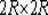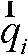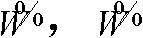Anti-attack robustness multiple zero watermark method
A zero-watermark, anti-attack technology, applied in the field of information security, can solve the problem of little research on zero-watermark, and achieve the effect of enhancing the performance against various attacks and improving reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In the process of constructing multiple zero watermarks, Harris corner detection is first performed on the image after translation and zoom invariant normalization to obtain a feature area with a radius of R; then the zero padding operation is used to map the feature domain to a size of 2R ×2R image blocks, calculate the Zernike moment magnitude of each feature block and construct feature vectors, and binarize these feature vectors to form multiple zero watermarks; finally encrypt multiple zero watermarks to enhance the zero watermark scheme The security, the encrypted multi-fold zero watermark is stored in the registration center as the basis for copyright judgment. The construction process of multiple zero watermark is as follows: figure 1 shown.
[0037] In the process of multiple zero-watermark detection, similar to the process of multiple zero-watermark construction, firstly, the Harris corner detection and zero-padding operation are performed on the detection im...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com