Method for securely transmitting equipment information
A technology for safe transmission of equipment information, applied in the field of information security, can solve problems such as reducing the security of CPU card information, and achieve the effect of safe transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
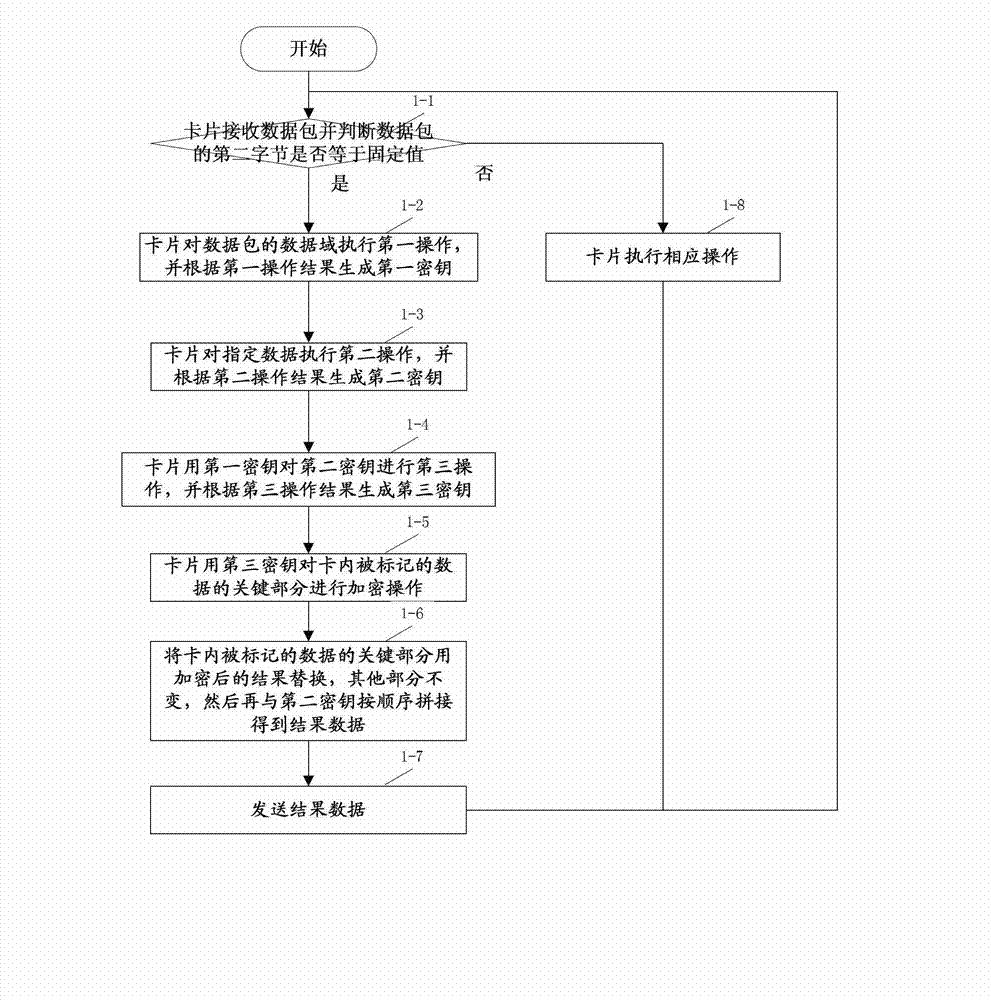
[0043] see figure 1 , Embodiment 1 provides a method for securely transmitting device information, specifically including:
[0044] Step 1-1: The card receives the data packet and judges whether the second byte of the data packet is equal to a fixed value;
[0045] If yes, go to step 1-2; if no, go to step 1-8.
[0046] In this embodiment, the second byte of the data packet has a fixed value of 0XF8.
