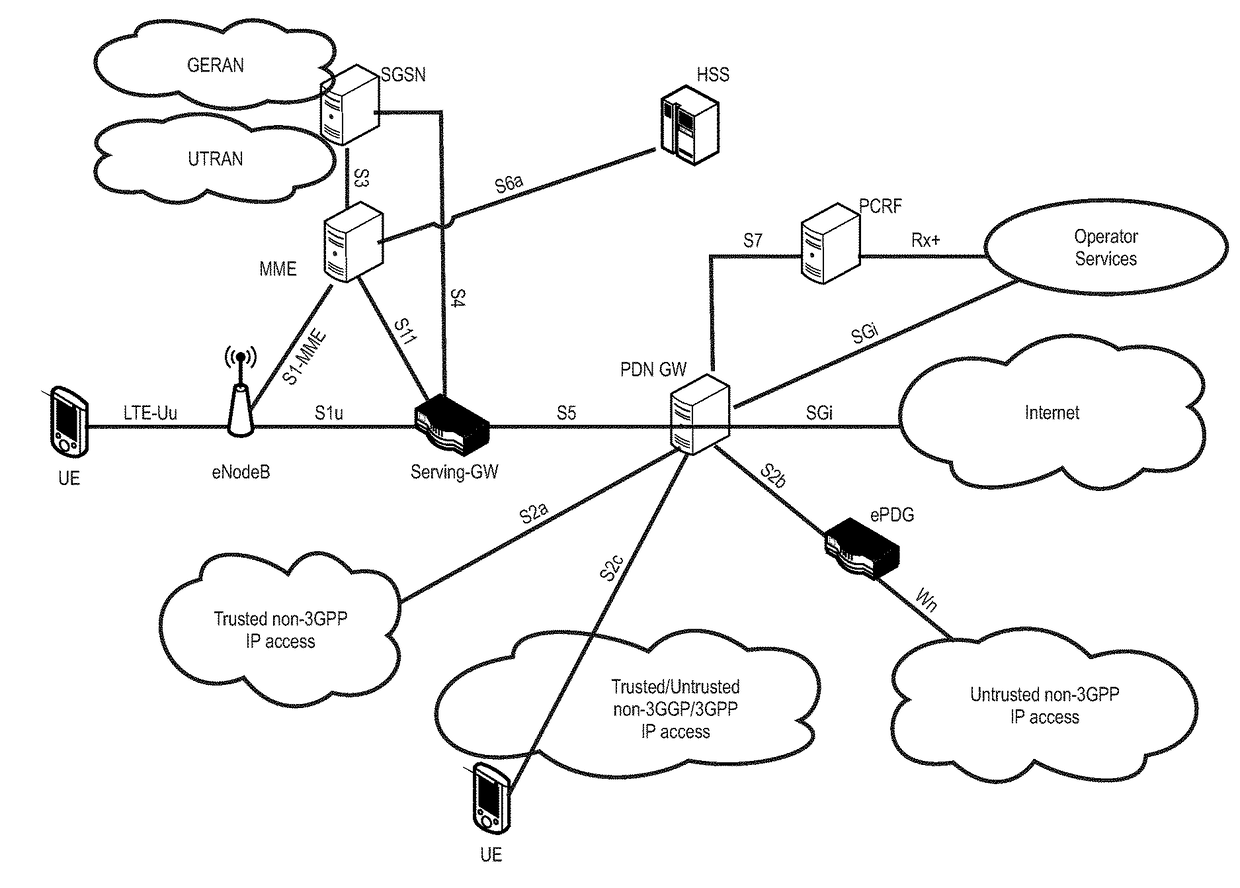
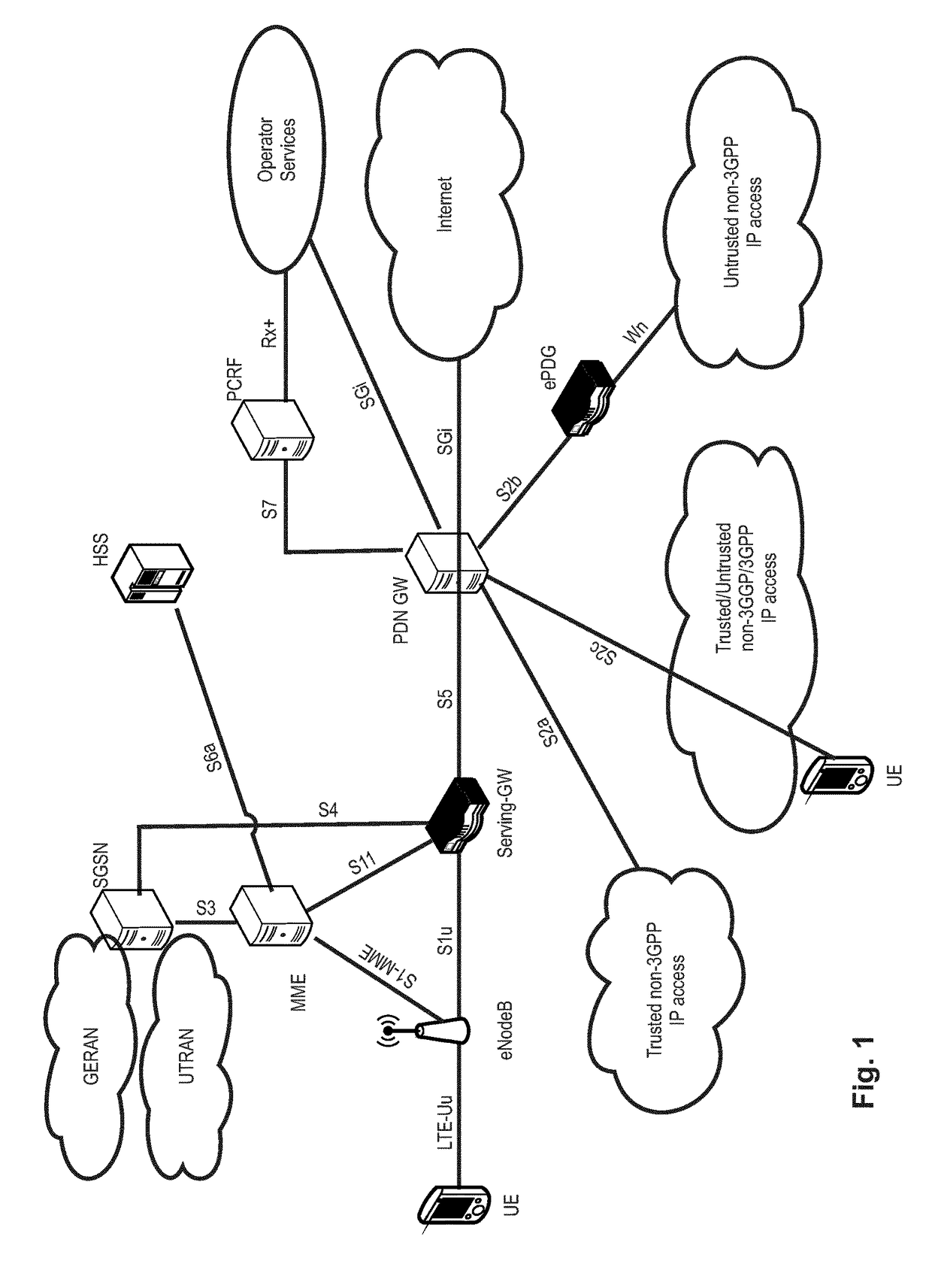
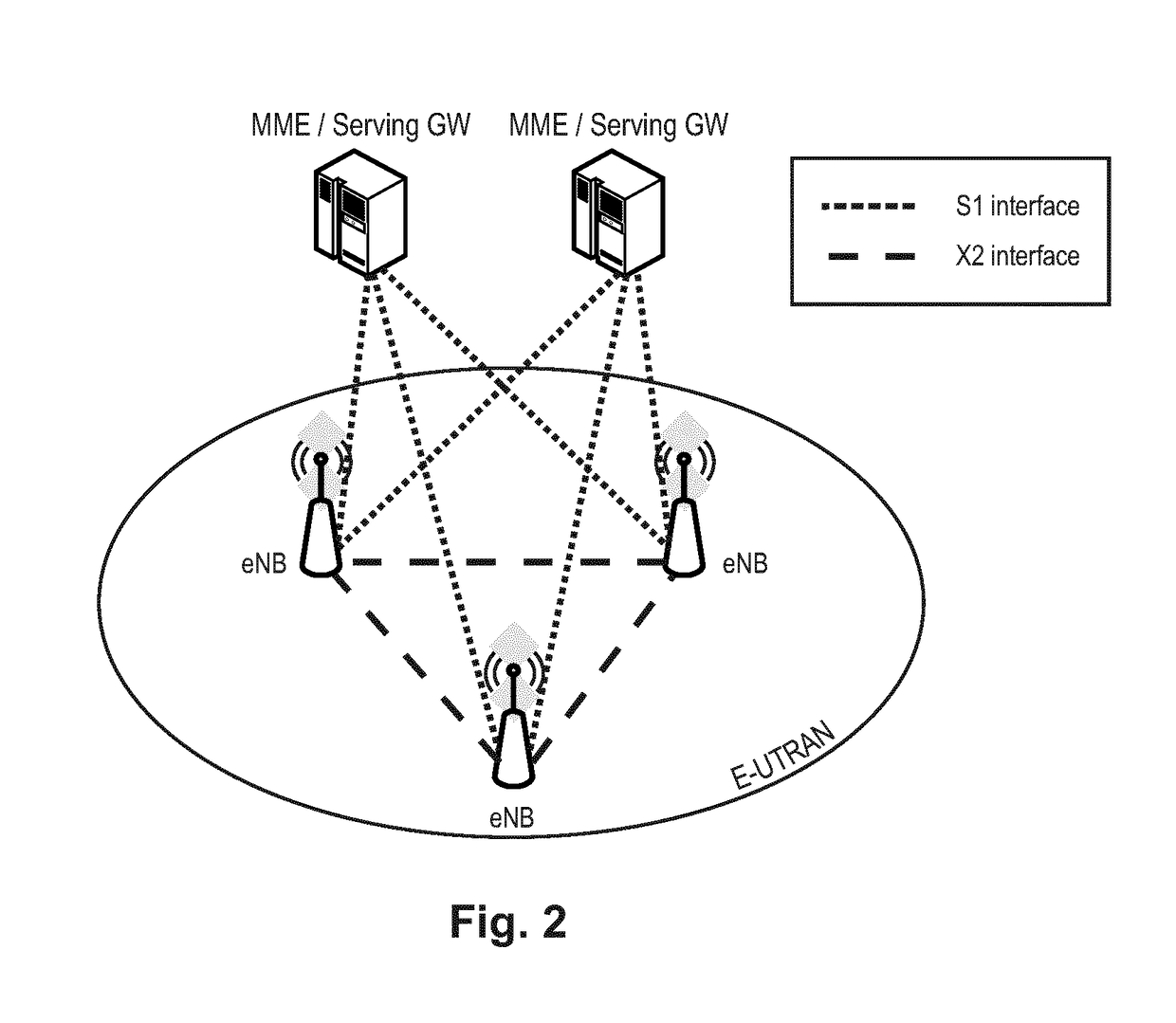
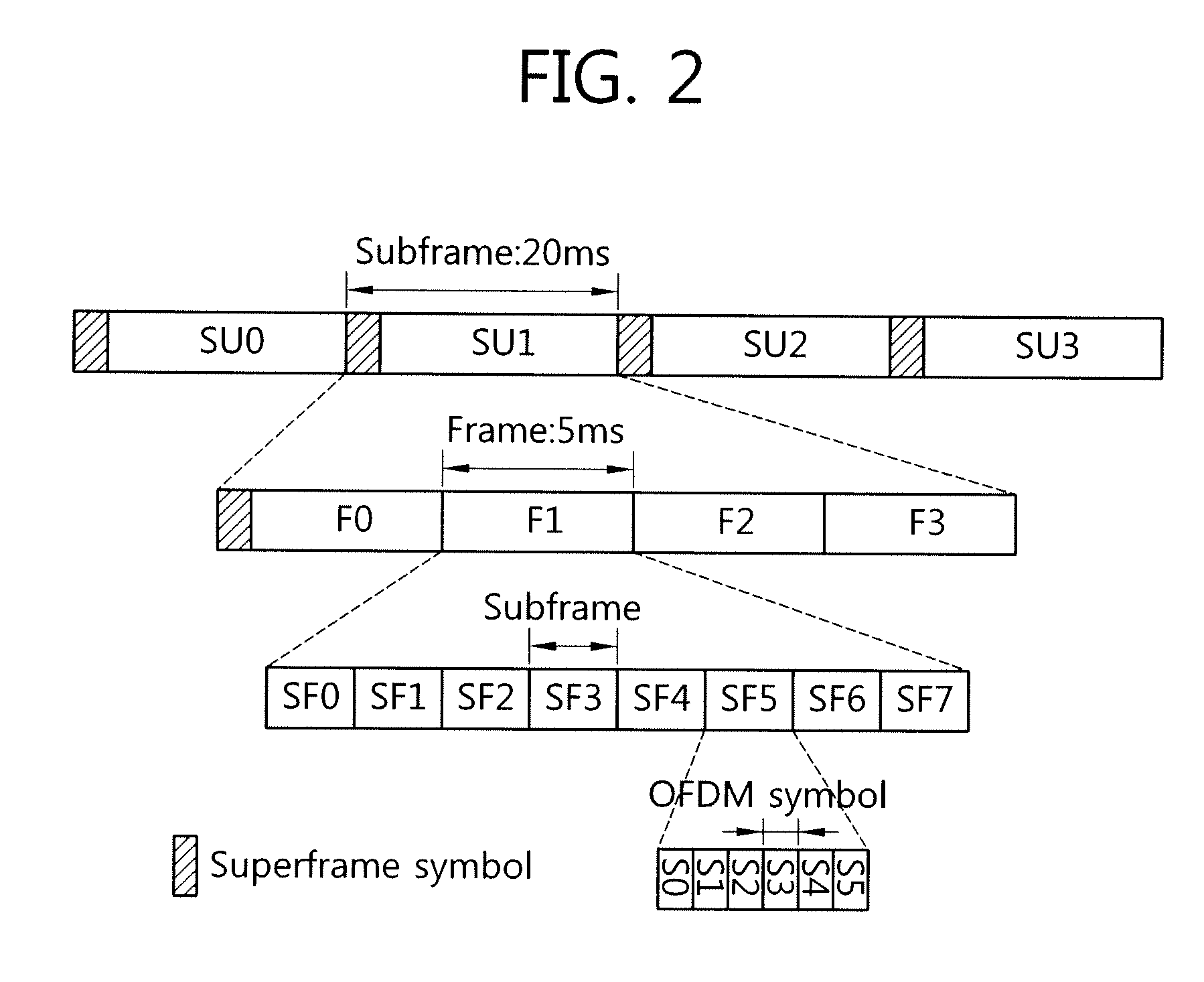
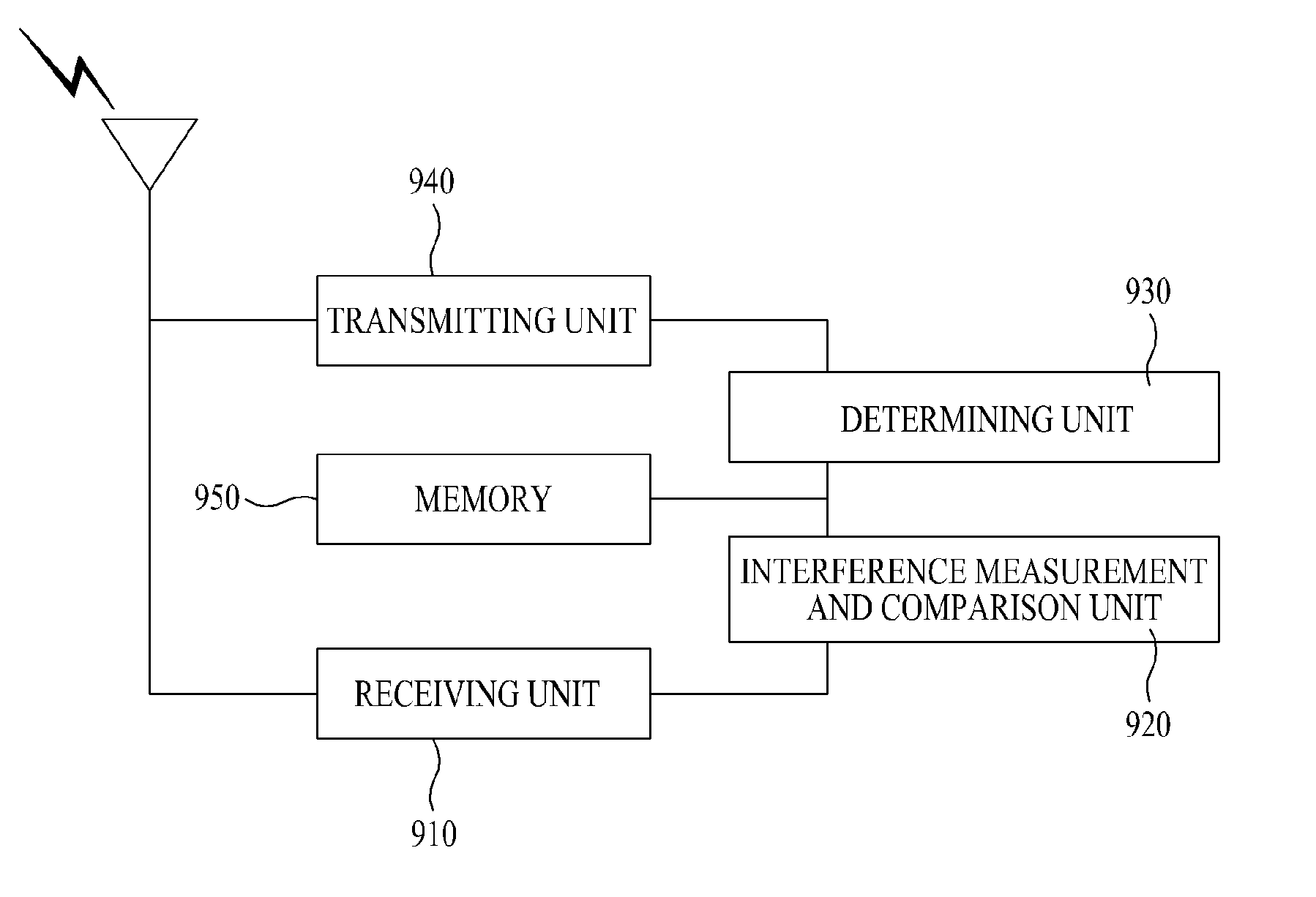
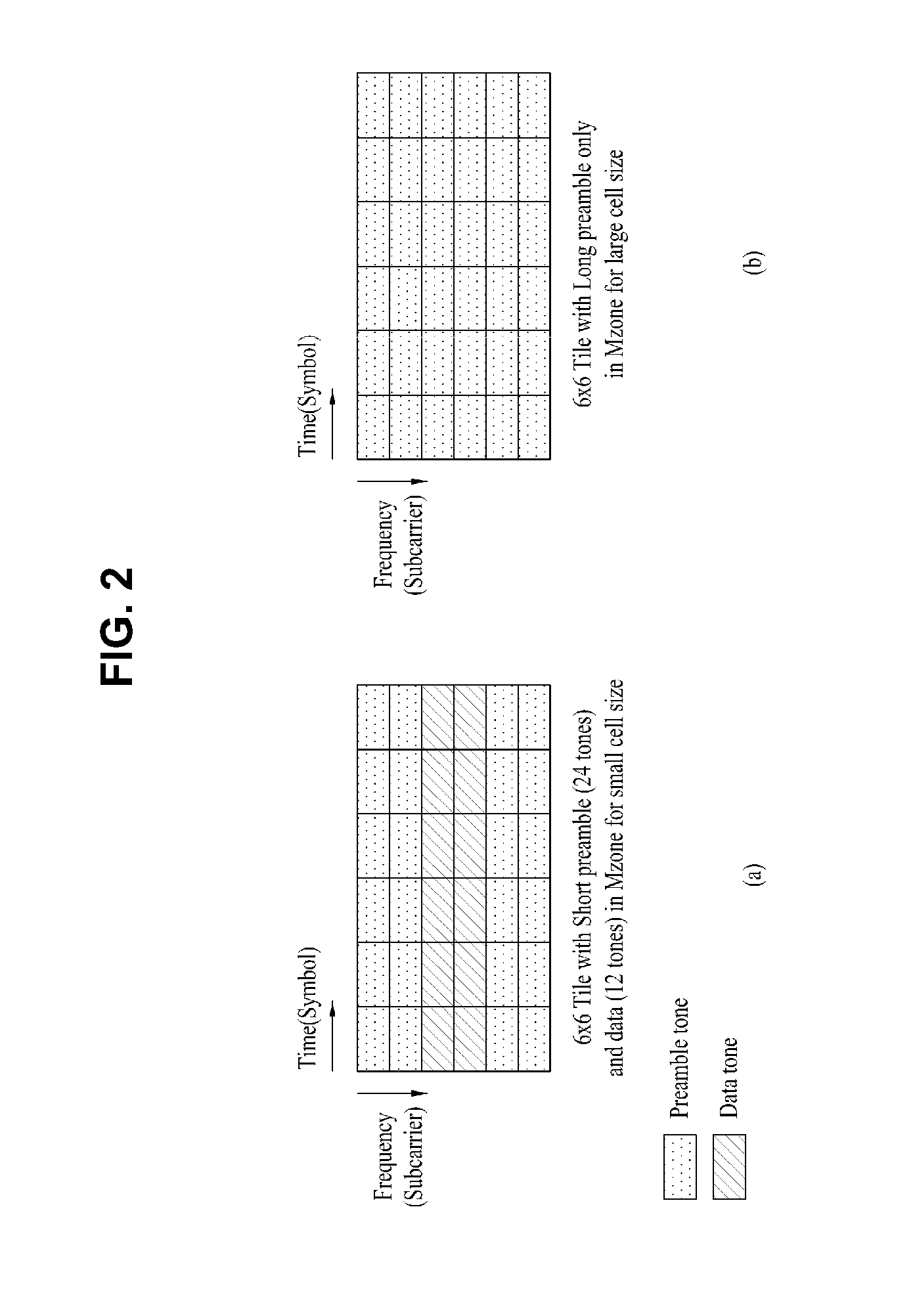
Patents
Literature
131 results about "Request procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for equitable bandwidth allocation for content distribution networks
ActiveUS7801177B2Optimize allocationReduce capacityError preventionFrequency-division multiplex detailsPerformance functionContent distribution
Owner:TELCORDIA TECHNOLOGIES INC
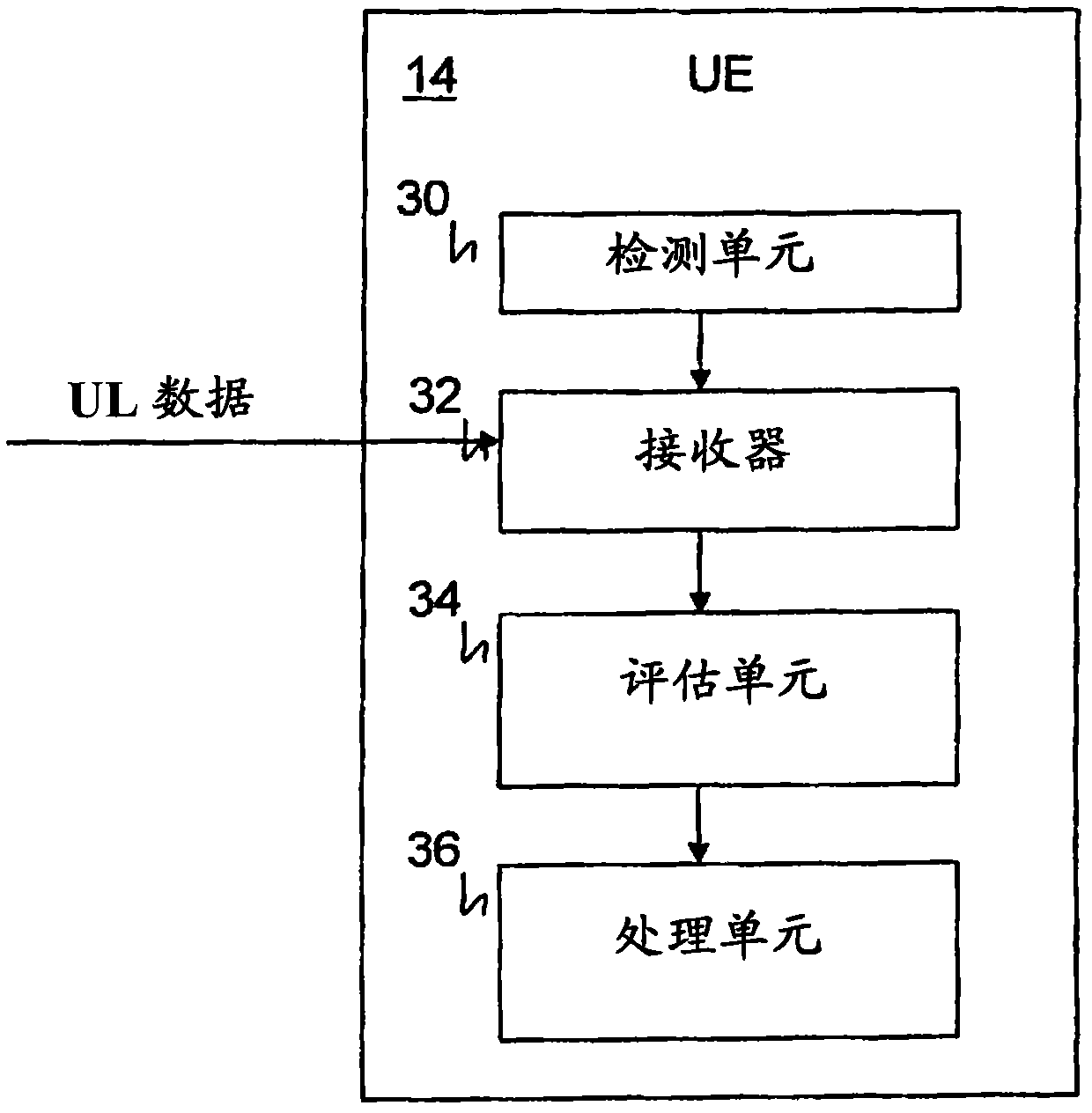
Threshold-based and power-efficient scheduling request procedure
ActiveUS20150117342A1Shorten total active timeReduce power consumptionConnection managementChannel coding adaptationPower efficientRequest procedure
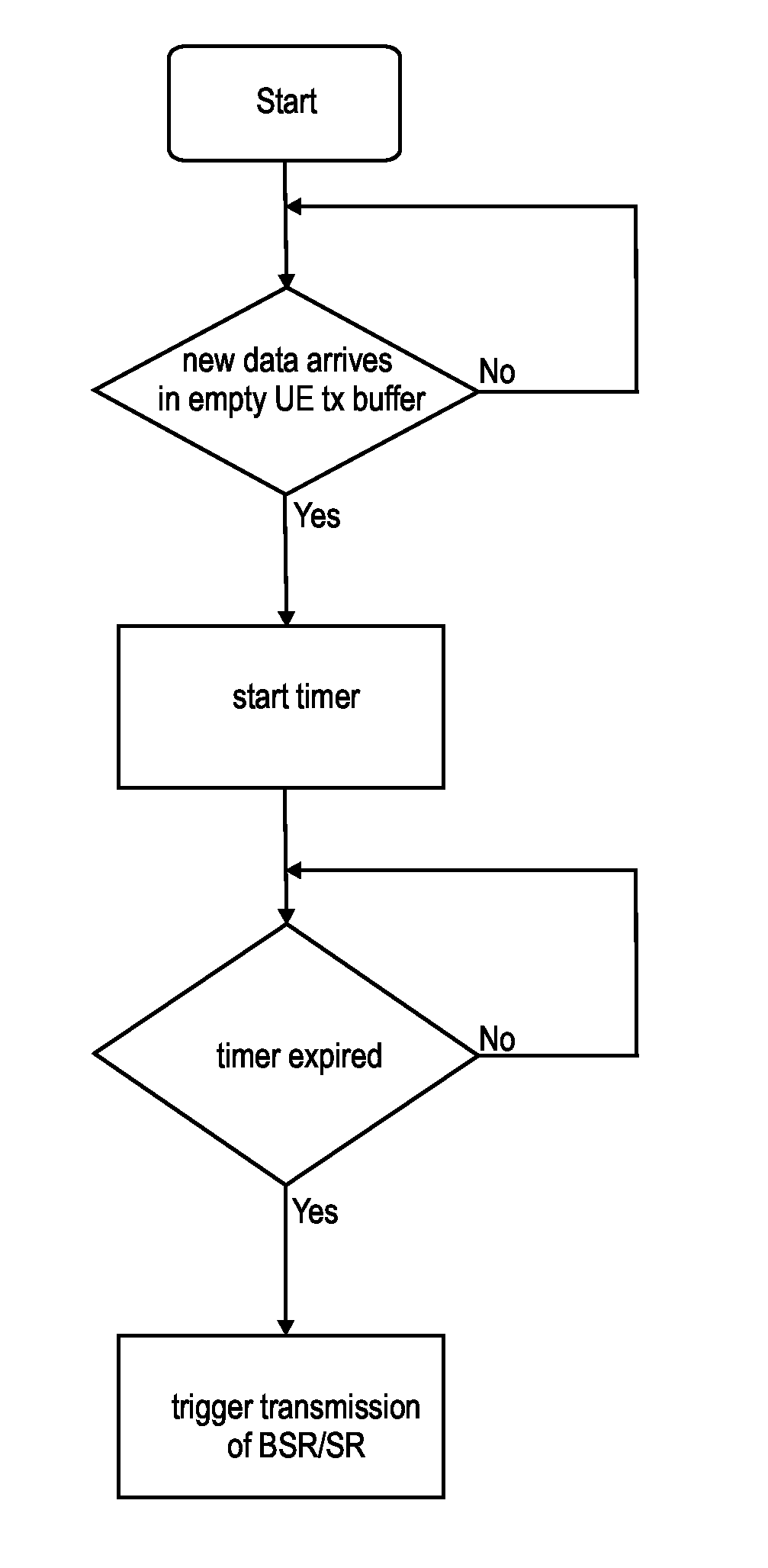
The invention relates to methods for improving a scheduling request transmission between a UE and a base station. The transmission of the scheduling request is postponed, by implementing a threshold that the data in the transmission buffer has to reach, before a transmission of the scheduling request is triggered. In one variant, the data in the transmission buffer needs to reach a specific amount, to trigger a scheduling request. The invention refers to further improvements: the PDDCH monitoring time window is delayed after sending a scheduling request; the dedicated scheduling request resources of the PUCCH are prioritized differently such that low-priority scheduling requests are transmitted less often.
Owner:APPLE INC
Method for performing efficient bsr procedure using sps resource
ActiveUS20090197610A1Guaranteed normal transmissionWireless commuication servicesCommunications systemStart time
The present invention relates to a wireless communication system and a terminal providing a wireless communication service and to a method by which a base station and a terminal transmit and receive data in an evolved universal mobile telecommunications system (E-UMTS) evolved from universal mobile telecommunications system (UMTS) or a long term evolution (LTE) system, and more particularly, to a method whereby, in requesting allocation of radio resources by a user equipment (UE), which has been allocated continuous allocation radio resources, from a base station, the UE compares an allocation time point of continuous allocation radio resources and a start time point of a radio resource request procedure and effectively transmit a radio resource allocation request.
Owner:LG ELECTRONICS INC
Scheduling request procedure for d2d communication
