Method and system for controlling access right of internet users
A technology of access rights and control methods, which is applied in transmission systems, electrical components, etc., can solve the problems of inability to realize fine control of user rights, coarse access rights, and inability of user terminals to access resources, etc., to achieve safe and convenient access methods, Realize the effect of fine control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to describe the technical content, achieved objectives and effects of the present invention in detail, the following will be described in detail in conjunction with the implementation methods and accompanying drawings.
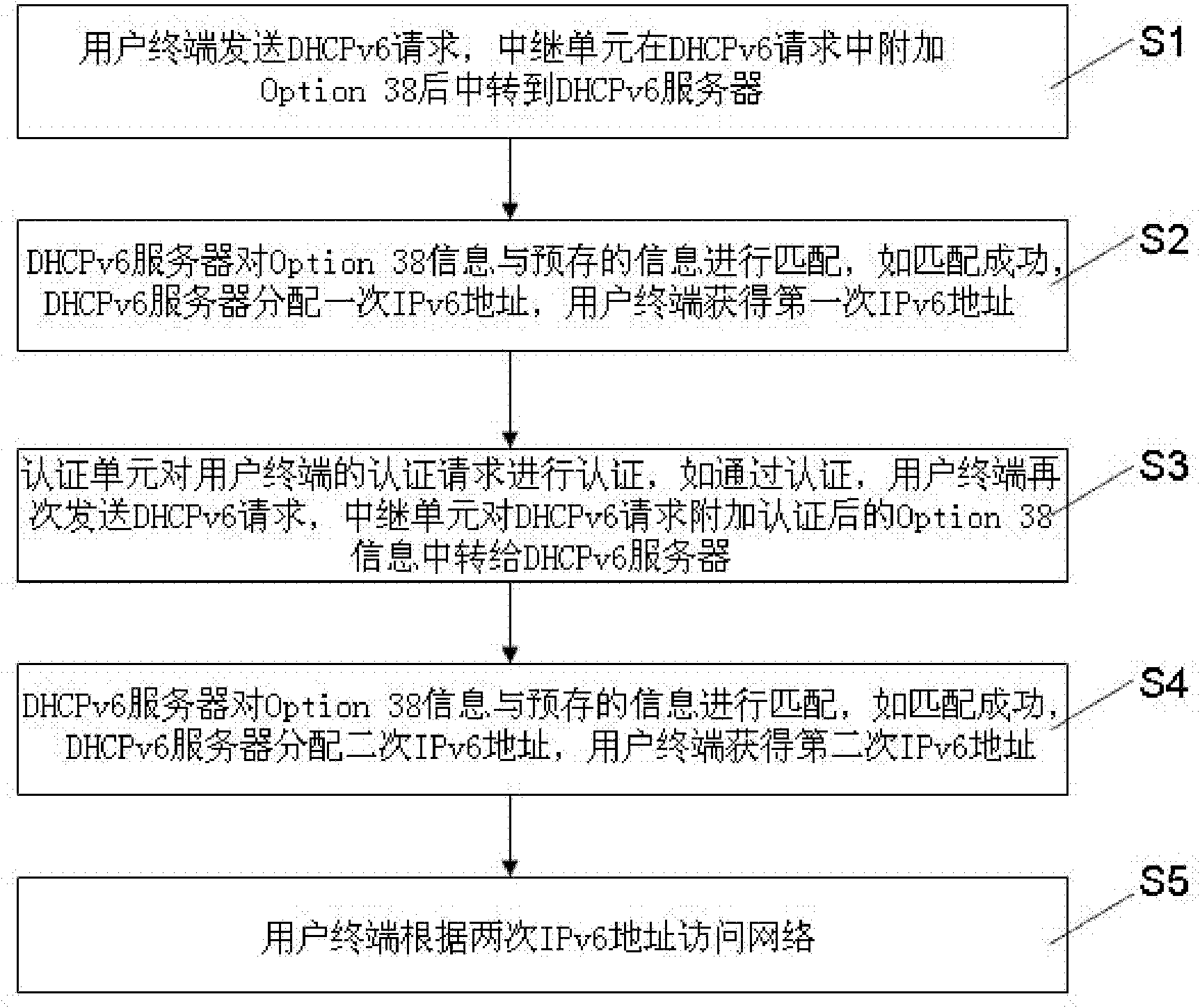
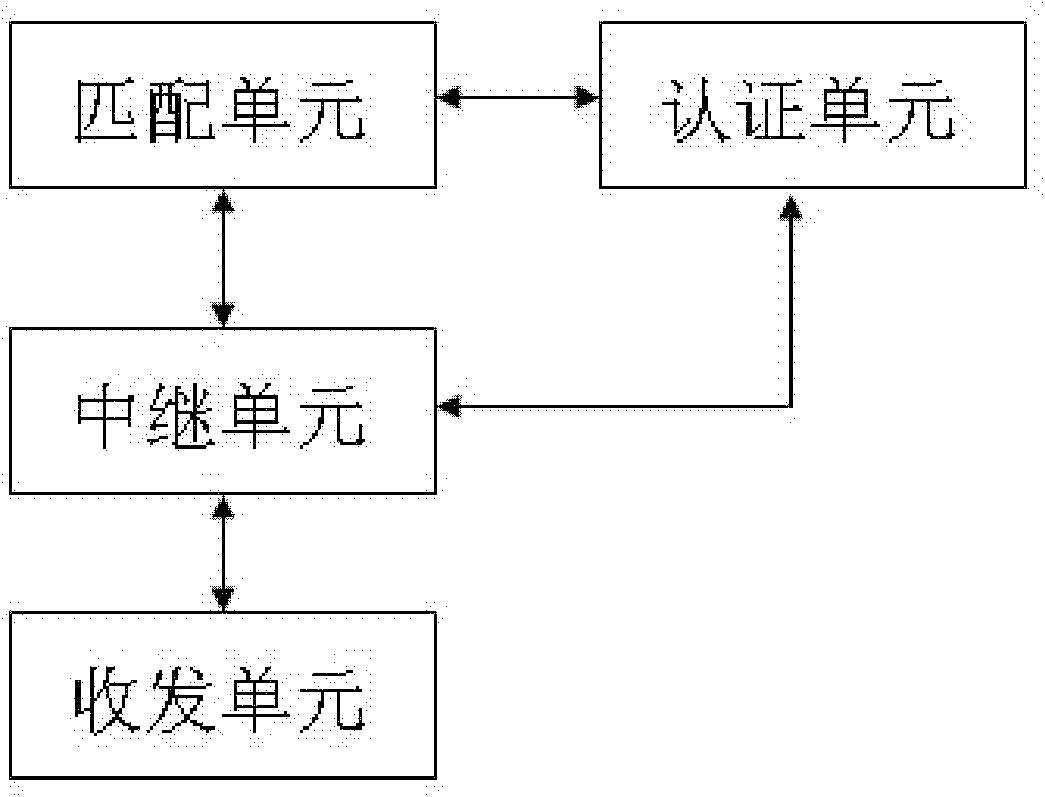
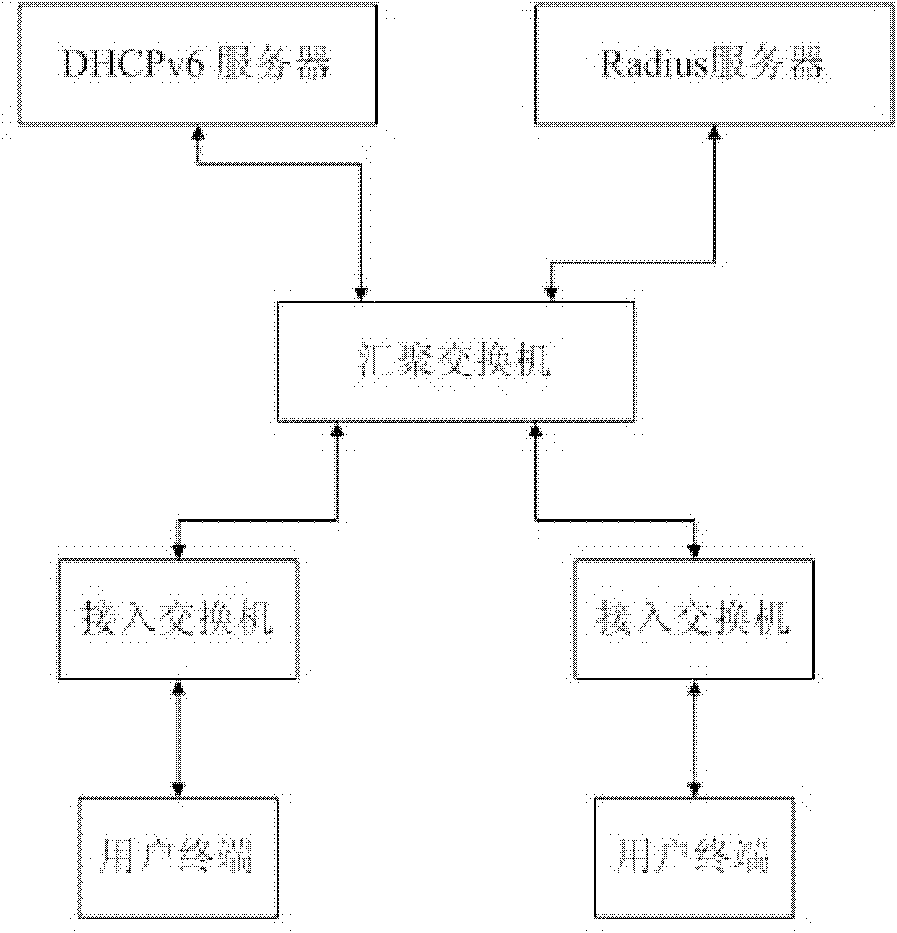
[0030]The technical principle of the present invention: the present invention utilizes the DHCPv6 Snooping module to add Option 38 information when monitoring the DHCP v6 request of the user terminal, and when the user terminal obtains the address successfully and passes the authentication, the Radius server sends the Option 38 of the user through a message Authentication information. After the user terminal is successfully authenticated, the 802.1x module re-applies for an address. The DHCPv6 Snooping module adds the authenticated Option 38 information to the DHCPv6 request. The DHCPv6 server assigns another address to the user according to the authenticated Option 38 information. Layer switches are configured with hardware ACL entries, which l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com