Quick filtering method for malicious application programs
A malicious application, application technology, applied in the field of application detection, can solve the problem of inability to filter applications quickly and efficiently, and achieve the effect of improving screening efficiency and reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
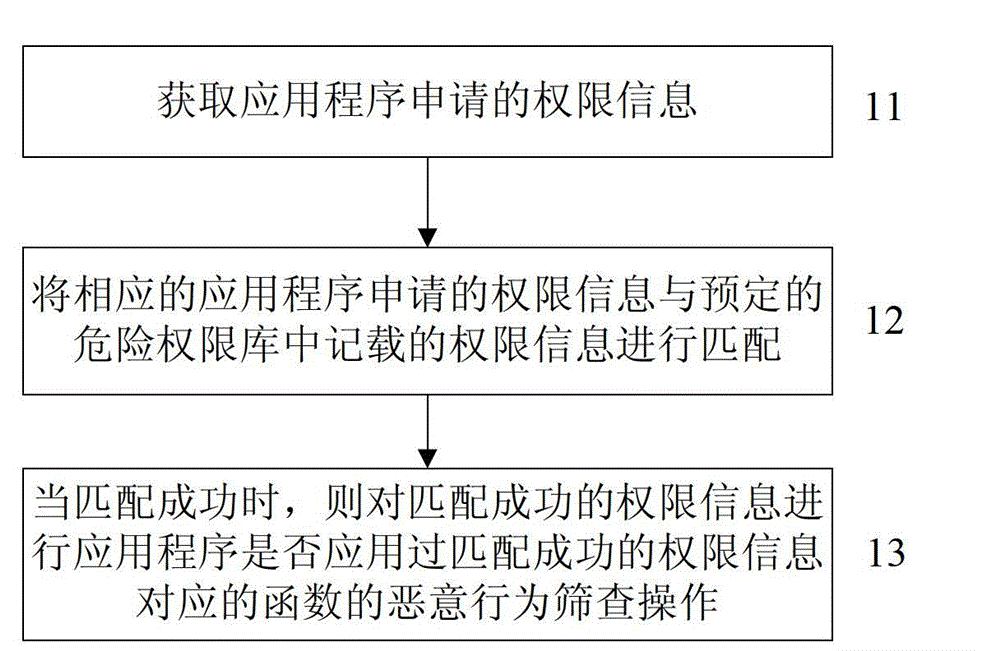
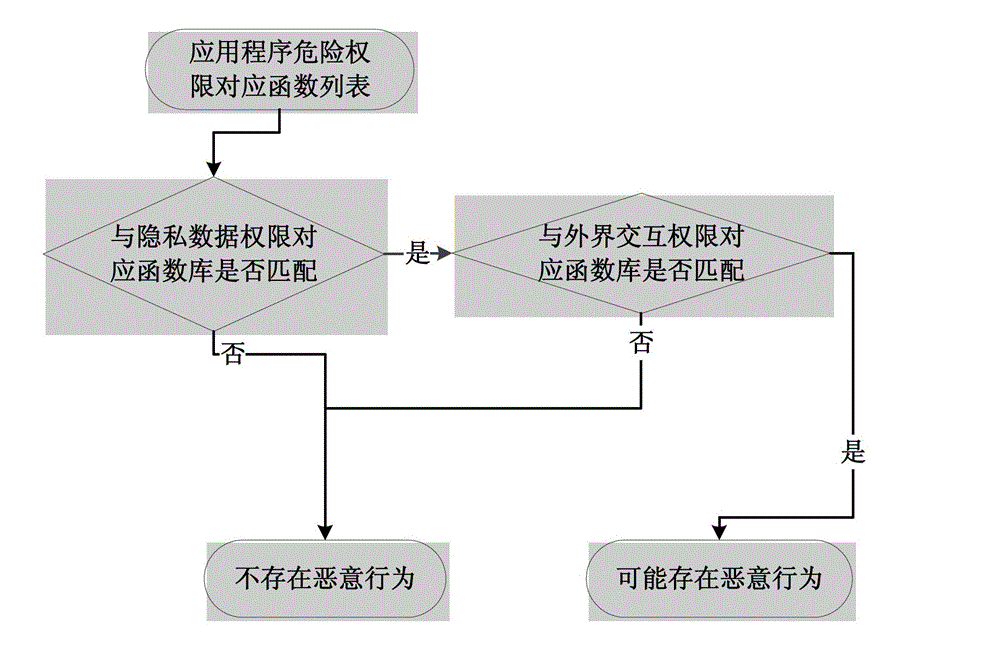
[0087] The fast filtering method of the malicious application program based on the Android system provided by this embodiment one mainly includes:
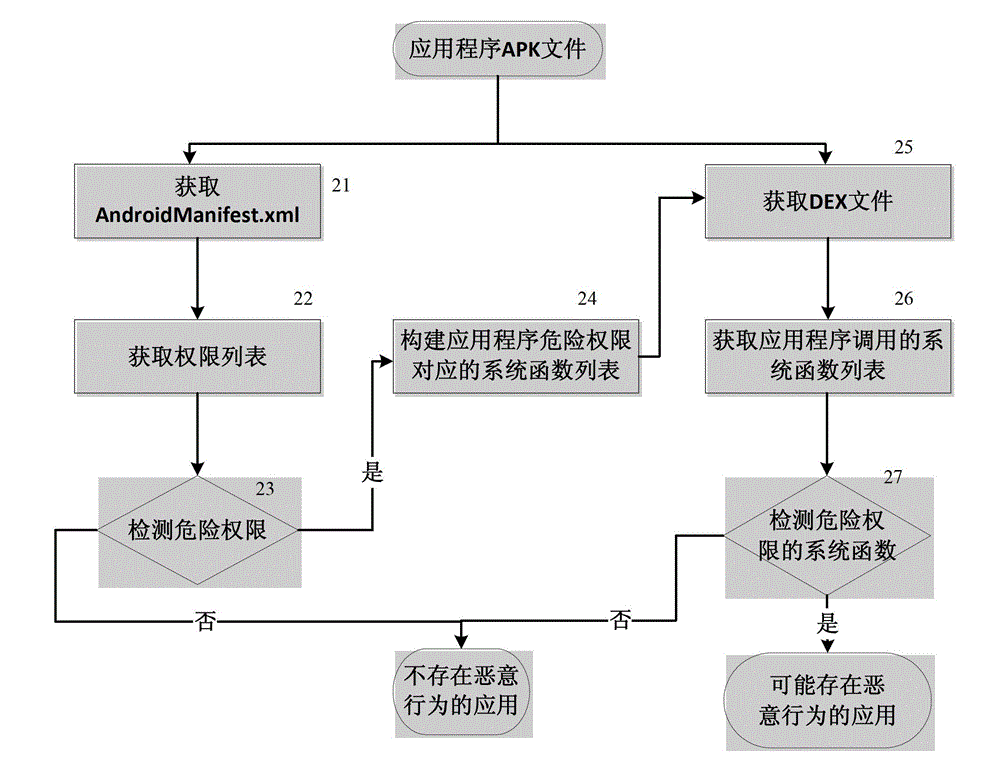
[0088] (1) Get AndroidManifest.xml
[0089] Specifically, you can use WinRAR software to decompress the encrypted AndroidManifest.xml file from the APK file, or you can use any other software that supports APK file format unpacking, such as WinZip, 7Zip, etc.;
[0090] Further, in this step, AXMLPrinter2.jar can be used to decrypt the encrypted AndroidManifest.xml file to obtain the unencrypted original AndroiManifest.xml file, or other decryption software such as APKTool.jar can be used to perform corresponding decryption operations .
[0091] (2) Obtain the permission list requested by the application
[0092] Specifically, the xml file parsing package in Java can be used to parse the permission description part in AndroidManifest.xml to obtain the permission list applied by the application program;
[0093] Of course, you ca...
Embodiment 2
[0108] In the second embodiment, the application program of Angry Birds Space (Angry Birds Space, ngryBirdsSpace v1.1.0.APK) is analyzed as an example, and the final conclusion is that the application program is safe. The specific analysis steps include:
