Method for routing protocol supporting of mobility in integrated network access subnetwork
A mobility and network technology, applied in wireless network protocols, electrical components, wireless communication, etc., can solve the problems of wasting control message processing overhead, aggravating HA node processing overhead, etc., and achieve the effect of reducing single point failure rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0037] First, some terms used in this embodiment are introduced:
[0038] Host ID (HID): It is only used for accessing the network and represents the public identity of the access terminal or subnet, and the ID does not change during the movement of the mobile terminal. For simple description and convenient discussion, this embodiment assumes that each terminal has only one globally unique HID.
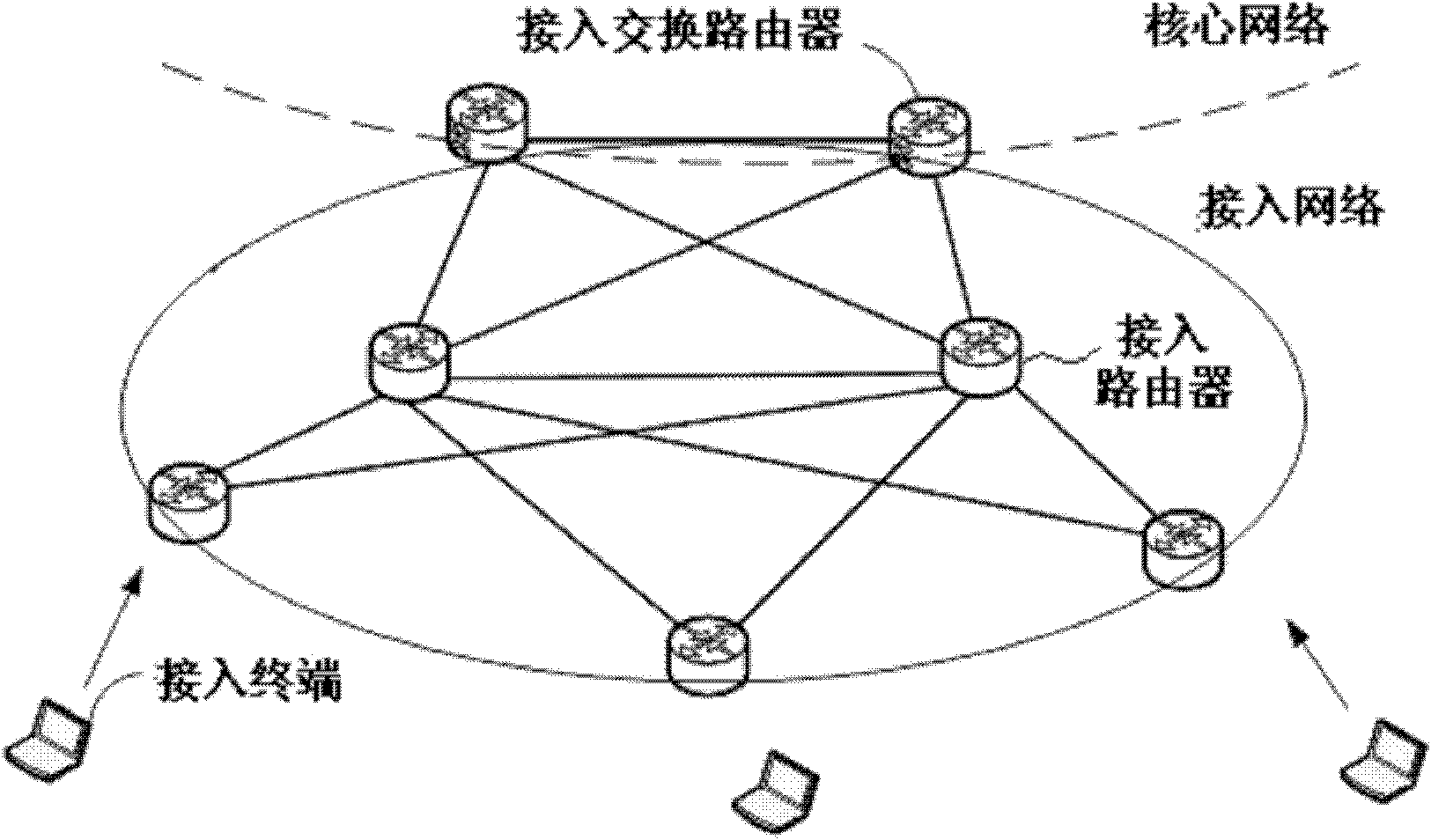
[0039] Access router: Appears only in the access network, connects with access terminals and other access routers, generates and stores host-location relationships for host agents, and registers host-location relationships with designated access routers, and communicates with other access routers The router provides the host-location query service, forms a router link state maintenance area with other access routers, and maintains reachability through the underlying routing protocol;
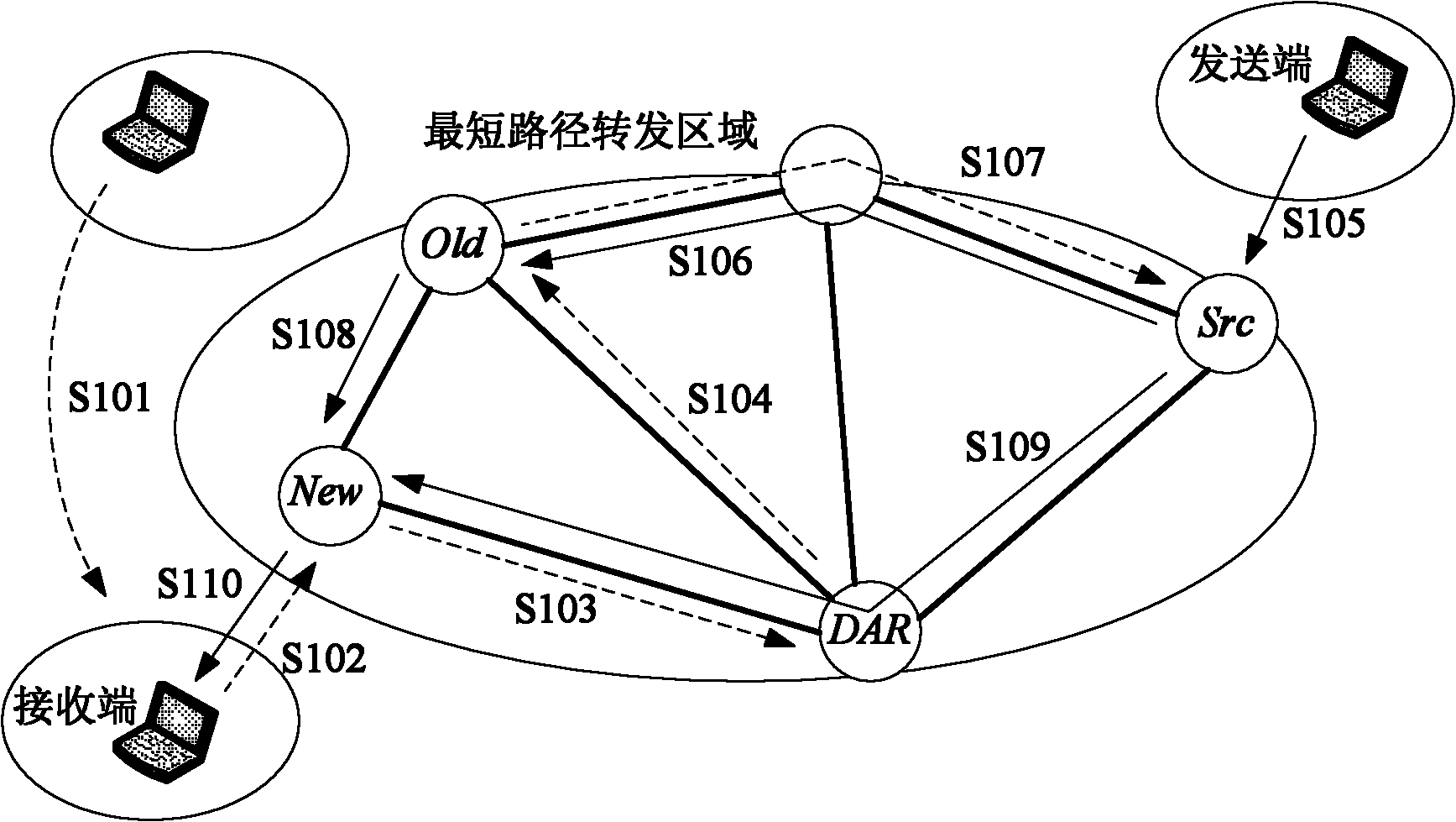
[0040] This embodiment includes: a mobile access terminal, an old access router before the terminal...
