Resource authorization method and system
A technology of resources and resource information, applied in the field of resource authorization methods and systems, which can solve problems such as rough architecture
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
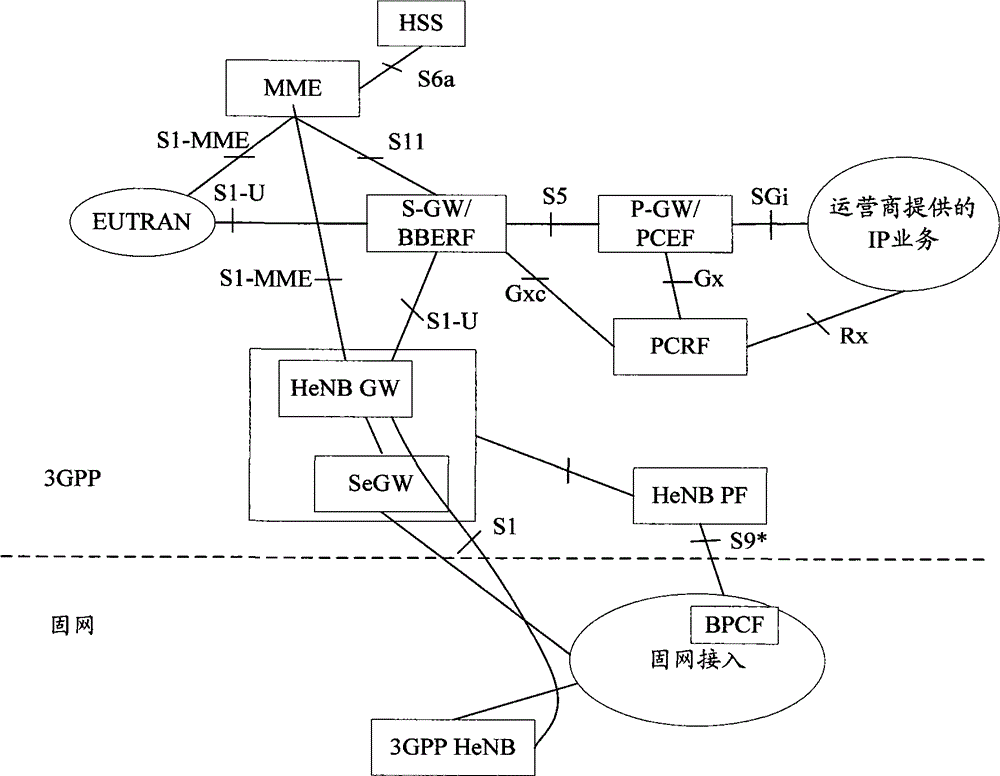
[0119] Figure 5 It is a flowchart of H(e)NB reporting IPSec tunnel information in the method of the present invention, and is applicable to EPS system or 3G system. exist Figure 4 In the technical solution shown, the step 1 includes:
[0120] Step 11. The H(e)NB is powered on and connected to the fixed network. The fixed network assigns a local IP address to the H(e)NB through relevant mechanisms, and this address is used as the subsequent IPSec tunnel encapsulation between the H(e)NB and the SeGW. The external IP address of the packet.
[0121] Step 12, the H(e)NB establishes an IPsec tunnel with the SeGW to ensure the security and integrity of data during transmission.
[0122] Step 13: The SeGW reports the tunnel information of the IPsec tunnel and the H(e)NB identification information to the H(e)NB PF through the interface T1.
[0123] Step 14, the H(e)NB PF saves the tunnel information and the H(e)NB identification information.
[0124] In this embodiment, the SeGW...
