Method for finding landing page from phishing page
A technology for phishing web pages and finding targets, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
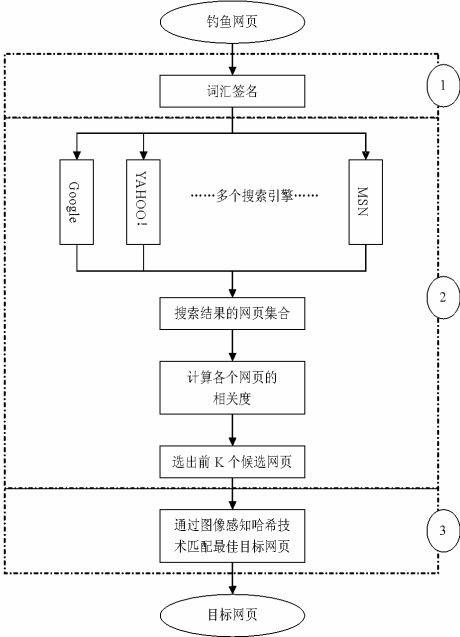
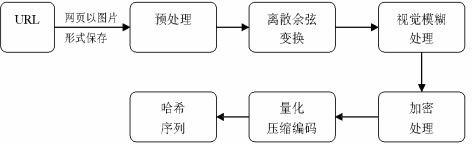
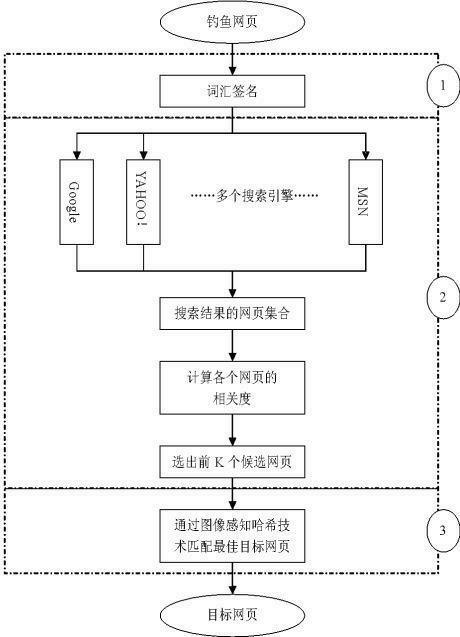
[0054] The purpose of the present invention is to provide a method for finding target webpages from phishing webpages. First, keywords are extracted from known phishing webpages to form a vocabulary signature; According to the results of the engine, select the most relevant ones as candidate webpages; then save the candidate webpages in the form of pictures, extract the image perception hash sequence, and calculate the Hamming distance between these webpage pictures and the phishing webpage pictures, according to the size of the distance One or more target web pages of the phishing web page may be selected.
[0055] The method by which a phishing page finds its target page requires the following steps:
[0056] Step 1) Extract the text from the webpage title, the main body and the webpage image respectively, synthesize these words, and then calculate the word frequency-inverse document frequency TF-IDF value of these words, and form a vocabulary signature from the top 5 words ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com