End-to-end speech encryption method for low-speed narrowband wireless digital communication
A voice encryption, digital communication system technology, applied in the field of digital mobile communication systems, can solve the problems of low communication rate, voice quality degradation, affecting user experience, etc., to ensure continuity, improve synchronization efficiency, and avoid voice interruption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
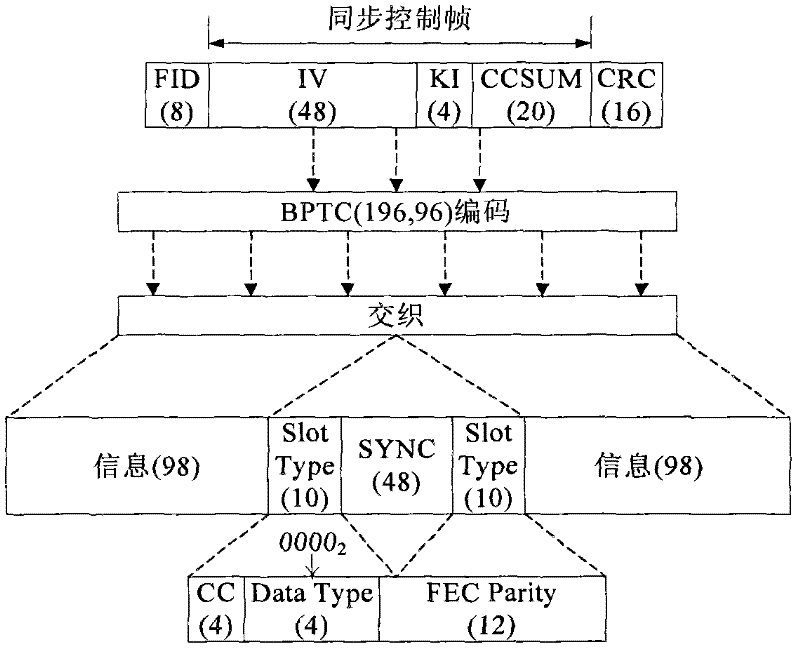
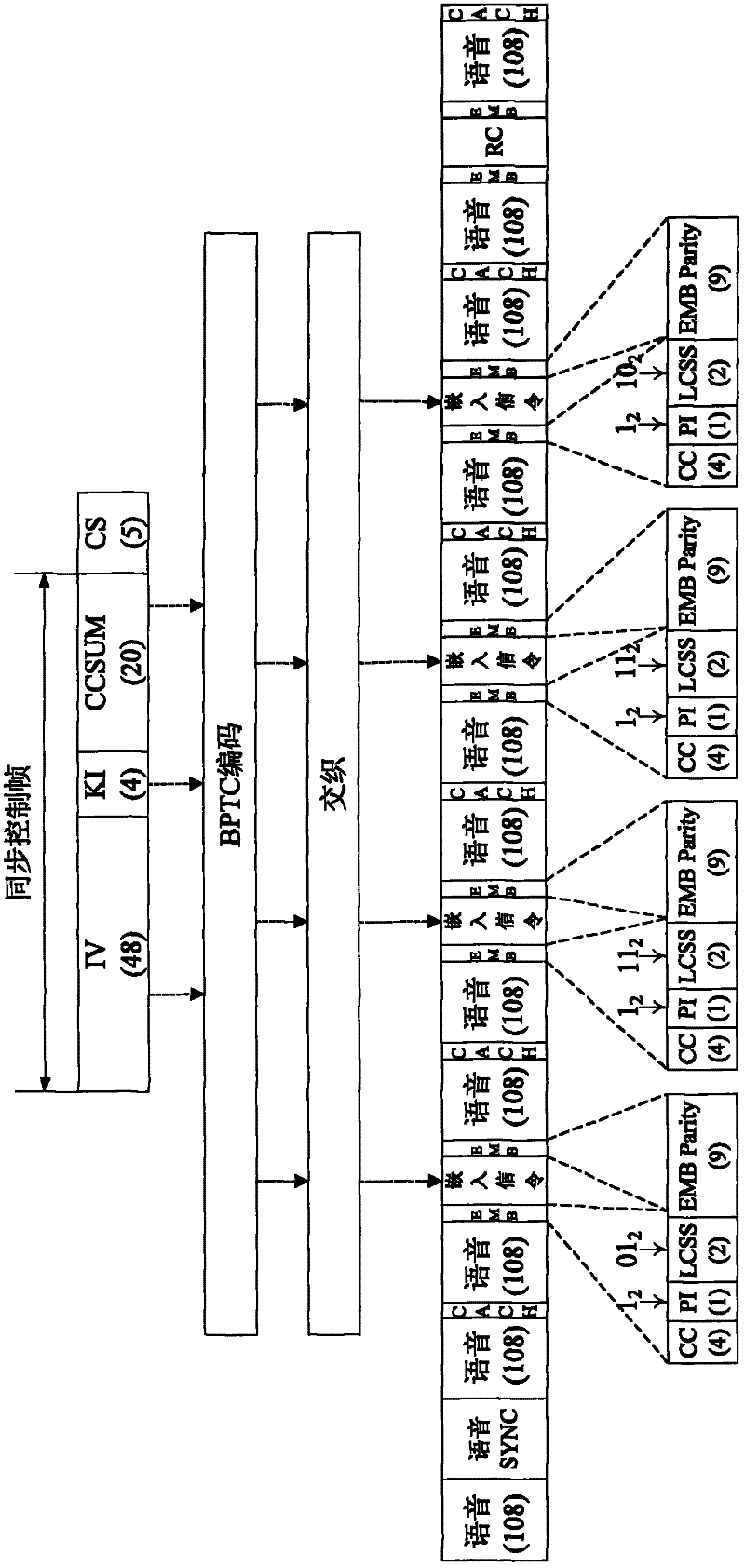
[0044] Embodiment 1: The present invention relates to an end-to-end voice encryption method suitable for low-speed narrowband wireless communication systems, and can be applied to digital mobile communication systems of various systems. Here, the DMR digital trunking system is taken as an example for illustration.