no. 2 example
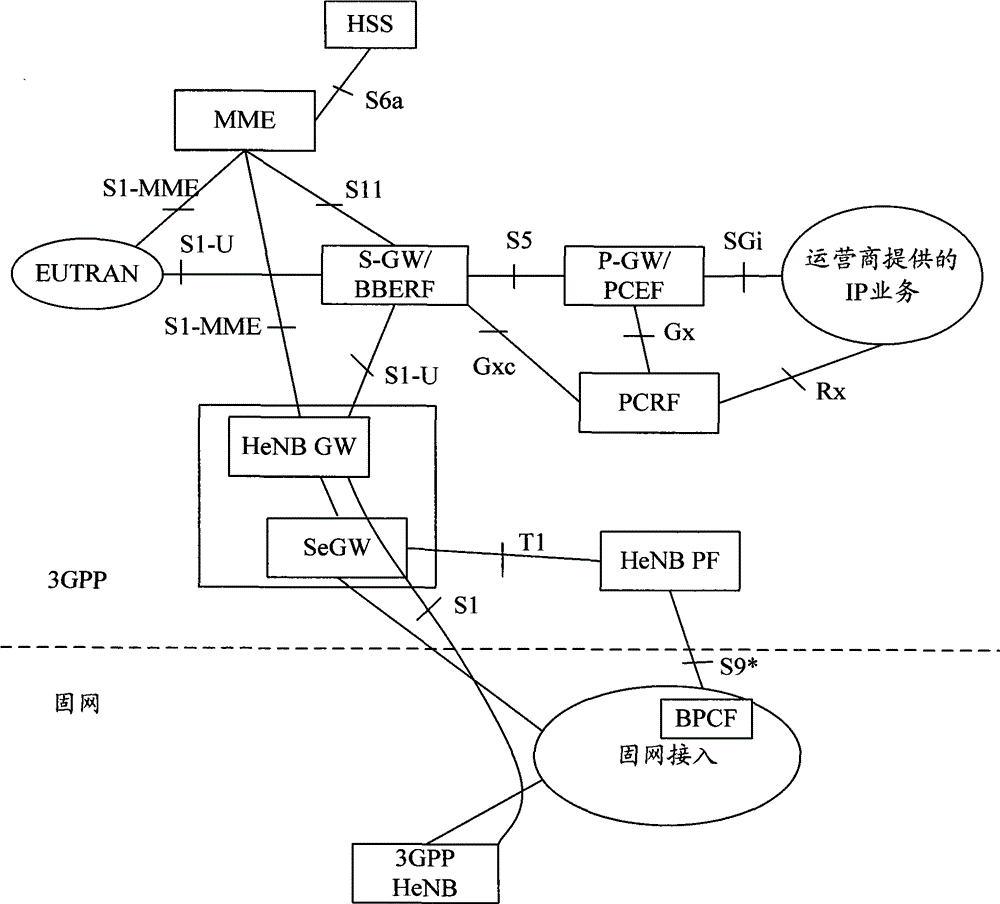
[0128] In this example, Figure 4 Step 1 in the shown technical solution includes:
[0129] Step 11. The H(e)NB is powered on and connected to the fixed network. The fixed network assigns a local IP address to the H(e)NB through relevant mechanisms, and this address is used as the subsequent IPSec tunnel encapsulation between the H(e)NB and the SeGW. The external IP address of the packet.
[0130] Step 12, the H(e)NB establishes an IPsec tunnel with the SeGW to ensure the security and integrity of data during transmission.
[0131] The difference from the first embodiment is that the H(e)NB identification information in this embodiment is brought to the H(e)NB PF when the SeGW sends a resource authorization, resource modification or resource release request message in subsequent procedures.
no. 3 example
[0133] Image 6 is a flow chart of sending a resource authorization or resource modification message in the method of the present invention, in Figure 4 In the technical solution shown, the step 2 includes:
[0134] Step 211, the core network is triggered to initiate a resource authorization or resource modification process.
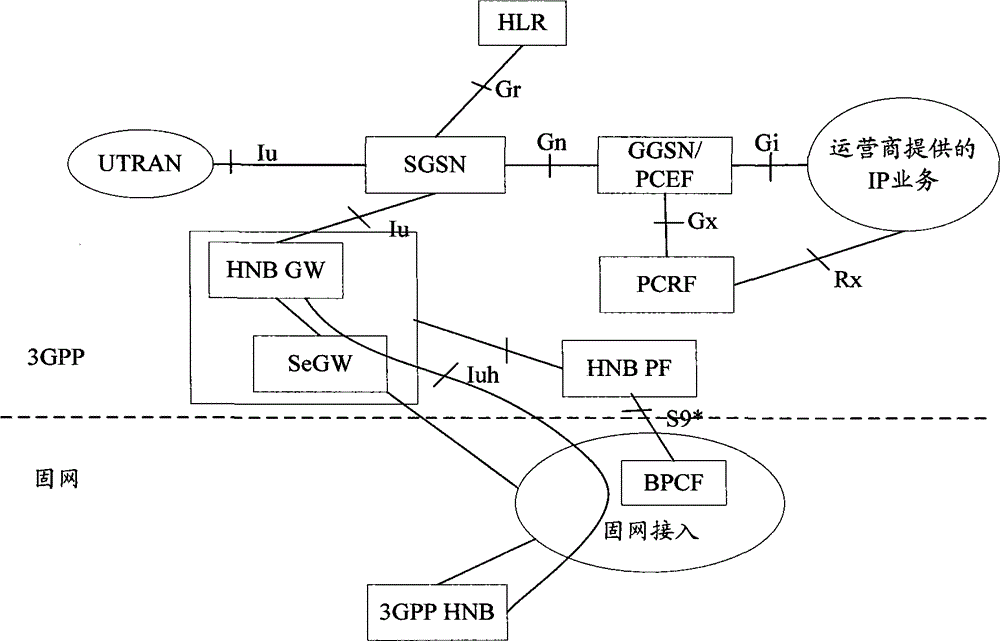
[0135] In the technical solution of the present application, the core network is an EPS network or a 3G network. For resource authorization or resource modification, the triggers on the core network include but are not limited to the following situations: the default bearer establishment process in the EPS network attachment process, the default bearer establishment process in the EPS network terminal request to create a PDN connection, and the dedicated bearer activation process in the EPS network , Bearer modification process in EPS network, PDP context activation process in 3G network, PDP context secondary activation process in 3G network, PDP con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com