Radio frequency identification (RFID) encryption verification system and method
A technology of radio frequency identification and verification method, applied in the field of information security and radio frequency identification encryption and verification system, can solve the problems of increase of electronic label logic and control circuit, increase of chip cost, etc., and achieve the effect of low-cost hardware encryption and decryption algorithm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
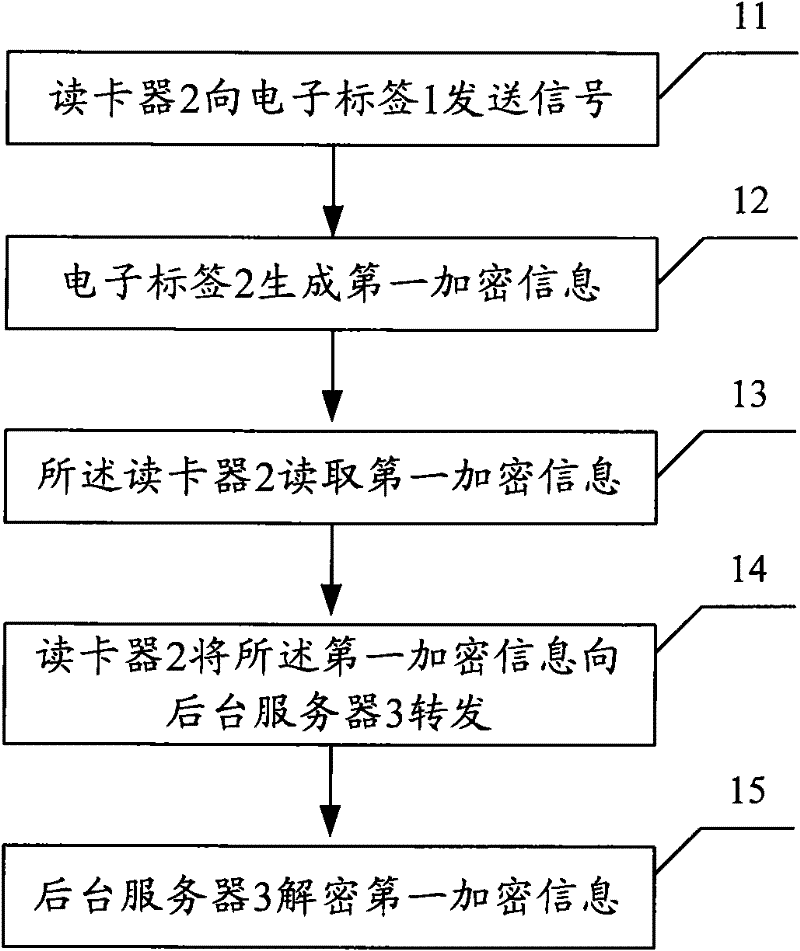
[0060] Embodiment 1 The process of card reader verification electronic label
[0061] The first embodiment is used to illustrate a situation of one-way authentication, that is, the RFID card reader performs one-way authentication on the electronic tag. This embodiment only uses a general public key algorithm to complete the process of identity authentication. According to the computing power and storage space of different chips, many public key schemes such as RSA, ECC, Rabin, ElGamal, etc. may be used.