[0109] (1) Get AndroidManifest.xml
[0110] That is, you can use WinRAR software to decompress the encrypted AndroidManifest.xml file from the AngryBirdsSpace v1.1.0.APK file;
[0111] Use AXMLPrinter2.jar to decrypt the encrypted AndroidManifest.xml file to obtain the non-encrypted original AndroiManifest.xml file.
[0112] (2) Get permission list
[0113] That is, you can use the xml file parsing package in Java to parse the permission description part in AndroidManifest.xml to obtain the list of permissions applied for by the application;
[0114] The obtained permission list contains a permission: android.permission.INTERNET.
[0115] (3) Detect dangerous permissions
[0116] Match the list of permissions obtained i...
Embodiment 3
[0139] The third embodiment is to analyze the application program Walk and Text (WalkandTextv1.3.7.APK), and finally conclude that the application may be unsafe. Specific steps include:
[0140] (1) Get AndroidManifest.xml
[0141] Use WinRAR software to decompress the encrypted AndroidManifest.xml file from the WalkandTextv1.3.7.APK file;
[0142] Use AXMLPrinter2.jar to decrypt the encrypted AndroidManifest.xml file to obtain the non-encrypted original AndroiManifest.xml file.
[0143] (2) Get permission list
[0144] Use the xml file parsing package in Java to parse the permission description part in AndroidManifest.xml to obtain the list of permissions applied for by the application, including:
[0145] android.permission.CAMERA,
[0146] com.android.vending.CHECK_LICENSE,
[0147] android.permission.ACCESS_FINE_LOCATION,
[0148] android.permission.ACCESS_COARSE_LOCATION,
[0149] android.permission.ACCESS_NETWORK_STATE,
[0150]android.permission.SEND_SMS,
[01...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com