Security management method and system for vehicular mobile Internet
A security management and vehicle-mounted mobile technology, applied in the transmission system, electrical components, etc., to achieve efficient authentication mechanism and encrypted communication mechanism, to ensure the effect of not being stolen and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
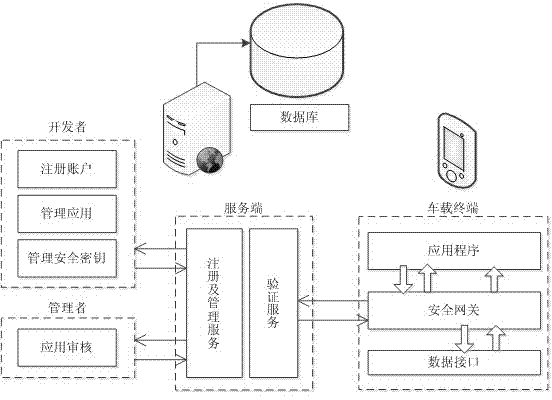
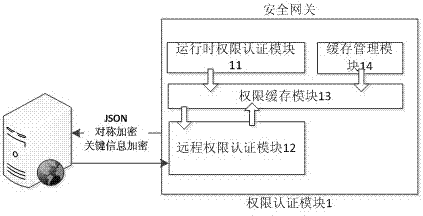
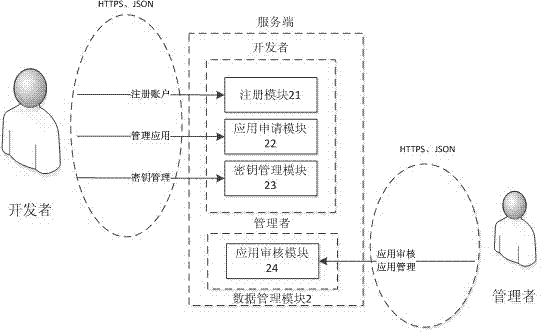
[0032] Such as figure 1 , 2 . As shown in 3, the application program accesses the vehicle terminal, and the vehicle terminal judges the access authority of the application program. If it is a local access, that is, it does not apply for Internet access authority, that is, it does not access the Internet. At this time, it can use the important information of the vehicle to run Time-level information application, the important information of vehicle terminal users will not be illegally used through Internet access through this application, which ensures the user's information security.
[0033] When installing the application, the vehicle terminal user will be reminded that the application uses the "obtain important information" permission, and the user must confirm before continuing to install the application. When the application is installed, the system is used to interact with the user in the form of a graphical and text interface, and inform the user of the permission perm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com