Authentication method and relevant device
An authentication and equipment technology, applied in the field of communication, can solve the problems of affecting the accuracy of authentication, authentication failure, inconvenient use, etc., and achieve the effect of saving authentication time, simplifying the authentication process, and improving flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0064] This embodiment will be described from the perspective of a first terminal, where the first terminal may serve as an NFC initiating device, specifically a personal computer (PC, Personal Computer), a tablet computer, or a mobile phone.
[0065] An authentication method, comprising: sending an authentication request message of a current service to a second terminal through NFC; receiving authentication information returned by the second terminal through NFC according to the authentication request message; business authentication.
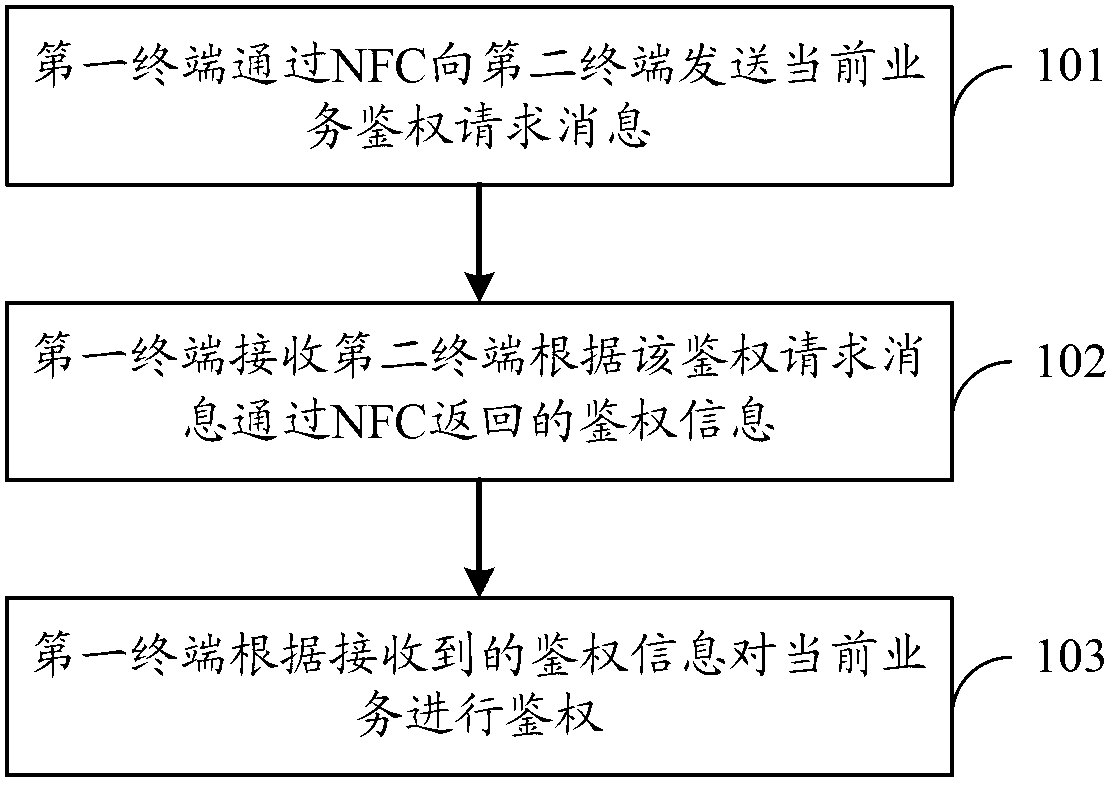
[0066] Such as figure 1 As shown, the specific process can be as follows:
[0067] 101. The first terminal sends an authentication request message of the current service (that is, the current service of the first terminal) to the second terminal through NFC;
[0068] Wherein, the second terminal may serve as an NFC target device, specifically, a terminal such as a personal computer (PC, Personal Computer), a tablet computer, or a mobile phon...
Embodiment 2
[0080] This embodiment will be described from the perspective of a second terminal, where the second terminal may serve as an NFC target device, specifically a terminal such as a PC, a tablet computer, or a mobile phone.