The present invention relates to a D2D capable a communication method and to a transmitting user equipment, which transmits data to a receiving user equipment over a direct link data channel, uses the services of the eNode B in order to have resources allocated for transmitting said data. To this end the UE sends to the eNB scheduling information using resources of a subframe dedicated for standard uplink communication through the eNode B, rather than using resources on the subframe dedicated to D2D data transmission. In order to allow the eNB to distinguish whether the received scheduling request is for allocating resources for transmitting data over the direct link channel or over the eNB, UE may send along with the scheduling information also identification information associated to the scheduling information.
Owner:SUN PATENT TRUST
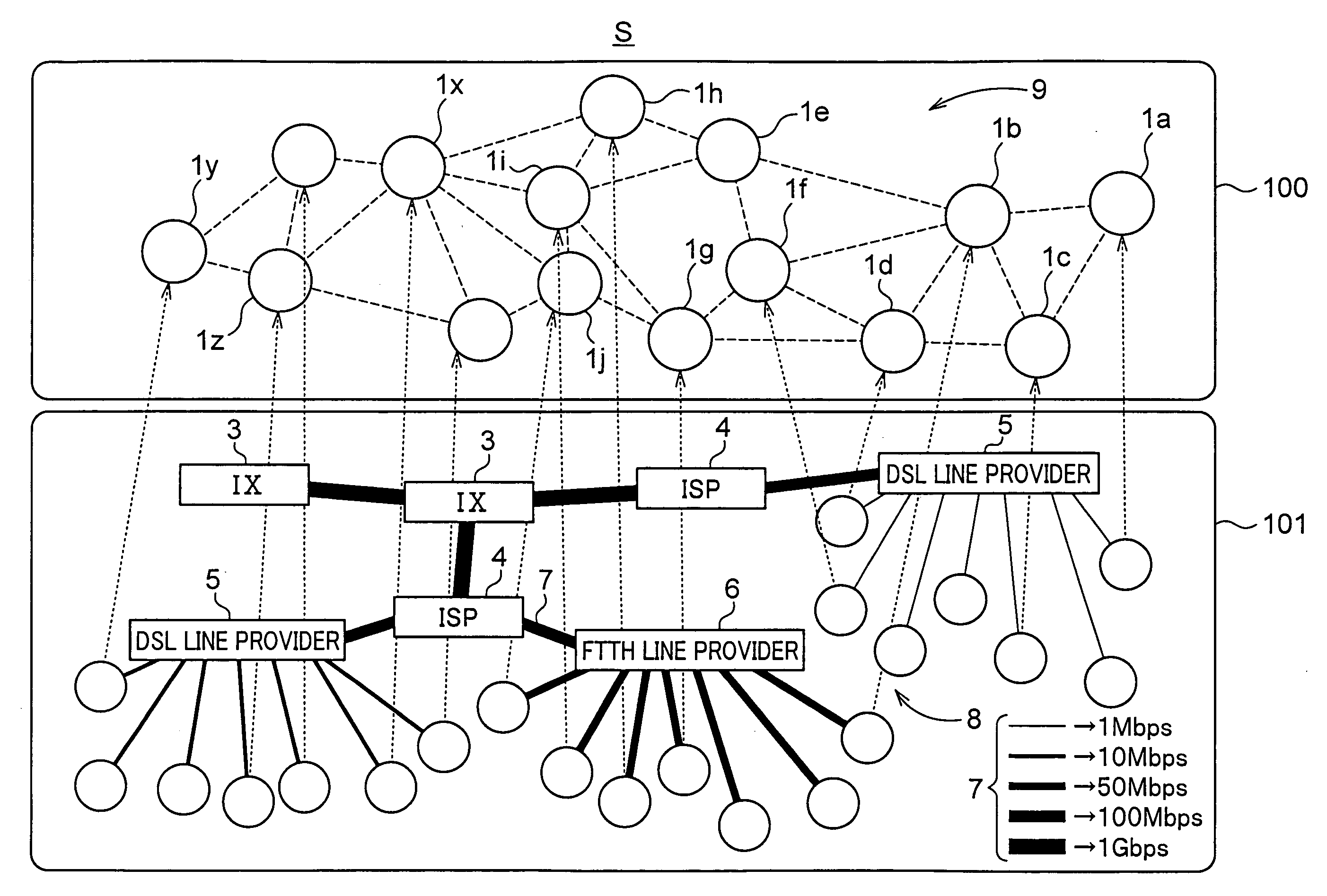
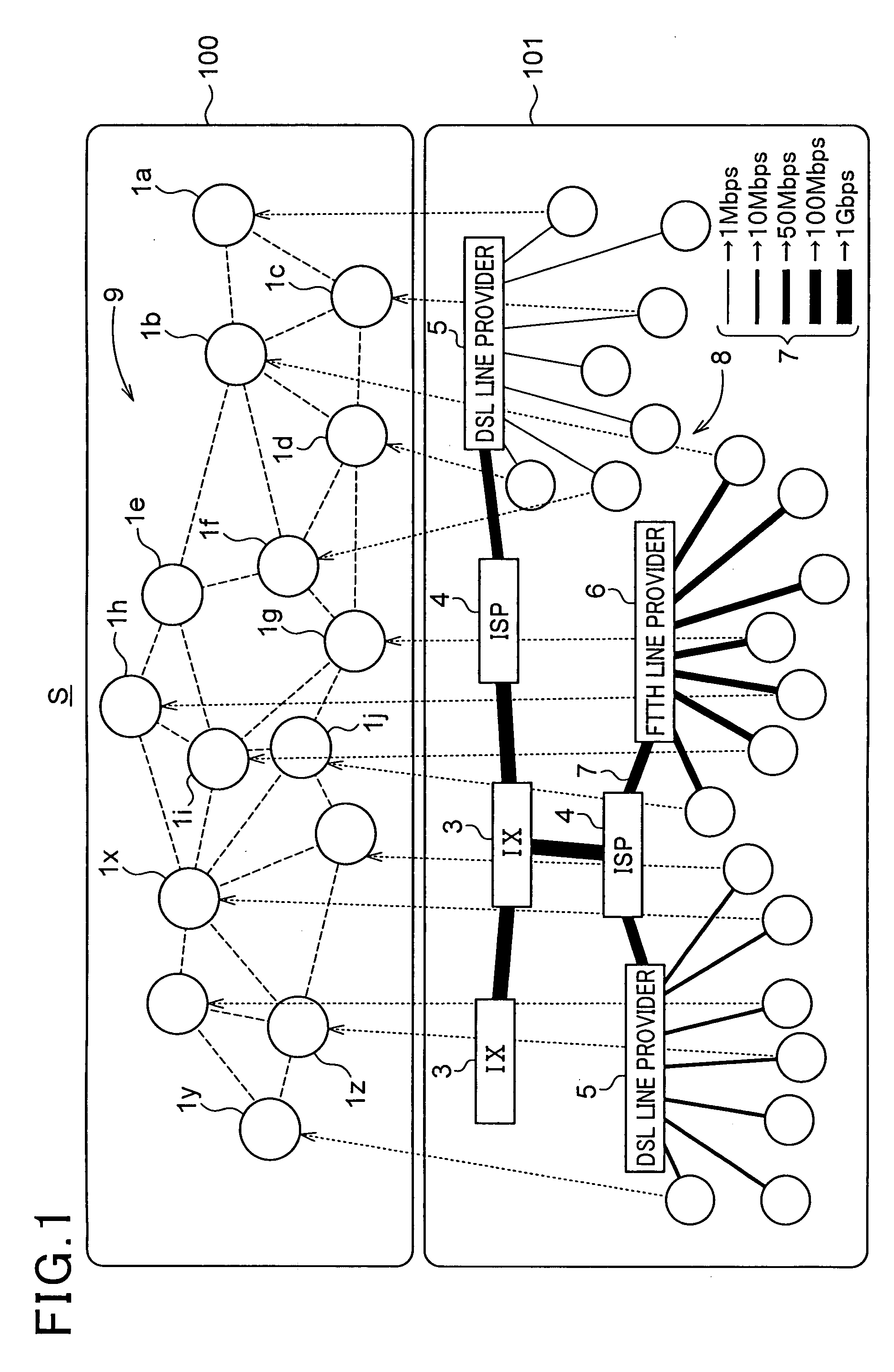
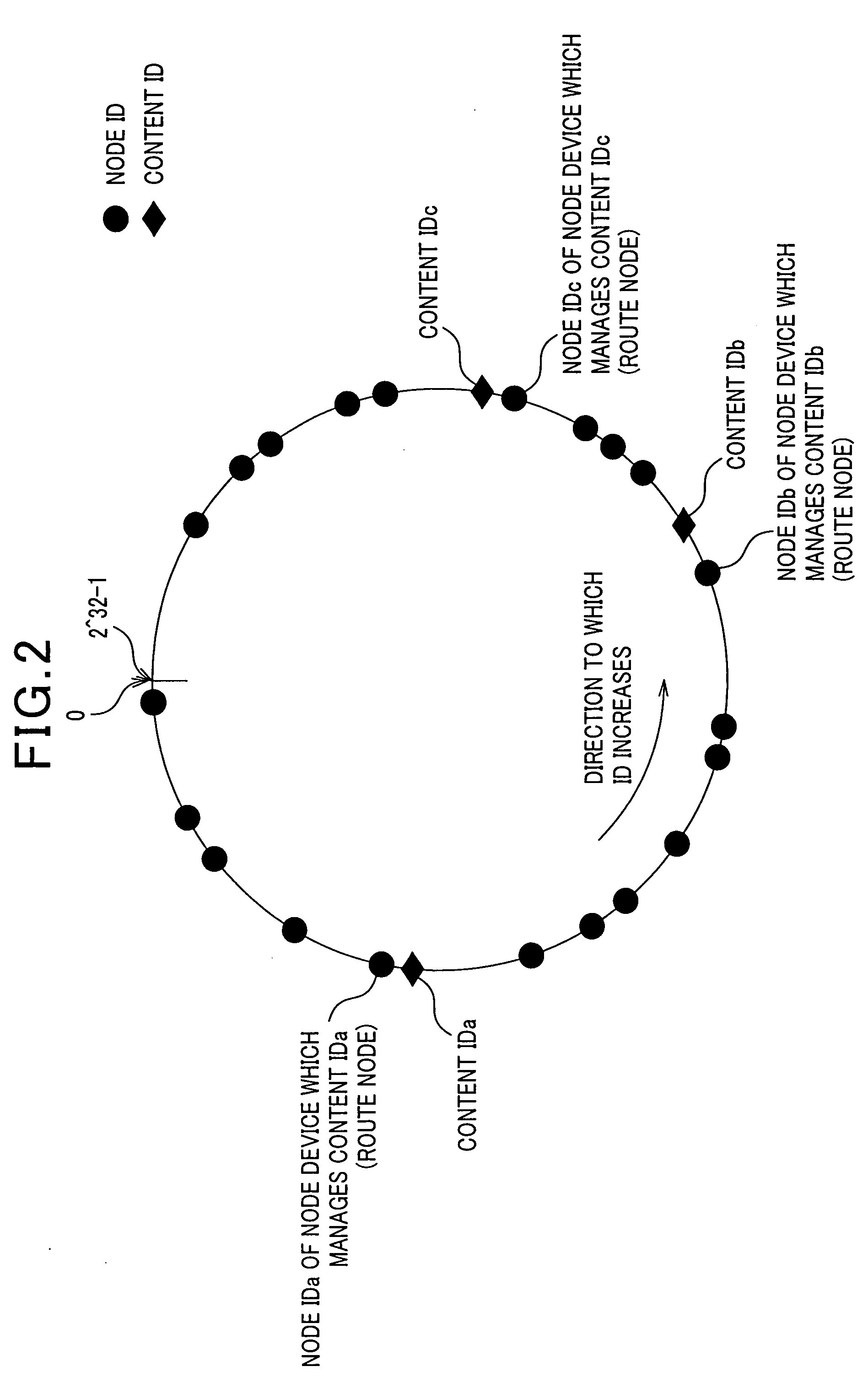
Information delivery system, delivery request program, transfer program, delivery program, and the like
InactiveUS20070283043A1Digital data processing detailsMultiple digital computer combinationsRelevant informationPublic information
A first node device transmits to a second node device unique identification information corresponding to specific common information, receives from the information saving node device the relevant information regarding the information saving node device, and requests to a selected information saving node device delivery of the specific common information, the second node device searches the node information and, in a case where there is node information, transfers the identification information to the information saving node device, which is indicated by node information, and the information saving node device, in a case where the transmission of the specific common information indicated by the identification information is available, transmits to the first node device the relevant information regarding the information saving node device, and, in a case where delivery request for the specific common information is received from the first node device, delivers specific common information.
Owner:BROTHER KOGYO KK +1
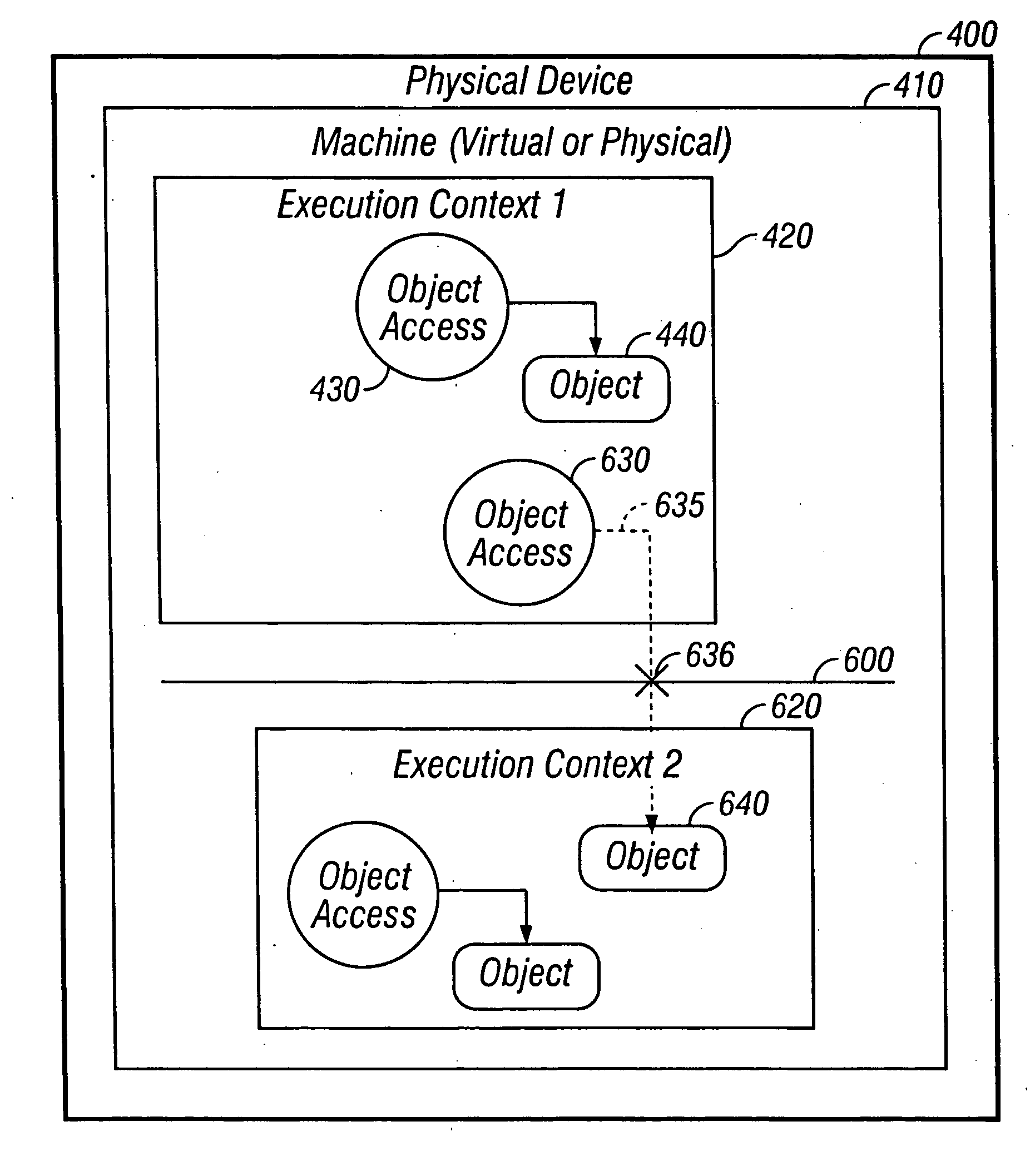
Techniques for permitting access across a context barrier on a small footprint device using an entry point object
InactiveUS20050193218A1Specific access rightsDigital data processing detailsSmall footprintSecurity check
A small footprint device can securely run multiple programs from unrelated vendors by the inclusion of a context barrier isolating the execution of the programs. The context barrier performs security checks to see that principal and object are within the same namespace or memory space and to see that a requested action is appropriate for an object to be operated upon. Each program or set of programs runs in a separate context. Access from one program to another program across the context barrier can be achieved under controlled circumstances by using an entry point object. The entry point object can either perform accesses across the context barrier on behalf of a requesting program or can pass the request to the program to be accessed and switch contexts to the program to be accessed.