Embodiment 2
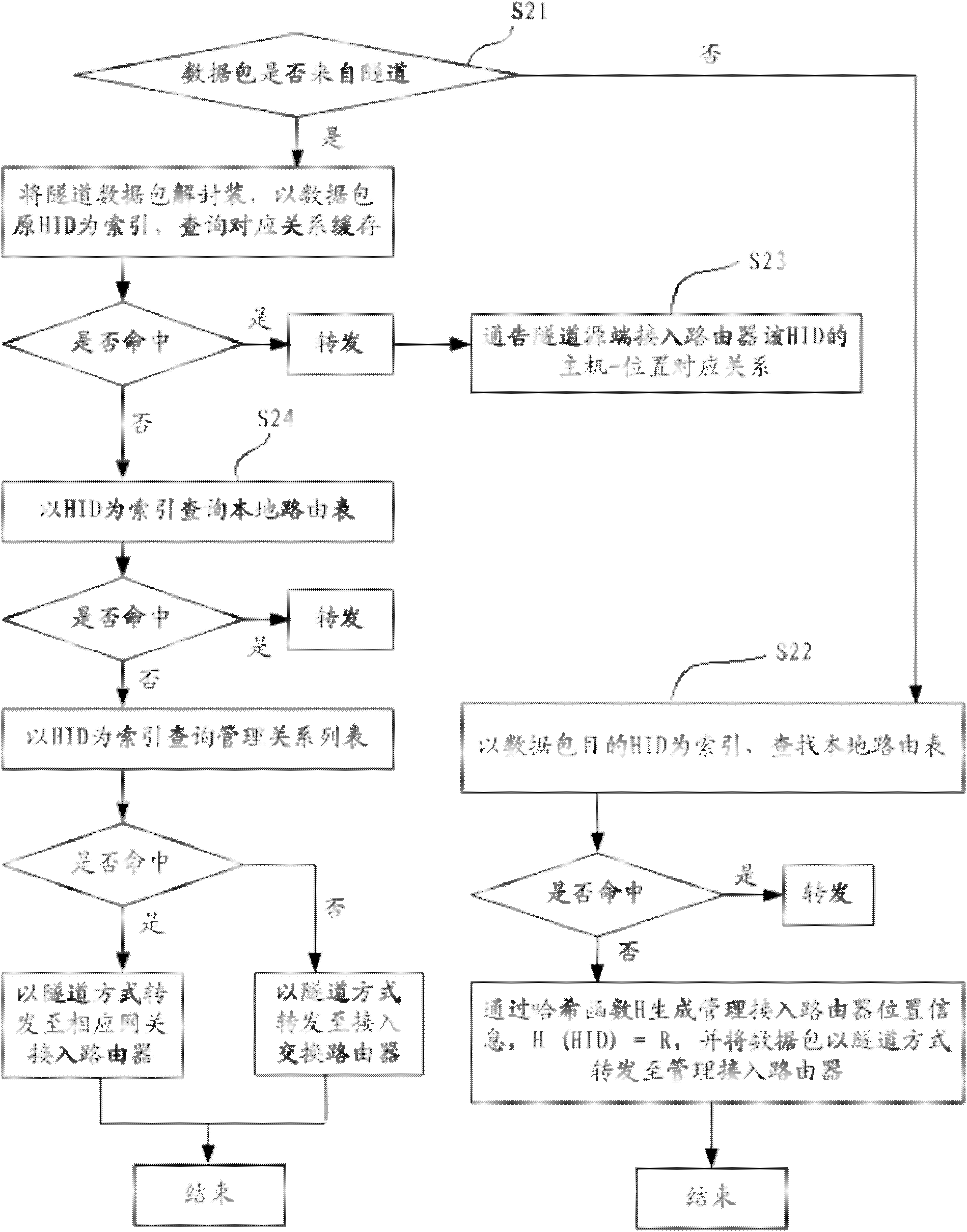
[0061] This embodiment is an improvement of Embodiment 1 on the data packet forwarding process of the access router, such as image 3 shown. This embodiment includes steps:
[0062] S21. For the access router, if the data packet is not from the tunnel, jump to step S22; if the data packet is from the tunnel, decapsulate the tunnel data packet, and use the original destination HID of the data packet as an index to find its own host-location Correspondence cache, if hit, then forward to the corresponding interface, and jump to step S23; if not hit, then jump to step S24;
[0063] S22. Using the data packet purpose HID as an index, search the local routing table, if it is hit, then forward it to the corresponding interface, and the forwarding process ends; if it is not hit, then generate the location information of the designated access router through the hash function H, H(HID) =R, and the packet is forwarded to the designated access router R in a tunnel mode (tunnel is establ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com