Formal verification method for security protocol
A formal verification and security protocol technology, applied in the field of formal verification of security protocols based on model detection, to achieve the effect of reducing scale, reducing the probability of state explosion, and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The method of the present invention will be described in detail below in conjunction with the drawings and specific embodiments.
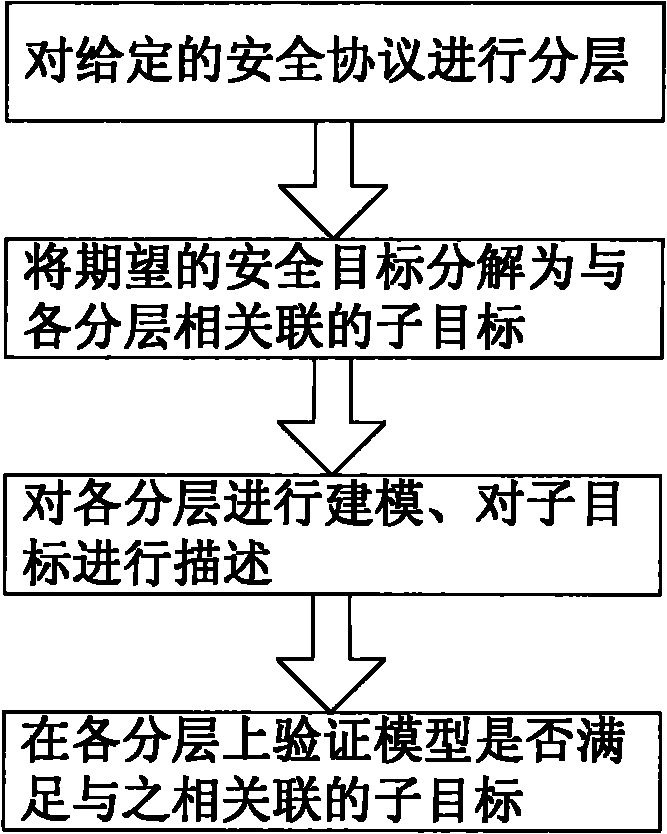
[0030] Such as figure 1 As shown, under the condition of a given network environment, a security protocol is given, and the flow of the verification method of the present invention includes steps such as protocol layering, target decomposition, hierarchical modeling and description, and layered verification.
[0031] 1) Protocol layering Specific protocols use certain security measures in order to achieve security goals. In actual protocols, it is reflected in the fact that the protocols include certain steps to achieve these security guarantees. Therefore, we can stratify the protocol according to the functions realized by the protocol steps. The layering should ensure that the functions of different layers are relatively independent or that the underlying functions are the basis for the realization of the upper layer functions and try to a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com