Electronic document security device
A technology of electronic documents and security devices, applied in computer security devices, digital data protection, electronic digital data processing, etc., can solve problems such as insufficient confidentiality, inconsistent code tables, and documents that cannot be displayed normally, and achieve high confidentiality Effect
Inactive Publication Date: 2011-06-15
SHANGHAI DIAIBI CHEM TECH
View PDF3 Cites 5 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
The biggest disadvantage of the regular method is that the confidentiality is not strong enough. In theory, as long as there is a computer with a fast enough operation speed, any regular encryption method can be cracked through computer operations.
In addition, if the language environment of the computer system used for encryption and decryption is not the same or the code tables used by the encryptor and decryptor are inconsistent, the decrypted document may not be displayed normally
For example, for a piece of Chinese civilized text, if the Chinese version of the Linux operating system is used to obtain the ciphertext when encrypting, and the Japanese version of the Windows system is used for decryption, the original plaintext may not be displayed normally after decryption
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
Embodiment 2
Embodiment 3
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
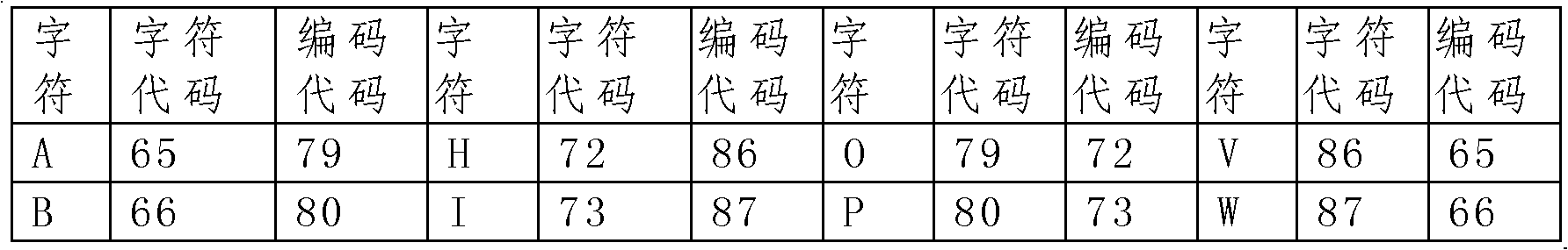
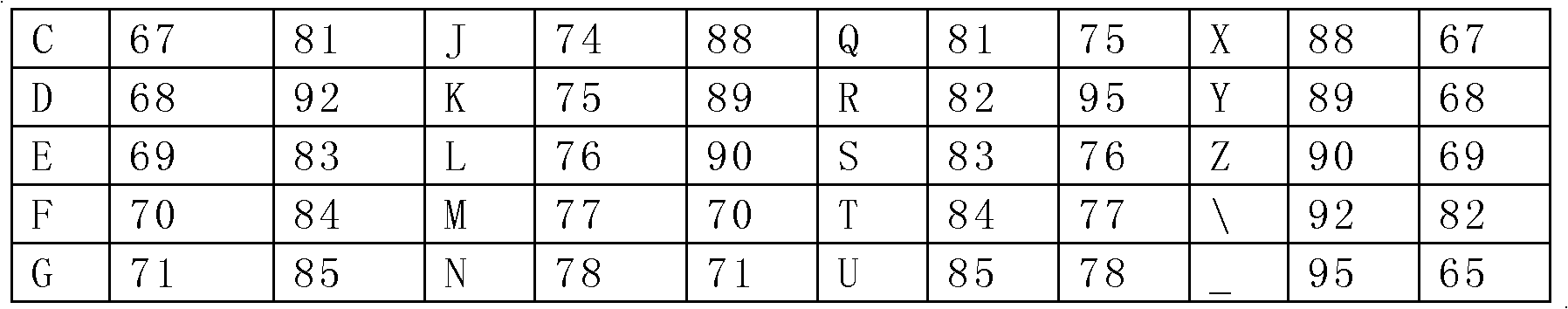
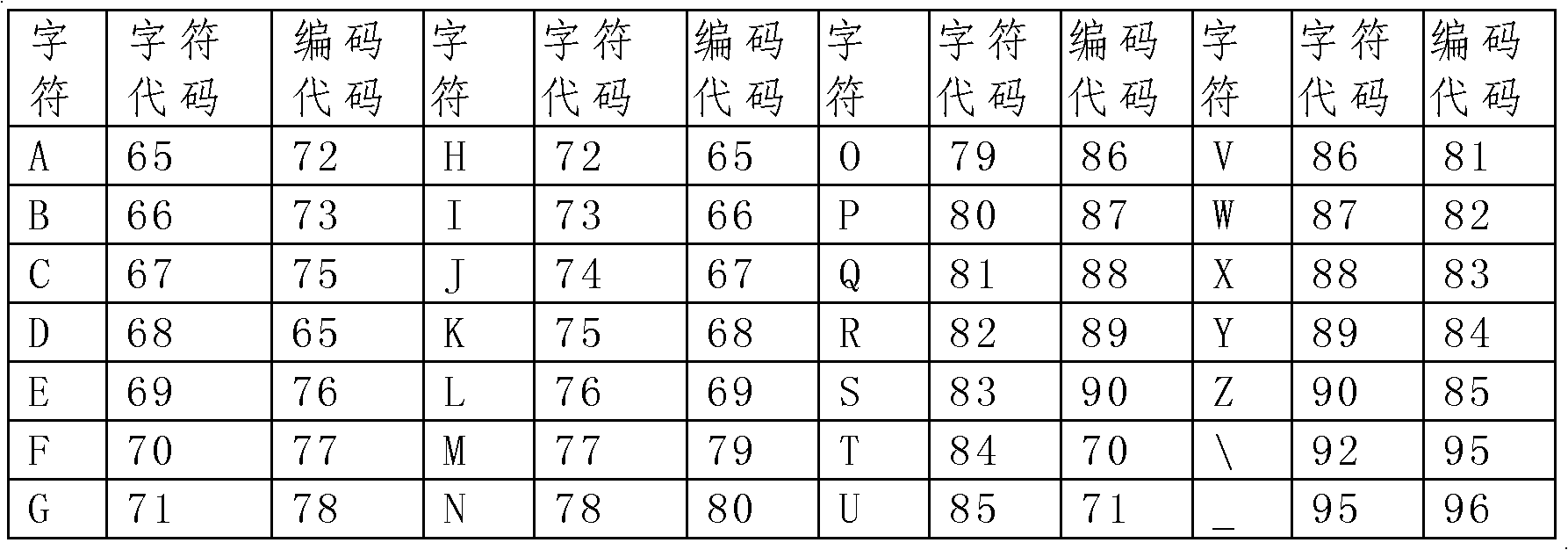
The invention discloses an electronic document security device. The device comprises a code generation module, an encryption / decryption module, a code loading module, a code storage module, and a computer with an editing device, wherein the code storage module can store more than one encrypted code table; each encrypted code table is generated previously or immediately by the code generation module according to character codes in a universal code table; and the encrypted code table is irregular, i.e., the coding codes in the encrypted code table have no mathematical rule with the character codes. The electronic document security device has the advantages of extremely high security, safety, convenience and generality.
Description
Security device for electronic documents technical field The invention relates to electronic documents, in particular to a security device for electronic documents. Background technique Documents contain a large number of language symbols, or "characters". In order to protect the content of the plaintext document from being illegally obtained, the characters in the document need to be encrypted. Traditional encryption methods can be divided into two categories: regular and irregular. The regular encryption method is to transform the characters in the plaintext to obtain the ciphertext according to certain rules or rules, so as to achieve the purpose of encryption. The biggest disadvantage of this method is that theoretically any regular encryption method can be cracked through mathematical operations. The random encryption method is an encryption method that replaces another character with a code, and there is no inherent mathematical law in the correspondence between ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): G06F21/24G06F21/60
Inventor 顾晓军
Owner SHANGHAI DIAIBI CHEM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com