Owner:ORACLE INT CORP
Method and Apparatus for Improving Interaction between Scheduling Request Procedure and Random Access Procedure
ActiveUS20100080184A1Enhanced interactionAssess restrictionWireless commuication servicesCommunications systemUplink transmission
The present invention provides a method for improving interaction between a Scheduling Request procedure and a Random Access procedure in a user equipment (UE) of a wireless communication system. The method includes steps of triggering a Scheduling Request procedure; repeatedly sending a Dedicated Scheduling Request (D-SR) message on a Physical Uplink Control Channel (PUCCH) until an uplink transmission resource for a new transmission is received or the number of D-SR transmissions reaches to a specific value when the PUCCH is configured for the UE; and deactivating all pre-configured transmission resources before performing a Random Access procedure corresponding to the Scheduling Request procedure when the number of D-SR transmissions reaches to the specific value.
Owner:INNOVATIVE SONIC
Apparatus, method and computer program product providing simultaneous radio resource and service requests
ActiveUS20070041343A1Network traffic/resource managementConnection managementRequest procedureRadio resource
A method includes, at a user equipment, combining a message requesting the radio resource connection and a message requesting at least one service into a single message. The single message is transmitted from the user equipment to a network element in a wireless network. Another method includes receiving, from a user equipment, a single message including both a message requesting a radio resource connection and a message requesting at least one service. In response to the message requesting radio resource connection, performing radio resource control connection establishment for the user equipment in order to establish the radio resource control connection between the user equipment and at least one of a plurality of network elements of a wireless network. In response to the message requesting at least one service, performing service request procedures for the user equipment, wherein at least part of the radio resource control connection establishment and at least part of the service request procedures are performed in parallel.
Owner:CONVERSANT WIRELESS LICENSING LTD
Method and system for providing PTT to conference
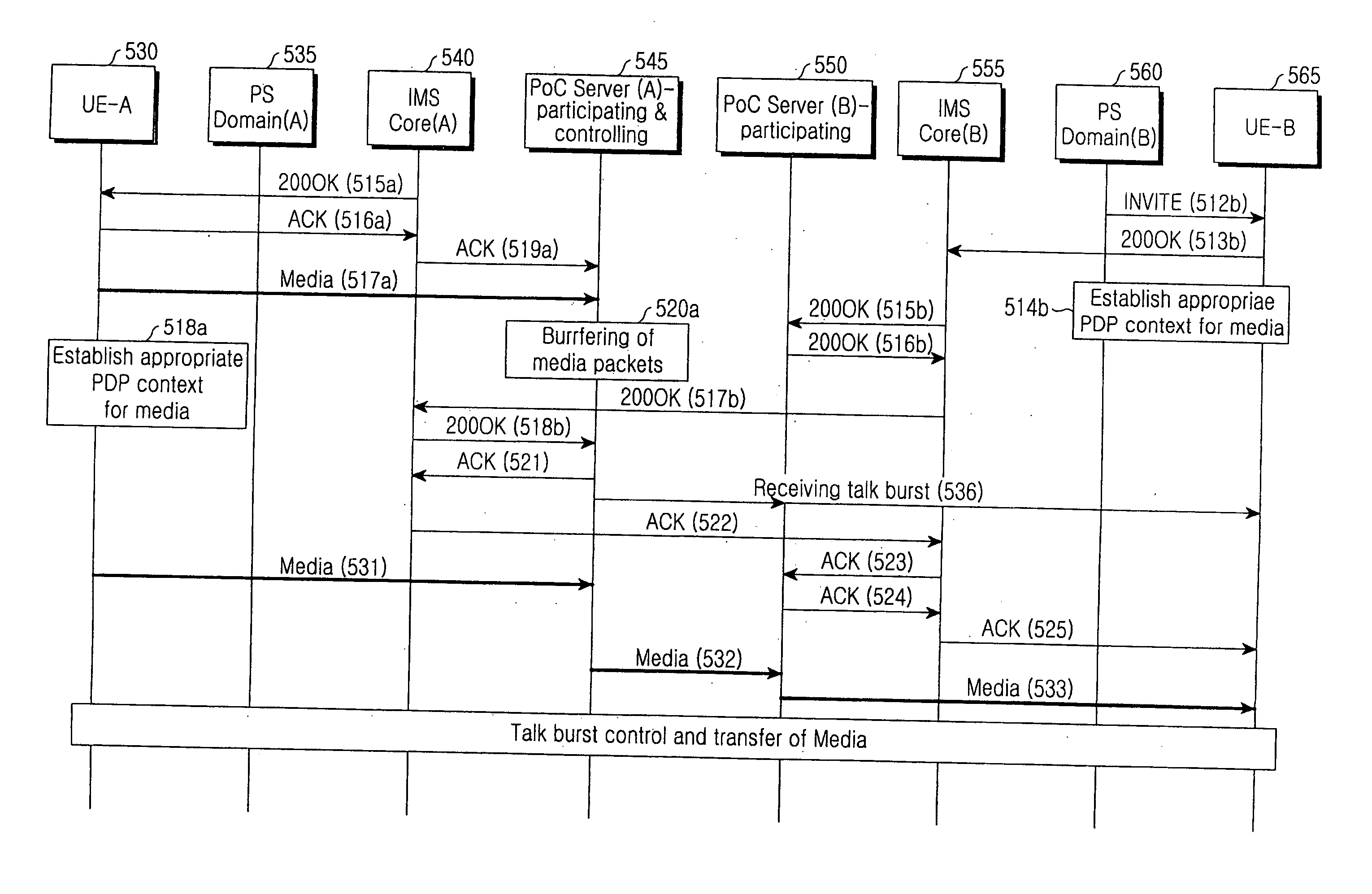
InactiveUS20070002779A1Multiplex system selection arrangementsSpecial service provision for substationPush-to-talkRequest procedure
A method for providing push-to-talk (PTT) so as to conference between a plurality of user equipments (UEs) serving as clients in a mobile communication network including a PTT over cellular (PoC) server, a conference server, and a mixer for mixing for the conference. The method comprises performing a request procedure for switching over to the conference during a PoC session between the UEs; performing a conference client invitation or participation procedure for opening a conference session through the conference server; and performing a procedure for releasing the conference session between the PoC server and the UEs. The method can switch over to a conference service during a PTT service without newly initializing the conference service after completing an old PoC session, and can also switch over to bidirectional communication between all or some of the participants during a PoC session which is using unidirectional communications.
Owner:SAMSUNG ELECTRONICS CO LTD
Method for transmitting data according to dynamic resource request
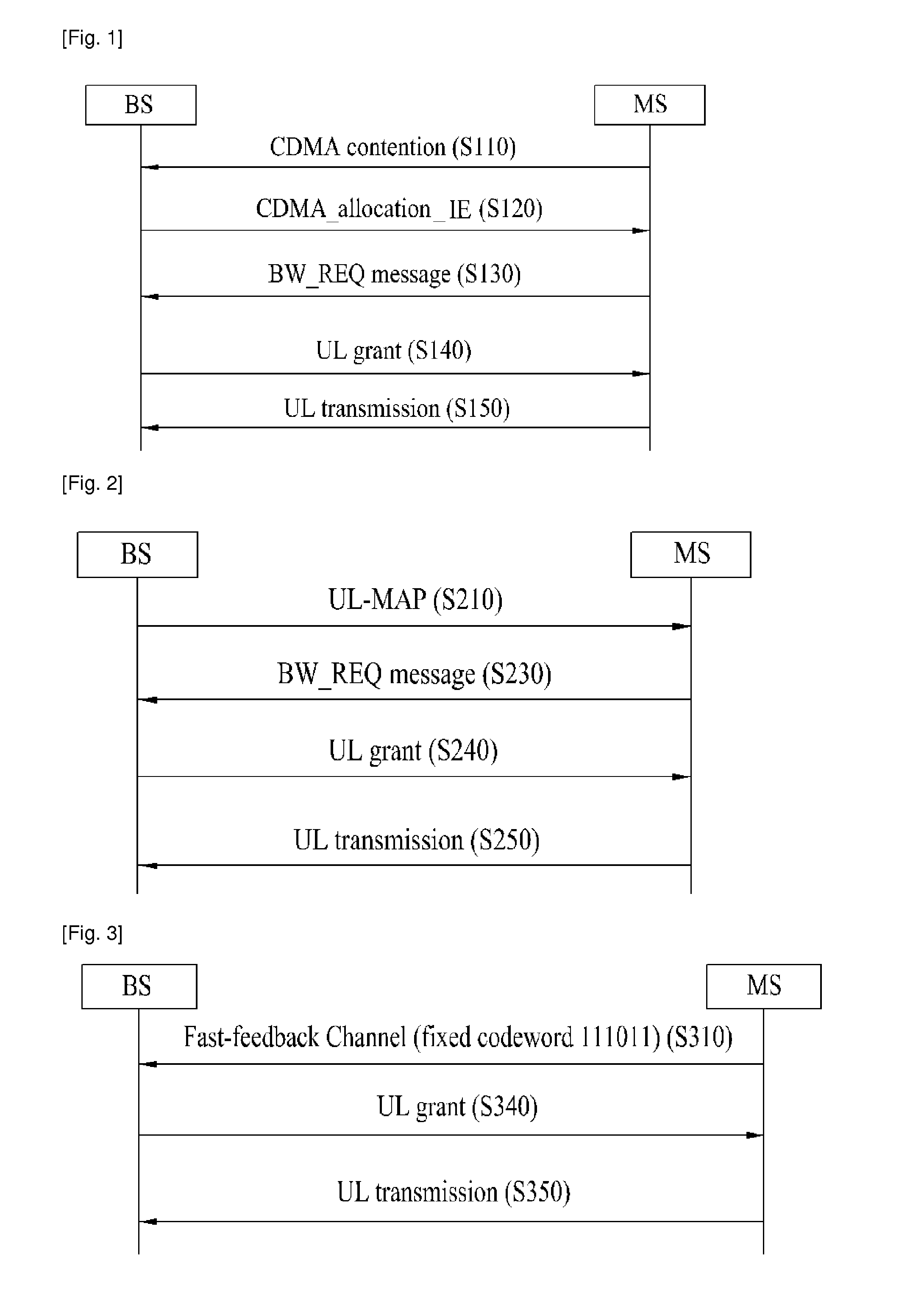
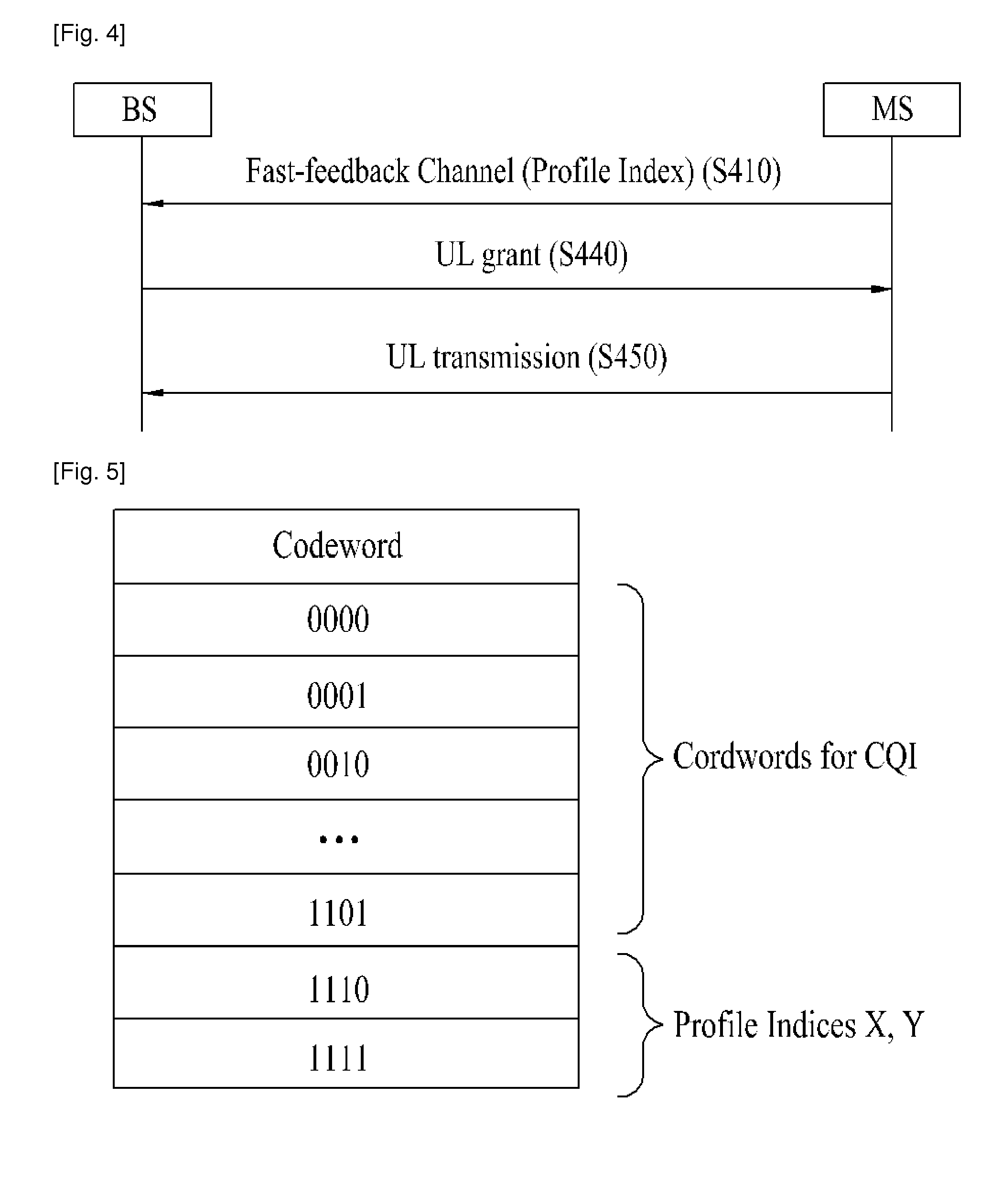
InactiveUS20110075628A1Satisfy quality of serviceReduce message overheadNetwork traffic/resource managementSignalling characterisationQuality of servicePhase shifted
A method for transmitting uplink data according to a dynamic resource request is disclosed. The method includes confirming, at a mobile station, whether a service type for a bandwidth request is sensitive to delay, if the service type is not sensitive to delay, shifting a phase of a fast feedback channel and transmitting the phase-shifted fast feedback channel, if the service type is sensitive to delay or if a bandwidth request grant message corresponding to the phase-shifted fast feedback channel is received from a base station, transmitting a bandwidth request information corresponding to the service type to the base station, and upon receiving an uplink grant message for an uplink resource according to the bandwidth request information from the base station, transmitting data though the uplink resource. As a result, collision does not occur during a resource request, quality of service (QoS) of a real-time traffic sensitive to delay can be satisfied, an uplink allocation request procedure is dynamically changed according to a service type, thus reducing message overhead, and a resource can be efficiently used according to a characteristic of a service provided to the mobile station.
Owner:LG ELECTRONICS INC
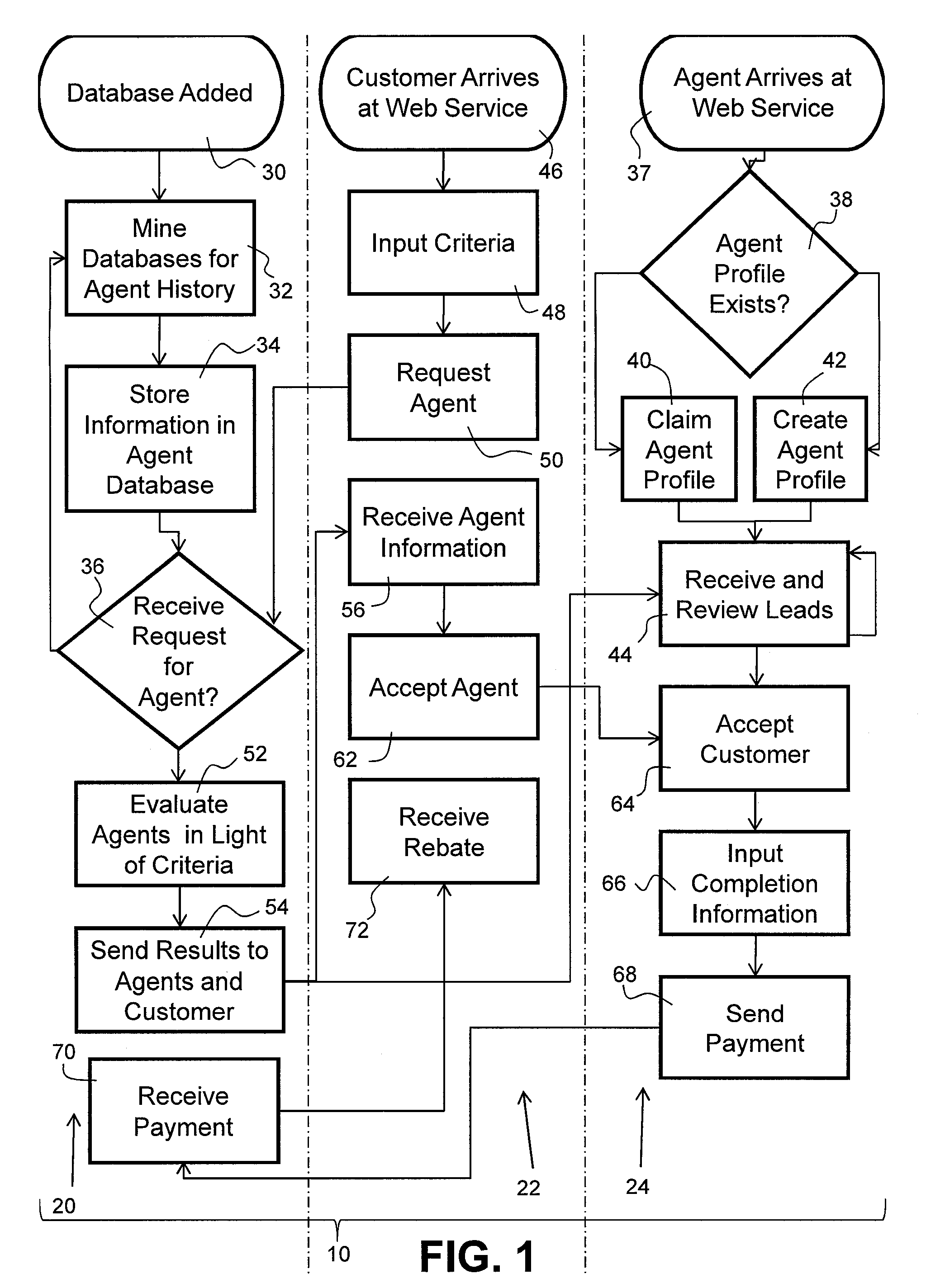
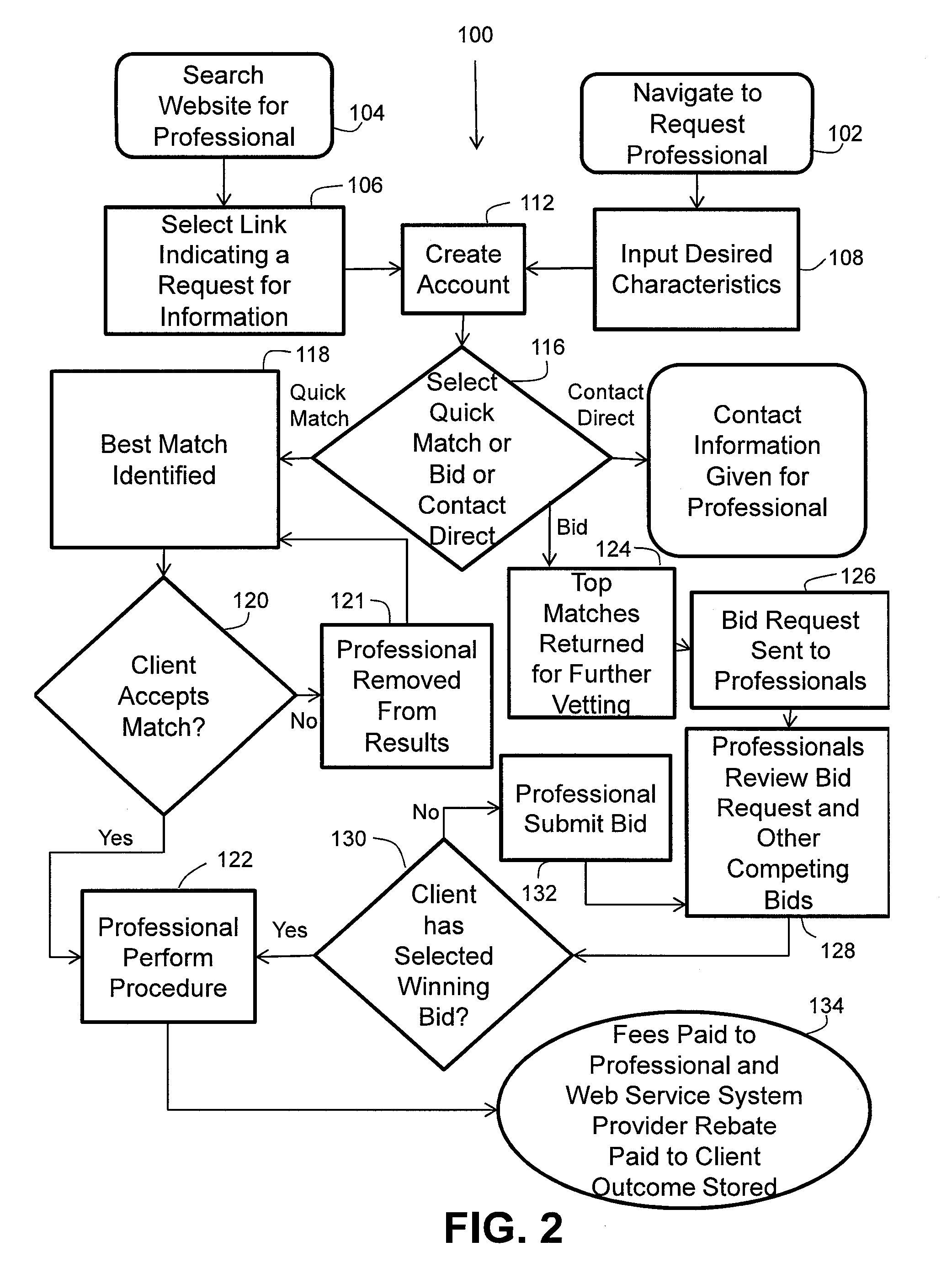
System for Matching Procedure Characteristics to Professional Experience
InactiveUS20110060737A1Digital data processing detailsMultiple digital computer combinationsWeb serviceRequest procedure
A web service system dynamically matches professional experience with procedure characteristics submitted by a client through evaluating a professional's history of procedure outcomes in light of the requested procedure characteristics.
