Distributed control method for information of accessing internet of things by user
An access control and access object technology, applied in the field of communications, can solve the problems of inefficient authority management, low efficiency, and difficult control, and achieve the effects of efficient authority management, less energy consumption, and improved efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
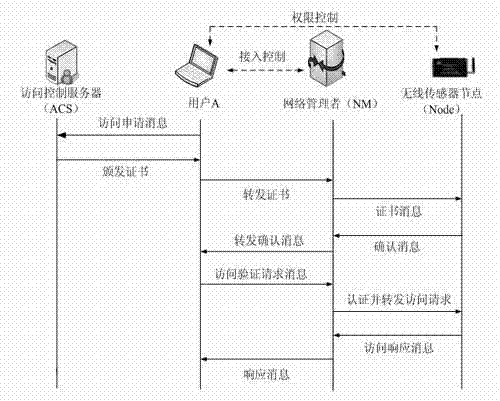
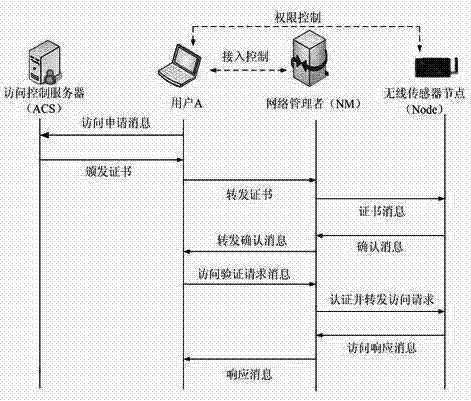
[0023] In this embodiment, the authentication system based on public and private keys in the content of the present invention is used to complete the authentication between entities other than nodes and the encryption of transmitted data. The nodes in the present invention are used to control the user's access to the network. Inter-authority delegation completes the change of user authority, and handles the threat of user unauthorized access through the network management center.
[0024] Assume that before the user applies for access, the access control server has shared their public keys with the network management center, and the network management center and wireless sensor nodes have established the keys needed to ensure the security of the wireless sensor network. The method specifically includes:
[0025]In the access authorization stage, the user applies to the access control server to access network resources, and the access control server issues access certificates t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com