Method for realizing delegation of cipher function of TCM (trusted cryptographic module) under cloud computing environment
A cloud computing environment and cryptographic module technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of TCM inability, virtual TCM function and implementation complexity, cumbersome and time-consuming process of establishment and use, etc. Achieve the effect of improving data processing efficiency and ensuring data confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
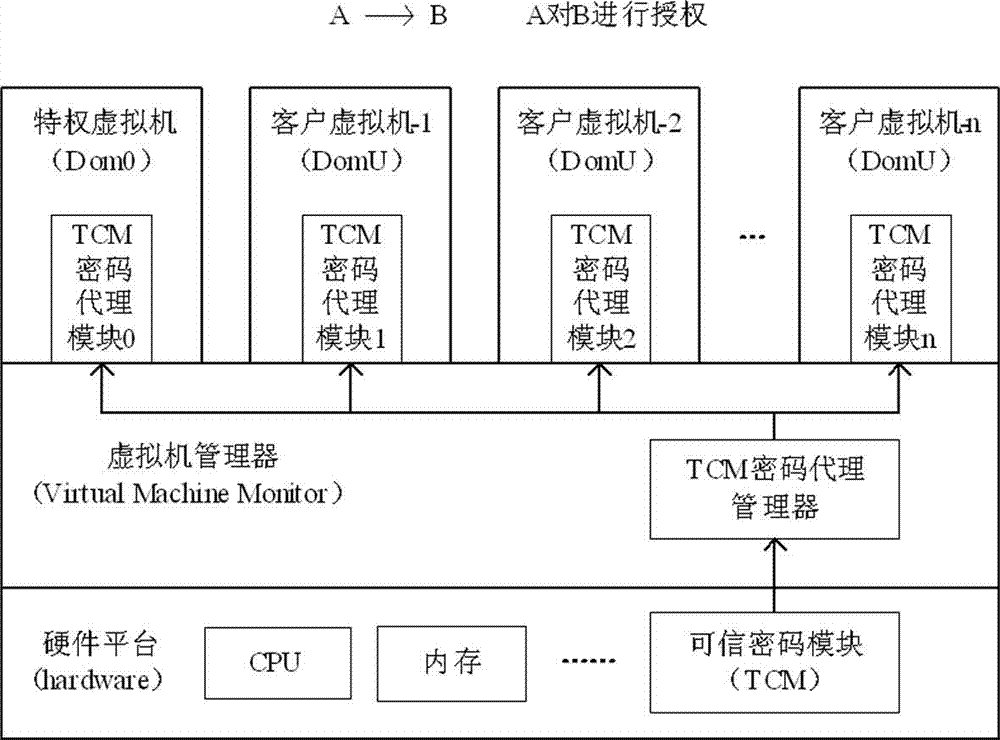
[0014] The present invention proposes a method for realizing the TCM cryptographic function authorization agent under the cloud computing environment, such as figure 1 Shown: On a virtual computing platform based on the VMM architecture, the password-related functions of the TCM are authorized by the TCM password proxy manager located in the VMM and the TCM password proxy module located in the VM. The TCM and each level of proxy need to generate corresponding The encryption / decryption key and signature key are used for authorization authentication and encryption to protect the key of the lower-level agent.
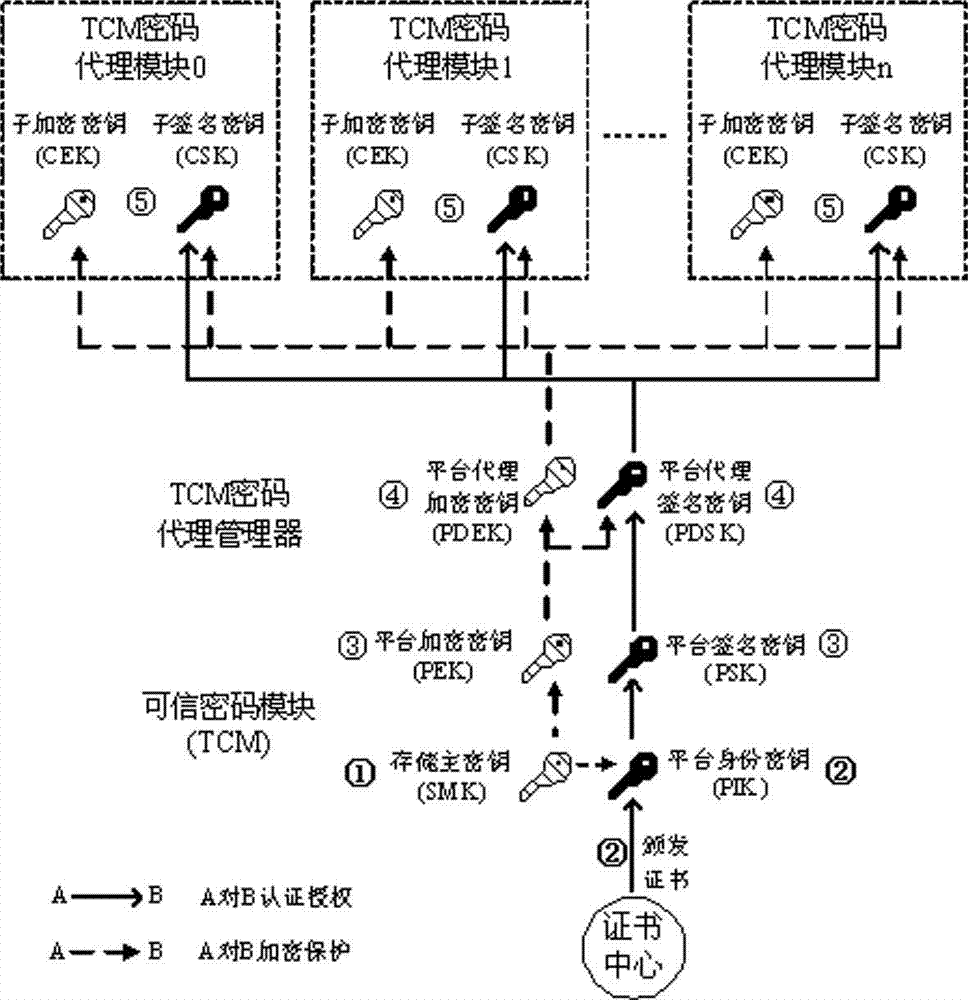
[0015] combine figure 1 with figure 2 , the specific implementation method that the TCM cryptographic function agent system of the present invention sets up is:
[0016] ①. The ownership of hardware TCM is established by VMM and SMK is generated.
[0017] In this step, the specific implementation can be divided into the following details:
[0018] 1. In the process of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com