[0081] An authentication method, comprising: receiving an authentication request message of the first terminal's current service sent by the first terminal through NFC, obtaining authentication information according to the authentication request message, and sending the authentication information to the first terminal through NFC , so that the first terminal authenticates the current service according to the authentication information.
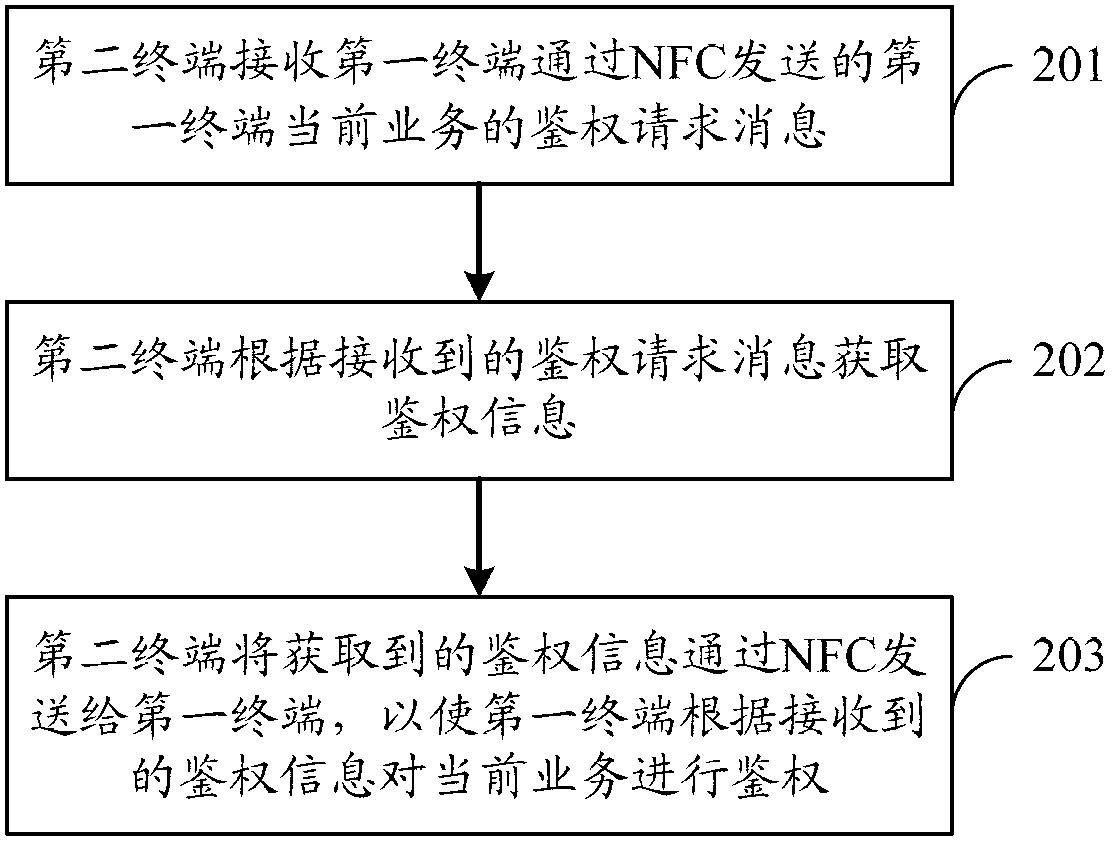
[0082] Such as figure 2 As shown, the specific process can be as follows:
[0083] 201. The second terminal receives an authentication request message for the current service of the first terminal sent by the first terminal through NFC;
[0084] Wherein, the first terminal may serve as an NFC initiating device. Specifica...
Embodiment 3
[0107] According to the methods described in Embodiment 1 and Embodiment 2, the following examples will be used to describe in detail.
[0108] In this embodiment, the first terminal is specifically a PC, and the second terminal is specifically a mobile phone for illustration. Both the PC and the mobile phone have an NFC module, that is, have an NFC function. The so-called NFC function refers to the possibility of data transmission through NFC.
