Malicious program detection method and scan engine
A malicious program and scanning engine technology, applied in the field of network virus detection and killing, can solve the problems of low implementation efficiency, malicious program detection and killing, and program failure, and achieve the effect of simple implementation, improved accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
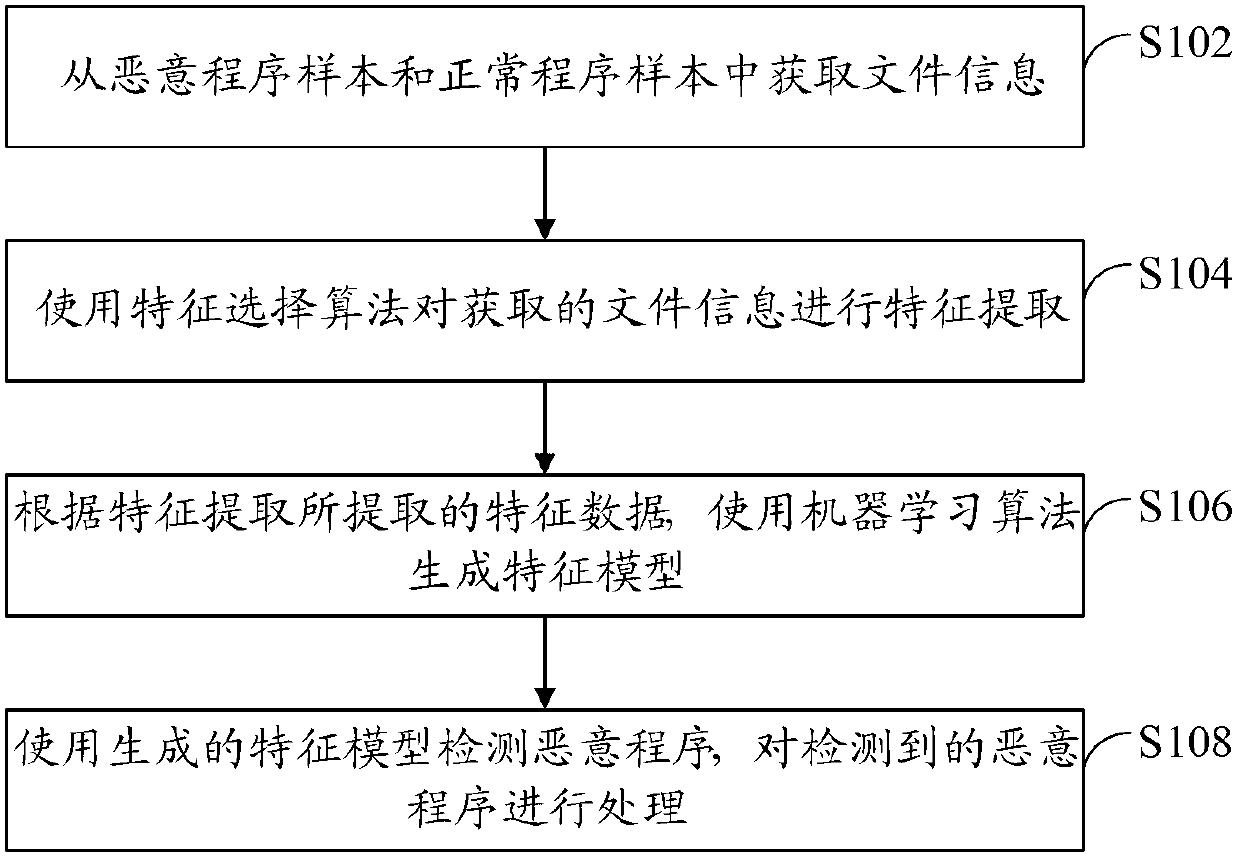
[0033] refer to figure 1 , shows a flow chart of steps of a malicious program detection method according to Embodiment 1 of the present application.
[0034] The malicious program detection method of the present embodiment includes the following steps:
[0035] Step S102: Obtain file information from malicious program samples and normal program samples.
[0036] Wherein, the file information includes a file name and a file path.
[0037] Malicious program samples and normal program samples can be existing samples, or both existing samples and samples collected in real time. Malicious program detection tools can obtain malicious program samples and Normal procedure sample.
[0038] File information can be acquired in a common way, such as from file attributes of the file, etc. Those skilled in the art can use an appropriate method according to the actual situation, which is not limited in this application.
[0039] Step S104: Use a feature selection algorithm to perform fea...