Owner:BATEMAN IP LAW GRP
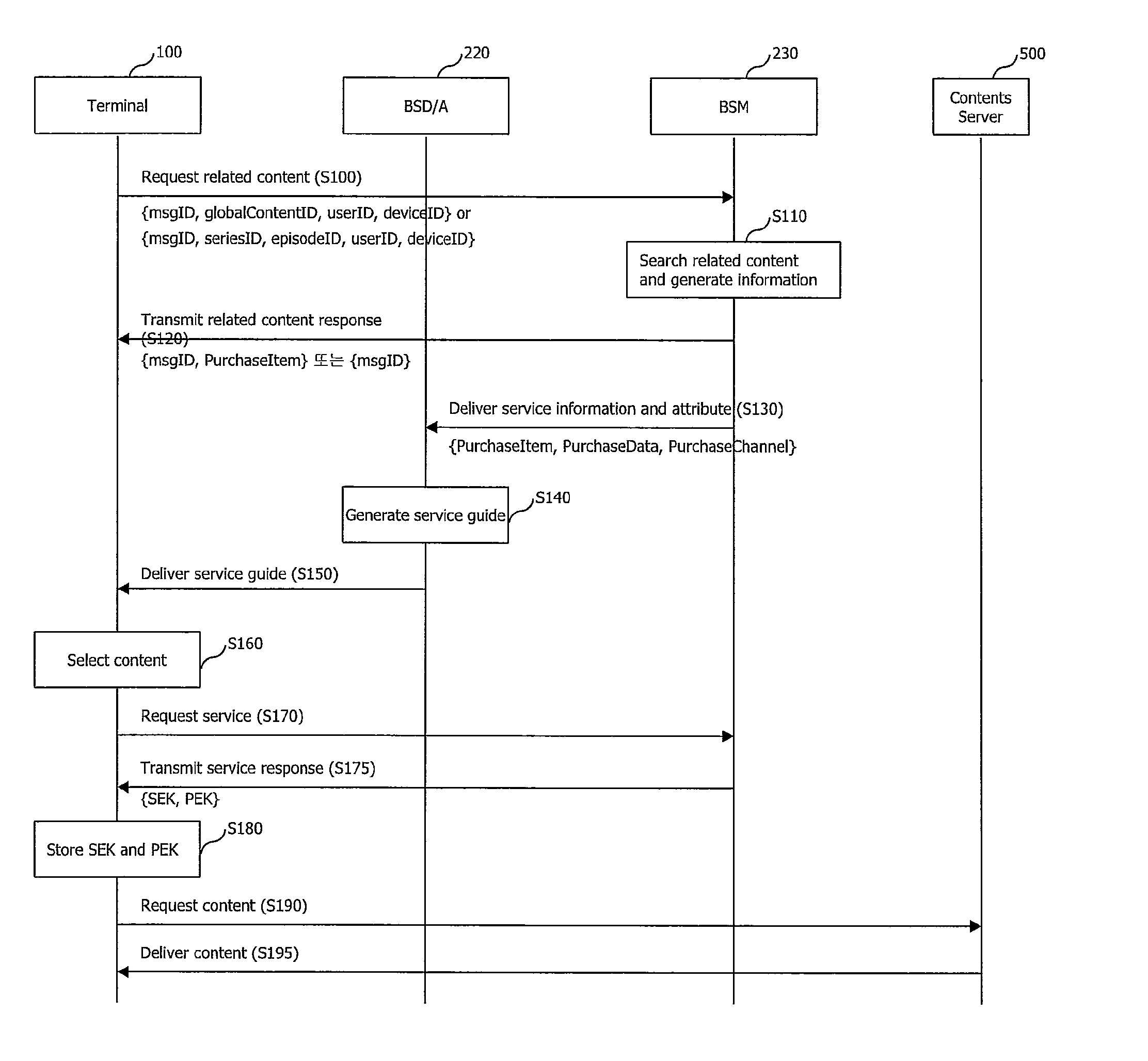
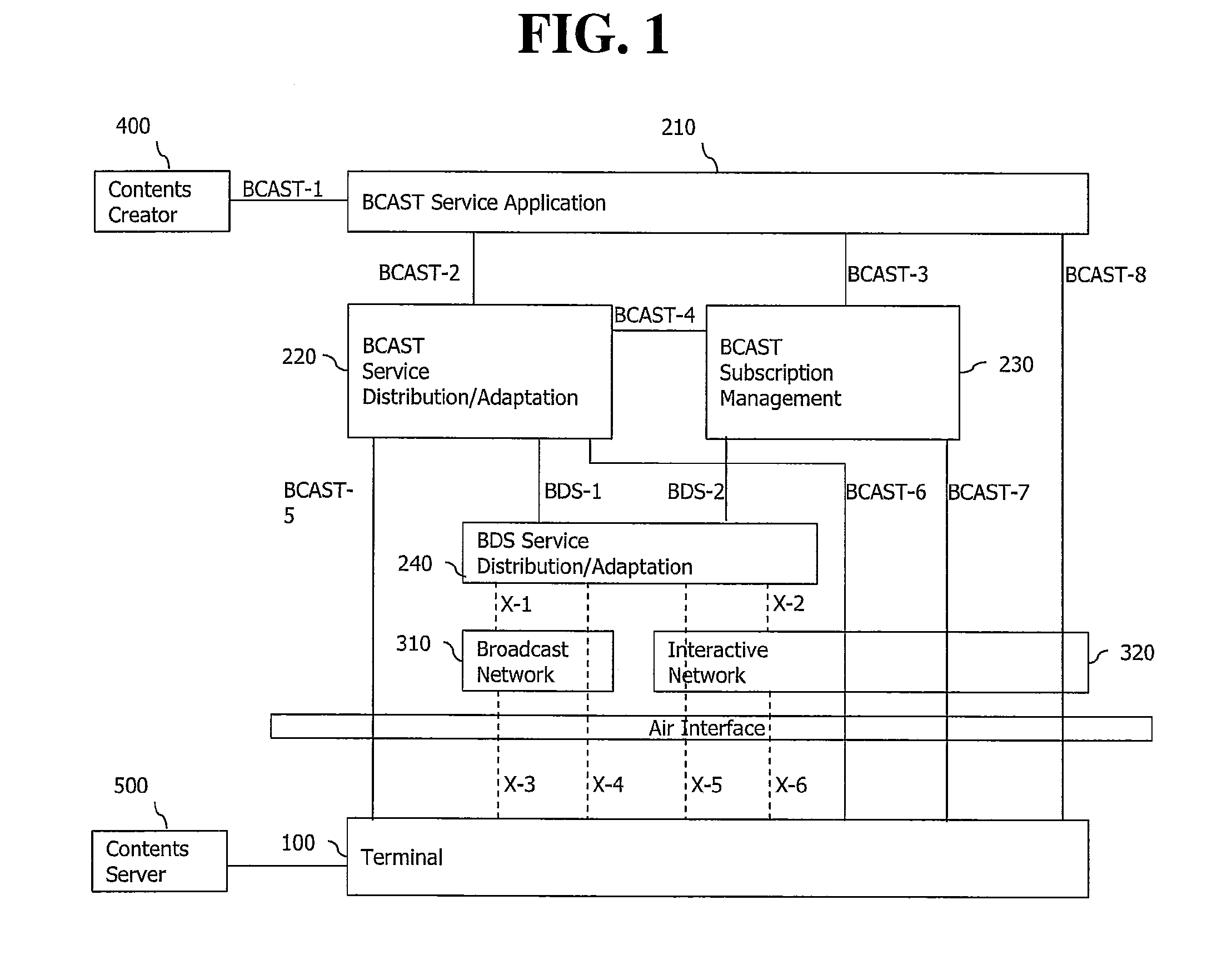
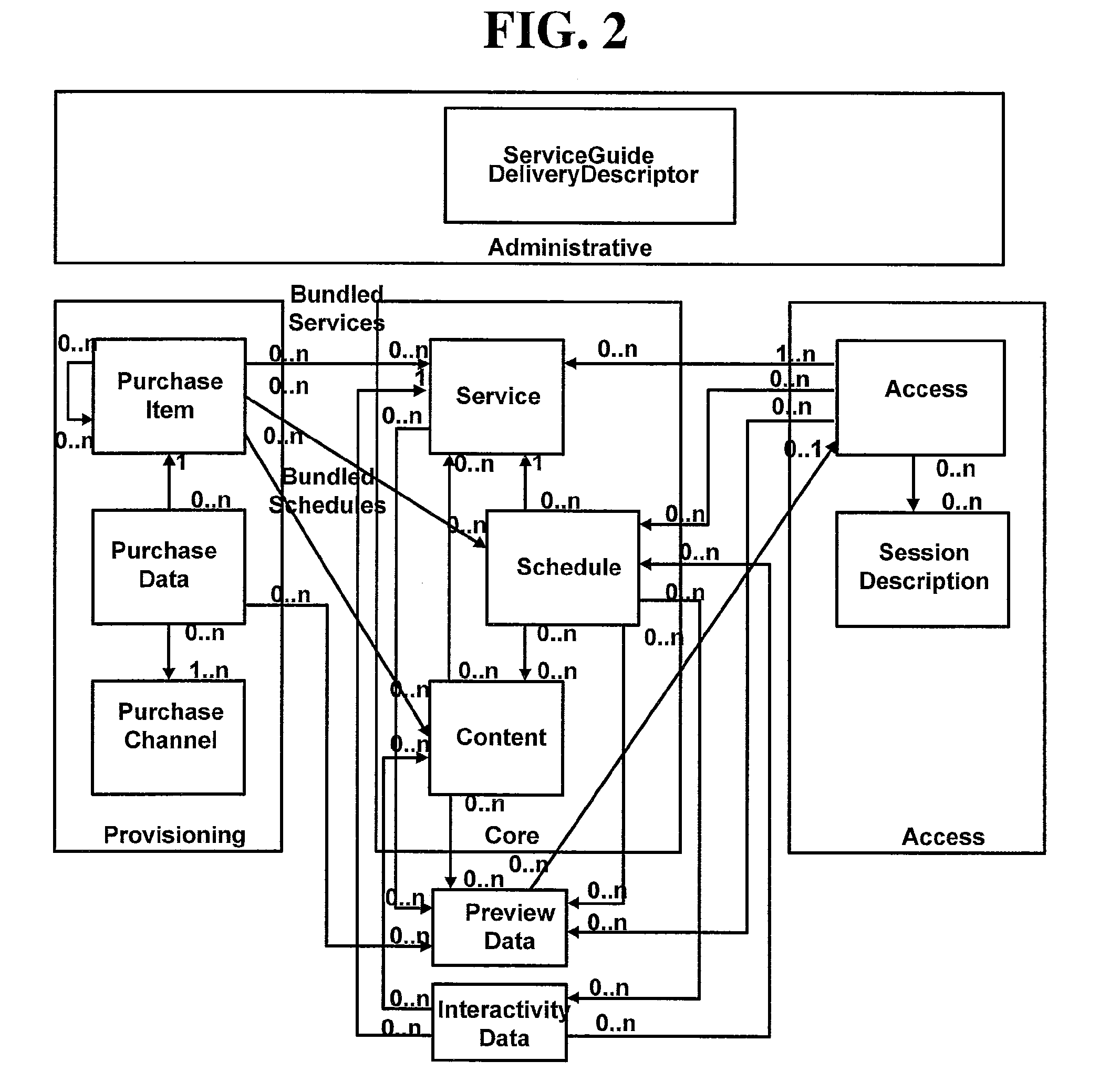
Method and apparatus for searching and downloading related contents by terminal through broadcast service
InactiveUS20110055867A1Simple processNetwork be preventedTelevision system detailsColor television detailsContent IdentifierRequest procedure
A method and apparatus for receiving information regarding content related to particular content interested by a user and downloading the related contents in a terminal are disclosed. The method for receiving content related to a particular content, includes: transmitting a content request message including a content identifier of a particular content to a server; receiving a content response message including information regarding content related to the content identifier from the server, wherein if there are at least one or more contents related to a global content identifier, the global state code has a value indicating success; checking whether there exists second information in guide information referred to by the first information on the related contents; receiving the second information if there is not the second information; and initiating a service request procedure by using the referred reception information.
Owner:LG ELECTRONICS INC
Improved scheduling request procedure
ActiveUS20180014322A1Accelerated programAvoid the needPower managementNetwork traffic/resource managementDuration periodCommunications system
The invention relates to a method for requesting uplink resources by a user equipment in a communication system, wherein a DRX, Discontinued Reception, function is running at the user equipment. The transmission of a scheduling request for requesting uplink resources to a radio base station is triggered upon triggering of a buffer status report in the user equipment. However, the triggering of the scheduling request is delayed such that the scheduling request is triggered in one of the subframes—preferably the first subframe—of an On-Duration period of a DRX cycle according to the DRX function. Correspondingly, the triggered scheduling request is transmitted to the radio base station in the next possible scheduling request transmission occasion after the triggering of the scheduling request is delayed.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
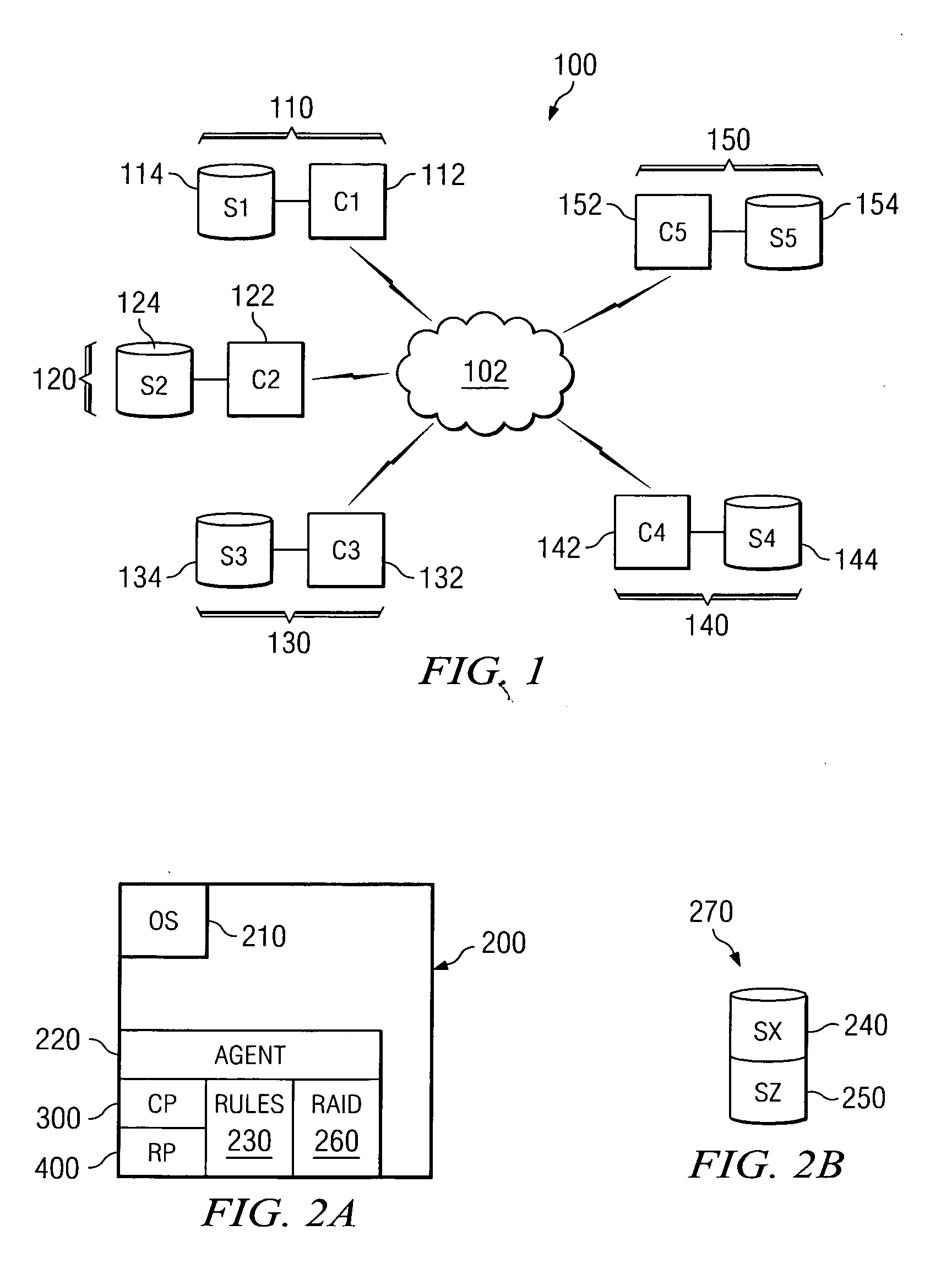
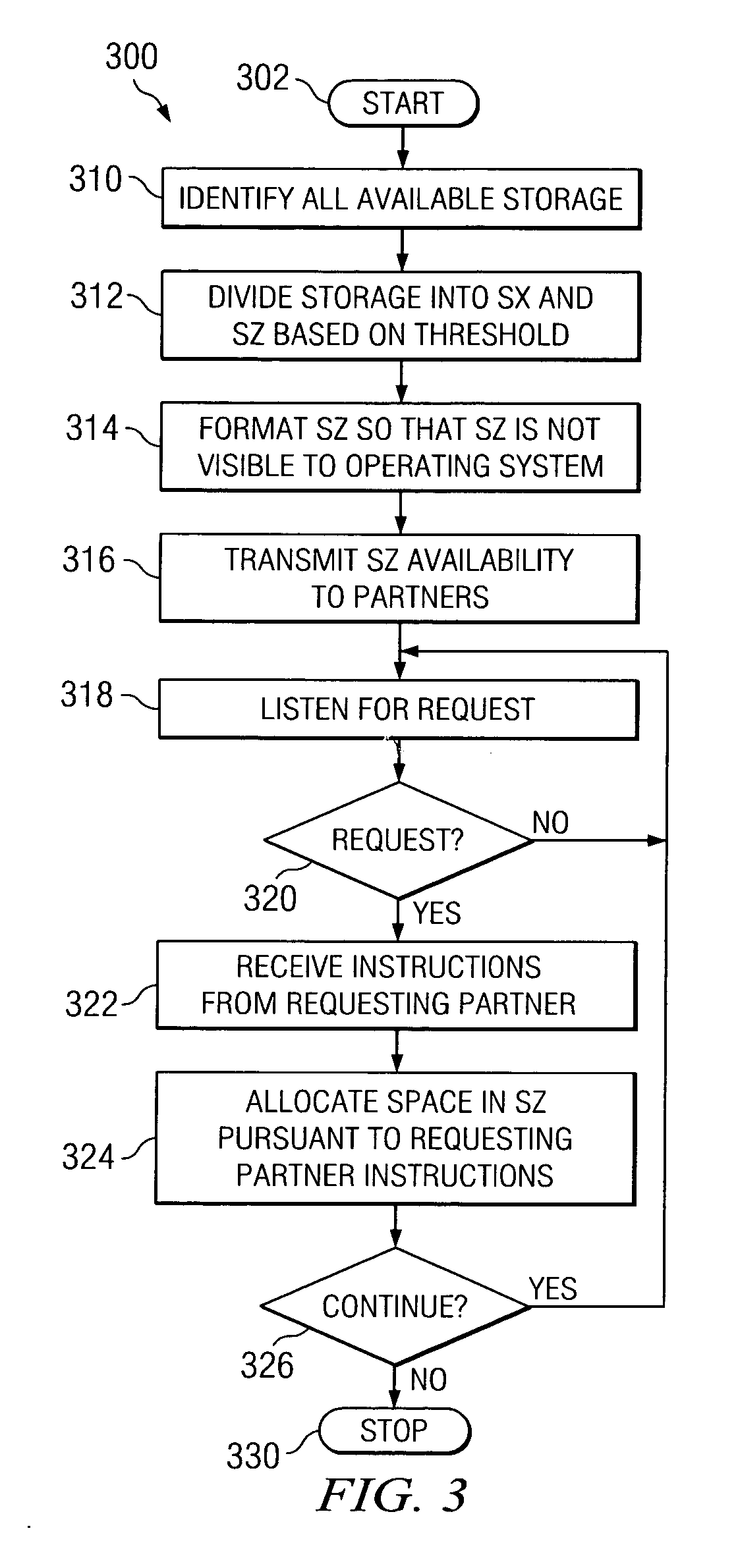
System and method for an on-demand peer-to-peer storage virtualization infrastructure
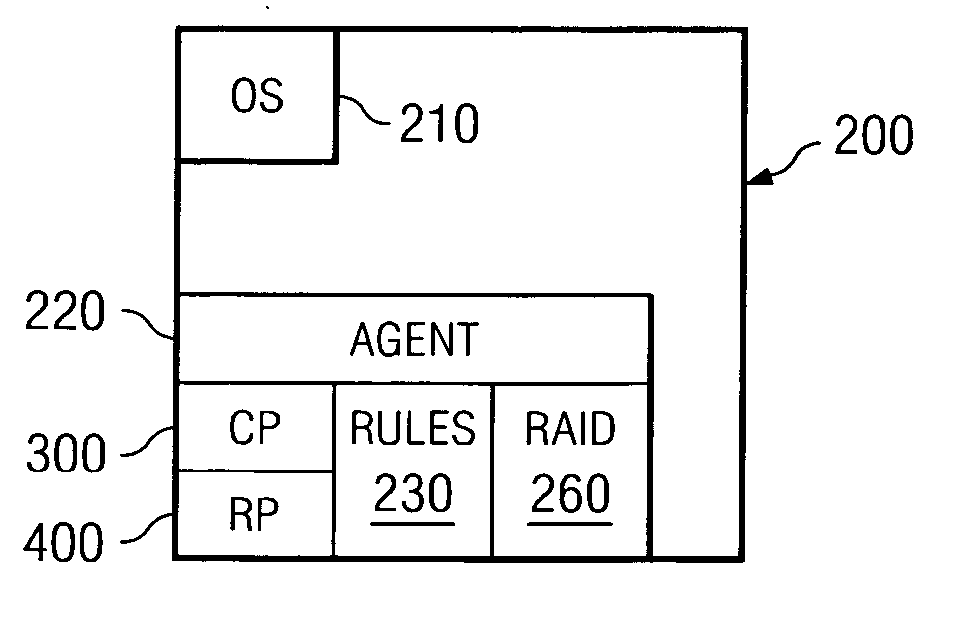
A system and method for creating an on-demand virtual drive from dedicated storage on a plurality of partners in a peer-to-peer network using an agent installed on each of the partners. The agent has a contributing program and a requesting program. The contributing program creates a first storage unit and a second storage unit, formatting the second storage unit so that it is not visible to the operating system of the partner and transmitting the size of the second storage unit to the other partners. The requesting partner creates a virtual drive using space on selected partner's second drives, and directs data blocks in and out of the virtual drive. A rules engine incorporating RAID algorithms governs the selection of the partners and allocation of available space.
