Secure communication method, terminal, server and system
A security communication and server technology, applied in transmission systems, electrical components, user identity/authority verification, etc., can solve problems such as man-in-the-middle attacks, and achieve the effect of low cost and convenient implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0057] This embodiment describes the technical solution of the present invention from the perspective of a terminal.
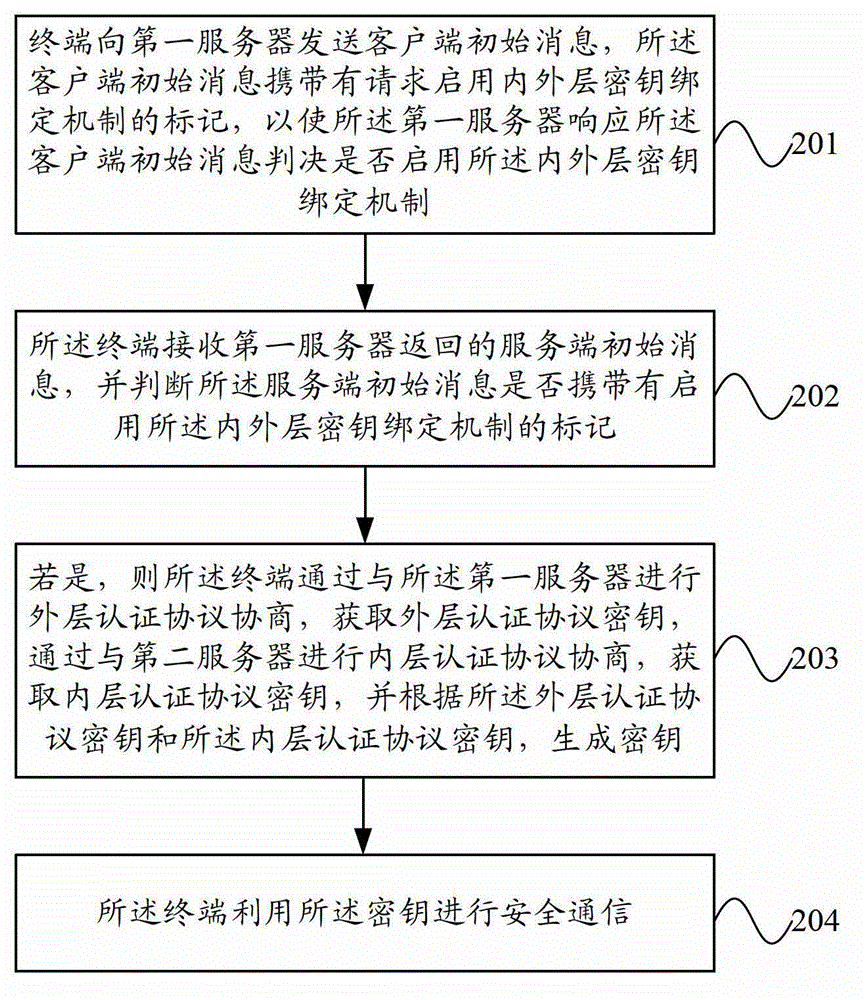
[0058] figure 2 It is a schematic flowchart of a secure communication method according to an embodiment of the present invention. Such as figure 2 As shown, the secure communication method includes the following steps:
[0059] Step 201, the terminal sends a client initial message to the first server, the client initial message carries a flag requesting to enable the inner and outer key binding mechanism, so that the first server responds to the client initial message to determine whether to Enable the inner and outer key binding mechanism;
[0060] Step 202, the terminal receives the server initial message returned by the first server, and judges whether the server initial message carries a flag for enabling the inner and outer key binding mechanism;
[0061] Step 203, if yes, the terminal obtains the outer authentication protocol key by negotiating the...
Embodiment 2
[0096] On the basis of the secure communication method in the above embodiment, the terminal sends a client initial message to the server, and the client initial message carries a flag requesting to enable the inner and outer key binding mechanism, specifically including:
[0097] The terminal sends a client initial message carrying a tunnel key binding extension field to the server;
[0098] Correspondingly, the judging whether the server initial message carries a flag for enabling the inner and outer key binding mechanism specifically includes:
[0099] Judging whether the server initial message carries the tunnel key binding extension field.
[0100] Specifically, by adding a new extension type, Tunnel Key Binding (TKB) Extension, to the client initial message / server initial message, it serves as a mark for enabling the inner and outer key binding mechanisms. That is, the terminal notifies the server that it intends to use the TKB extension by adding the TKB extension fiel...
Embodiment 3
[0107] This embodiment describes the technical solution of the present invention from the perspective of a server supporting the inner and outer key binding mechanism.
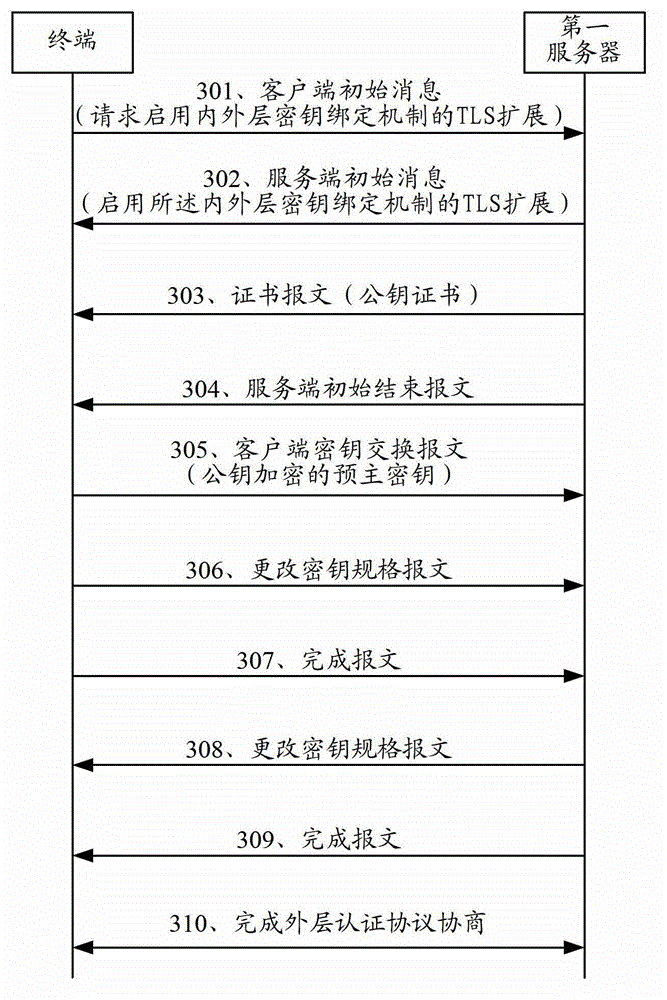
[0108] Figure 6 It is a schematic flowchart of a secure communication method according to another embodiment of the present invention. like Figure 6 As shown, the secure communication method includes the following steps:
[0109] Step 601, the first server receives the client initial message sent by the terminal, and the client initial message carries a mark requesting to enable the inner and outer key binding mechanism;
[0110] Step 602, the first server responds to the client initial message, and sends to the terminal a server initial message carrying a flag for enabling the inner and outer key binding mechanism, so that the terminal knows that the Internal and external key binding mechanism;
[0111] Step 603, the first server acquires an outer authentication protocol key by negotiating an outer auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com