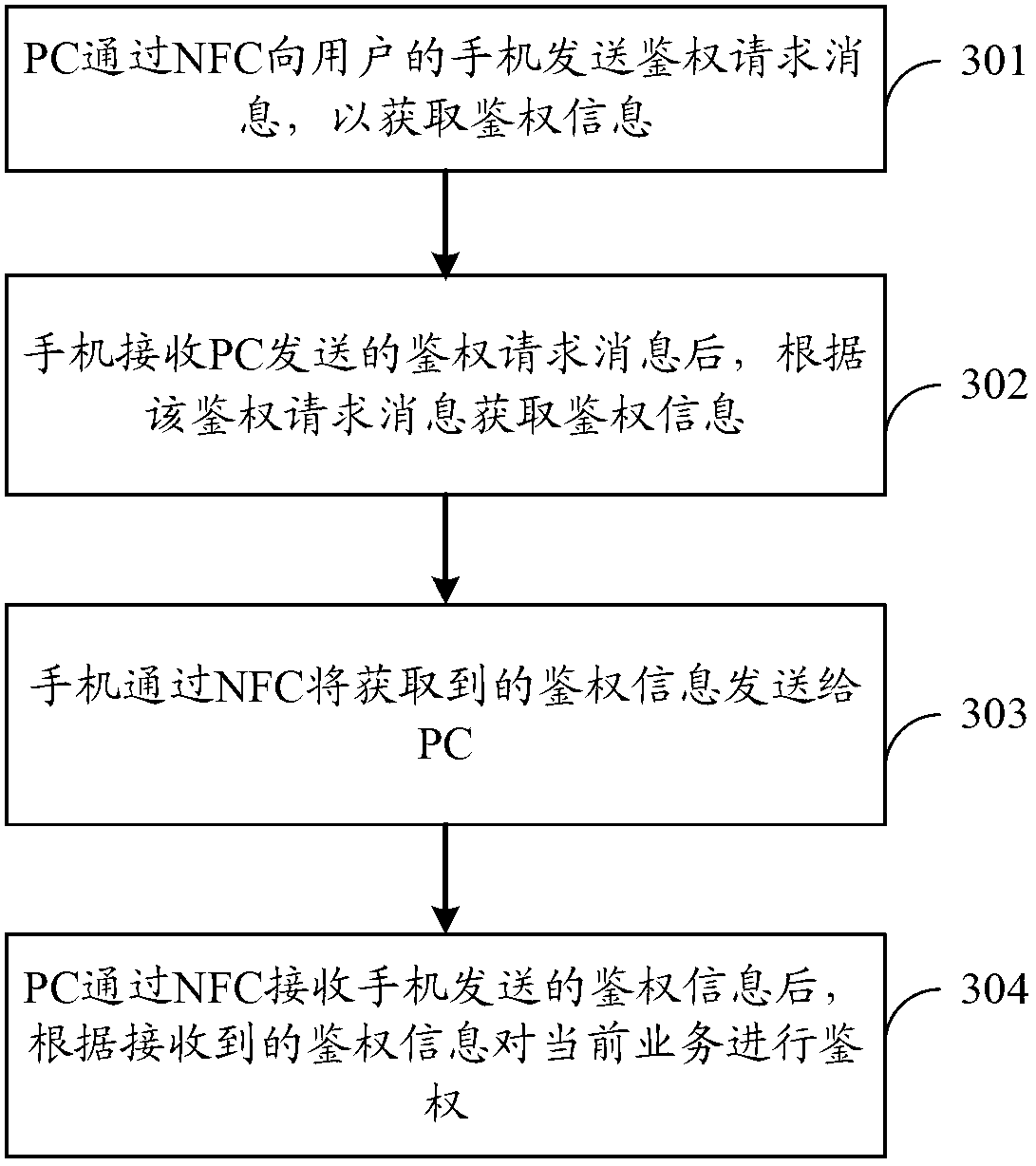
[0109] Such as image 3 As shown, the specific process can be as follows:
[0110] 301. The PC sends an authentication request message of the current service to the mobile phone of the user through NFC, so as to obtain authentication information.
[0111] Wherein, the authentication request message may carry the identity information of the user, and may also carry information such as the service identifier of the current service. Identity information may include user identification, user name (such as user's nickname, etc.) and / or ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com