Method, system and method for controlling access of host computer
A technology for controlling hosts and hosts, applied in the field of network security, can solve problems such as inability to effectively control host access, and achieve the effect of controlling host access and facilitating access management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
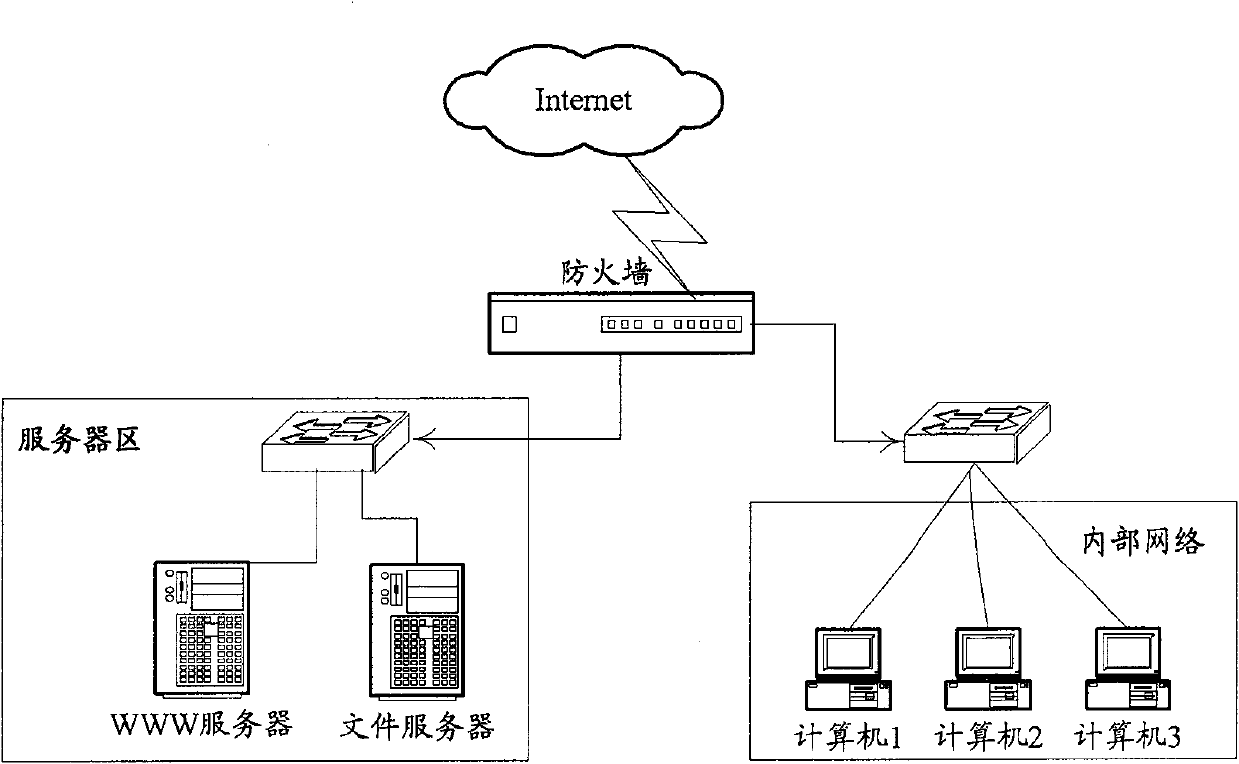
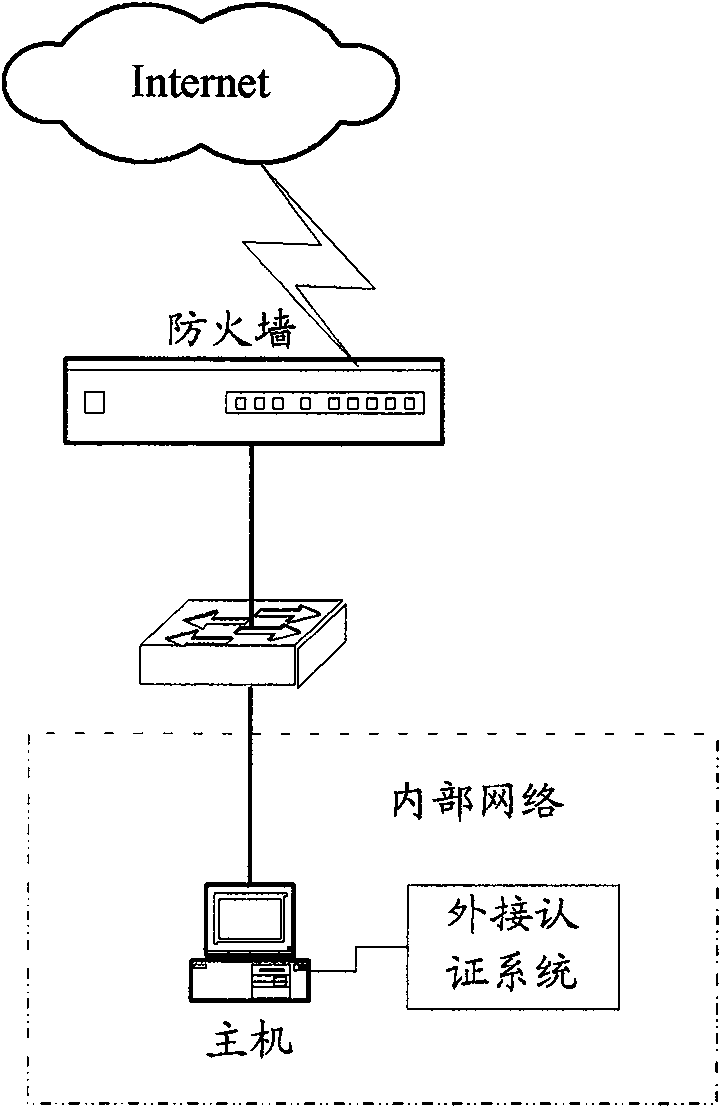
[0018] The deployment location of the firewall determines that it is the first security barrier for network security, so its own software security requirements are extremely high, and the operating system used is also proprietary or security-reinforced. The USB (Universal Serial BUS) interface is a standard peripheral interface on modern host systems, which is versatile and extensive. The main idea of the invention is to use the firewall to communicate with the host USB system to realize the user's identity authentication mechanism, thereby effectively controlling the host access, so that the unauthorized intranet host cannot access the Internet.