[0047] Step 1-2: The card performs a first operation on the data field of the data packet, and generates a first key according to the result of the first operation;
[0048] In this embodiment, a specified key must participate in the first operation. The specified key is the key agreed by both parties inside the card and outside the card, and cannot be read outside the card. The first operation includes, but is not limited to, symmetric encryption, asymmetric encryption, random number encryption, data hashing, bit operations, and combinations thereof. Part or all of the dat...
Embodiment 2
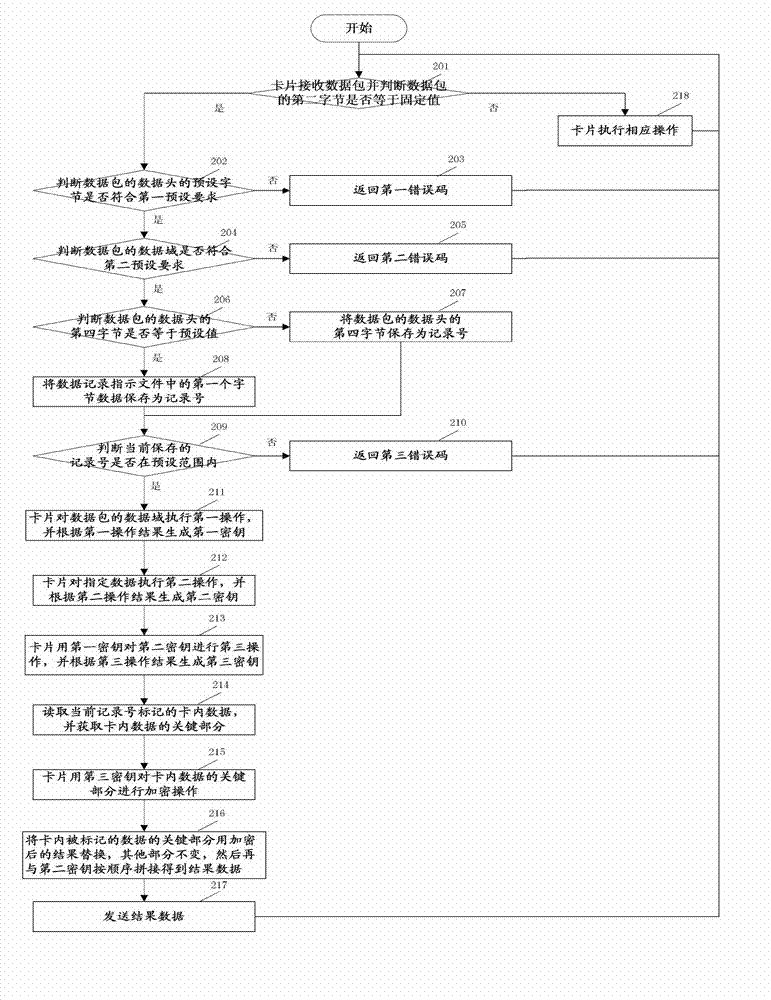
[0071] see figure 2 , Embodiment 2 provides a method for specifically processing security device information, specifically including:
[0072] Step 201: the card receives the data packet and judges whether the second byte of the data packet is equal to a fixed value;
[0073] If yes, go to step 202; if no, go to step 218.
[0074] In this embodiment, the second byte of the data packet has a fixed value of 0XF8.
[0075] Specifically, if the second byte of the received data packet is 0XF8, the data packet is composed of a data header and a data field, wherein the first five bytes of the high-order end are the data header, and the remaining part is the data field.
[0076] For example: The received data packet is: 80F80201082012040917375080, the data header is: 80F8020108, and the data field is: 2012040917375080.
[0077] Step 202: judging whether the preset byte of the data header of the data packet meets the first preset requirement, if yes, execute step 204, if no, execut...
