3DES (triple data encrypt standard) encryption method
An encryption method and encrypted technology, applied to encryption devices with shift registers/memory, key distribution, can solve problems such as inability to distinguish well, and achieve the effect of enhancing encryption operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0020] Embodiment 1, byte exchange method:
[0021] 1. Encryption processing rules:
[0022] Assume that the original data DATA0 to be encrypted is 8-byte binary data.
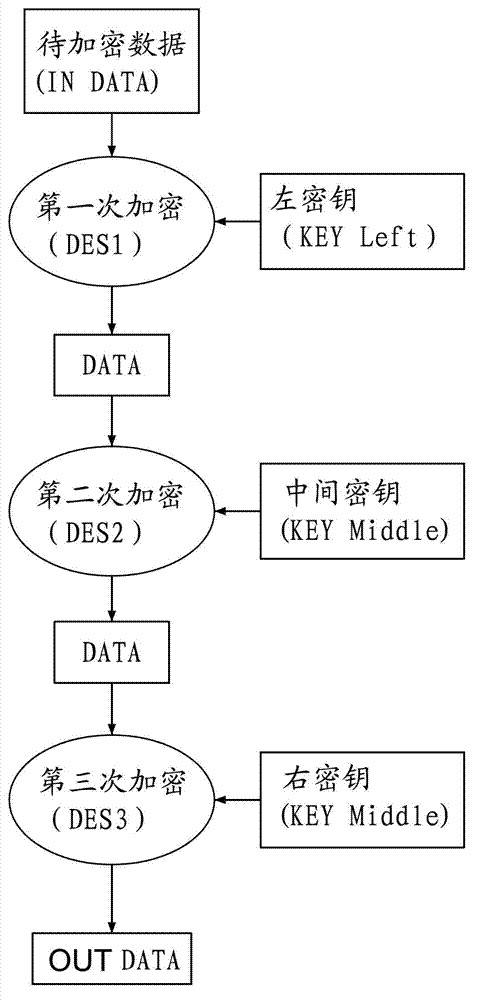
[0023] The first DES encryption: the result of DATA0 encryption is DATA1;
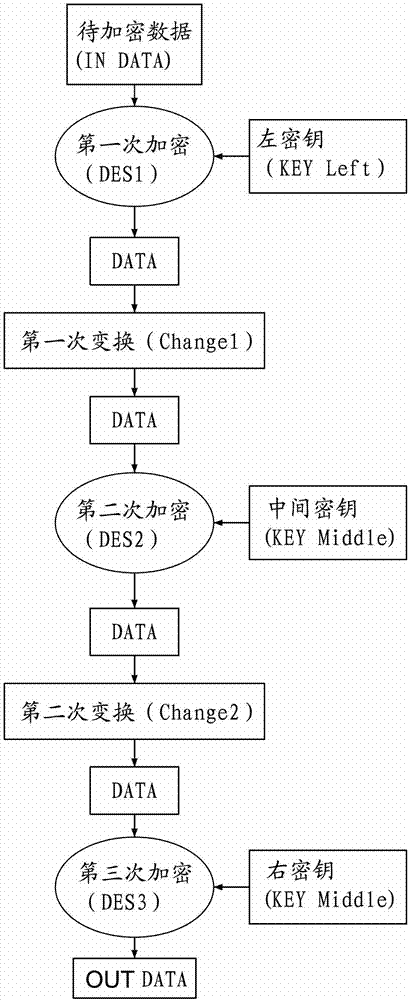
[0024] The first change rule: D8 and D1 byte exchange. After changing the original data of DATA1 [D8.D7.D6.D5.D4.D3.D2.D1], the new data DATA1-1 [D1.D7.D6.D5] will be obtained .D4.D3.D2.D8]; (Note: The arrangement position of data D1 and D8 is swapped)
[0025] The second DES encryption: After encrypting the DATA1-1 after the first change, the encrypted result DATA2 is obtained;
[0026] The second change rule: D4 and D5 byte exchange. The new data DATA2-1 [D8.D7.D6.D4.D5] will be obtained after the original data of DATA2 [D7.D6.D5.D4D3.D2.D1.D0] is changed. .D3.D2.D1]; (Note: The arrangement positions of data D4 and D5 are interchanged)
[0027] The third DES encryption: after encrypting the DATA2-1 after the second change, the e...
Embodiment 2
[0037] Embodiment 2, byte reverse sequence method
[0038] 1. Encryption processing rules:
[0039] Assume that the original data DATA0 to be encrypted is 8-byte binary data.
[0040] The first DES encryption: the result DATA1 after DATA0 encryption;
[0041] The first change rule: After the original data DATA1, bytes are arranged in reverse order [D8.D7.D6.D5.D4.D3.D2.D1] byte by byte, the new data DATA1-1, character Sections in order [D1.D2.D3.D4.D5.D6.D7.D8]; (Note: data in reverse order)
[0042] The second DES encryption: the result DATA2 after DATA1-1 encryption;
[0043] The second change rule: After the original data DATA2, the bytes are arranged in the order [D8.D7.D6.D5.D4.D3.D2.D1], the new data DATA2-1 is obtained after the byte-by-byte inversion is changed. , the bytes are in order [D1.D2.D3.D4.D5.D6.D7.D8]; (Note: the data is in reverse order again)
[0044] The third DES encryption: after the second changed DATA2-1 is encrypted, the encrypted result DATA3 i...
Embodiment 3
[0054] Embodiment 3, byte cyclic shift method
[0055] 1. Encryption processing rules:
[0056] Assume that the original data DATA0 to be encrypted is 8-byte binary data.
[0057] The first DES encryption: the result DATA1 after DATA0 encryption;
[0058] The first change rule: the original data DATA1, the bytes are in the order [D8.D7.D6.D5.D4.D3.D2.D1], and the new data DATA1- 1 byte in order [D5.D4.D3.D2.D1.D8.D7.D6]; (Note: data rotates 3 bytes to the left)
[0059] The second DES encryption: the result DATA2 after DATA1-1 encryption;
[0060] The second change rule: the original data DATA2, the bytes are in the order [D8.D7.D6.D5.D4.D3.D2.D1], and after the 4-byte change, the new data DATA2- 1 byte in order [D4.D3.D2.D1.D8.D7.D6.D5]; (Note: data rotates 4 bytes to the left)
[0061] The third DES encryption: after encrypting the DATA2-1 after the second change, the encrypted result DATA3 is obtained;
[0062] DATA3 is the encrypted result of 2C3DES encrypted DATA0. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com