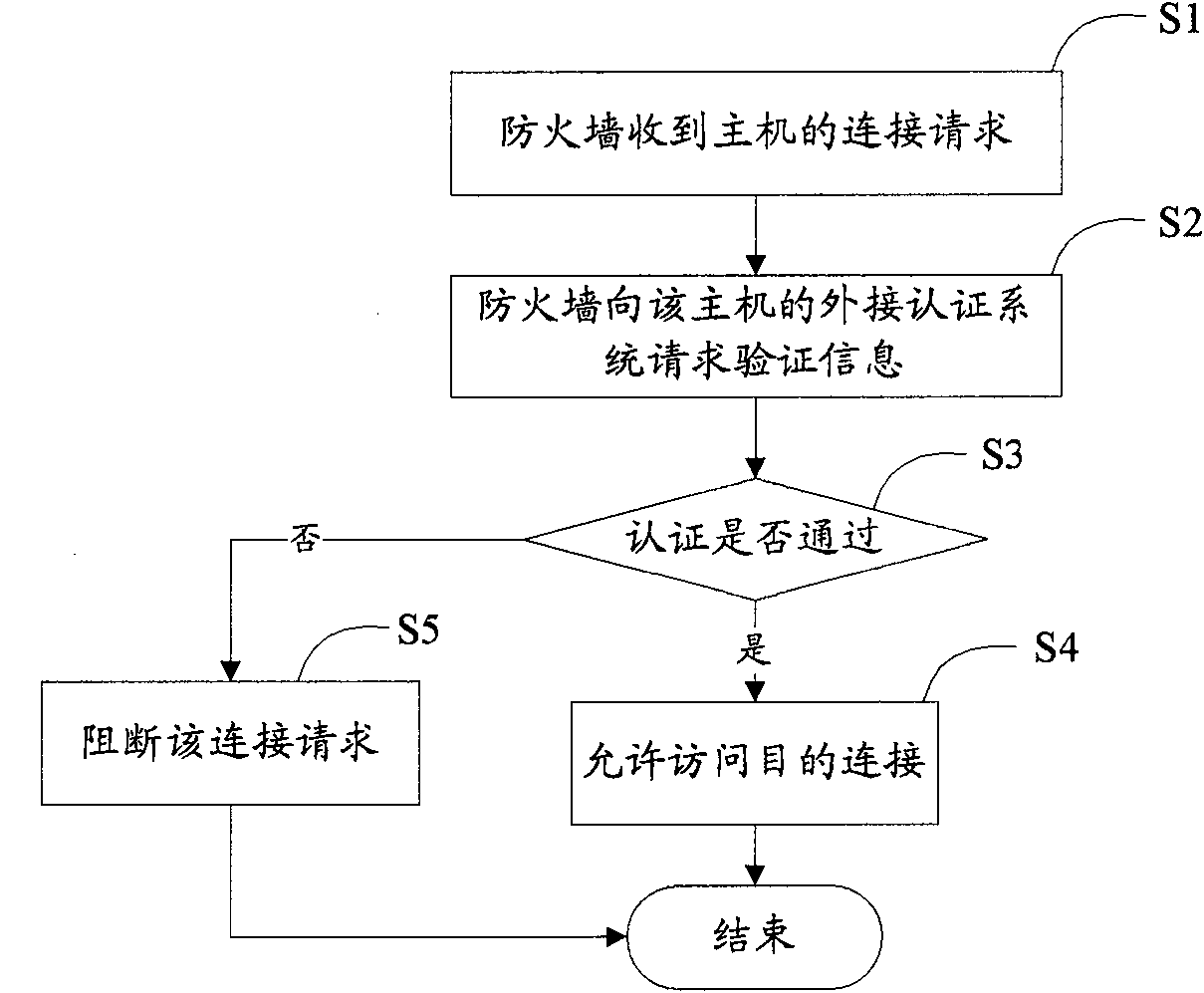
[0019] See figure 2 As shown, an embodiment of the present invention provides a method for controlling host access, which includes the following main steps:
[0020] S1. The firewall receives the connection request initiated by the internal network host.
[0021] After the firewall receives the connection request, it obtains the IP add...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com