Embodiment 2
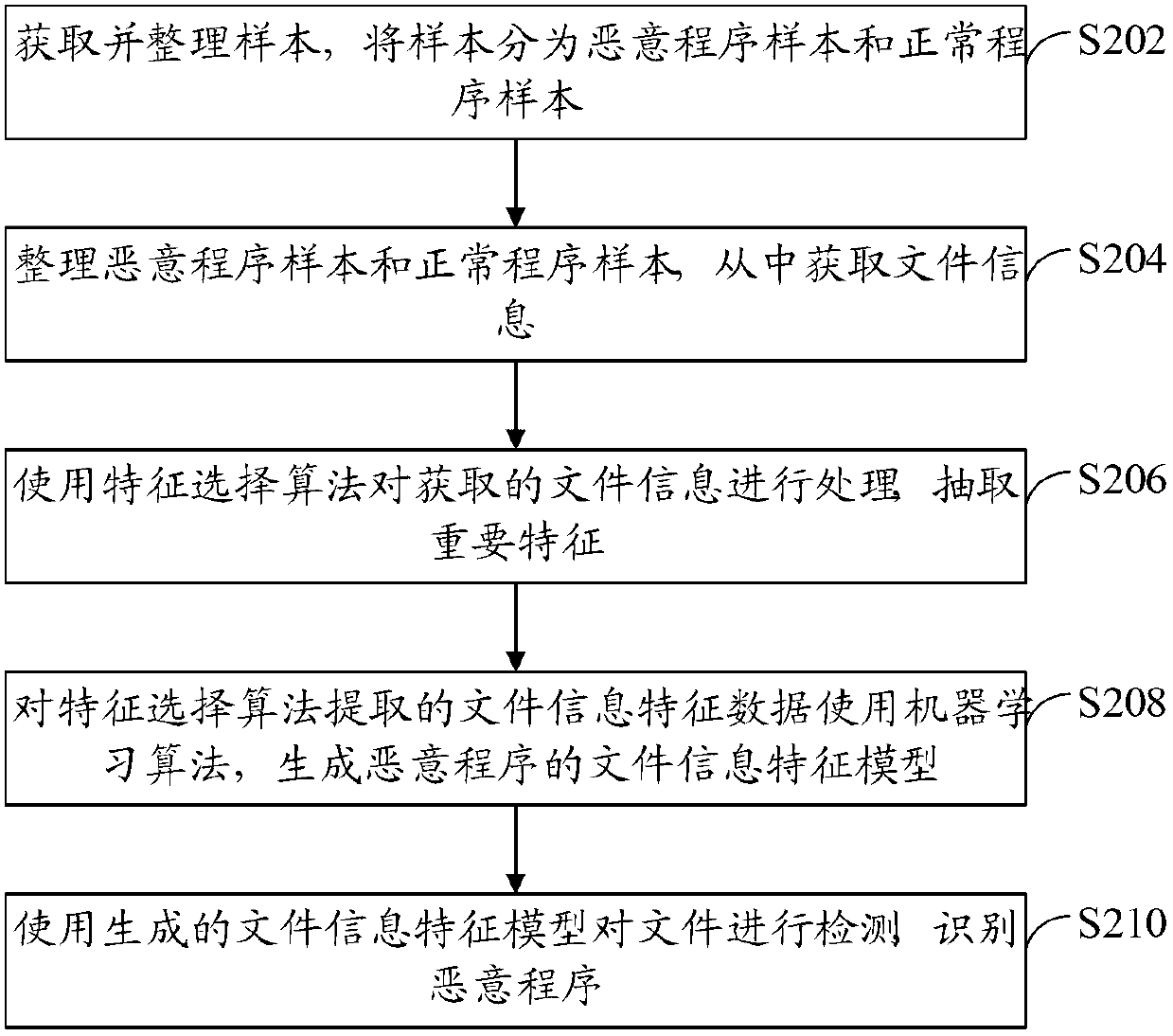
[0049] refer to figure 2 , shows a flow chart of steps of a malicious program detection method according to Embodiment 2 of the present application.
[0050] The malicious program detection method of the present embodiment includes the following steps:
[0051] Step S202: Acquiring and sorting the samples, and classifying the samples into malicious program samples and normal program samples.
[0052] Step S204: sort out malicious program samples and normal program samples, and obtain file information therefrom.
[0053] In this embodiment, the file information includes not only the file name and the file path, but also at least one of the following: file resource segment information, file copyright information, file time stamp information, and file length information.
[0054] According to the observation of malicious program samples, file name, file path, file resource information (including product description, file information, company name), file copyright information, ...