[0045] 1) End-to-end encrypted speech coding scheme
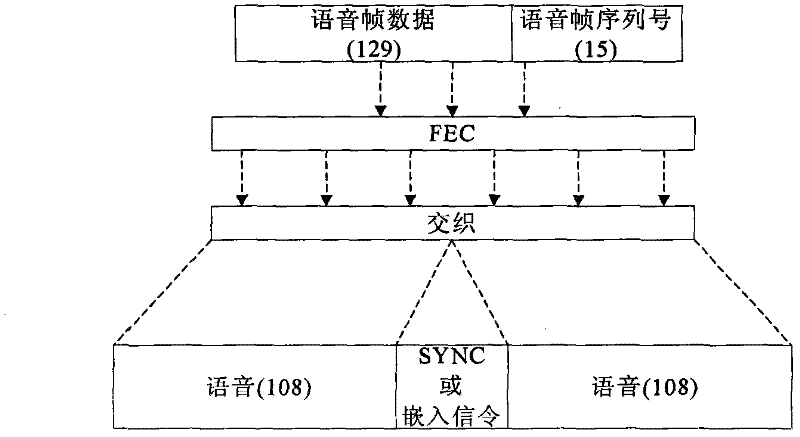
[0046] When communicating in plain language, the DMR system uses a voice coding algorithm with a code rate of 2.4Kbps. When using end-to-end voice encryption, in order to transmit the voice frame sequence number, the present invention needs to occupy 15 bits in the 60ms voice frame. In this way, the data length after 60ms speech encoding needs to be shortened to 129bits, that is, the actual speech encoding rate is reduced to 2.15Kbps when end-to-end encryption is adopted. Speech frame structure for end-to-end encryption, such as figure 1 shown.
[0047] The 15bit voice frame sequence number can support a cal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com