Owner:IBM CORP
Method and arrangement in a telecommunication system
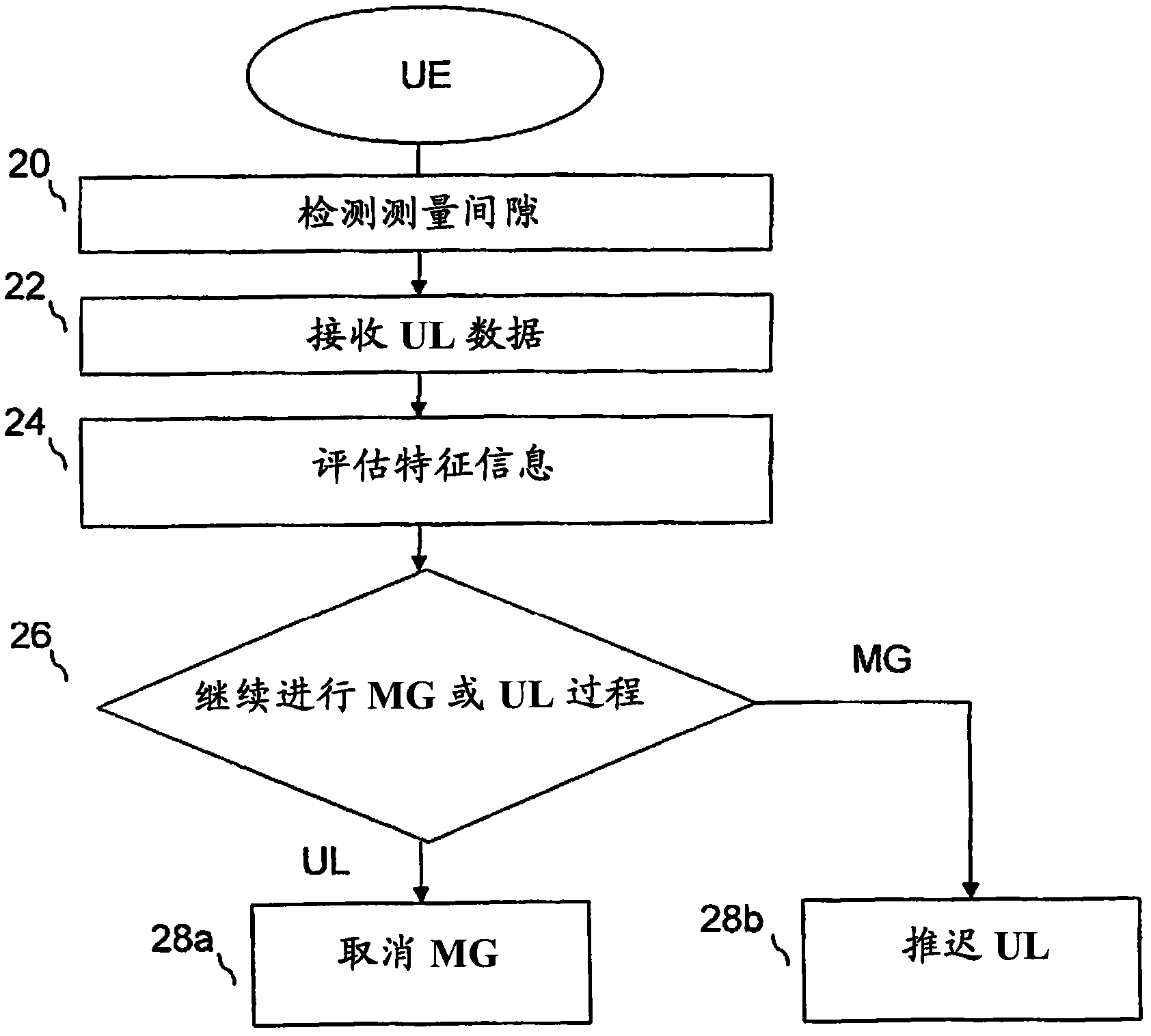
InactiveCN102084682AMinimized transmission delayEasy to measureWireless communicationRequest procedureData transmission
The present invention comprises a method and an arrangement for priority handling between a measurement gap procedure and an uplink data transmission procedure in an evolved UTRAN. The user equipment (UE) detects an active measurement gap. When the UE receives data into the transmission buffer the received data triggers an uplink data transmission procedure such as a scheduling request procedure or a random access procedure. An evaluation on characteristics information associated with the received data is performed and based on the performed evaluation the UE proceeds with the uplink data transmission procedure or the measurement gap procedure. In case the characteristics information associated with the received data is of high priority, the UE proceeds with the uplink data transmission procedure and cancels the measurement gap procedure. However, if the characteristics information associated with the received data is of low priority, it proceeds with the measurement gap procedure and postpones the uplink data transmission procedure to a later occasion.
Owner:IDTP HLDG
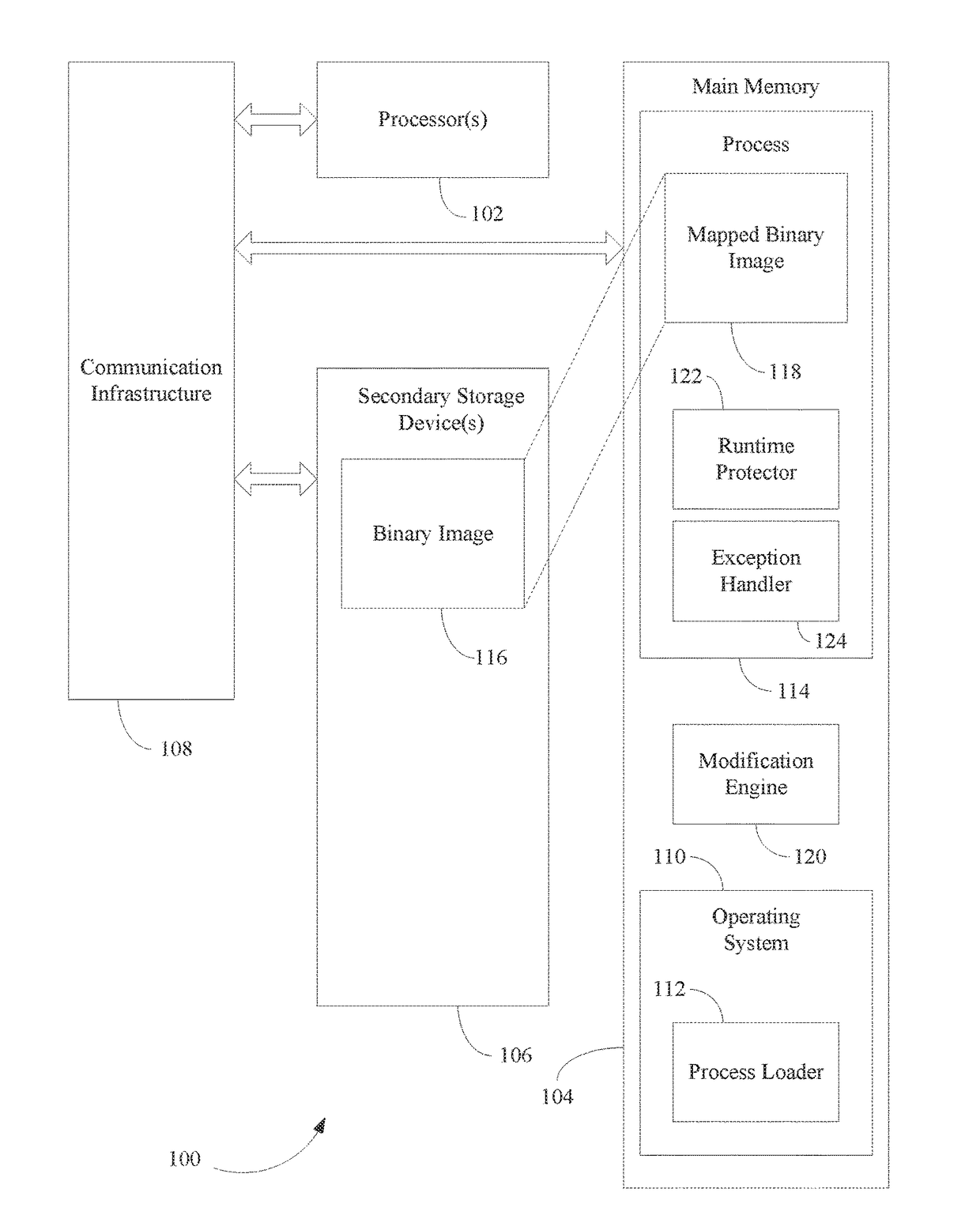
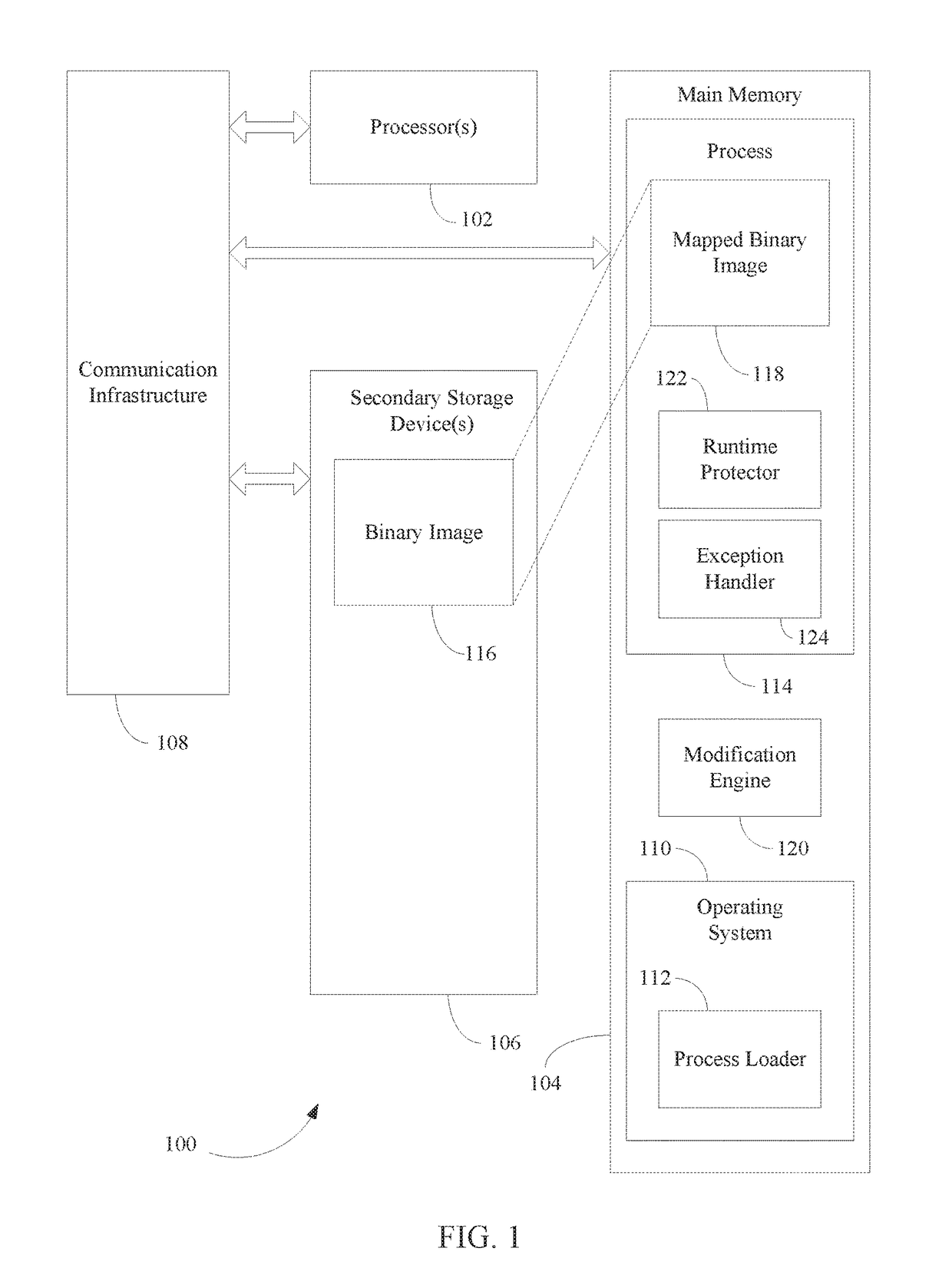
Malicious code protection for computer systems based on process modification
Various approaches are described herein for, among other things, detecting and / or neutralizing attacks by malicious code. For example, instance(s) of a protected process are modified upon loading by injecting a runtime protector that creates a copy of each of the process' imported libraries and maps the copy into a random address inside the process' address space to form a “randomized” shadow library. The libraries loaded at the original address are modified into a stub library. Shadow and stub libraries are also created for libraries that are loaded after the process creation is finalized. Consequently, when malicious code attempts to retrieve the address of a given procedure, it receives the address of the stub procedure, thereby neutralizing the malicious code. When the original program's code (e.g., the non-malicious code) attempts to retrieve the address of a procedure, it receives the correct address of the requested procedure (located in the shadow library).
Owner:MORPHISEC INFORMATION SECURITY 2014
Method and mobile terminal providing priority-based uplink scheduling information
Provided are a method and a mobile terminal for providing uplink scheduling information to a scheduler in a wireless telecommunication system. When a logical channel having data available to transmit triggers a buffer status report, the mobile terminal determines whether a priority level associated with the logical channel exceeds a predefined threshold. If so, the mobile terminal performs a scheduling request procedure with the scheduler. If not, the mobile terminal delays the scheduling request procedure until a predefined timing event has occurred. The predefined timing event may be at least one of expiration of a timer, a radio bearer associated with the logical channel becoming active, and if the scheduling request procedure is being performed using a contention-based random access, contention resolution succeeding for the mobile terminal.
Owner:BLACKBERRY LTD
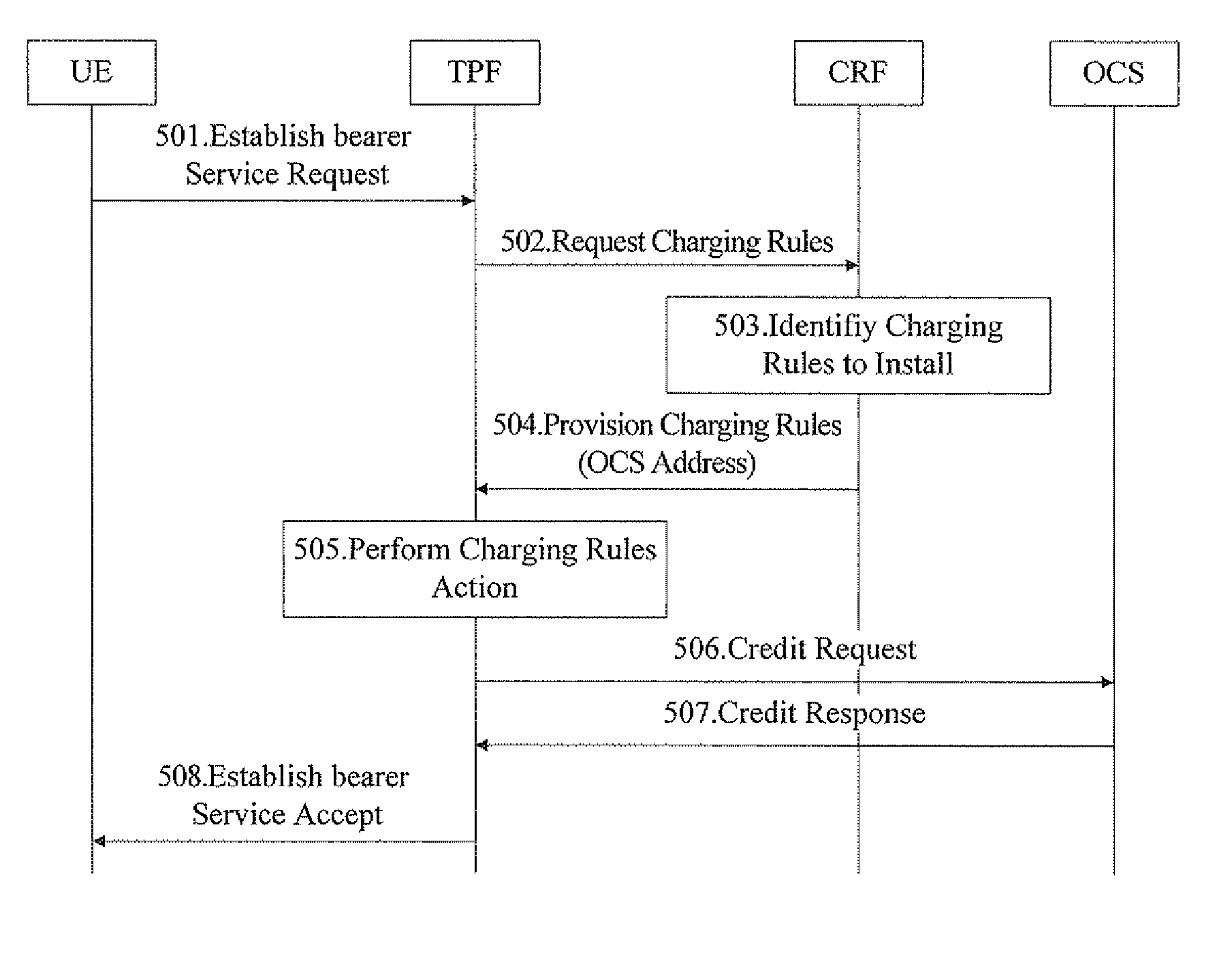
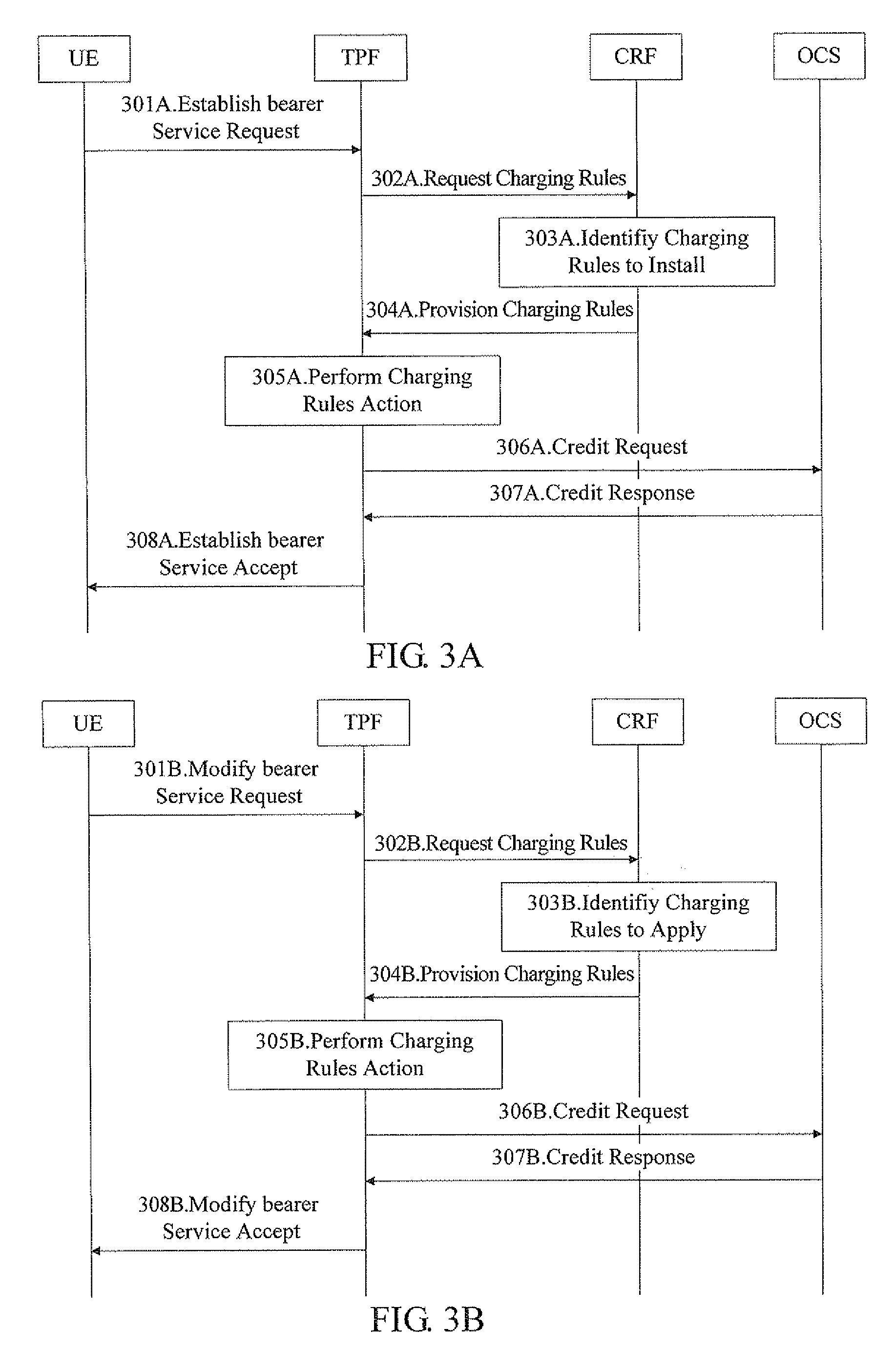
Method for Improving Service Data Flow Based Charging and System Thereof
ActiveUS20070124160A1Speed up the flowMetering/charging/biilling arrangementsAccounting/billing servicesComputer networkData stream
A method for improving service data flow based charging and a system thereof are disclosed, A CRF may determine, according to input information provided by an AF or TPF, that the charging method for the current data flow service is an online or offline charging method, and provide the TPF with the charging rules with the corresponding mechanism. Moreover, the CRF may provide the TPF with the address information of an OCS or OFCS corresponding to the UE, to enable the TPF to address the corresponding OCS according to the address information of the OCS and trigger the following credit request procedure for the UE, or enable the TPF to address the corresponding OFCS according to address information of the OFCS and send collected charging data information of the UE to the OFCS. Therefore the charging procedure based on the FBC mechanism is more complete and more reasonable.
