Security defense and abnormity detection method, device and system based on MQTT message queue
A detection method and message queue technology, applied in transmission systems, electrical components, etc., can solve problems such as low security performance, low security defense capabilities, and low abnormal behavior detection capabilities, so as to prevent leakage and theft, and avoid potential safety hazards , the effect of fine control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
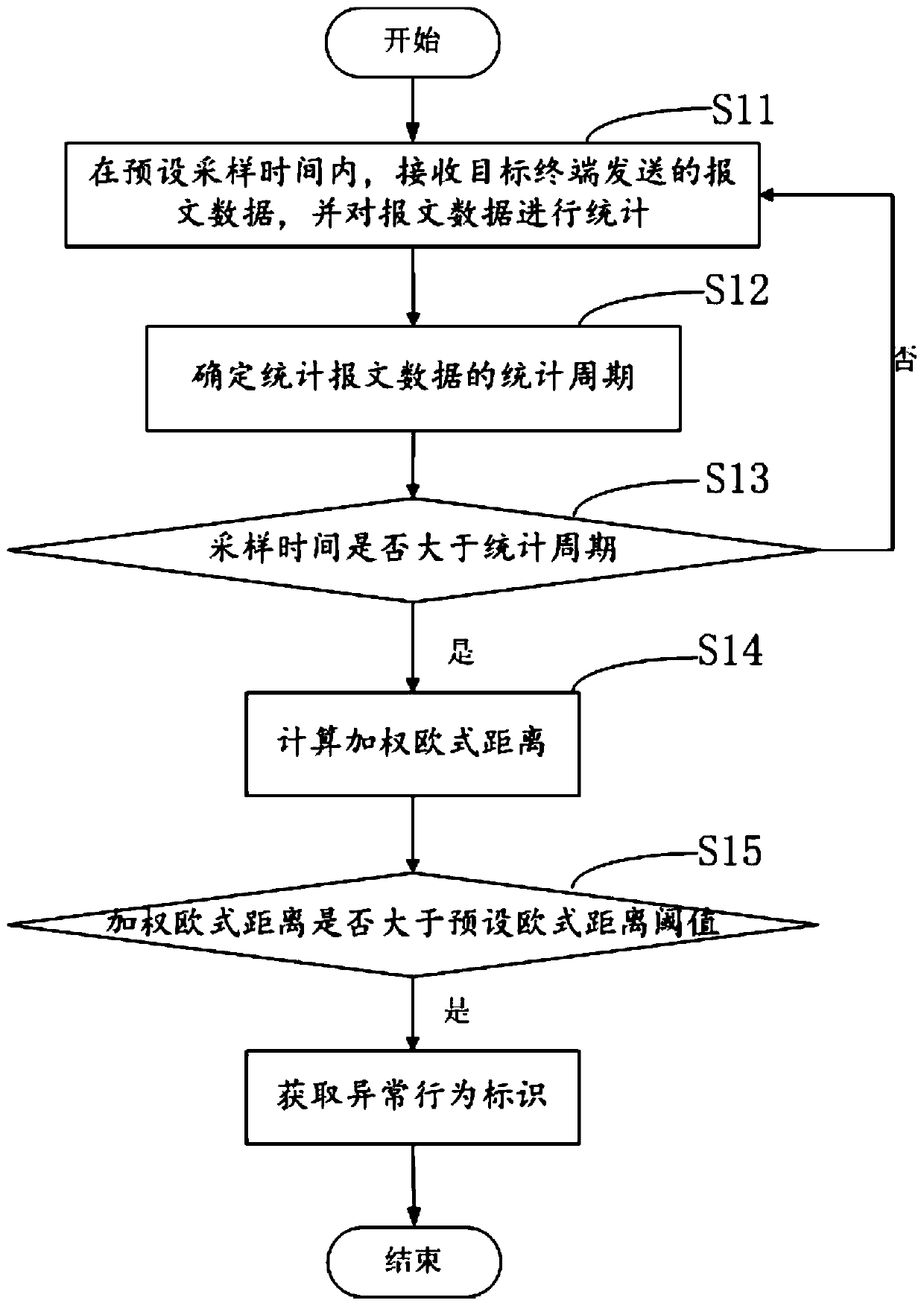
[0073] In order to more clearly illustrate the process and advantages of the inventive method of this embodiment, the present invention provides a method for detecting abnormal behavior based on MQTT message queues.
[0074] figure 1 It is a schematic flowchart of a method for detecting abnormal behavior based on MQTT message queue provided by the embodiment of the present invention.
[0075] see figure 1 The abnormal behavior detection method based on the MQTT message queue provided by the embodiment of the present invention may include the following steps:
[0076] S11. Receive the message data sent by the target terminal within the preset sampling time, and make statistics on the message data.
