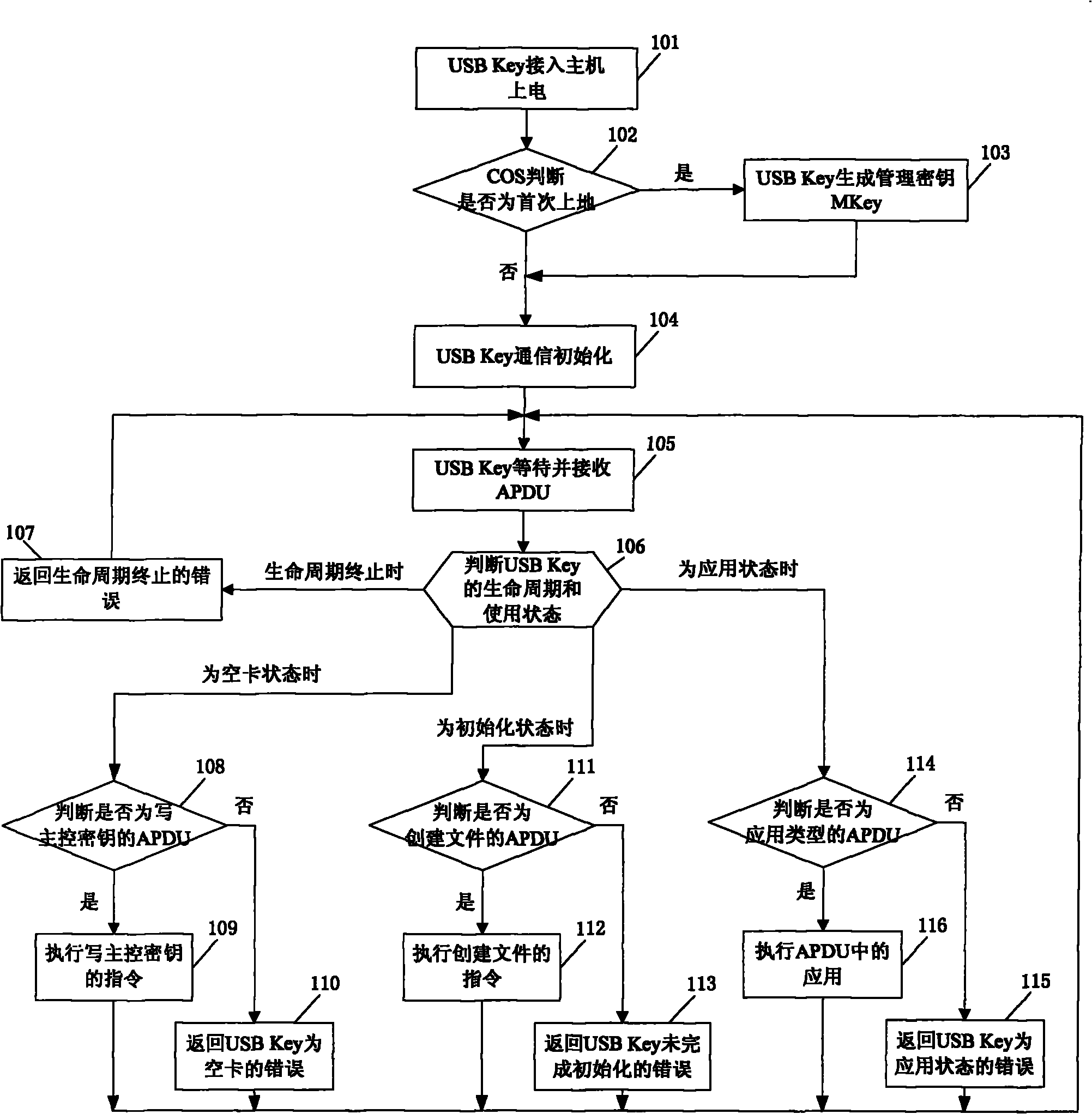
[0181] This embodiment provides a key management method. In this embodiment, the smart key device is described using USBKey as an example. Through the process from power-on to application of the USB Key, the main key in the USB Key and explain the process of key generation, storage, use and destruction, and participate in figure 1 , specifically as follows:
[0182] Step 101, the USB Key is connected to the host computer and powered on;