Owner:HUAWEI TECH CO LTD
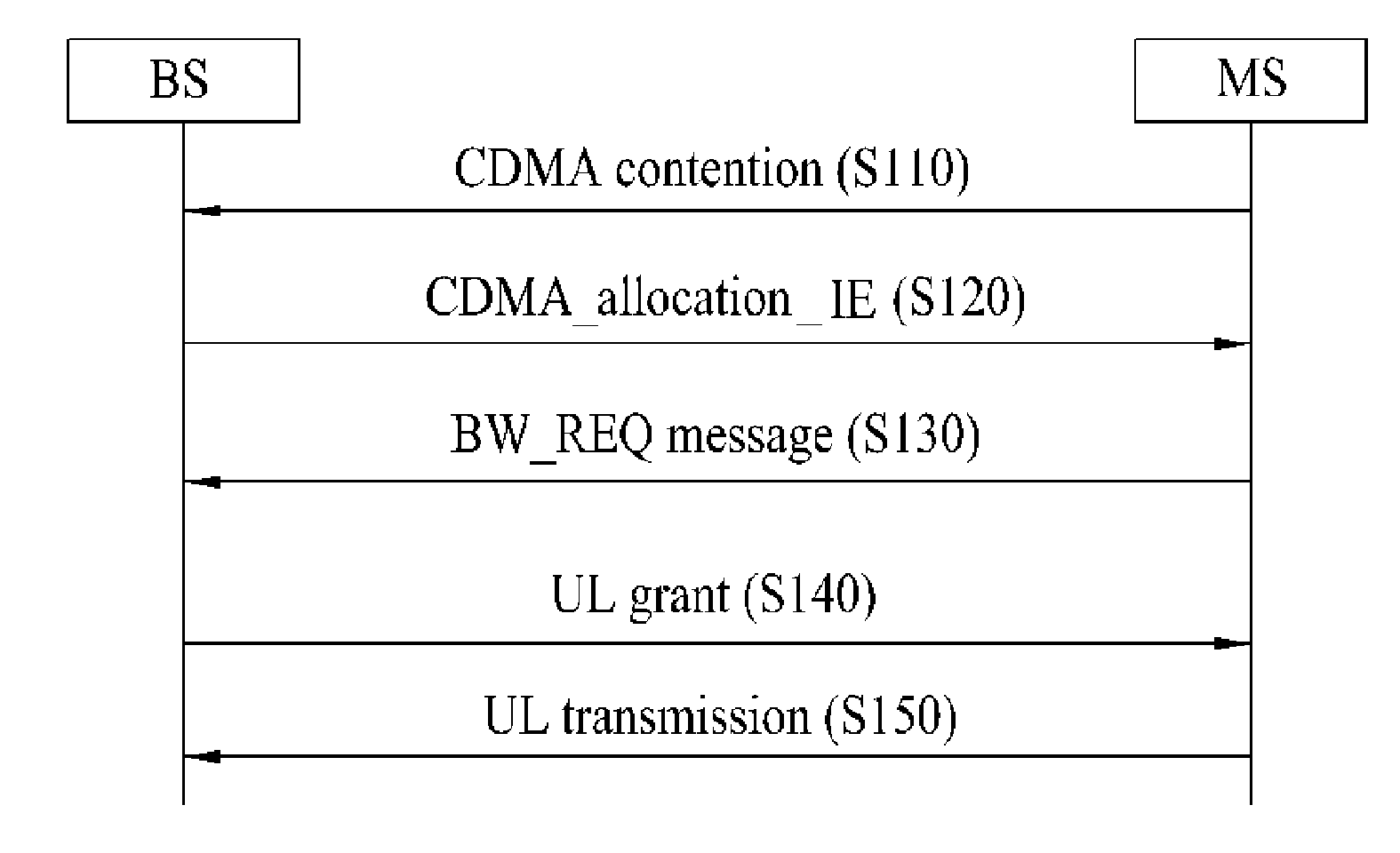
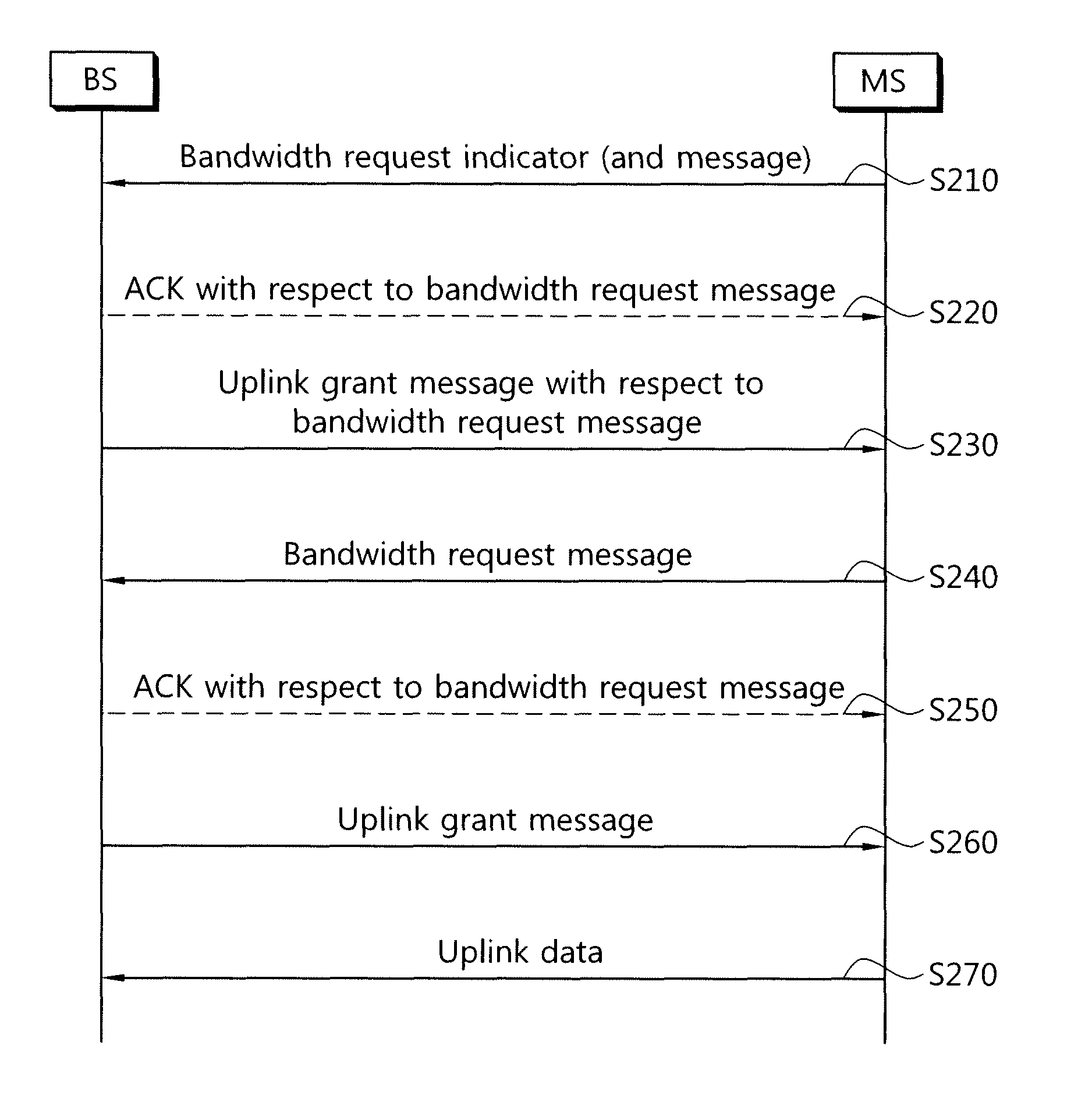
Method for performing bandwidth request process in wireless communication system
InactiveUS8553634B2Efficient executionPerformed quickly and effectivelyTransmission path divisionSignal allocationCommunications systemRequest procedure
A bandwidth request procedure is performed in a wireless communication system by transmitting a bandwidth request indicator and a bandwidth request message through a bandwidth request channel; receiving an uplink grant message indicating uplink radio resource in response to the bandwidth request indicator and the bandwidth request message; and transmitting uplink data after receiving the uplink grant message, wherein the uplink grant message includes information regarding the type of the uplink grant message.
Owner:LG ELECTRONICS INC
Semi-reliable arq method and device thereof
InactiveUS20050201378A1Degree of delayDelay can be acceptedError prevention/detection by using return channelTransmission systemsExchange protocolRequest procedure
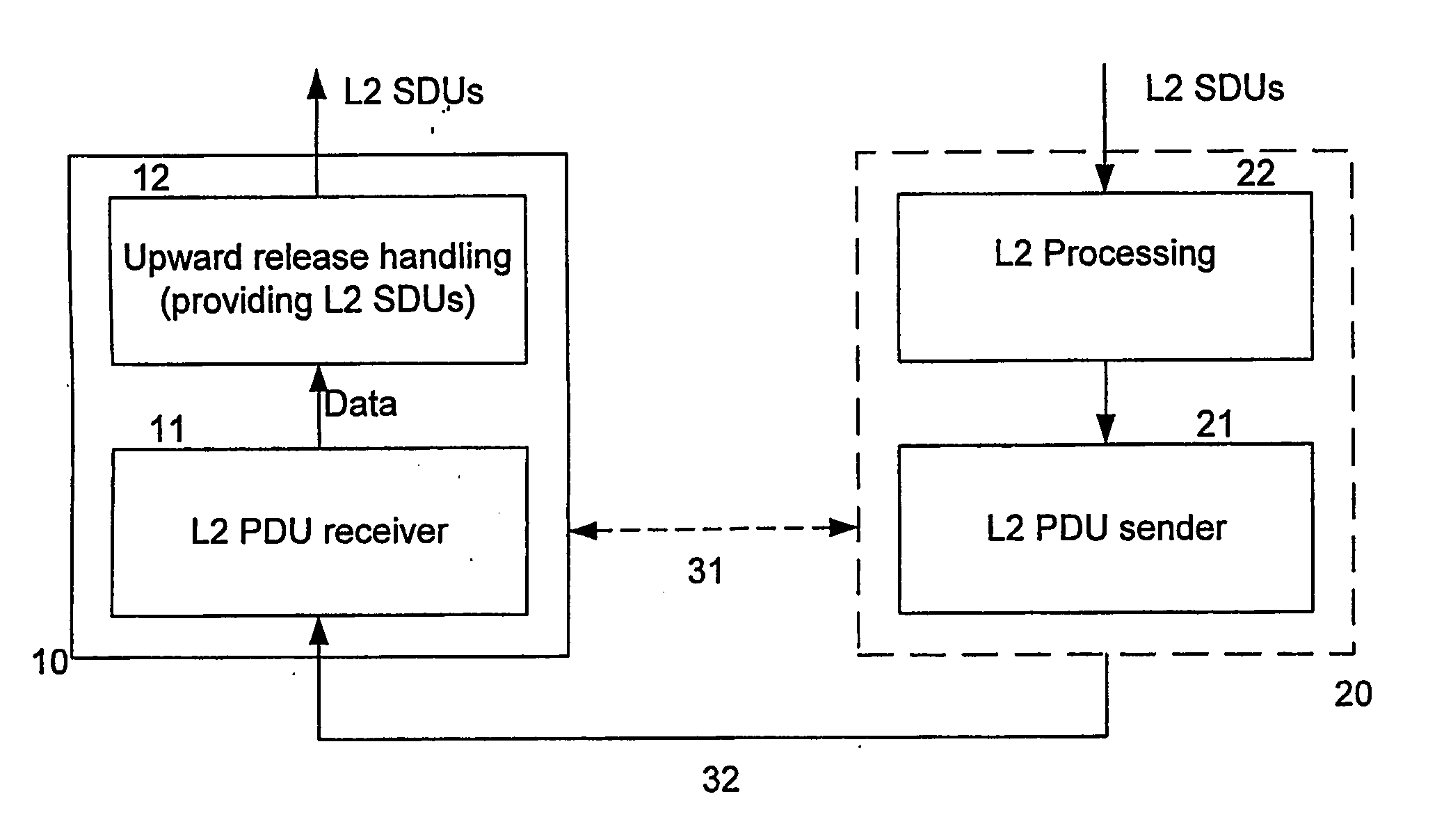
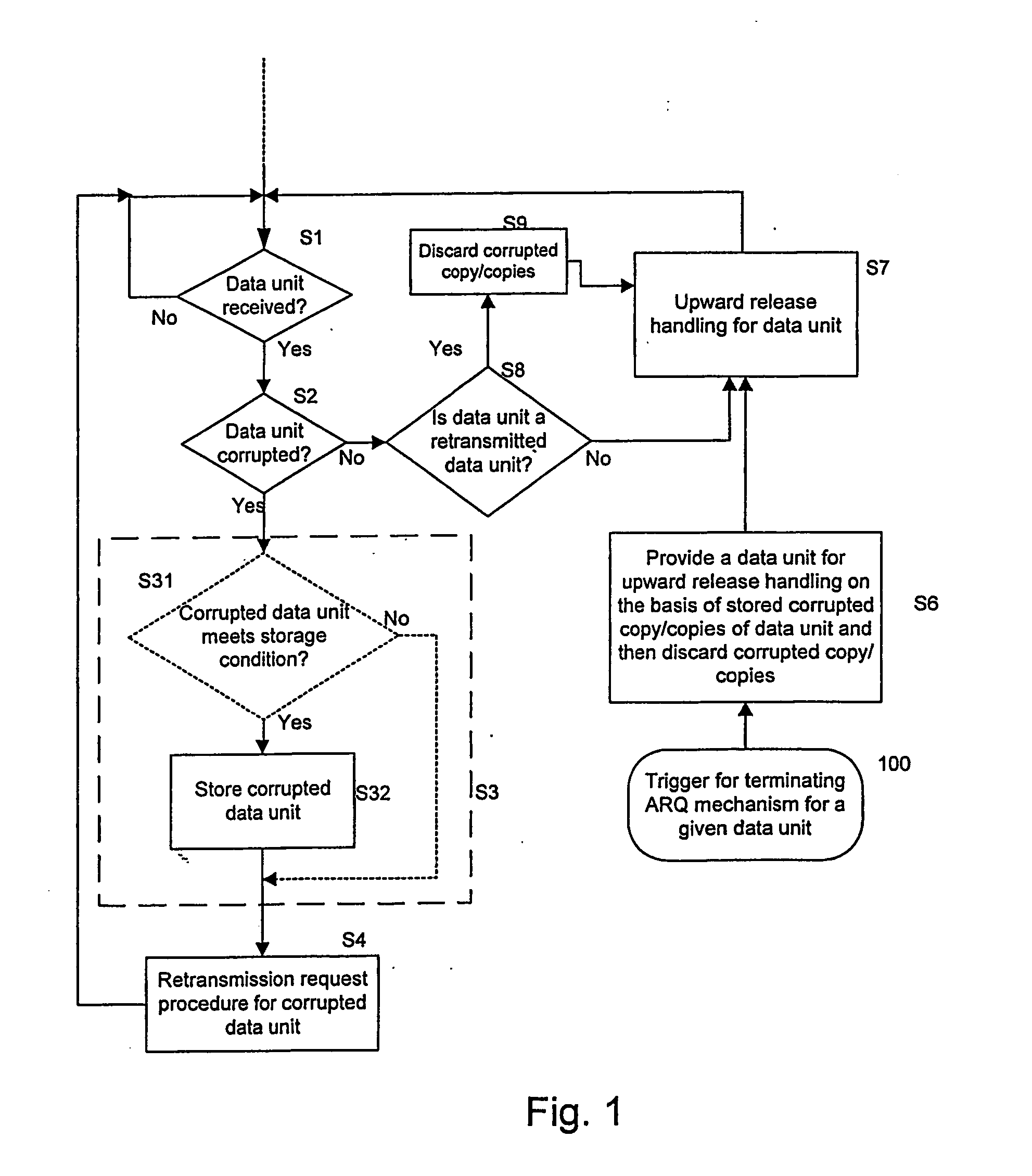
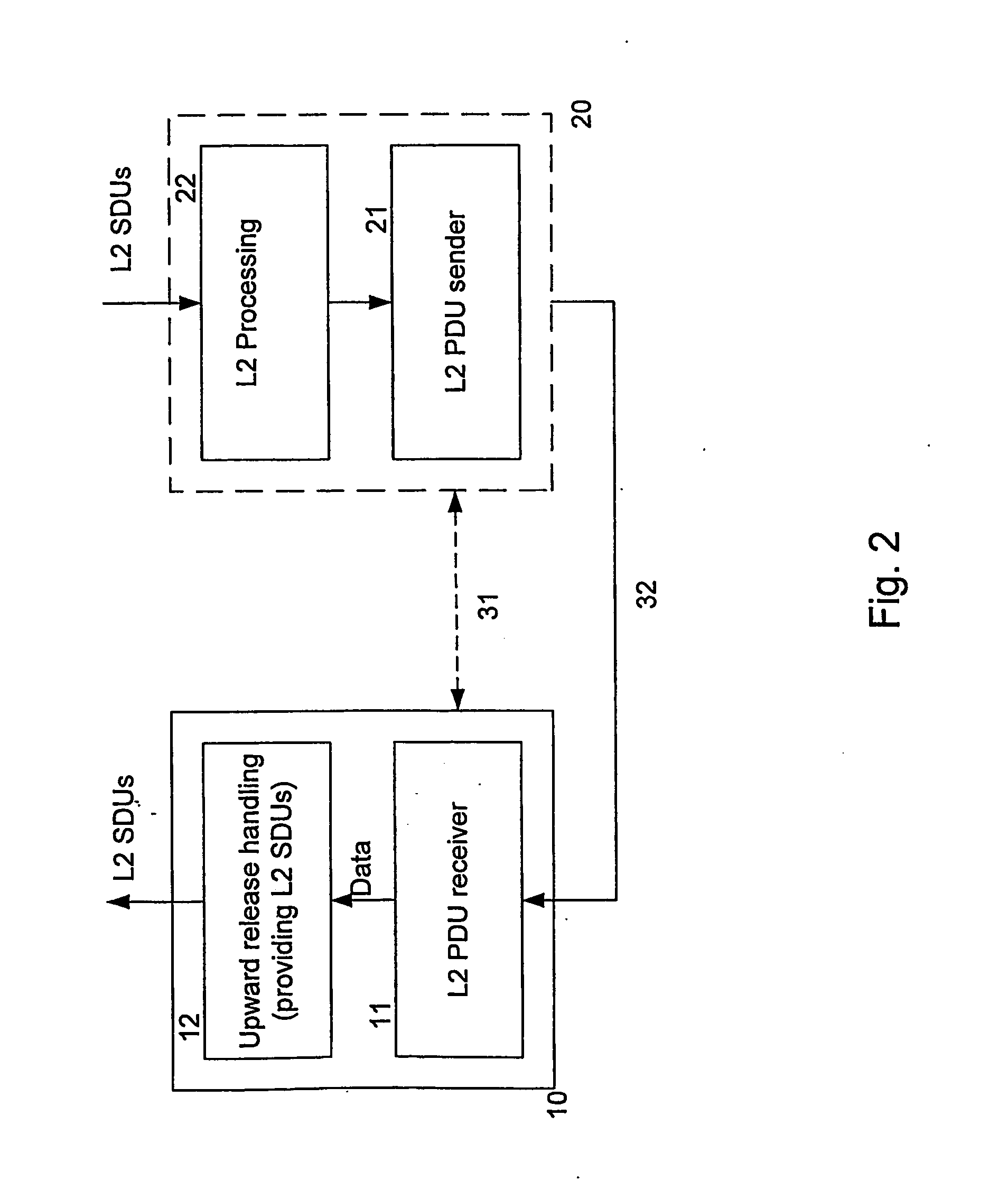
A method and device for handling received data units at the receiving peer of a predetermined data unit exchange protocol at a given layer is described, where said method and device carry out a limited ARQ mechanism for received data units, and are characterised by providing the possibility of storing corrupted copies of received data units, and providing a data unit to an upward release handler on the basis of one or more stored corrupted copies of a given data unit after a triggering event terminating the operation of the retransmission request procedure for the given data unit.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method for transmitting signal on bandwidth request channel at mobile station, mobile station apparatus using the same, method for performing bandwidth request procedure at base station, and base station apparatus using the same
InactiveUS20100214985A1Increase power levelEasy to detectModulated-carrier systemsWireless commuication servicesSignal onMobile station
A method for transmitting a signal on a bandwidth request channel, a mobile station apparatus using the same, a method for performing a bandwidth request procedure in relation to a bandwidth request from a mobile station, and a base station apparatus using the same are disclosed. A mobile station transmits a bandwidth request preamble and a bandwidth request message together to a base station to request a bandwidth. A region of the bandwidth request message may be configured as null tones. In response to the bandwidth request of the mobile station, the base station transmits a BR ACK A-MAP IE indicating reception of the bandwidth request to the mobile station in response to the bandwidth request. The base station transmits an uplink grant to the mobile station by a BR ACK A-MAP IE or a CDMA allocation A-MAP IE. Upon receipt of the uplink grant from the base station, the mobile station transmits uplink scheduled data to the base station. However, if the base station fails to decode the quick access message or the region of the quick access message is filled with null tones, the base station transmits a grant for a bandwidth request header to the mobile station, instead of an uplink grant.
Owner:LG ELECTRONICS INC
Method for performing bandwidth request process in wireless communication system
InactiveUS20110222499A1Bandwidth requestPerformed quickly and effectivelyWireless commuication servicesCommunications systemRequest procedure
A method for performing a bandwidth request procedure in a wireless communication system includes receiving a bandwidth request sequence, which has been selected from a sequence set including a plurality of sequences, via a bandwidth request channel, and selecting a bandwidth request procedure to be performed from among a general bandwidth request procedure and a quick bandwidth request procedure, wherein the sequence set is divided into a plurality of sub-sets corresponding to the general bandwidth request procedure and the quick bandwidth request procedure. The bandwidth request procedure can be quickly and effectively performed.
