Encryption-software based automated detection and maintenance methods
An encryption software and automatic detection technology, applied in the field of data security, can solve problems such as increased workload and difficult maintenance, and achieve the effect of simple maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
[0043] Such as figure 1 As shown, the present invention is divided into a server-side detection and maintenance method, a management-side detection and maintenance method, and a client-side detection and maintenance method according to the existing commercially available encryption software architecture; and all of them have reminder and alarm functions.
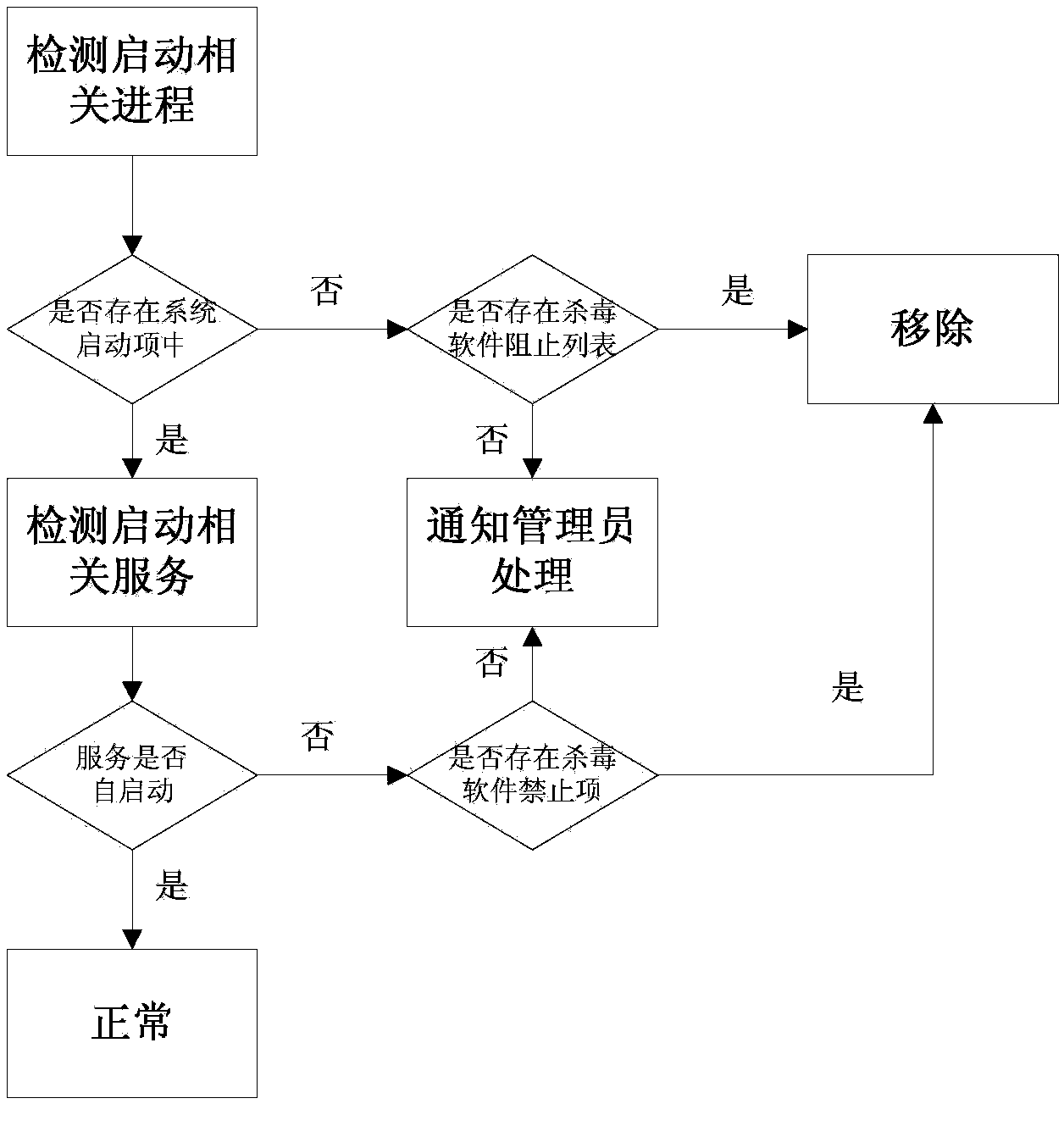
[0044] The detection and maintenance of the server side is mainly to solve the detection of server authorization expiration, startup abnormality detection (including no self-starting and being mistaken by anti-virus software for illegal programs to prevent operation), port abnormality detection, client information feedback, etc.;
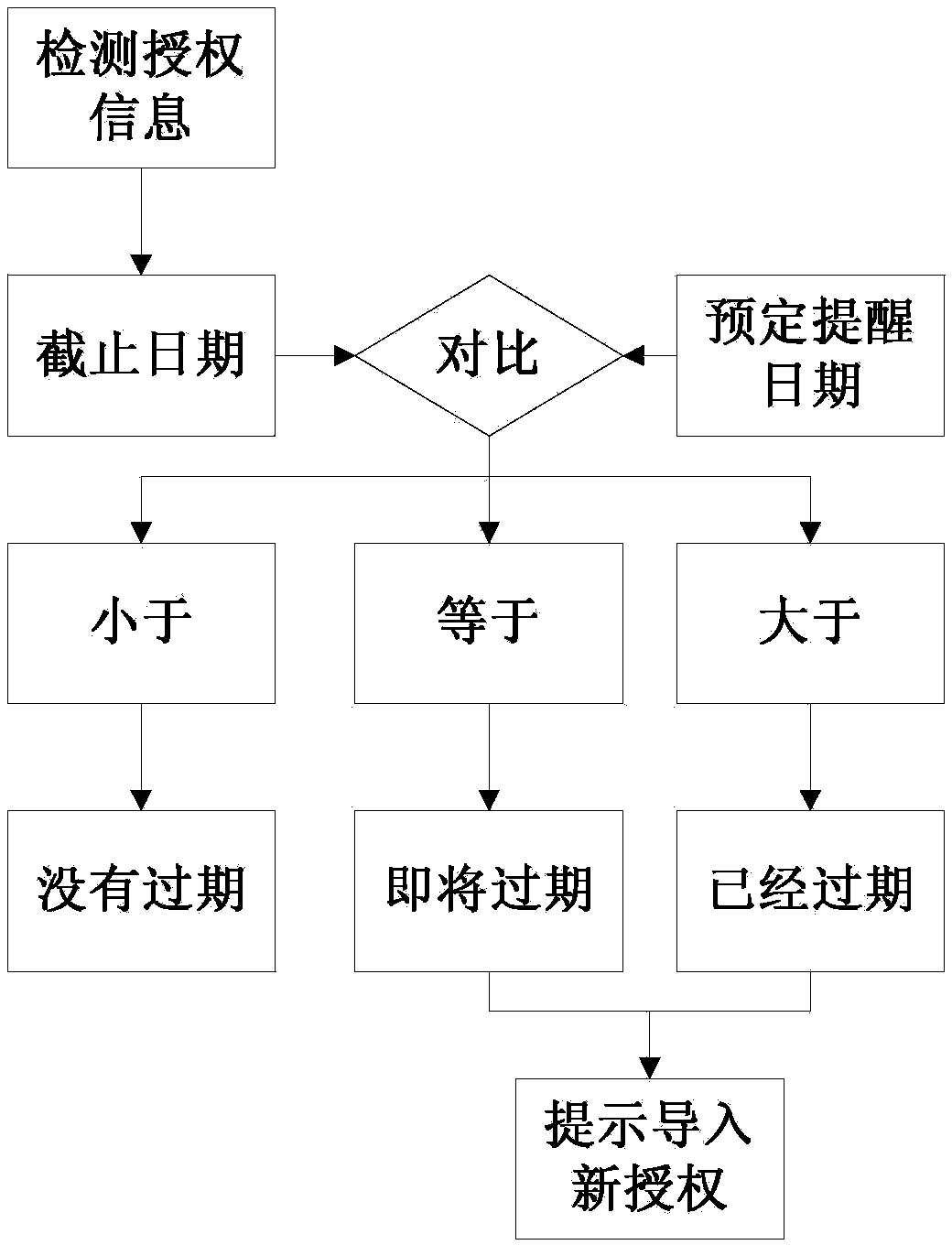
[0045] Such as figure 2 As shown, based on the corresponding encryption software, the present invention detects the expiry date of the corresponding authoriza...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com