Mixed structured query language (SQL) injection protection method
A security protection and syntax tree technology, which is applied in special data processing applications, instruments, electrical digital data processing, etc., to achieve performance improvement, increase accuracy, and avoid accuracy and false alarm rates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
[0067] (1) select * from a where username = ‘chenfeng’ and passwd = 123;
[0068] (2) select * from USER_CATALOG where name = ‘chen’or 1=1;
[0069] (3) select * from person where age = 24 and name = ‘li’ and 1=1;
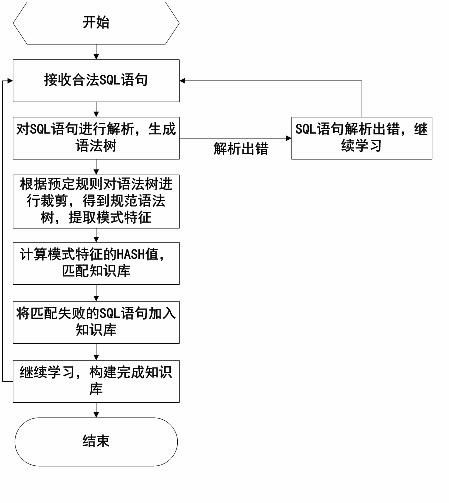
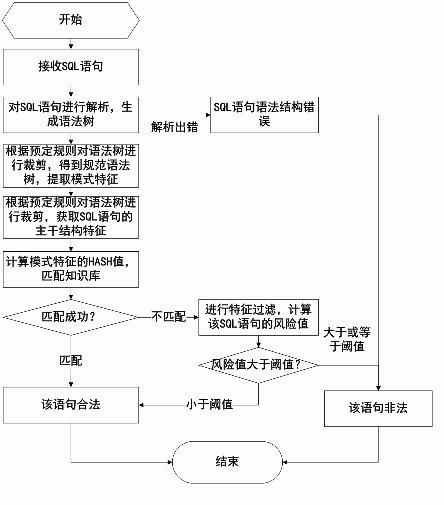
[0070] 402: parse the SQL statement to generate a syntax tree, if there is an error in the analysis, jump to step 407;
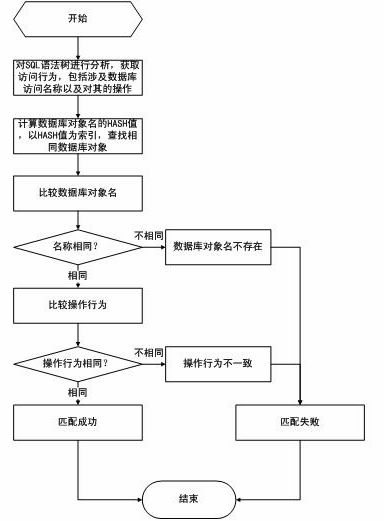
[0071] 403: Analyze the syntax tree to obtain access behavior characteristics, and match the access behavior characteristics with the knowledge base. If the matching is unsuccessful, skip to step 407, otherwise skip to step 404;
[0072] For (1) select * from a where username = ‘chenfeng’ and passwd = 123, its database access behavior:
[0073] Database object name Types of operating 1a table Inquire 2 username Column Inquire 3 passwd Column Inquire
[0074] Match the access behavior with the database behavior pool, refer to the matching process image 3 ;
[0075] As in the above steps, select * from USER_CATALOG where name = ‘chen’or 1=1 access behavi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com