[0077] Specifically, the target terminal here refers to various embedded terminal devices in the Internet of Things, and the MQTT client program is implemented on these terminal devices.
[0078] According to the requirement, a certain sampling time is preset, and the sampling ti...
Embodiment 2
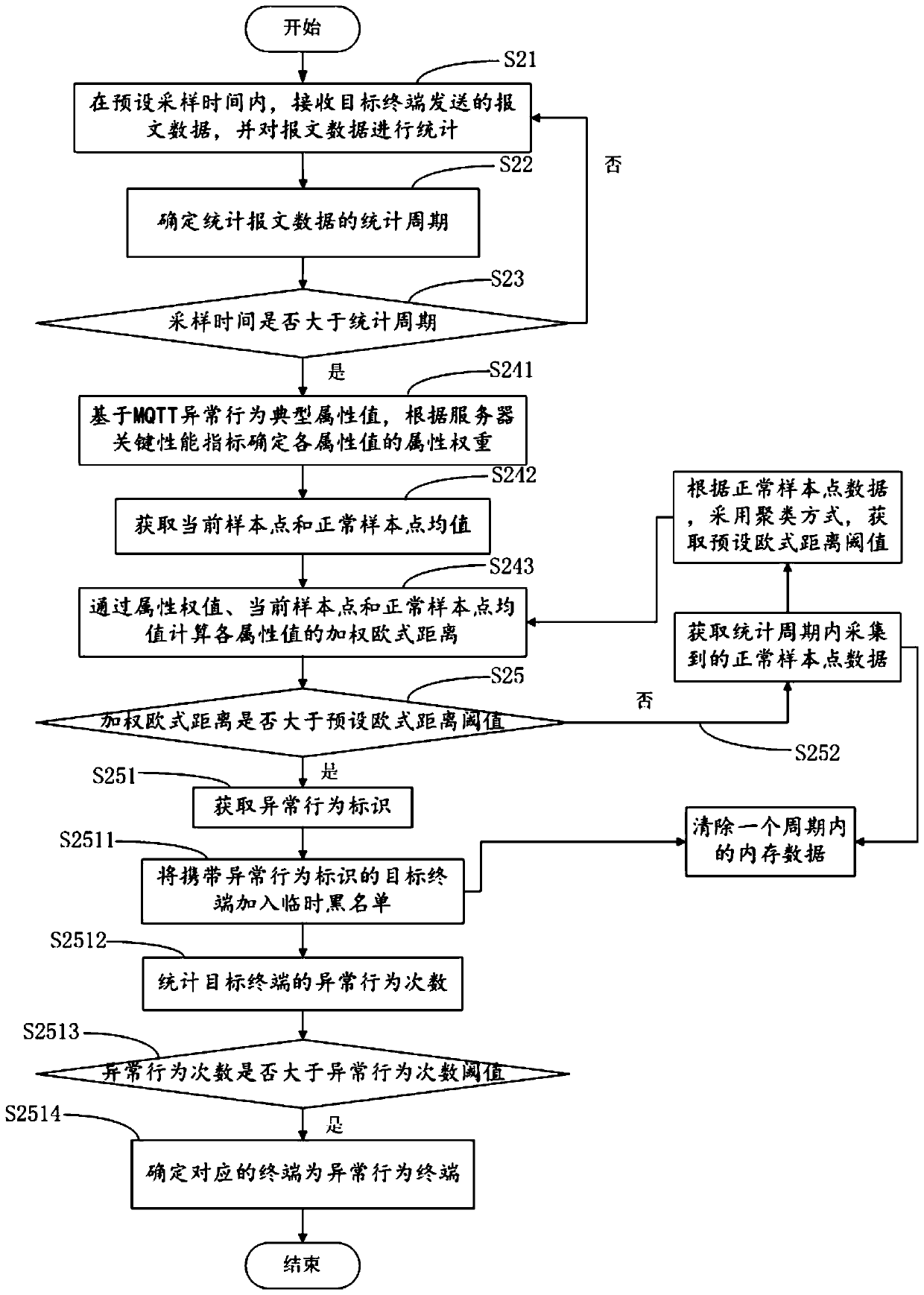
[0093] In order to further explain the abnormal behavior detection method based on the MQTT message queue provided by the embodiment of the present invention, the present invention also provides another embodiment.
[0094] figure 2 It is a schematic flowchart of another abnormal behavior detection method based on MQTT message queue provided by the embodiment of the present invention.
[0095] see figure 2 On the basis of the foregoing embodiments, another method for detecting abnormal behaviors based on MQTT message queues provided by the present invention may include the following steps:
[0096] S21. Receive the message data sent by the target terminal within the preset sampling time, and make statistics on the message data.
[0097] S22. Determine a statistical period for statistical packet data.
[0098] S23. Determine whether the sampling time is greater than the statistical period.
