Data isolation method used in storage cloud
A technology for data isolation and cloud storage, which is applied in digital data protection, electronic digital data processing, instruments, etc., and can solve problems such as inability to access data beyond authority and inability to share data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
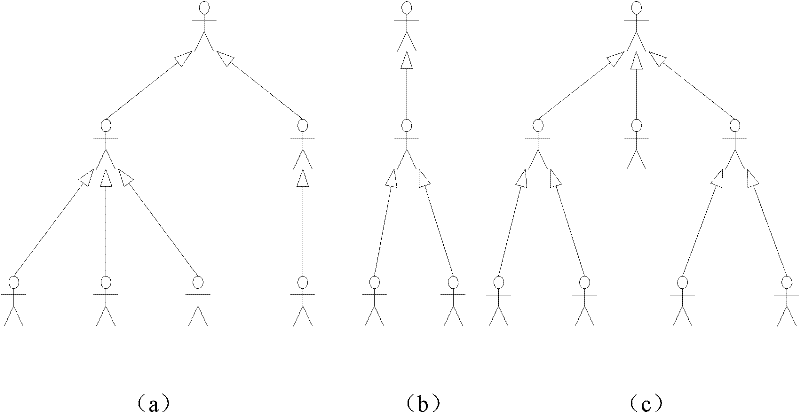
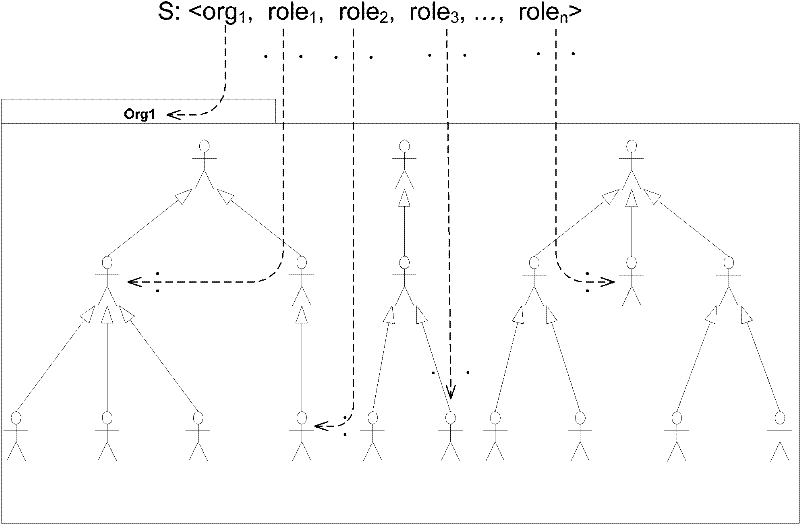
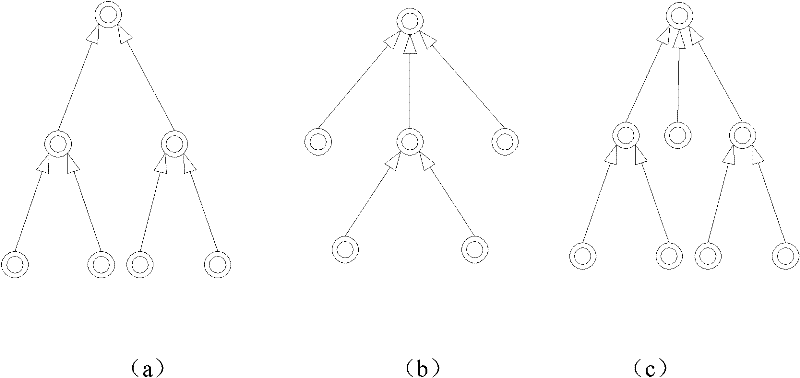
[0137] The invention develops a security mechanism for data isolation based on the Hadoop distributed file system (HDFS). Distributed file systems are widely used as the underlying infrastructure of cloud storage, and the underlying use of commercial cloud storage Cloudera is HDFS. The use of open source HDFS to develop a prototype of the security mechanism is conducive to the evaluation of the effect of the entire system.
[0138] Figure 5 Depicts the security architecture design based on HDFS architecture.
[0139] The core of the prototype system is the safety decision module. In order to determine whether the subject has permission to access the resource object, the security decision-making module needs to first obtain the information of the security label of the subject and object and the security policy of the current system. In HDFS, the meta-information of the file system is stored on the Namenode side of the master node, so security meta-information such as securi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com