Identity identification security method based on cloud computing
An identity recognition and cloud computing technology, applied in the field of cloud computing, can solve problems such as high capital threshold and expensive hardware investment, and achieve the effect of ensuring stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0010] The method of the present invention is described in detail below with reference to the accompanying drawings.
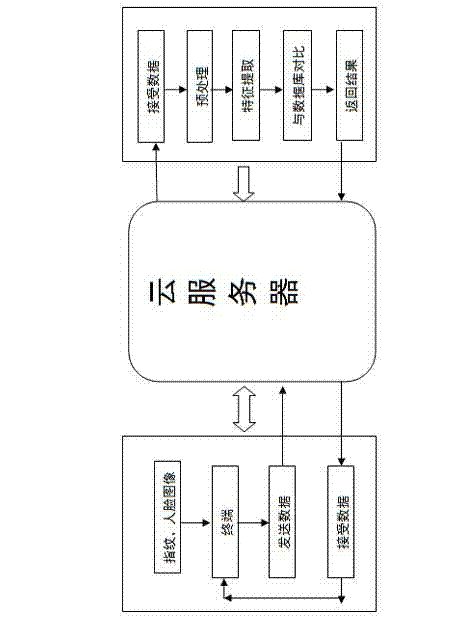
[0011] as appendix figure 1 As shown, data such as fingerprint images are transmitted from the client to the cloud computing server through the network for identification processing. The server side is a server group based on cloud architecture. Through cloud computing technology, multiple ordinary personal computers, standard servers (collectively referred to as computing nodes) and storage devices are combined using the network to form a supercomputer cluster. The access and identification operations of each client are distributed to different computing nodes for processing through the network, and the results are sent back to the client through the network. The cloud server provides powerful identification processing capabilities, thereby reducing the processing burden on the client, making the user terminal simplified into a simple input and output devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com