Method for detecting phishing webpage based on nearest neighbour and similarity measurement
A technology of phishing web pages and similarity, applied in the field of information security, can solve the problems of no consideration and failure of similarity detection, and achieve the effect of improving precision and recall rate, and saving program computing time and space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The implementation method requires the following steps:
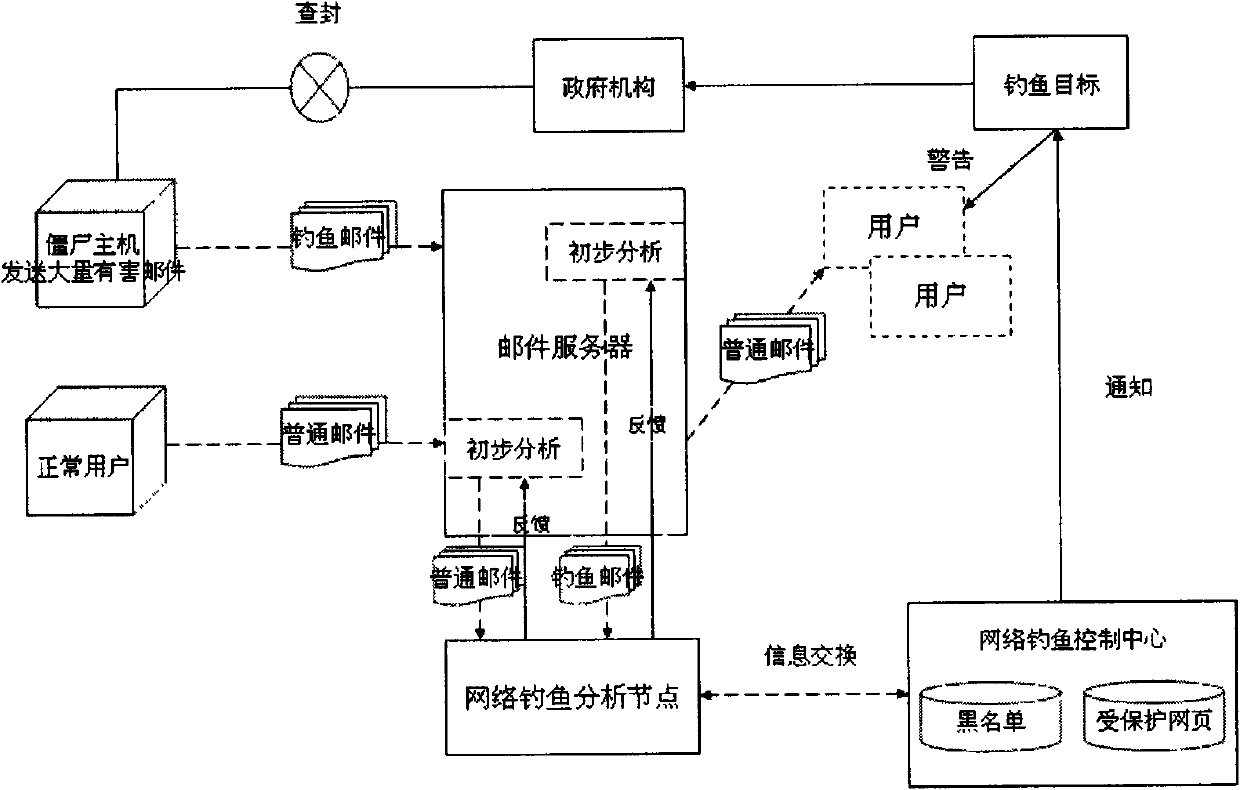
[0022] Step 1) Collect phishing webpages, corresponding legal webpages and other legal webpage data sets
[0023] From the website http: / / www.phishtank.com / Collect phishing web pages; legal web pages corresponding to phishing web pages; ordinary other legitimate web pages.
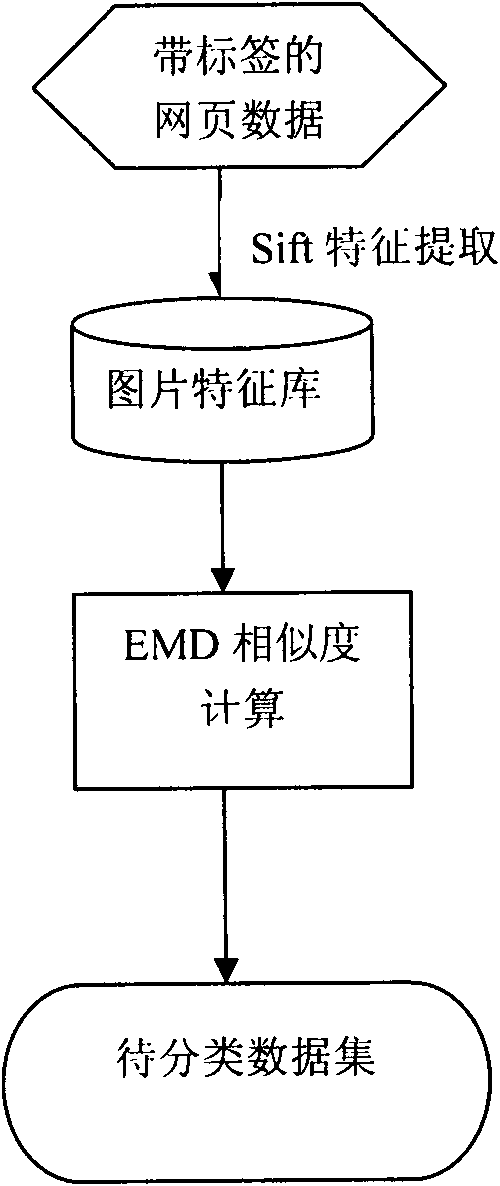
[0024] Step 2) Extract features from the collected data
[0025] Save the collected web pages as pictures. From these pictures, you can extract various color features, texture features, shape features, and some SIFT (Scale-invariant feature transform) features that can be used locally.
