Credible two-dimensional code system and application method thereof
A two-dimensional code, trusted technology, applied in transmission systems, user identity/authority verification, electrical components, etc., can solve the problem of low cost of two-dimensional code, achieve safe and effective supervision, ensure integrity, and prevent counterfeiting. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
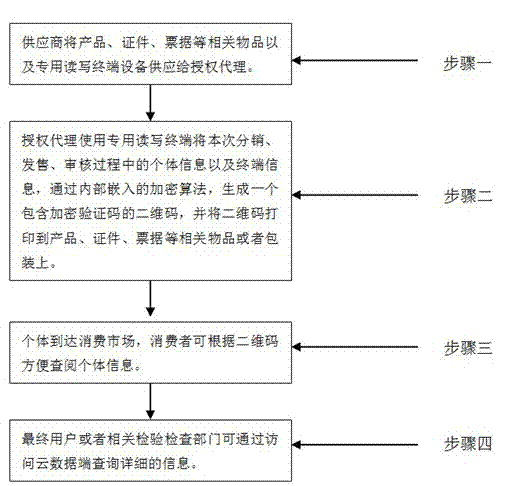
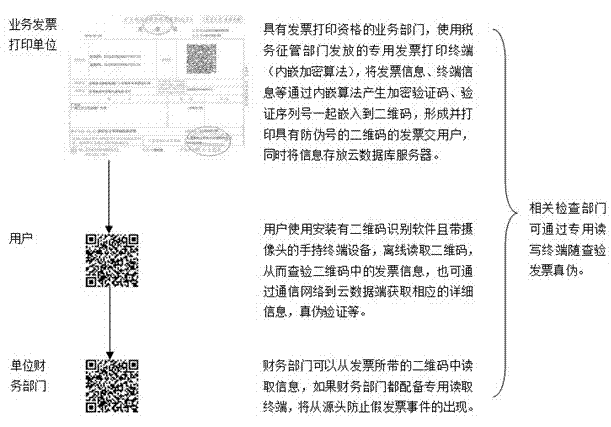
[0040] Hereinafter, the present invention will be further described in detail with reference to the examples and drawings, but the implementation of the present invention is not limited thereto.
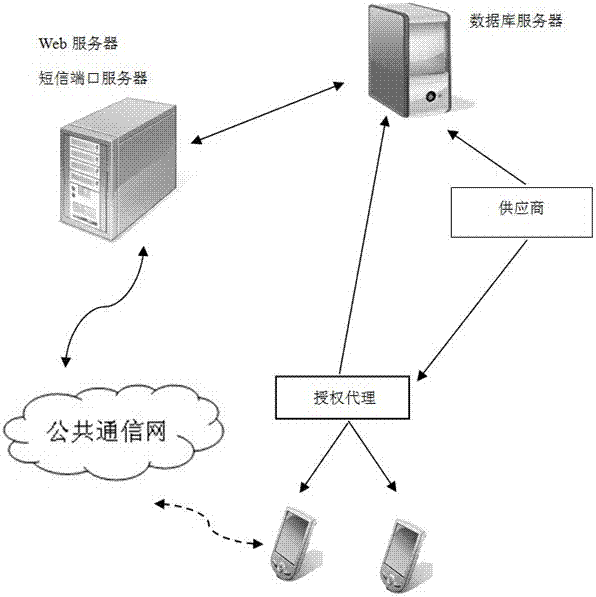
[0041] Figure 1 to Figure 7 The system structure and flow diagram of the trusted two-dimensional code system and its application method of the present invention are shown. The system includes the following parts:
[0042] 1. Cloud data terminal
[0043] The cloud data terminal includes network data servers such as web servers and mobile SMS ports. The database server includes various individual information of products, certificates, and bills. Through these individual information, the end user can understand the important processes and materials of the product production process, certificates, Information such as the validity period of the bill, the unit of use or personal information, the amount, the issuing unit, the receiving unit, and the issuing time. The web server and mobile SMS ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com