Method and device for filtering network attack traffic
A network attack and network traffic technology, applied in the field of network security, can solve the problems of reducing and filtering abnormal traffic, difficult to reflect the real boundary between normal traffic and abnormal traffic, and easy mutation, etc., to achieve the effect of filtering attack traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
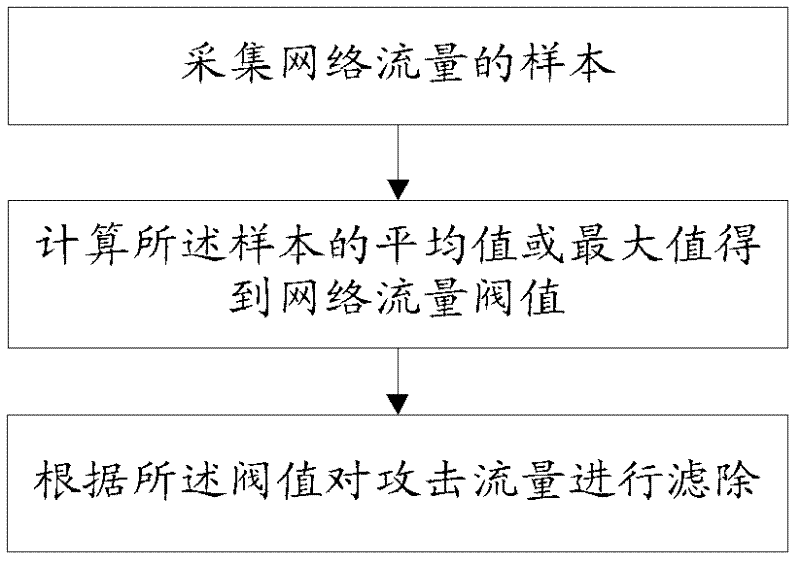
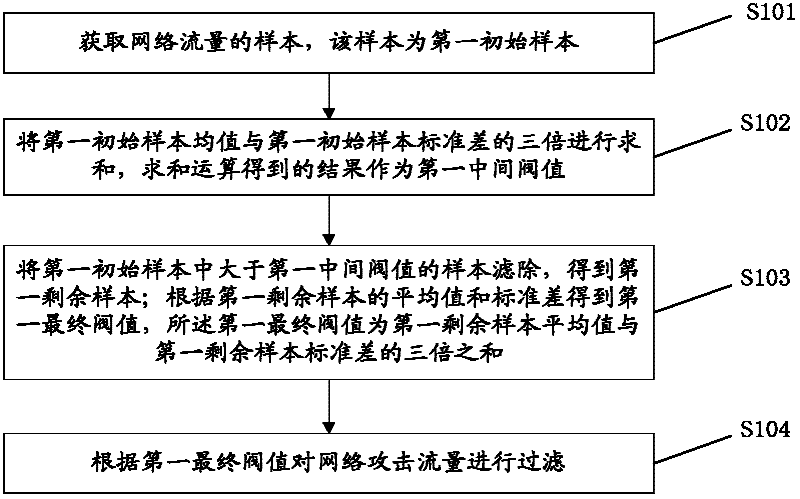
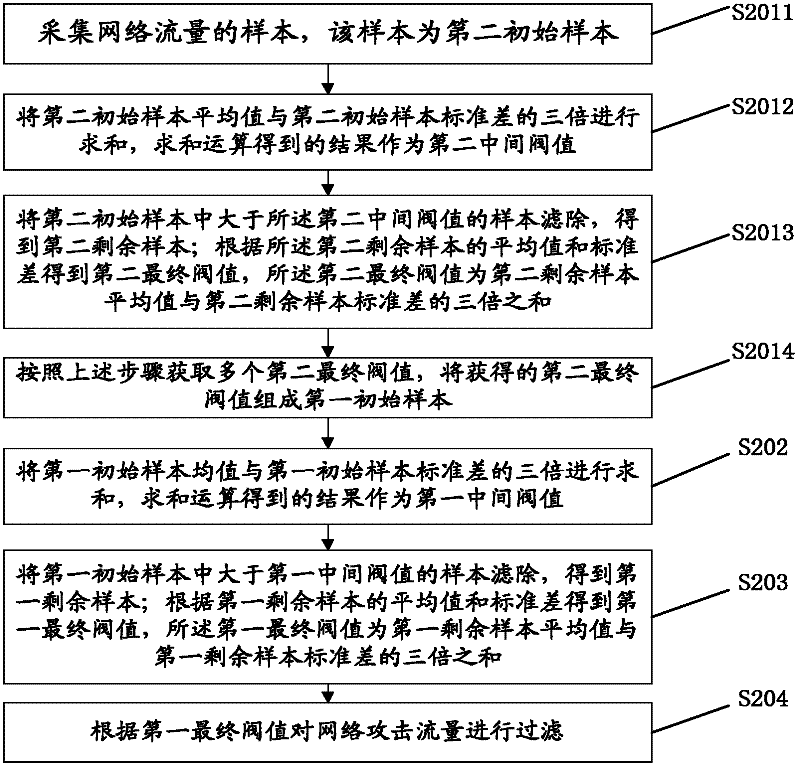
[0036] The main idea of the present invention is: after obtaining the samples of the network traffic, first perform data screening on the obtained sample space so as to filter out those sample values that obviously represent the attack traffic, and then use the normal distribution on the basis of the processed samples to Calculate the final threshold according to the law, and then filter the network attack traffic according to the final threshold, so as to realize the purpose of the present invention.
[0037] In order to enable those skilled in the art to further understand the features and technical content of the present invention, the technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0038] As mentioned earlier, network security issues are increasingly becoming a focus of attention. The so-called network security refers to the information security of the network, including the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com