Method for consuming electronic wallet
An electronic wallet and algorithm technology, applied in the field of information security, can solve the problems of insufficiency of electronic wallet transfer operation and consumption operation, and achieve the effect of convenient management, simplified implementation, and safe transaction process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
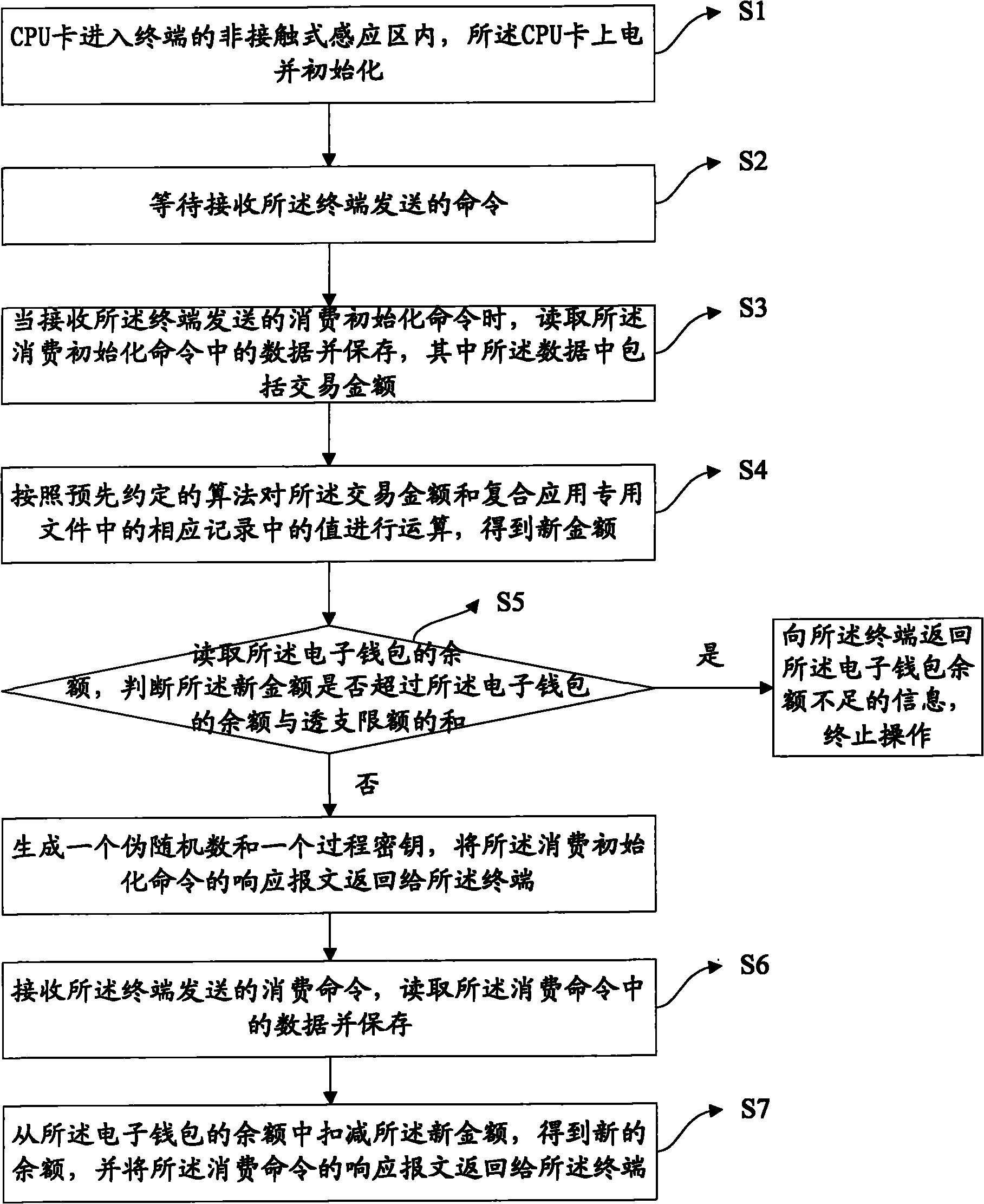
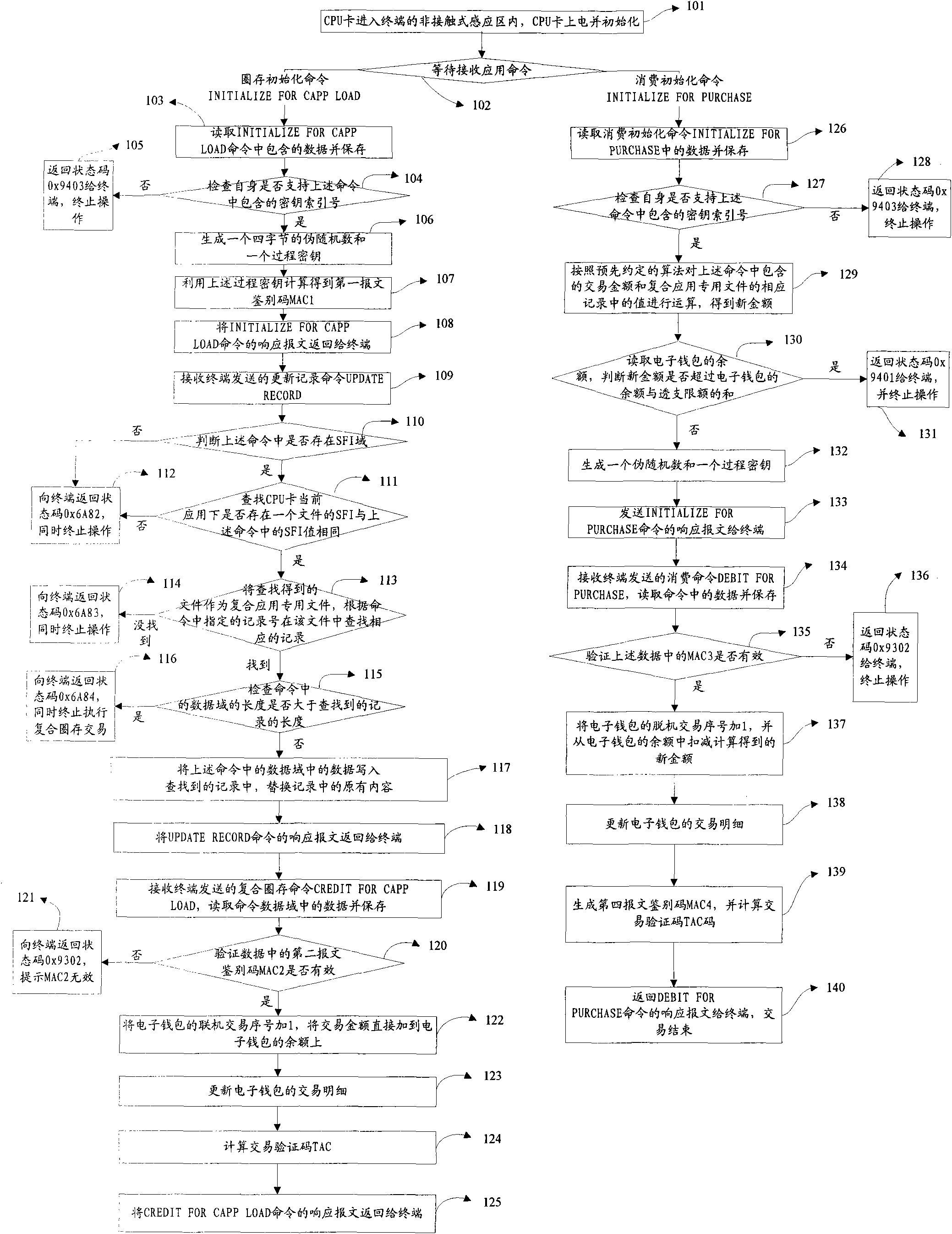
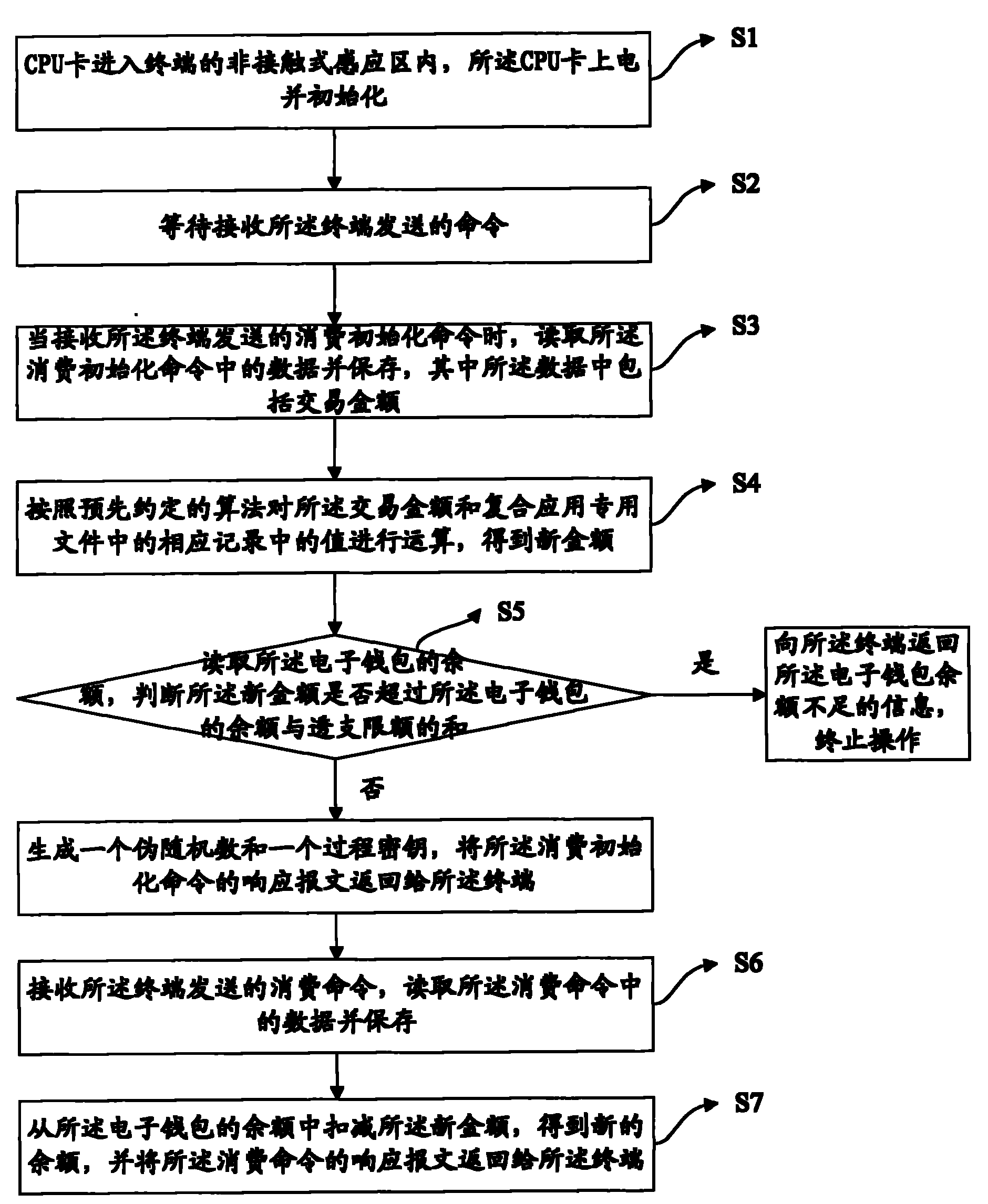
[0030] The embodiment of the present invention provides a method for consuming electronic wallets. In this embodiment, the electronic wallet in the CPU card not only has all the transaction functions of wallets that support composite applications, but also supports composite loading and consumption functions. , and the compound loading operation of the electronic wallet in the CPU card is carried out at the CPU terminal. When performing the compound loading operation in this embodiment, the transaction amount is directly added to the balance of the electronic wallet. Correspondingly, when consuming, According to the pre-agreed algorithm, the transaction amount and the value in the corresponding record of the composite special file are calculated to obtain the new amount, and then the new amount is deducted from the balance of the electronic wallet to obtain the new balance of the electronic wallet, and the consumption operation is completed .
[0031] see figure 2 , a method...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com