Embodiment 3
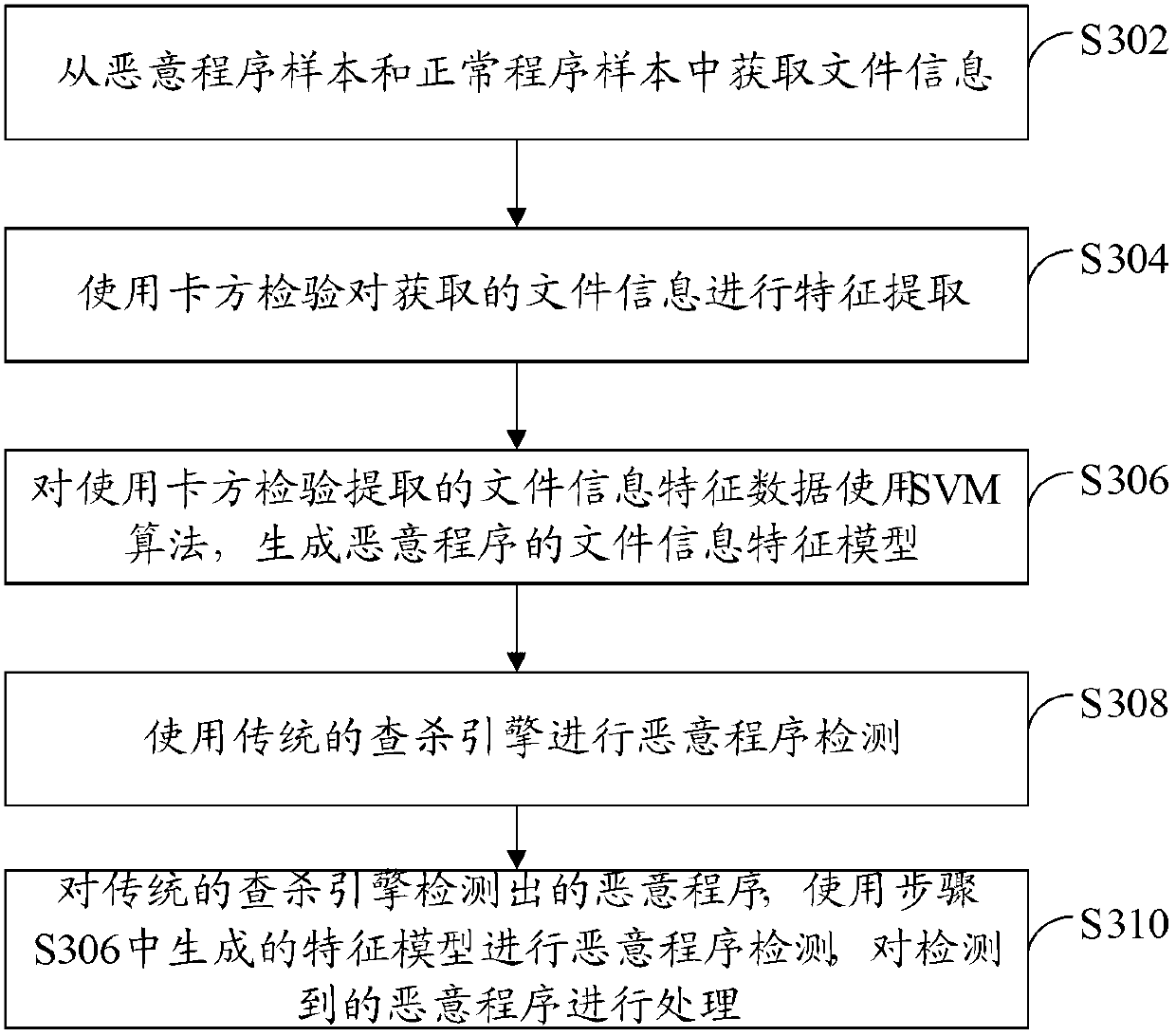
[0101] refer to image 3 , shows a flow chart of steps of a malicious program detection method according to Embodiment 3 of the present application.
[0102] In this embodiment, on the basis of detecting and killing malicious programs by the existing detection and killing engine, further detection of malicious programs is performed as an auxiliary means and beneficial supplement to the existing detection and killing engine.
[0103] Step S302: Obtain file information from malicious program samples and normal program samples.
[0104] In this embodiment, the file information includes not only the file name and the file path, but also at least one of the following: file resource segment information, file copyright information, file time stamp information, and file length information.
[0105] Step S304: Perform feature extraction on the acquired file information by using chi-square test.
[0106] For example, for the extracted file name sample "QQ hacking Trojan horse", use ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com