[0026] Step 3) Calculate the land movement distance of the two pictures based on the features of the extracted webpage pictures.
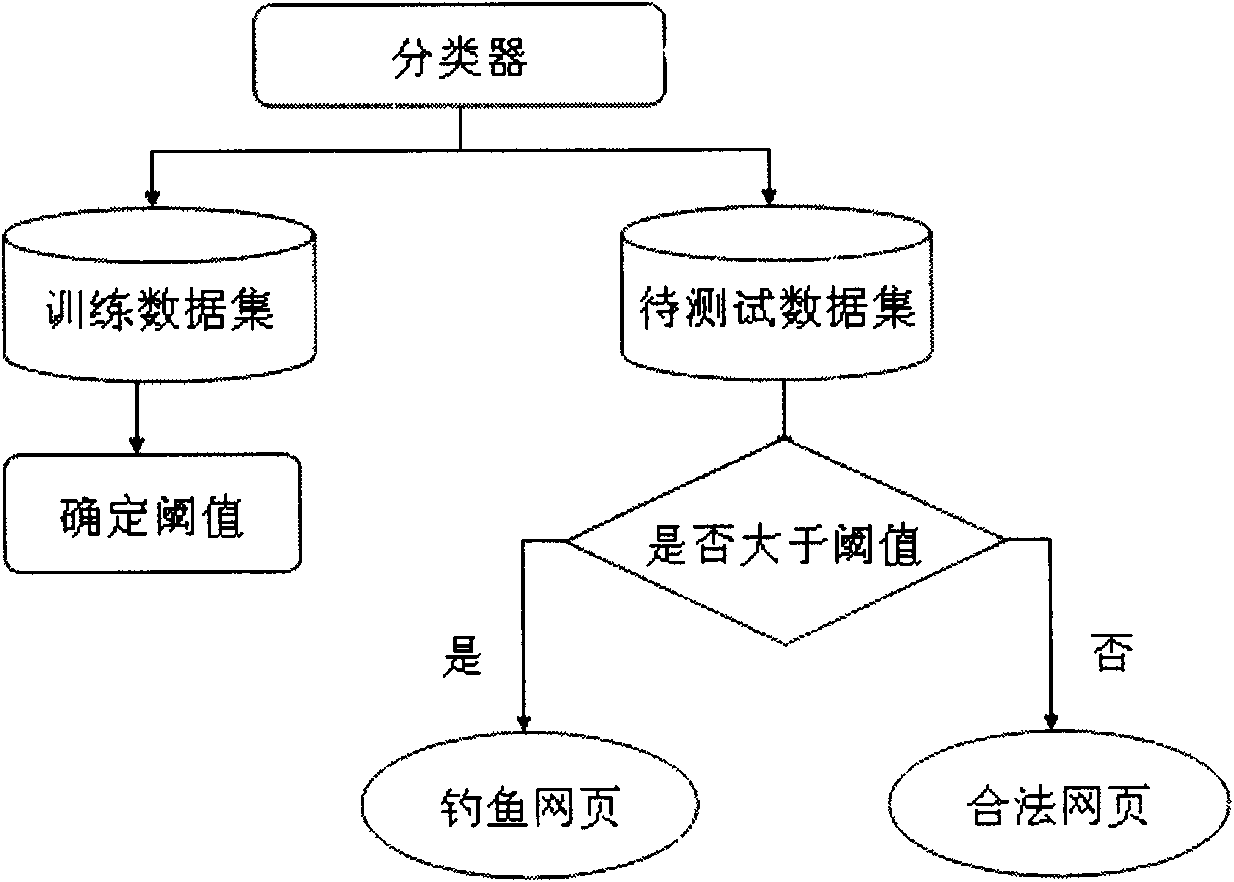
[0027] Step 4) Use machine learning methods to train to obtain a threshold;
[0028] Step 5) After selecting the threshold, predict suspicious web pages.
[0029] The technical scheme of the present invention is specifically divided into thr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com