Embodiment 3
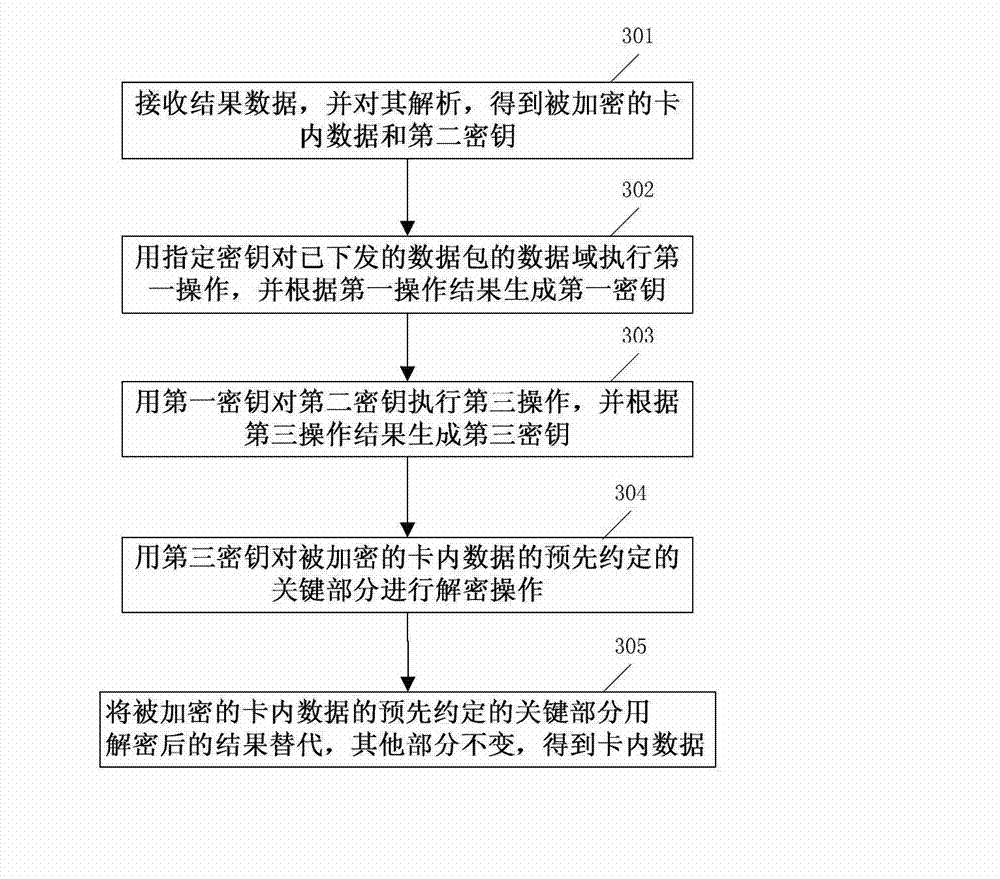
[0157] see image 3 , Embodiment 3 provides a method for decrypting the security device information in Embodiment 2, specifically including:
[0158] Step 301: Receive the result data and analyze it to obtain the encrypted data in the card and the second key;
[0159] In this embodiment, the specific received result data is:
[0160] 6963626320636172642020202020202020202020900758403049921820FF35DF1F4AE18C1E5F7EEED7449D59D76618237FFF0075D5C88B918020303F4FE0DA9380CED691E7405183A10FBD61E7405183A10FBD61231234454545454545454545454545454545FFFF1012FFFFB0D6D68C11987977
[0161] After parsing, the encrypted card data is obtained as follows:
[0162] 6963626320636172642020202020202020202020900758403049921820FF35DF1F4AE18C1E5F7EEED7449D59D76618237FFF0075D5C88B918020303F4FE0DA9380CED691E7405183A10FBD61E7405183A10FBD61231234454545454545454545454545454545FFFF1012FFFF
[0163] The second key is: B0D6D68C11987977
[0164] Step 302: Using the specified key to perform a first operation on ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com