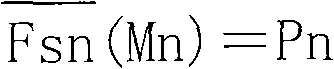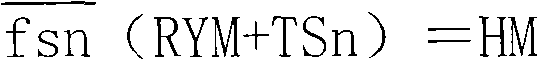Commodity anti-counterfeiting code construction and verification method
A commodity anti-counterfeiting code and verification method technology, which is applied in the field of digital anti-counterfeiting of commodities, can solve the problems of high risk of reuse and embezzlement, difficulty in identification, and high cost, and achieve the effects of improving anti-counterfeiting efficiency, reducing anti-counterfeiting costs, and increasing confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Take medicine, tobacco, and alcohol as examples for illustration, but the technology and scope of the present invention are not limited to the content of this example:
[0042] 1. On the product packaging production line, install a special software system for the control system of the digital or barcode printing device;
[0043] The clear code MM and the hidden code YM of the anti-counterfeiting code are generated by a special software system. The specific method is: the i-th anti-counterfeiting code is generated, the pointer Si of a certain algorithm in the algorithm library SFK is randomly selected, and according to the normal serial number and corresponding attributes of the product on the production line The encoding takes the digital string Pi with the length of the digital string W as agreed, and then calls the algorithm f(Si) in SFK according to the algorithm pointer Si in YMn, calculates and codes to form Mi, forms the plain code MMi together with the algorithm p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com