[0183] Step 102, COS judges whether the USB Key is powered on for the first time, if yes, execute step 103, if not, execute step 104;
[0184] In this embodiment, COS (Chip Operating System) is an operating system in the card, which is stored in the ROM in the above-mentioned USB Key;
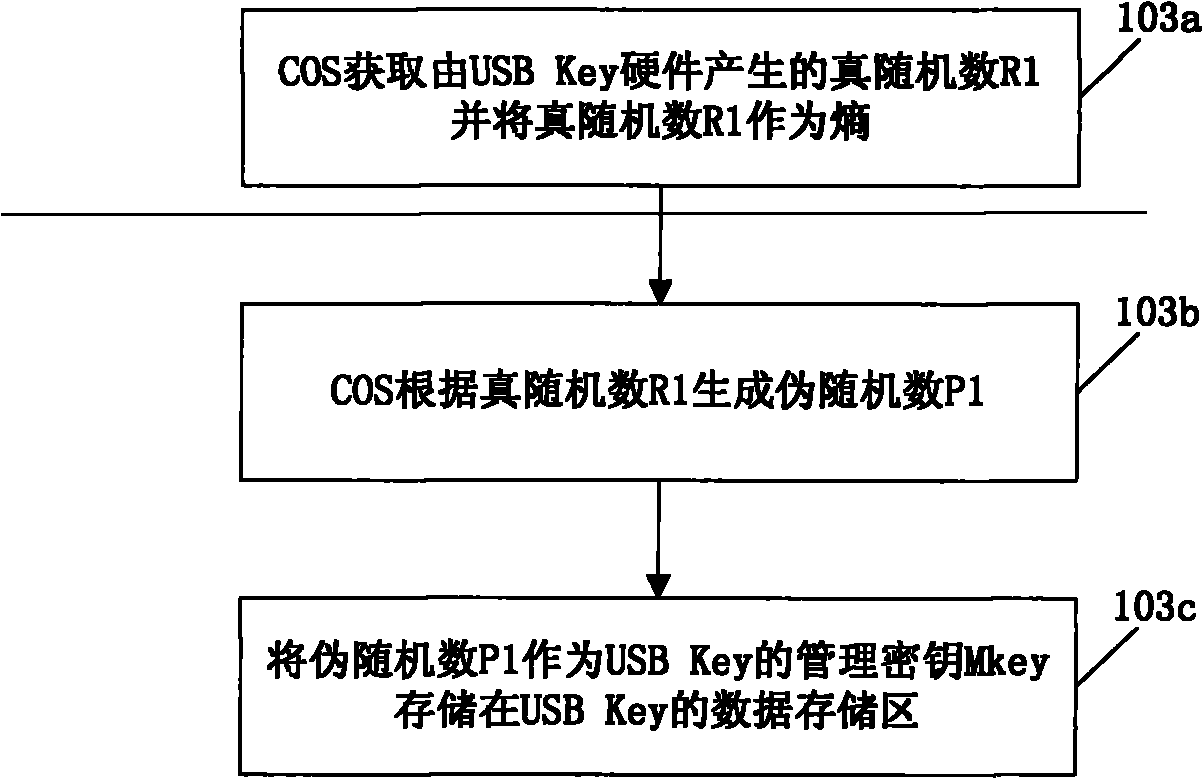
[0185] The method for COS to judge whether the USB Key is powered on for the first time is as follows: COS judges whether the data storage area of the above USB Key is all 0 or all F, when the data storage area of the USB Key is all 0 or all F, it means ...