Owner:LG ELECTRONICS INC
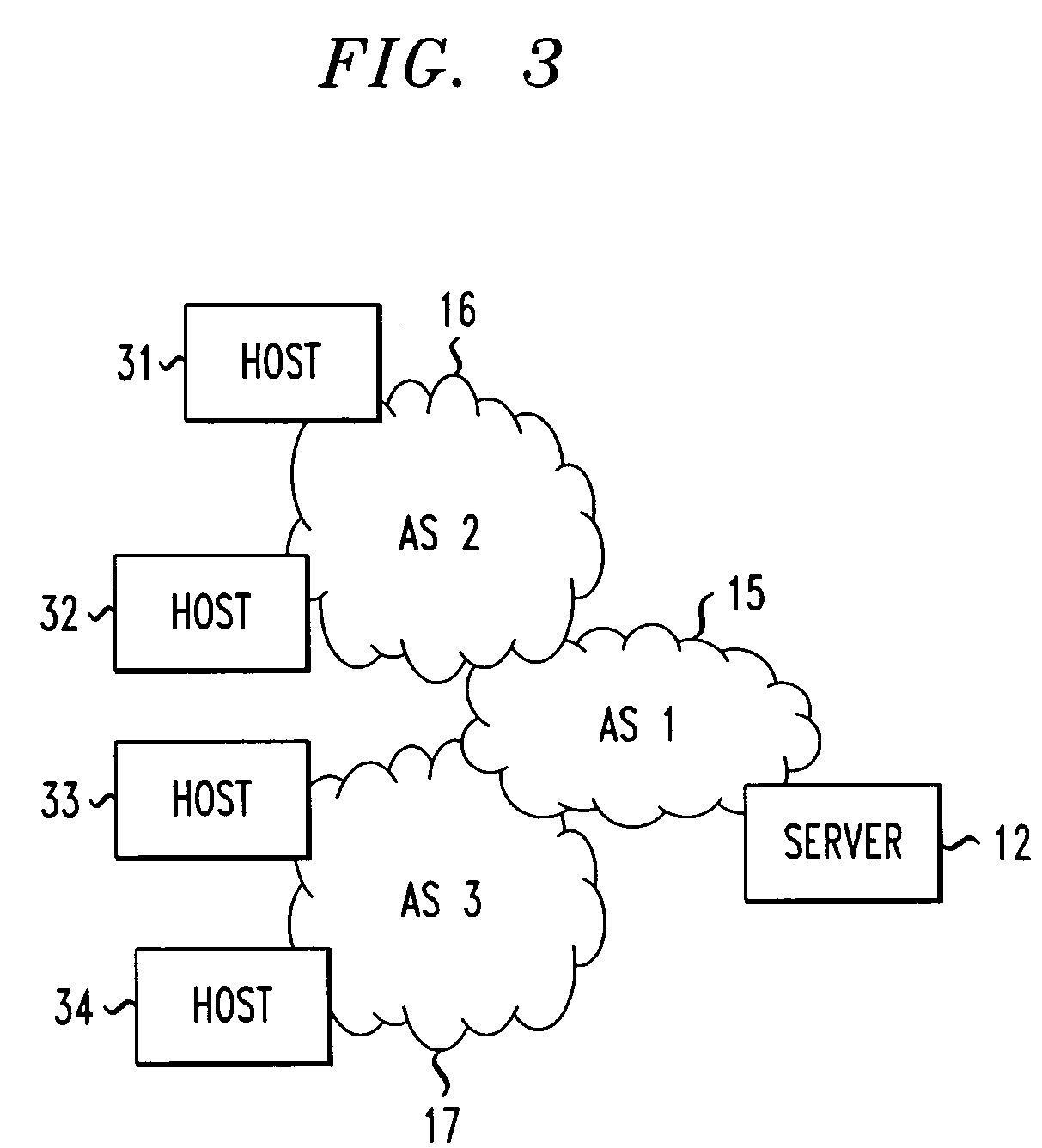
Path analysis tool and method in a data transmission network including several internet autonomous systems
Method for performing the analysis of the characteristics of a data path from a first data processing device to a second data processing device through a network comprising at least an autonomous system consisting in defining a scenario file the scenario to be used, such a scenario including the actions to be used, building a parameter file defining the parameters to be used in the actions, running at least one analysis module based upon the actions of the scenario file and the parameters of the parameter file, the analysis module calling at least a predefined information requesting procedure, and storing in at least an output file the data resulting from the running of the analysis modules
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
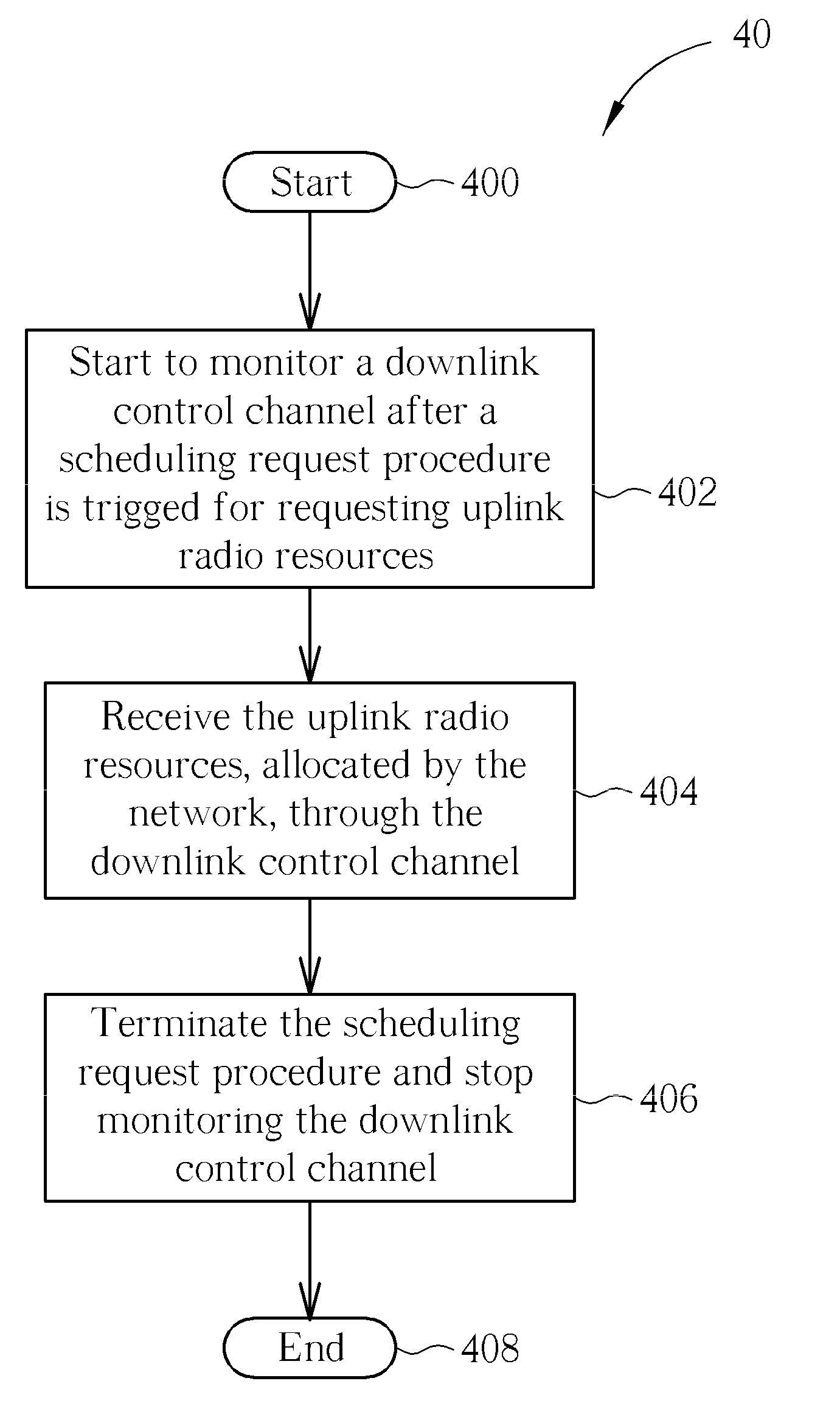
Method of Receiving Signaling and Related Communication Device
InactiveUS20090176502A1Improving uplink transfer delayIncrease delayTransmissionWireless communicationCommunications systemControl channel
A method of receiving signaling for a user equipment (UE) in a wireless communication system is disclosed. The method includes starting to monitor a downlink control channel after a scheduling request procedure, used for requesting uplink radio resources, is triggered until the uplink radio resources are received.
Owner:INNOVATIVE SONIC
Relative value unit monitoring system and method
InactiveUS20140142972A1Office automationHealthcare resources and facilitiesMonitoring systemProcedure requested
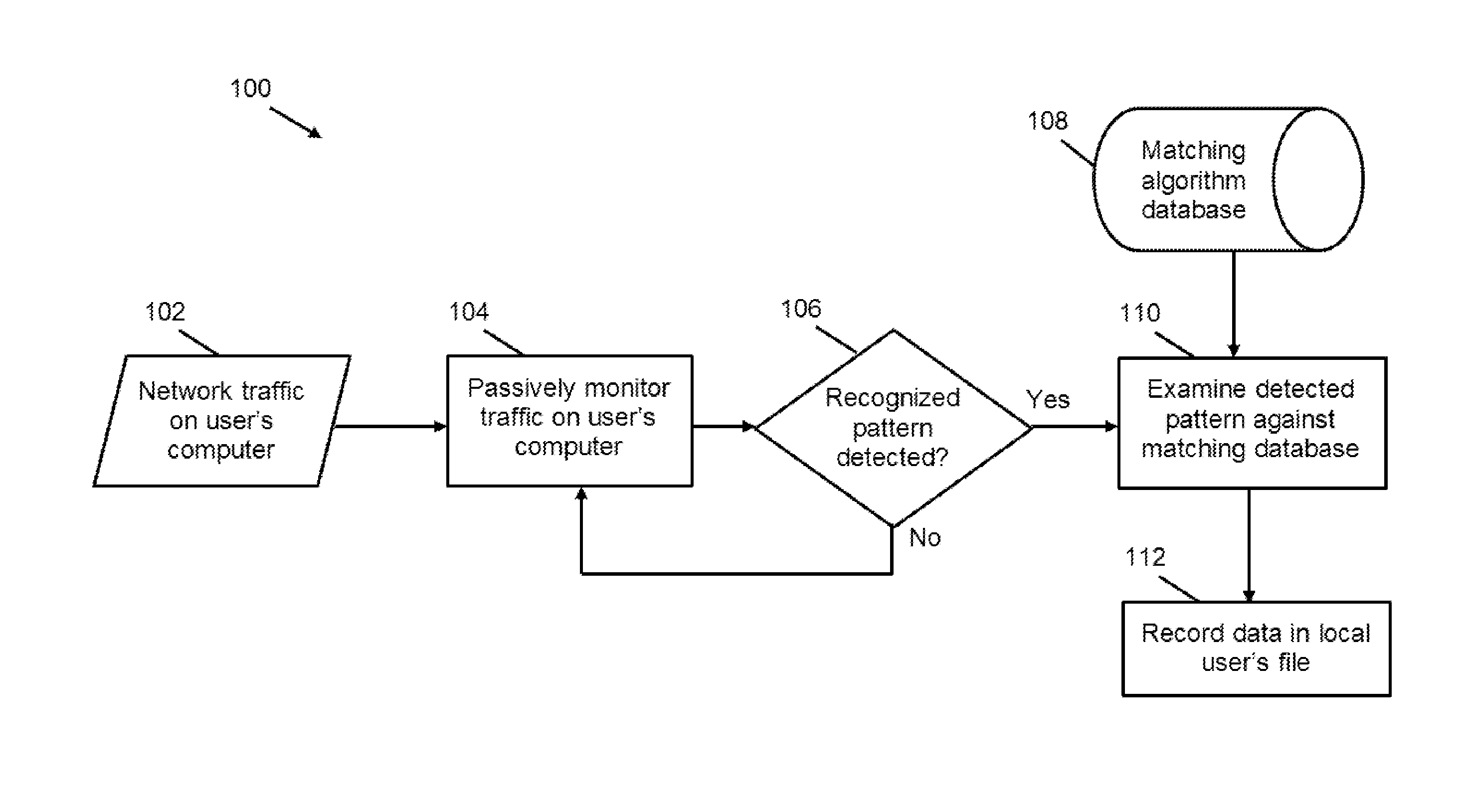
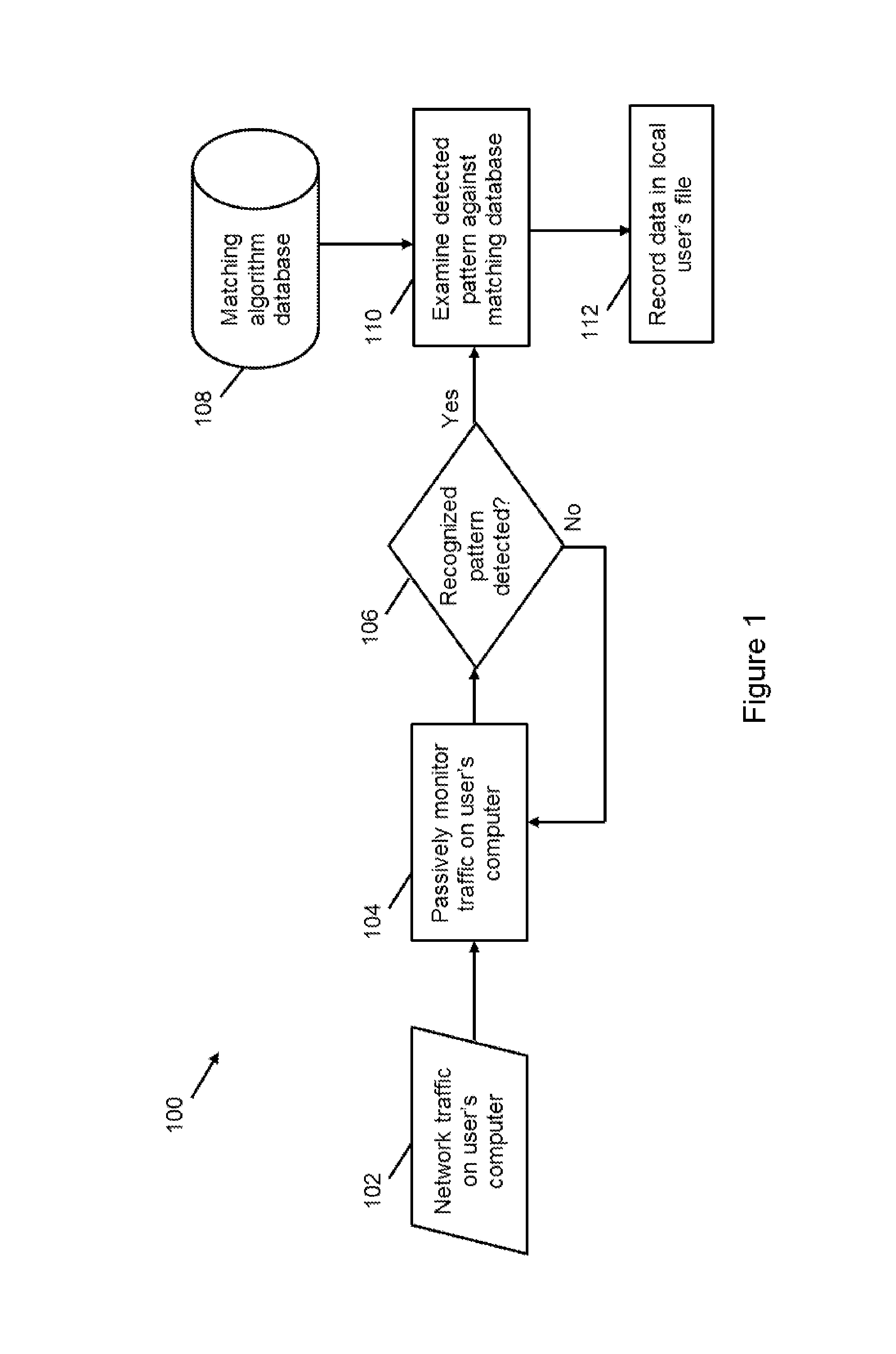
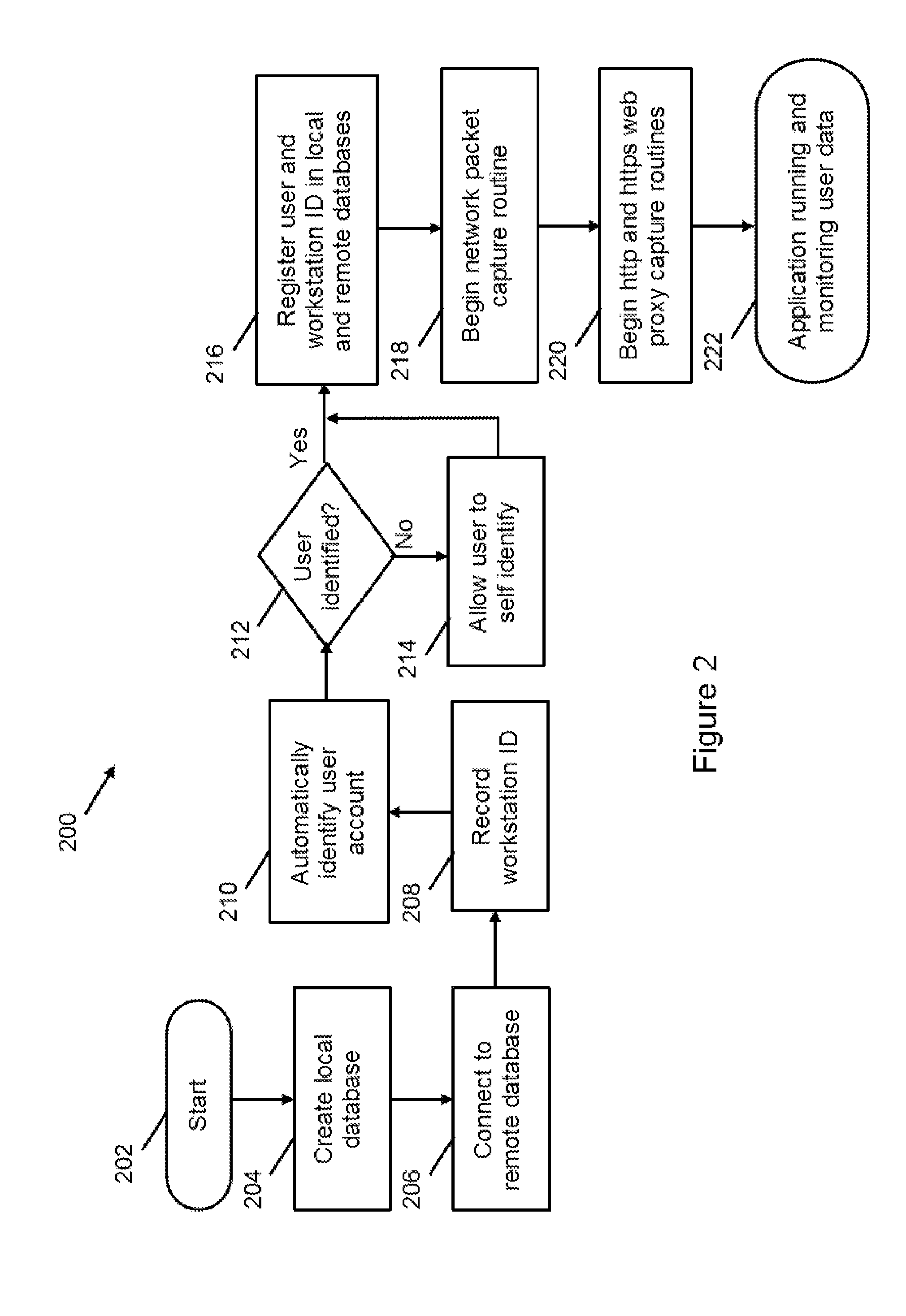
A Relative Value Unit (RVU) monitoring method and system is disclosed that includes passively monitoring network traffic; examining the monitored traffic for recognized patterns in a matching database; deriving detected RVU values from the matching recognized patterns; and updating an RVU tracking database with the detected RVU values. The matching database stores a plurality of recognized patterns and RVU values, and associates the recognized patterns and RVU values. The method can also include notifying the user of detected CPT codes and RVU values. The method can also include determining procedures requested by received medical orders; tracking fulfillment of the requested procedures; and notifying the user when requested procedures remain to be fulfilled. The method can include analyzing data associated with detected patterns to determine if it's a new or previously observed procedure. The method can simultaneously run on multiple computers; and update a common RVU tracking database.
Owner:LUCID RADIOLOGY SOLUTIONS
Mobile telephone, telephone number managing server, telephone number changing system, telephone number requesting method, and telephone number requesting program
InactiveUS20090305691A1Reduce financial burdenEnhances function of mobileDigital data processing detailsNetwork topologiesViewpointsThe Internet
It is desired from the viewpoints of accessory and economy to make common use of one telephone number among a plurality of mobile telephones. A server makes an ID intrinsic to a mobile telephone and a telephone number correspond to each other thereby to relay communications between the mobile telephones made to correspond. A mobile telephone requests the server managing the telephone number and the ID of the mobile telephone from itself via the Internet, to change the correspondence between the telephone number and the mobile telephone ID. In response to this request, the server changes the correspondence between the telephone number and the mobile telephone ID.
