Network access method, device and system
A technology for network access and configuration information, applied in the field of communication, can solve problems such as increasing network signaling load, and achieve the effects of avoiding sudden spikes, reducing signaling load, and solving congestion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
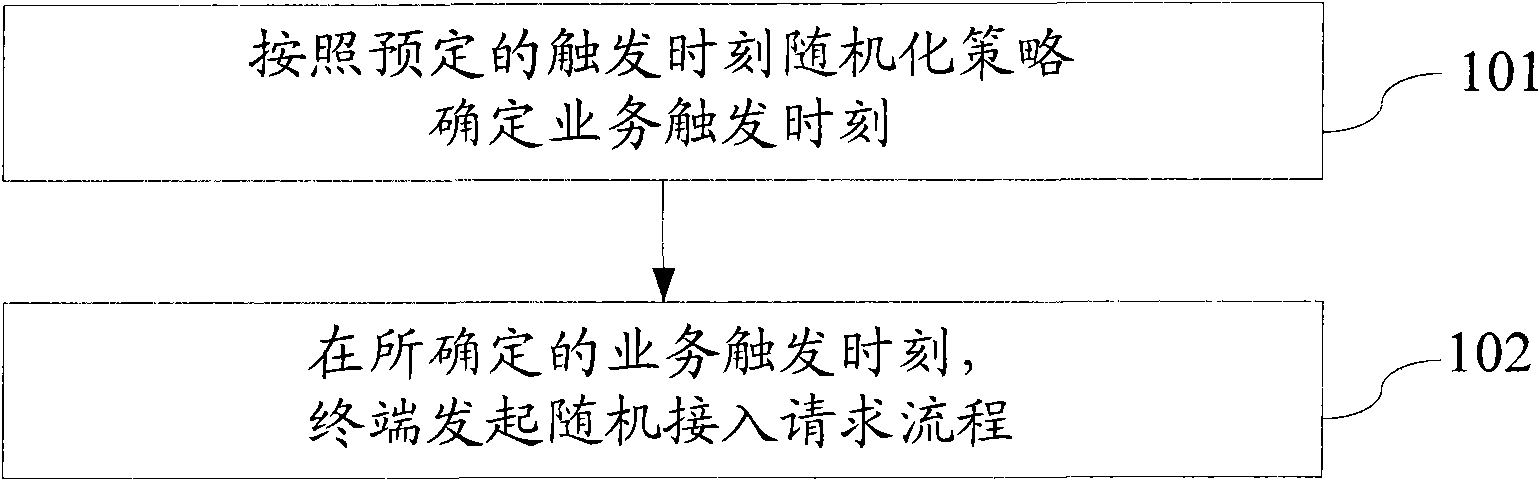
[0039] Such as figure 1 As shown, the network access method provided in this embodiment includes:
[0040] 101. Determine a service trigger time according to a predetermined trigger time randomization strategy.
[0041] The predetermined trigger moment randomization strategy may be to randomly select a certain moment within the time interval for data transmission as the service trigger moment; it may also be by setting a trigger condition (such as a threshold value) The moment of satisfaction is the service trigger moment.
[0042] The service triggering time may be the network access time when the M2M terminal reports information for a specific service; taking the smart meter reading service as an example, the service triggering time may be when the M2M terminal needs to report power consumption data. Moment of network random access request.
[0043] 102. At the determined service triggering moment, the terminal initiates a random access request procedure.
[0044] Specif...
