Database security protection system and method based on virtual databases and virtual patches
A security protection and database technology, applied in the field of information security, can solve problems such as attacks and achieve the effect of protecting database security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
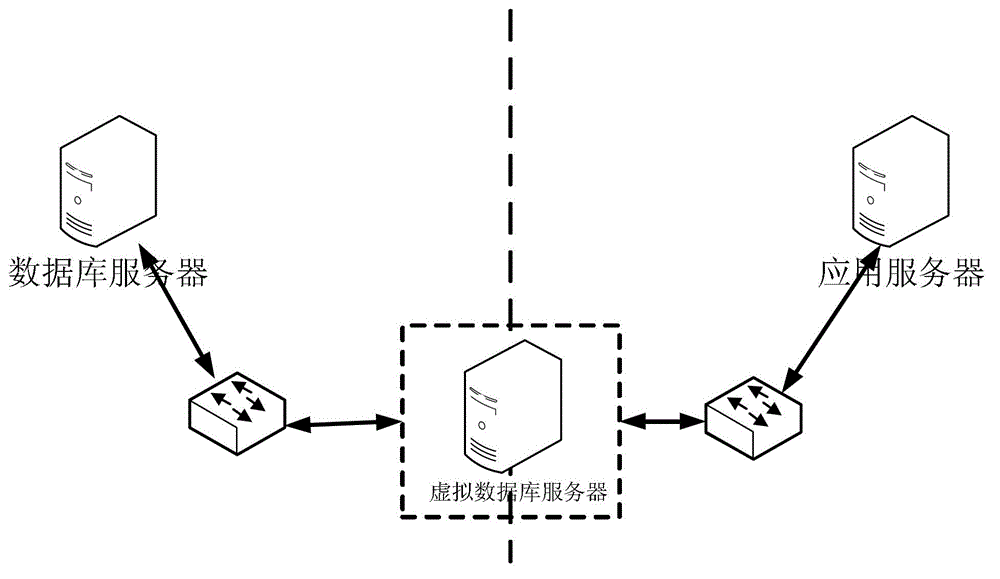
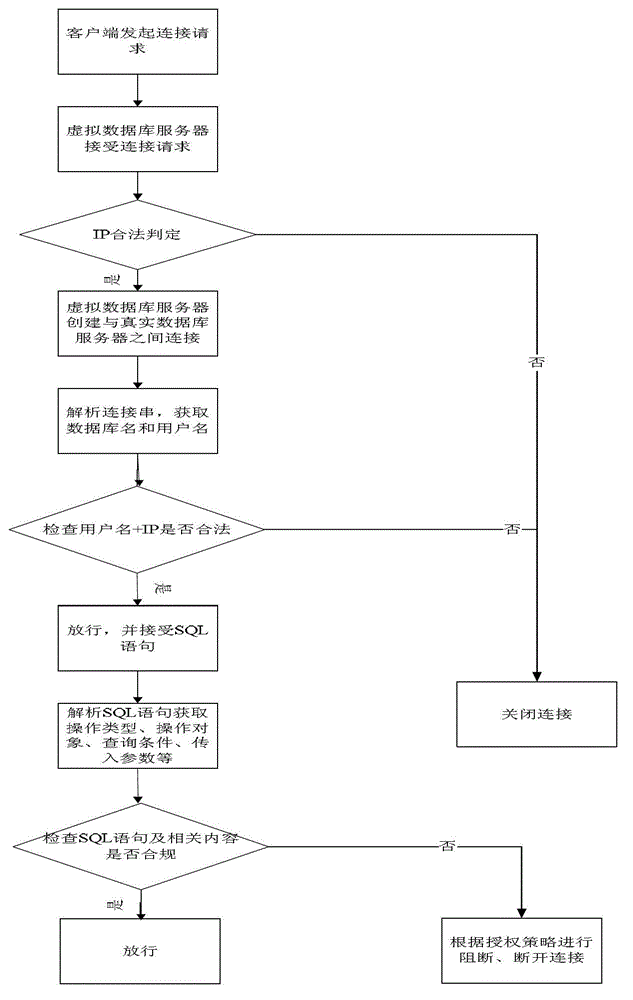
[0029] exist figure 1 In , the deployment location of the virtual database server is between the application server and the database server, that is, the database server and the virtual database server adopt a serial connection mode, and any SQL request reaching the database server must first pass through the virtual database server. The purpose of the screening process is to allow the virtual database to provide data services to the outside world, in this way the real server is fully hidden.
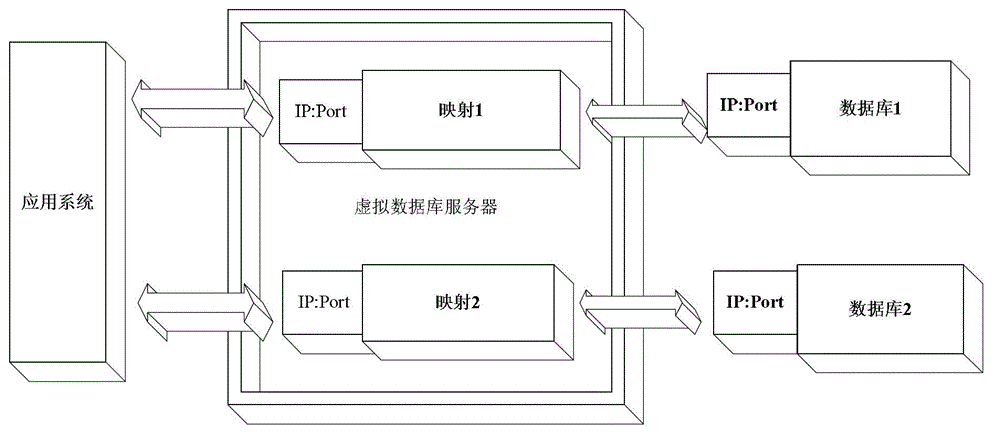
[0030] exist figure 2 In , after the virtual database server is deployed, the services provided by the database server are mapped to the IP address of the virtual database server and the specified free port, thus establishing a mapping relationship to the database server in the virtual database server. Multiple similar mapping relationships can be established in the database at the same time, and they are mapped to multiple different database servers. When the application server and c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com