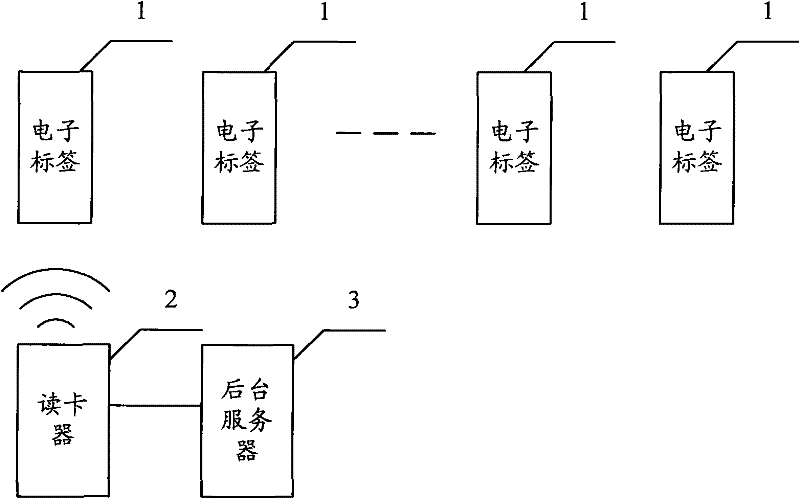
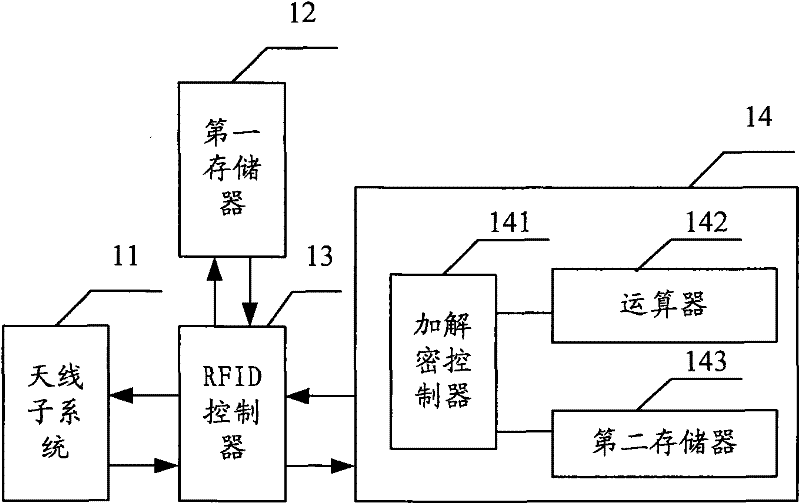
[0062] In the RFID encryption verification system of the present invention, the first memory 13 of the electronic tag 1 stores the private key of the electronic tag 1 and the public key of the card reader 2, and the backend server stores the private key of the card reader 2 And the public key of electronic label 1.
[0063] image 3 Shown is the flow chart of the first embodiment, including:
[0064] Step 11. The card reader 2 sends a signal to the electronic tag 1;
[0065] Step 12....
Embodiment 2
[0076] Embodiment 2 Electronic tag verification card reader process
[0077] The second embodiment is used to illustrate a situation of one-way authentication, that is, the RFID electronic tag performs one-way authentication on the card reader.
[0078] Figure 4 The flow chart of the second embodiment is shown, including:
[0079] Step 21: The card reader 2 sends a signature request to the background server 3;
[0080] Step 22: The backend server 3 generates a random number r2, a timestamp t2, and uses the private key of the card reader 2 to sign hash(r2, t2). The result is S2. Concatenate r2 and t2 to S2 to generate second encrypted information , Namely r2||t2||S2, sent to reader 2;
[0081] Step 23: The card reader 2 sends the second encrypted information to the electronic label 2, and the electronic label 2 reads the second encrypted information;
[0082] Step 24: The electronic tag 2 uses the public key of the card reader 2 to decrypt the second encrypted information and verify the...
Embodiment 3
[0090] Embodiment 3 Two-way verification process of electronic tag and card reader
[0091] Different from the first and second embodiments, the third embodiment is used to illustrate the situation of mutual authentication between the RFID electronic tag 1 and the card reader.
[0092] Figure 5 The flow chart of the third embodiment is shown, including:
[0093] Step 31: The card reader 2 sends a signal to the electronic tag 1;
[0094] Step 32, the second memory 143 of the electronic tag 2 generates a random number r3 and a time stamp t3, the encryption and decryption controller 141 of the electronic tag 2 reads the private key of the electronic tag 2 in the first memory 13, and the arithmetic unit 142 uses the electronic tag The private key of 2 signs hash(r3, t3), and the result is S3. The r3 and t3 are cascaded to S3 to generate the third encrypted information, namely r3||t3||S3;
[0095] Step 33: The card reader 2 reads the third encrypted information;
[0096] Step 34: The card ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com