[0099] Wherein, steps S21-S23 are the same as steps S11-S13 in the above-mentione...
Embodiment 3
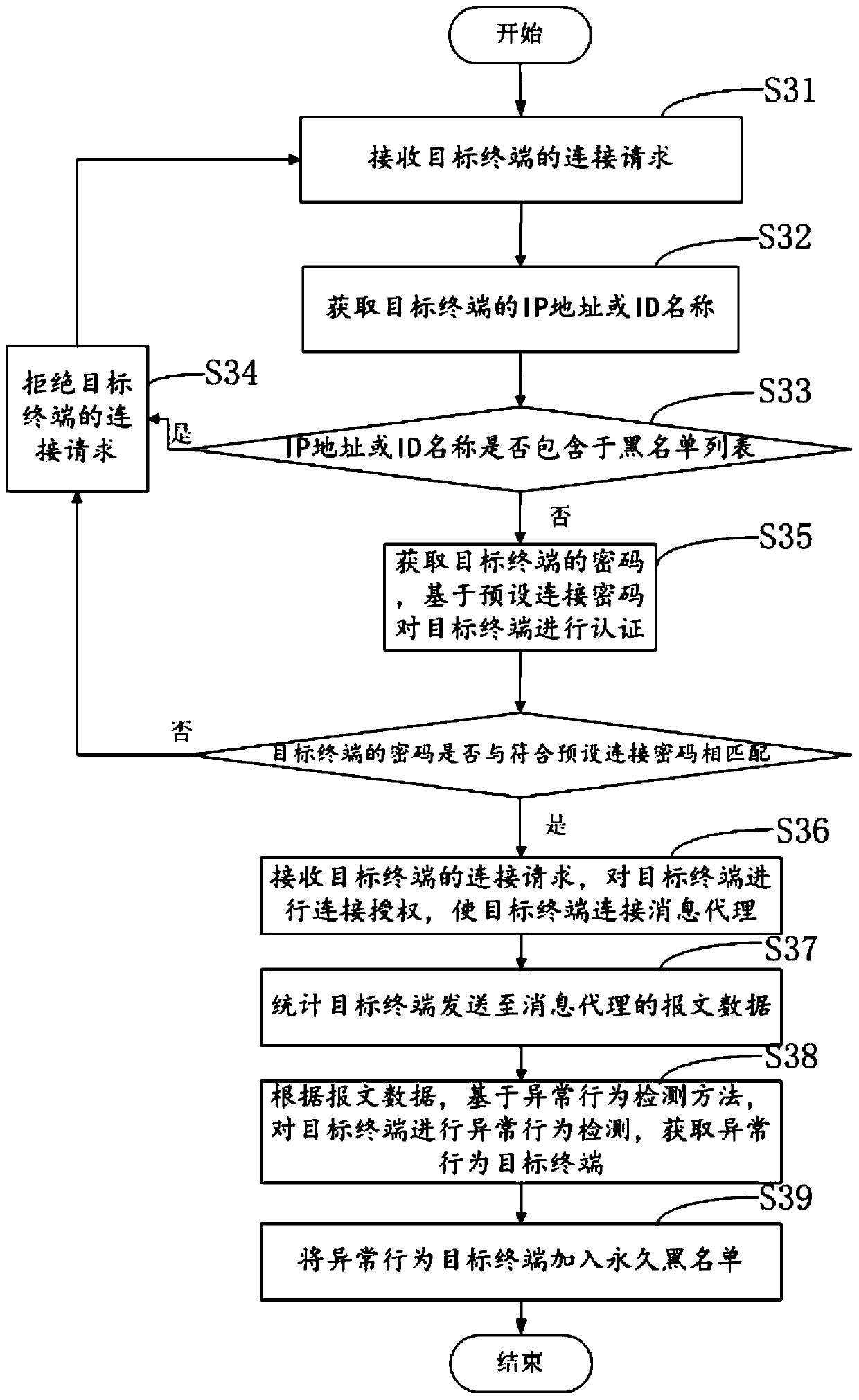
[0123] In order to more clearly illustrate the process and advantages of the inventive method of this embodiment, the present invention provides an MQTT message queue-based security defense method.
[0124] image 3 It is a schematic flowchart of an MQTT message queue-based security defense method provided by an embodiment of the present invention.
[0125] see image 3 A security defense method based on an MQTT message queue provided in an embodiment of the present invention may include the following steps:
[0126] S31. Receive a connection request from a target terminal.
[0127] The target terminal of the access must implement the MQTT client program, the device terminal establishes a connection with the MQTT message broker through TCP, and uses the TLS encryption mechanism between the transport layer and the application layer to realize a secure socket.
[0128] Specifically, the access terminal implements the MQTT client program, the terminal implements the FreeRTOS r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com