Owner:KYOCERA CORP
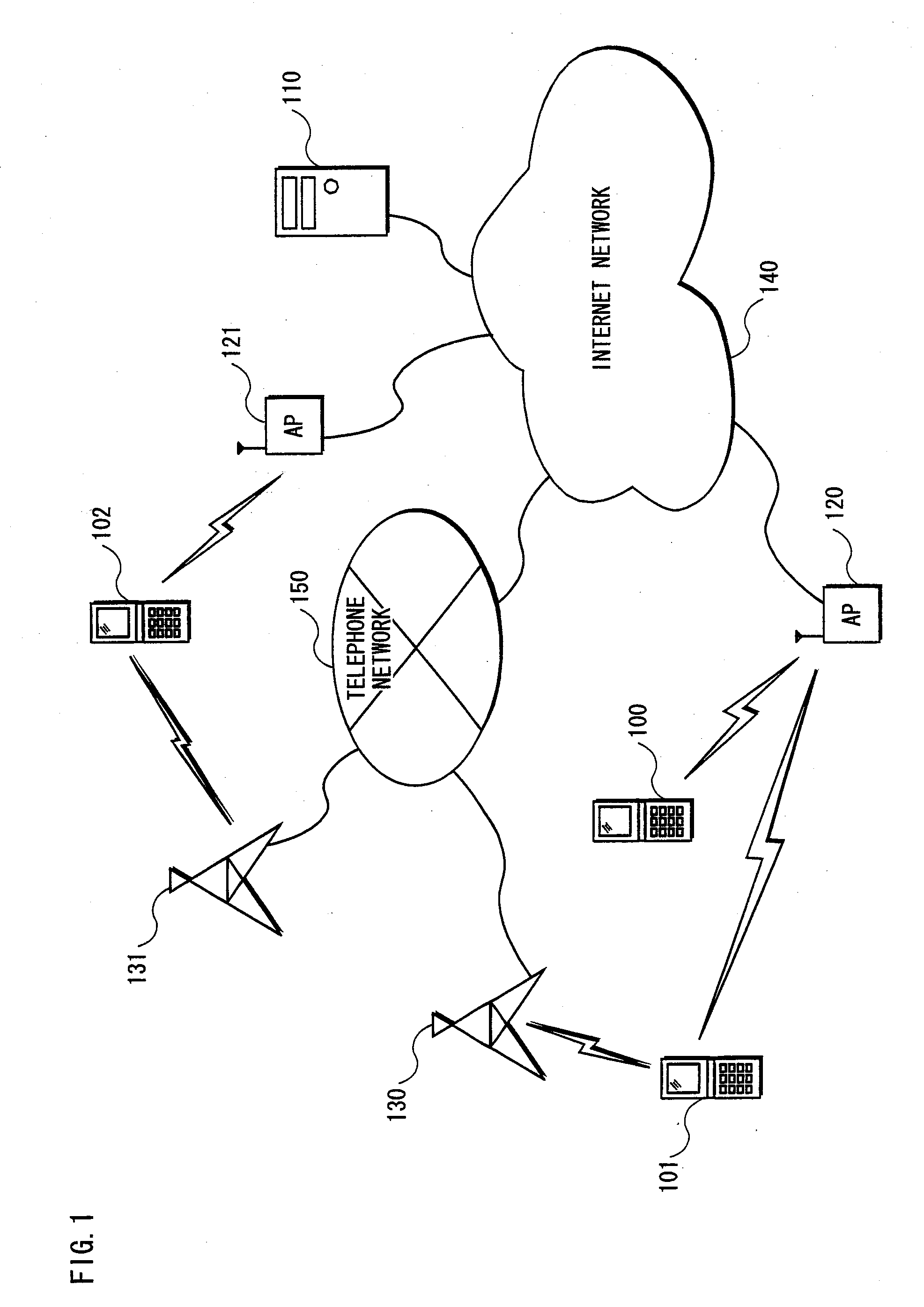
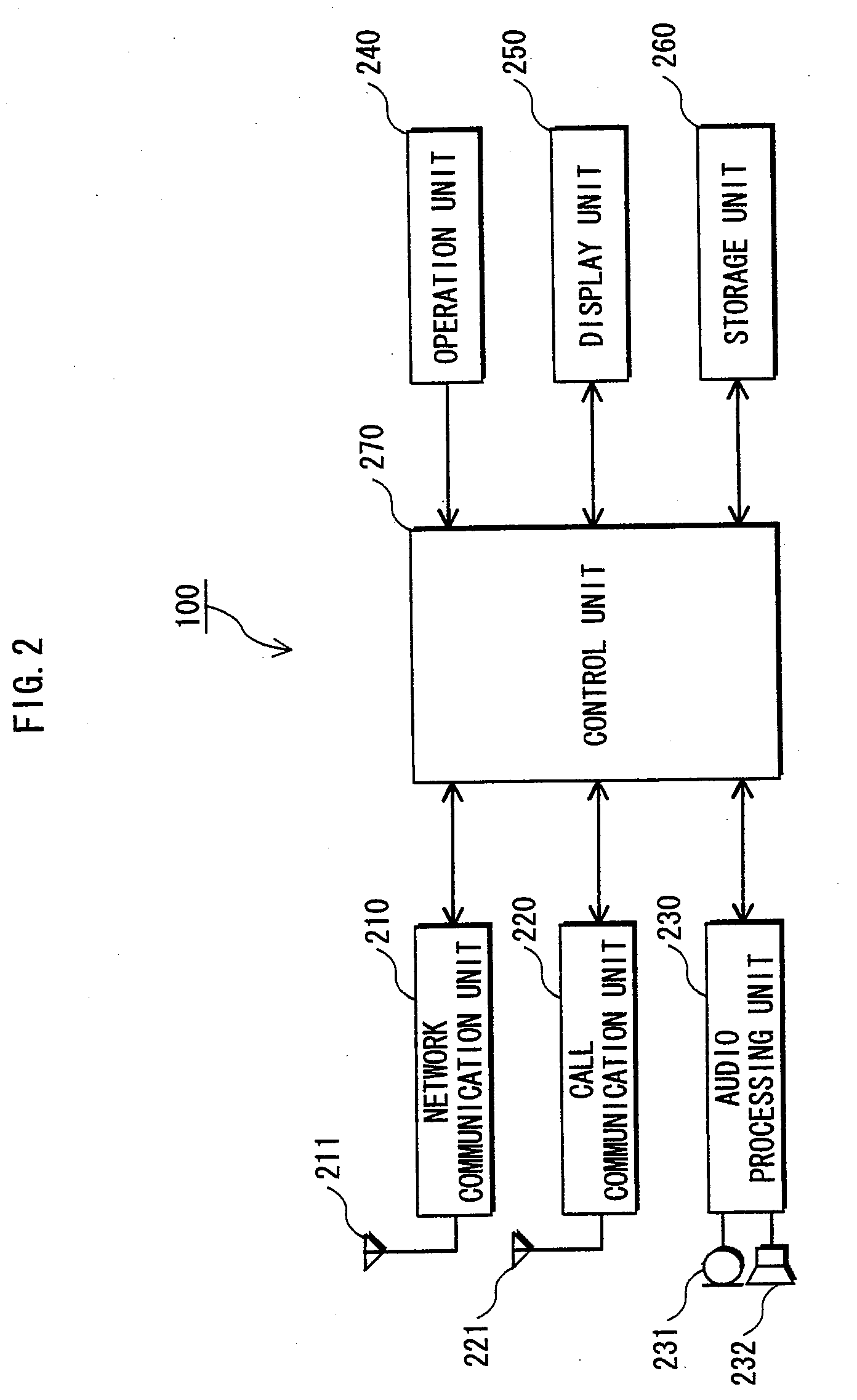
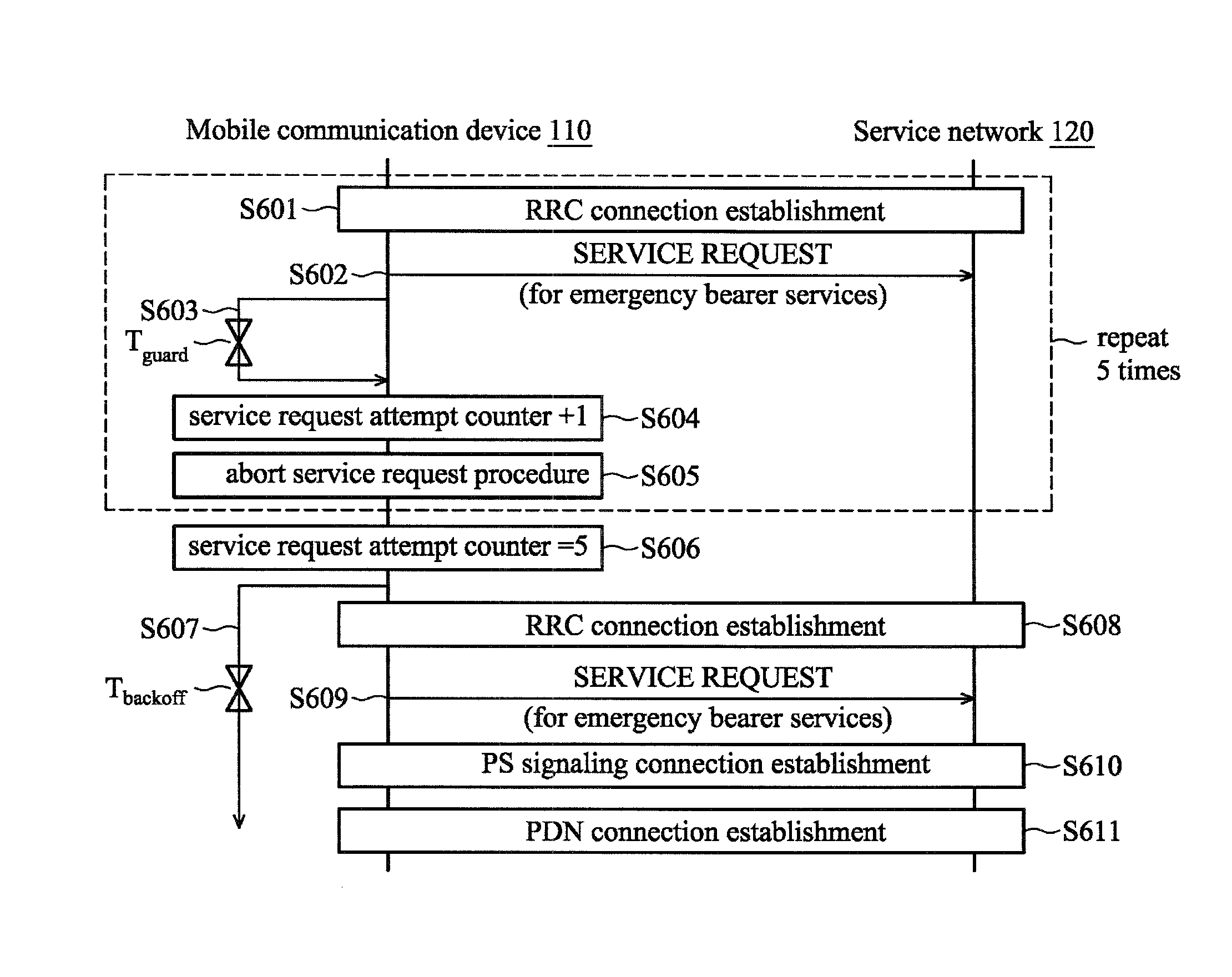
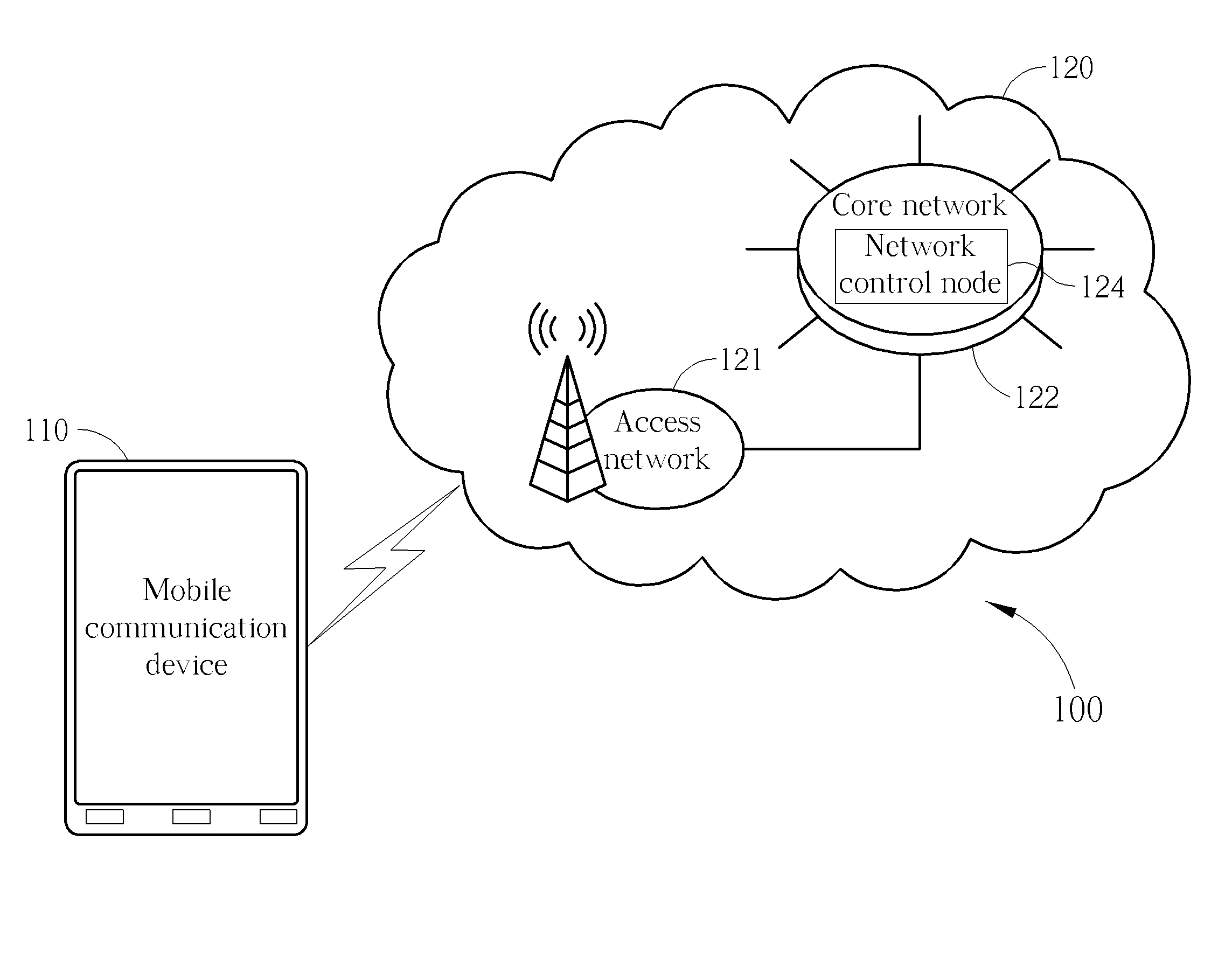
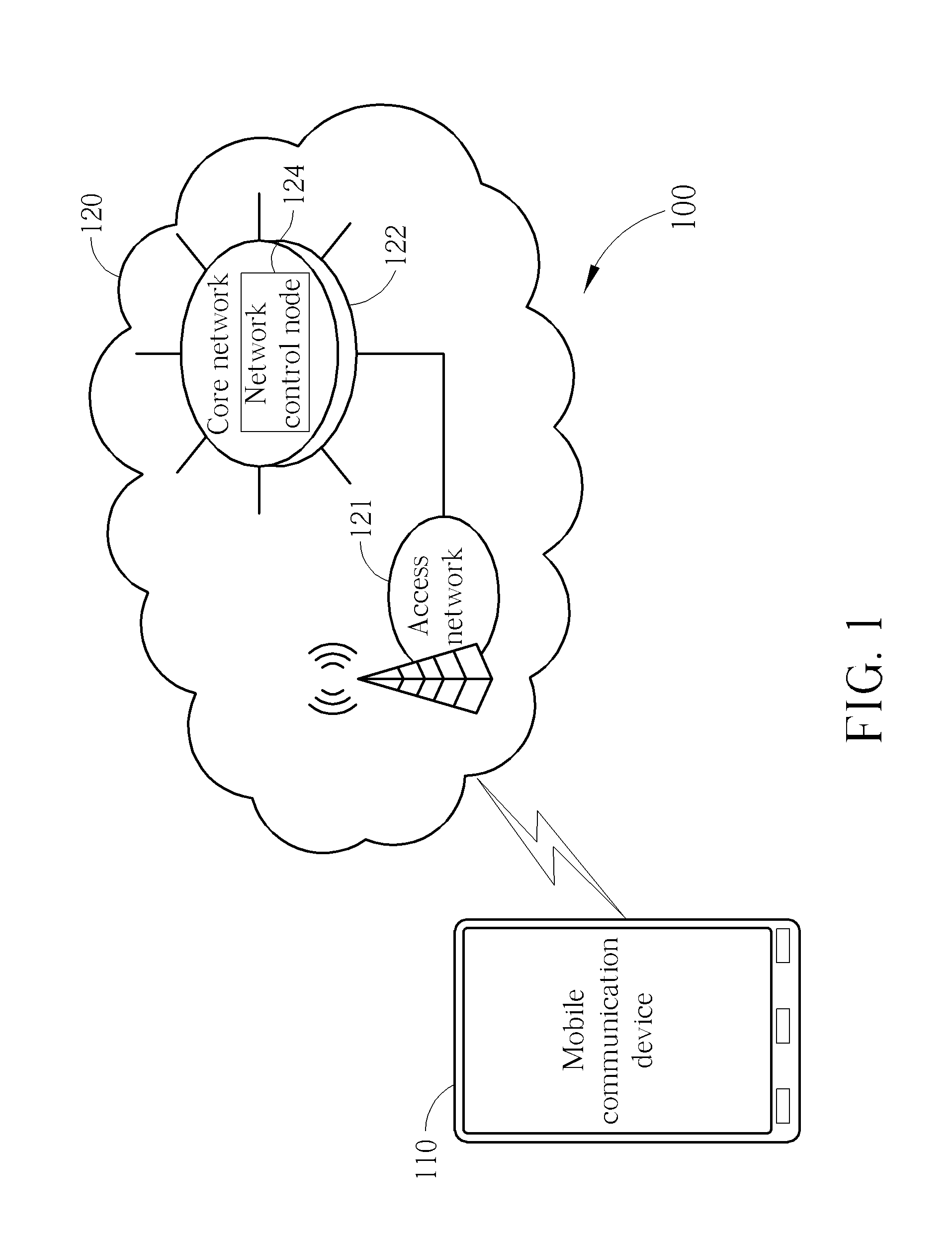
Methods for handling a service request procedures, and apparatuses using the same
A method for handling a service request procedure by a mobile communication device is provided. The method includes the steps of: starting a back-off timer associated with a service request procedure in response to the service request procedure for a normal service having been failed for a maximum number of retries, and initiating another service request procedure for an emergency bearer service before the back-off timer expires.
Owner:HTC CORP
Threshold-based and power-efficient scheduling request procedure
ActiveUS9723618B2Error prevention/detection by using return channelConnection managementPower efficientRequest procedure
The invention relates to methods for improving a scheduling request transmission between a UE and a base station. The transmission of the scheduling request is postponed, by implementing a threshold that the data in the transmission buffer has to reach, before a transmission of the scheduling request is triggered. In one variant, the data in the transmission buffer needs to reach a specific amount, to trigger a scheduling request. The invention refers to further improvements: the PDDCH monitoring time window is delayed after sending a scheduling request; the dedicated scheduling request resources of the PUCCH are prioritized differently such that low-priority scheduling requests are transmitted less often.
Owner:APPLE INC
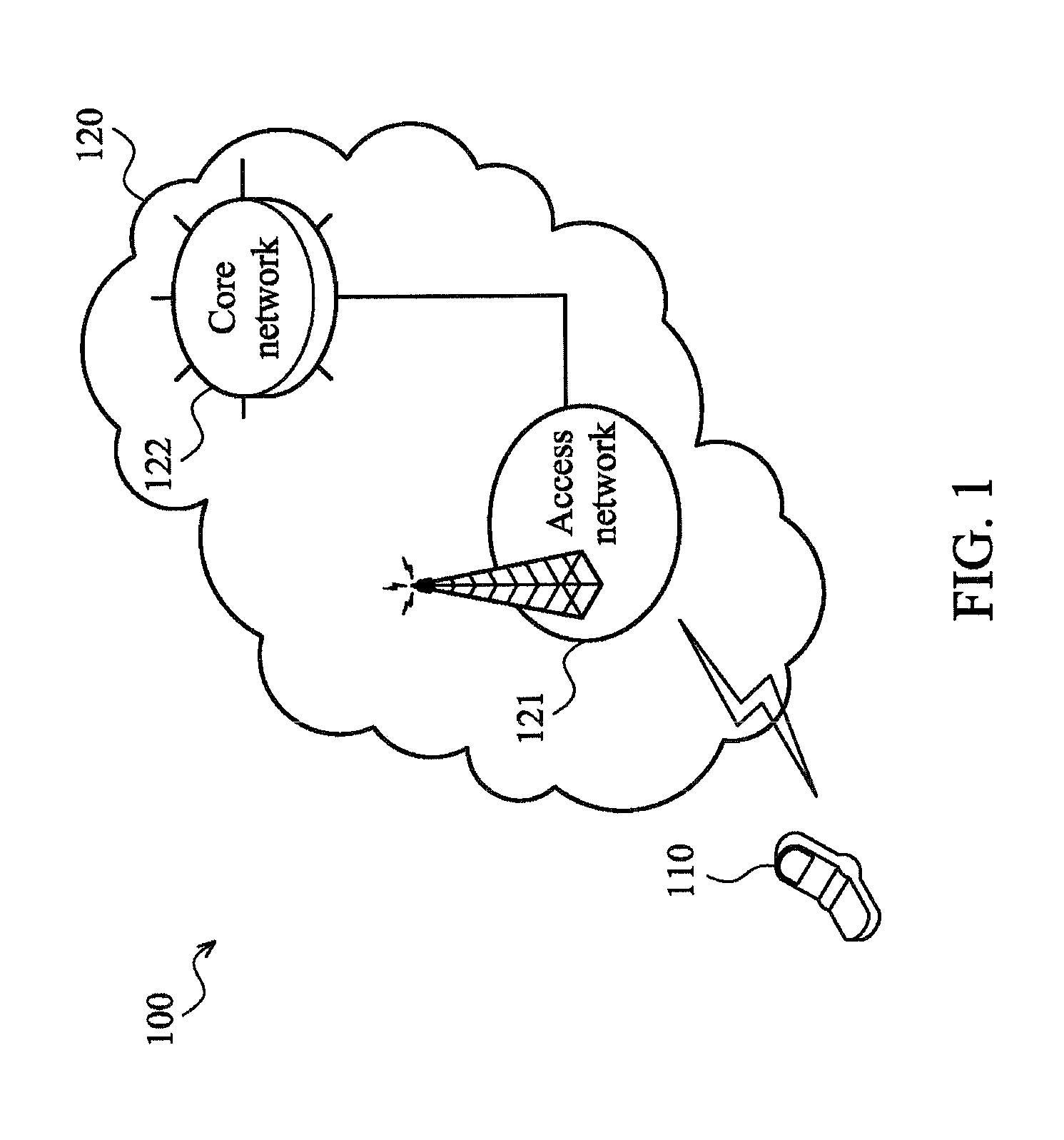
Method of Handling Singling in Congested Core Network
ActiveUS20130029631A1Emergency connection handlingTelephonic communicationRequest procedureMobile device
A method of handling singling in a congested core network for a mobile device is disclosed. The method comprises initiating a first service request procedure for an emergency bearer service when a back-off timer is running on the mobile device; and not deactivating non-emergency Evolved Packet System (EPS) context locally and keeping the non-emergency EPS context during the first service request procedure for the emergency bearer service, wherein the non-emergency EPS context corresponds to user plane radio bearers which was not established, locally or with signalling.
Owner:HTC CORP
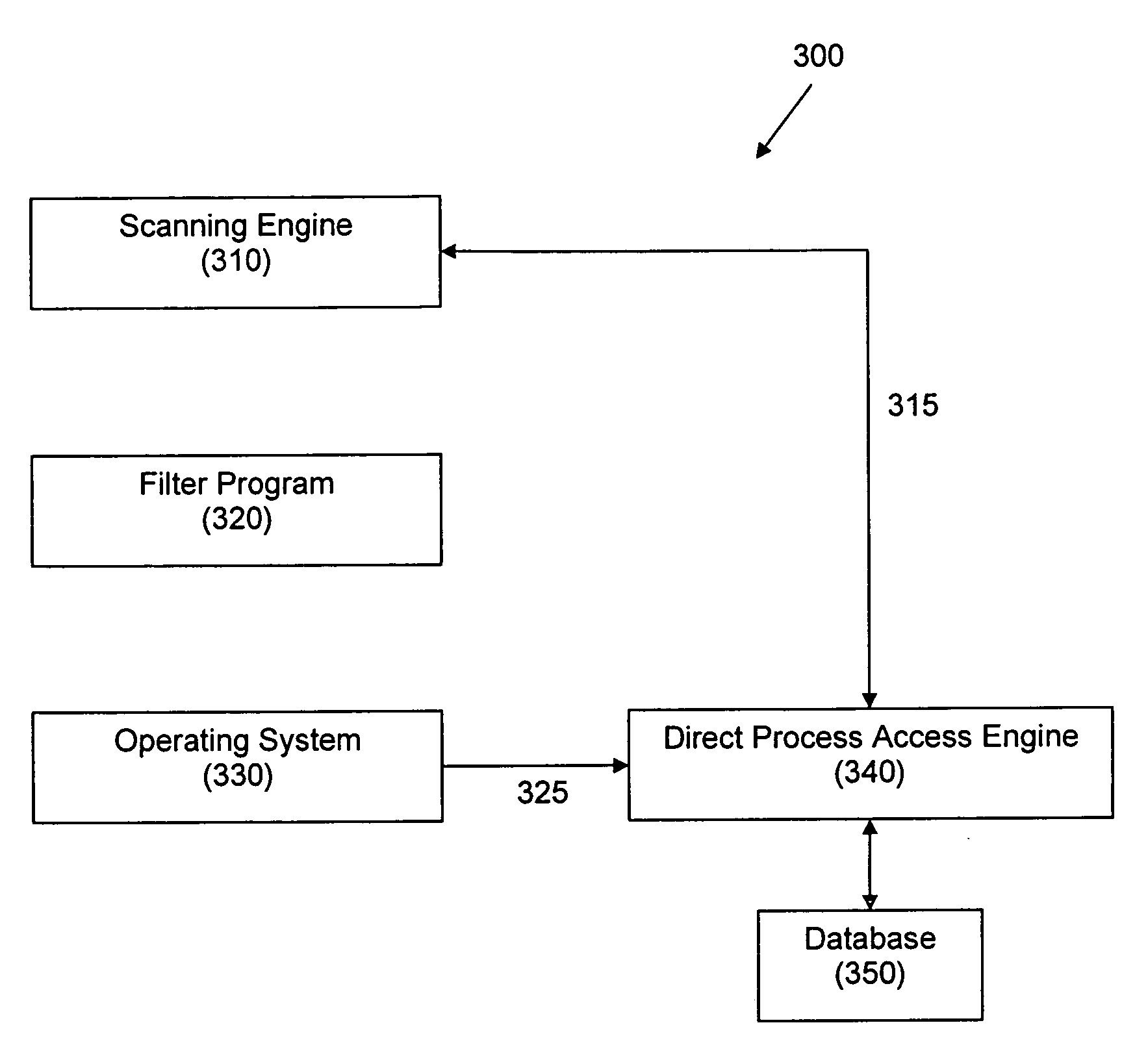
Direct process access
InactiveUS20080046977A1Memory loss protectionDigital data processing detailsComputer programReal-time computing
A method, computer program product and system for obtaining notification information about the state of an operating system 330. The method 300 includes the steps of receiving, by a Direct Process Access (DPA) engine 340, a request 315 for the notification information from a requesting program 310. The notification information is obtained from a database 350 associated with the DPA engine 340 and the notification information is provided to the requesting program 310. The DPA engine 340 receives update information 325 indicative of changes in the notification information directly from the operating system 330 and causes the notification information to be updated in the database 350.
Owner:NORTONLIFELOCK INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com