Method for restricting illegal JAVA software operation by using software watermarks
A software watermarking and watermarking technology, which is applied in the direction of instrument, program/content distribution protection, electronic digital data processing, etc., can solve the problems of malicious software attack, lack of verification of JAVA software, etc., achieve good anti-attack ability and meet the security requirements of JAVA software operation Requirements for performance and operating efficiency, effects of good operating performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
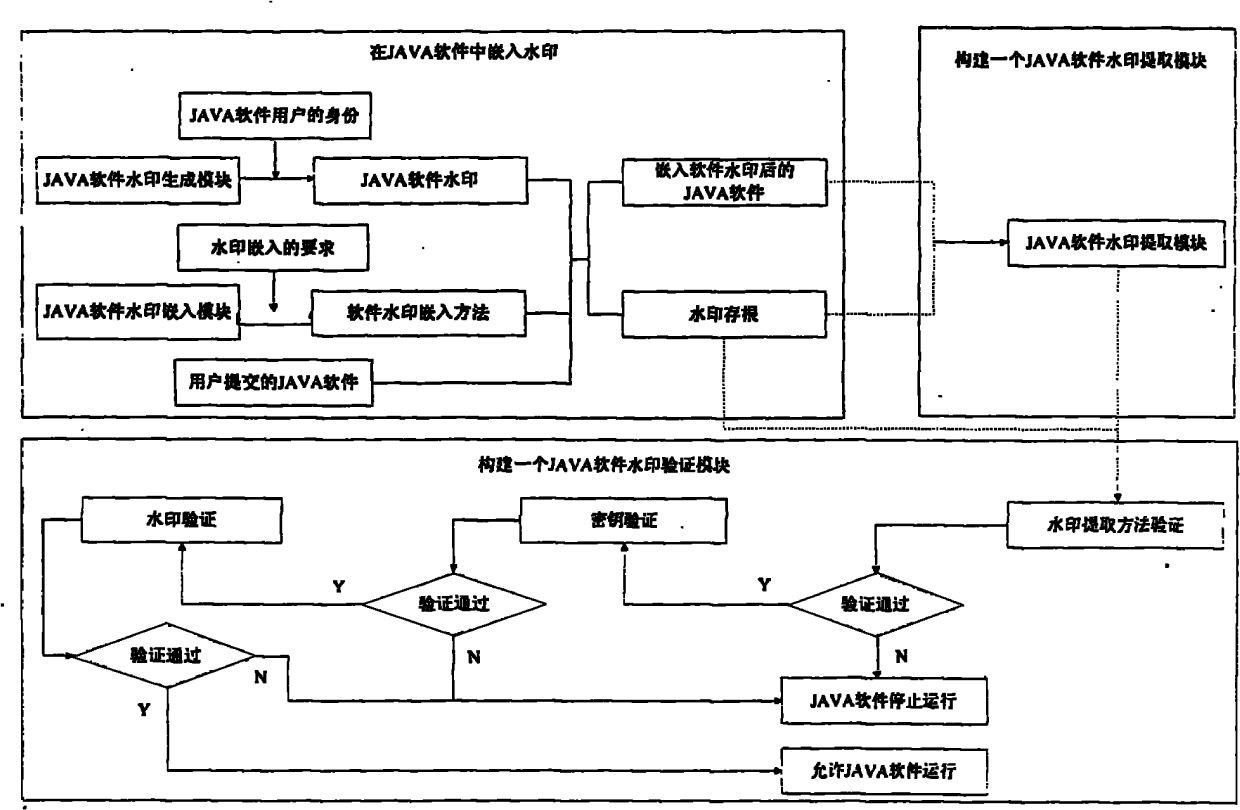
[0028] The method for restricting the operation of illegal JAVA software by utilizing software watermarks proposed by the present invention has a flow chart as follows: figure 1 shown, including the following steps:
[0029] (1) Embed a watermark in the JAVA software submitted by the user, and the embedding process includes the following steps:
[0030] (1-1) Build a JAVA software watermark generation module, and generate a JAVA software watermark according to the identity of the user submitting the JAVA software;
[0031] (1-2) Construct a JAVA software watermark embedding module including multiple watermark embedding methods;
[0032] (1-3) Select a software watermark embedding method from the JAVA software watermark embedding module according to the requirements of the submitted JAVA software user. The specific process is as follows:
[0033] (1-3-1) If the user requires the software watermark to have strong robustness, select the dynamic watermark embedding method;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com