Embodiment 2
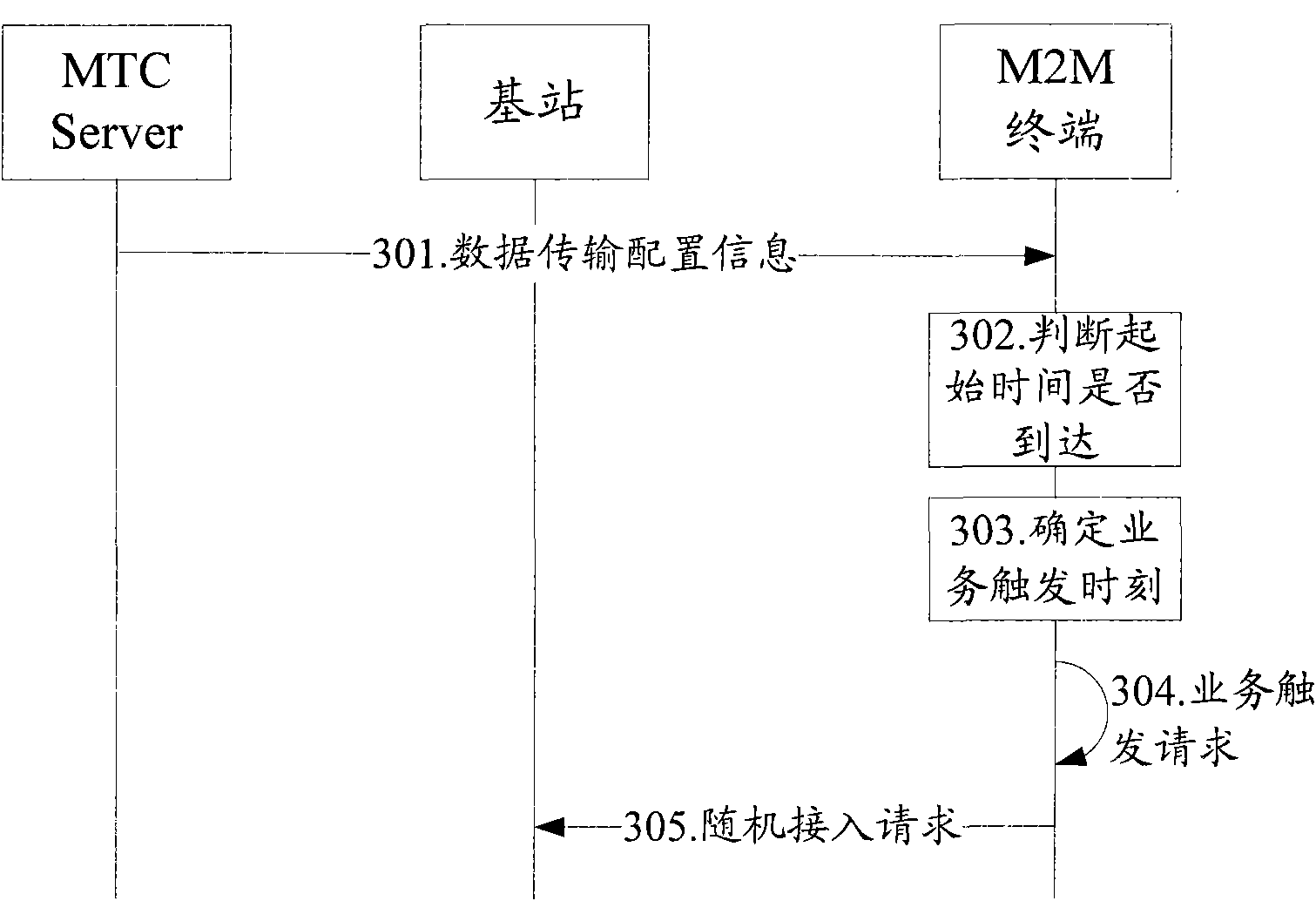
[0052] to combine image 3 As shown, the network access method provided in this embodiment includes the following steps:
[0053] 301. The MTC Server (Machine Type Communication Server, machine communication server) sends data transmission configuration information to the M2M terminals in the group.
[0054] Wherein, the M2M terminals in the group refer to the M2M terminals of the same terminal group;
[0055]In this embodiment, the data transmission configuration information includes the start time and valid duration of data transmission by the M2M terminal; the start time and valid duration together define a time interval in which an M2M terminal can transmit data. If the data transmission configuration information does not include a start time, the time when the terminal receives the data transmission configuration information by default is the start time of data transmission.
[0056] In addition, the data transmission configuration information may also include service r...
Embodiment 3
[0074] In the second embodiment, since the application layer of the M2M terminal cannot know the configuration of the access channel on the wireless interface, it is impossible to maximize the use efficiency of the service random trigger mechanism. For example, if the current cell is equipped with two random access channels at the same time, it can provide access opportunities for two M2M terminals at the same time, but the M2M terminal application layer can only select the service trigger time in the dimension of time, so it is vacant. 1 / 2 of the access channel resources. Based on the above reasons, this embodiment provides a network access method based on RR layer control to implement a service trigger randomization mechanism.
[0075] to combine Figure 4 As shown, the network access method provided in this embodiment includes the following steps:
[0076] 401. The MTC Server sends data transmission configuration information to the M2M terminals in the group.
[0077] In...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com