A Hardening Method Based on Host Monitoring Operating System
An operating system and host technology, applied in the field of intranet group monitoring and management systems, which can solve problems such as complex internal security management, removal or stop of computer experts, and complex user identities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be described in further detail below in conjunction with the accompanying drawings, but the implementation and protection scope of the present invention are not limited thereto.
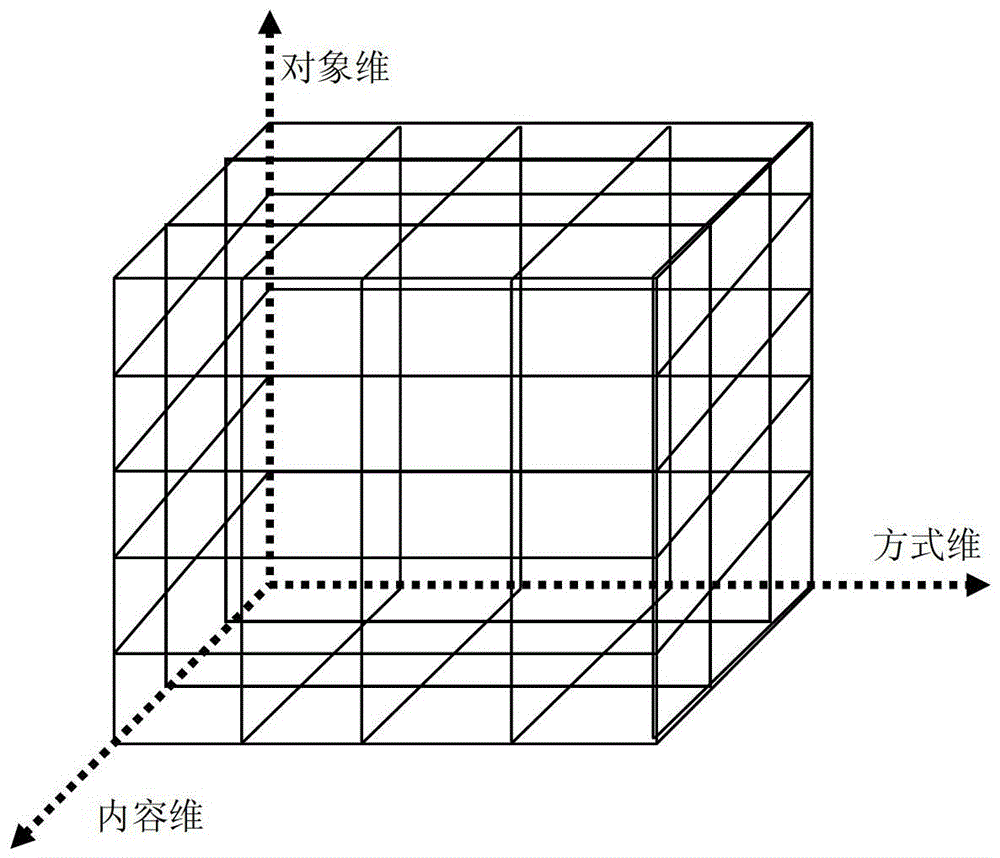
[0022] Such as figure 1 As shown in , we express the functional model of the host monitoring operating system from three dimensions: monitoring object, monitoring content, and monitoring method. Any point in the space formed by these three dimensions is a system function. Monitoring objects include network behavior (MAC layer, TCP layer, IP layer, ICP / IP application layer Email, FTP, HTTP, TelNet, etc. packet sending and receiving), file usage (OS file opening, modification, deletion, copying, Sending and other behaviors), system activity object calls (processes, services, distributed object EJB / COM / CORBA calls), system data structure access (such as registry and other configuration files), application system usage (various OS application systems and DBMS, services...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com