Embodiment 2
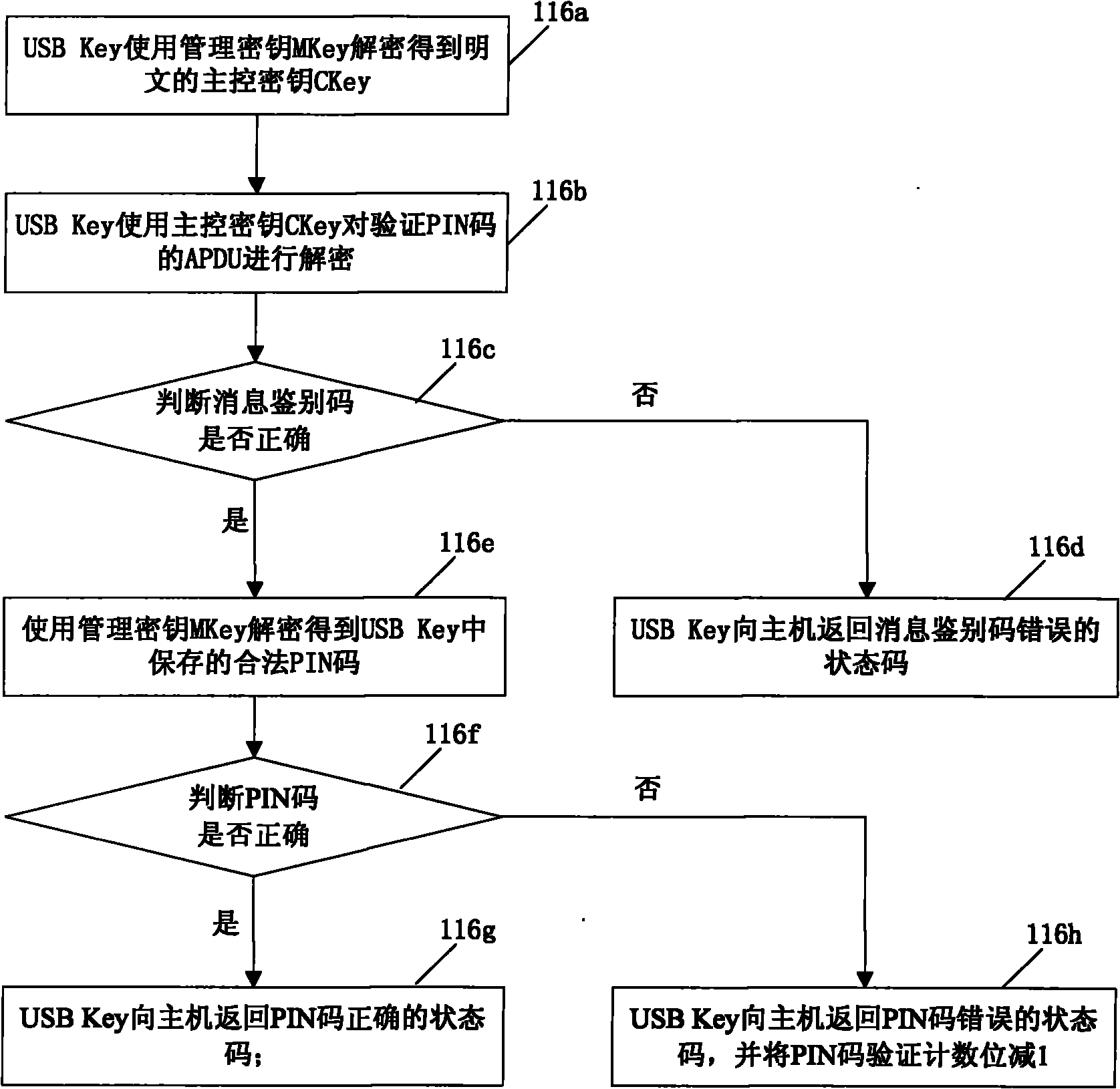
[0329] This embodiment provides a key management method. In this embodiment, the smart key device is described using USBKey as an example. Through the process from power-on to application of the USB Key, the main key in the USB Key The process of generating, storing, using and destroying the key is described. It is different from embodiment 1. In this embodiment, the USB Key first judges the APDU type according to the received APDU, and then judges the usage status of the USBKey. Figure 4 ,details as follows:
[0330] Step 201, the USB Key is connected to the host computer and powered on;
[0331] Step 202: COS judges whether the USB Key is powered on for the first time, if yes, execute step 203, if not, execute step 204;
[0332] In this embodiment, COS (Chip Operating System) is an operating system in the card, which is stored in the ROM in the above-mentioned USB Key;
[0333] The method for COS to judge whether the USB Key is powered on for the first time is as follows:...
Embodiment 3
[0438] This embodiment provides a key management method. The process of key management includes multiple processes, mainly four processes of key generation, key storage, key use and key destruction. In the embodiment of the present invention , the smart key device is described by taking the USB Key as an example, and the management process of various keys in the USB Key is illustrated by taking the USB Key from power-on to the completion of the application of the USB Key as an example.
[0439] join Figure 5 ,Specific steps are as follows:
[0440] Step 301, the USB Key is connected to the host computer and powered on;
[0441] Step 302, COS judges whether the USB Key is powered on for the first time, if yes, execute step 303, if not, execute step 304;
[0442] In this embodiment, COS is an operating system in the card, which is stored in the ROM in the above-mentioned USB Key;
[0443] The method for COS to judge whether the USB Key is powered on for the first time is as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com