Method and device for monitoring E-mail user behaviors
A technology of e-mail and e-mail protocol, which is applied in the field of transformation and optimization of standard e-mail protocol. It can solve the problems of e-mail attack, password attack without defense means, and error cannot guarantee the login user, etc., so as to reduce time and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
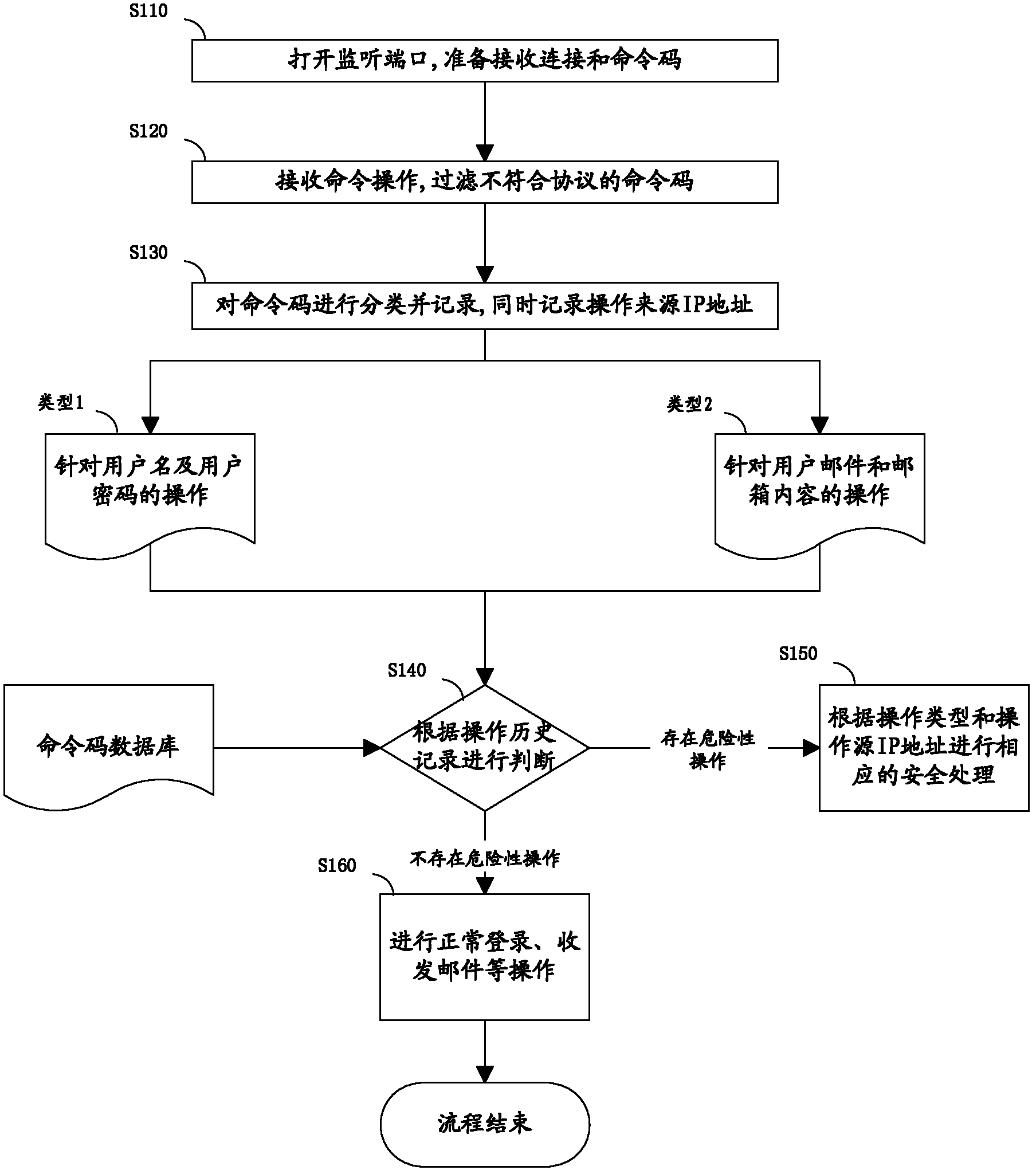
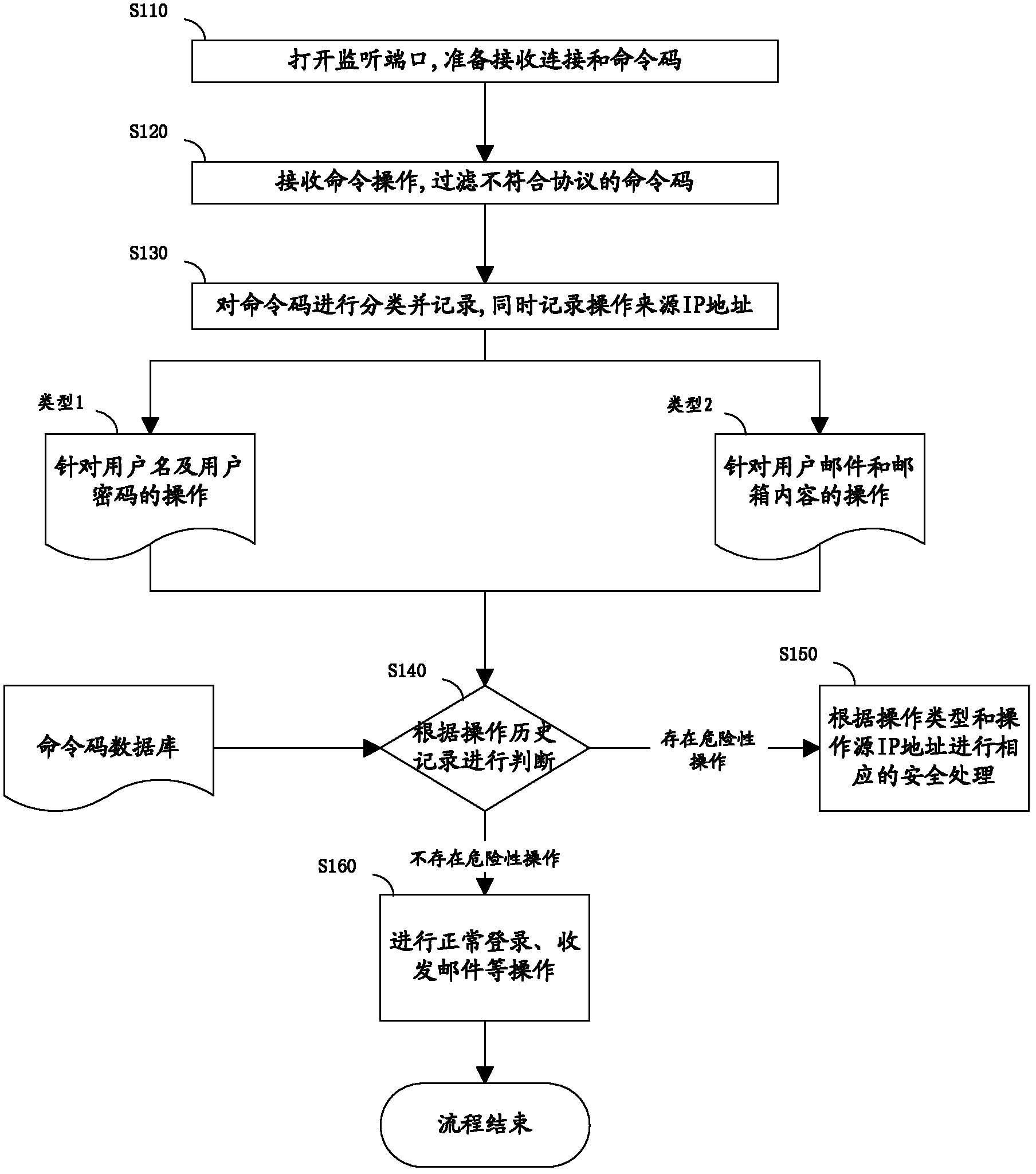
[0040] figure 1 It is a flow chart of the method for monitoring email user behavior according to Embodiment 1 of the present invention, and the direction of the arrow indicates the operation flow for realizing the method. Refer below figure 1 Each step of the method is described in detail.
[0041] Step S110, open the listening port, and prepare to receive the user's connection and command code.
[0042] The email server will open the listening port, ready to receive the user's connection and the user's email-related operation information (hereinafter referred to as operation), and analyze the command code in the user's operation, the user's operation includes login request or operation request .
[0043] Step S120, receiving command codes, and filtering command codes that do not conform to the protocol.
[0044] Receive the user's operation, obtain the command code in the operation, filter out the command code that does not meet the specification according to the standard...
Embodiment 2
[0092] figure 2 It is a schematic structural diagram of an e-mail user behavior monitoring device according to Embodiment 2 of the present invention, according to the following figure 2 Describe in detail the composition of the device.
[0093] The device mainly includes the following modules:
[0094] The command code receiving module is used for receiving the command codes related to the operation of the email user, and filtering the command codes that do not conform to the email protocol. This module is used to receive the user's operation, obtain the command code in the operation, filter out the command code that does not meet the specification according to the standard mail protocol, and receive the command code that meets the protocol specification. Specifically, according to the standard SMTP, POP3, and IMAP protocols, first filter the command codes obtained by the server monitoring port, discard those that do not meet the protocol specifications, and contin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com