Secret key storage method and telephone card authentication method of wireless fixed telephone
A key storage and authentication method technology, which is applied in the field of wireless fixed-line key storage method and machine card authentication, can solve the problem of high cost, achieve the effects of ensuring key security, reducing costs, and facilitating the expansion of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The preferred embodiments of the present invention are given below in conjunction with the accompanying drawings to describe the technical solution of the present invention in detail.
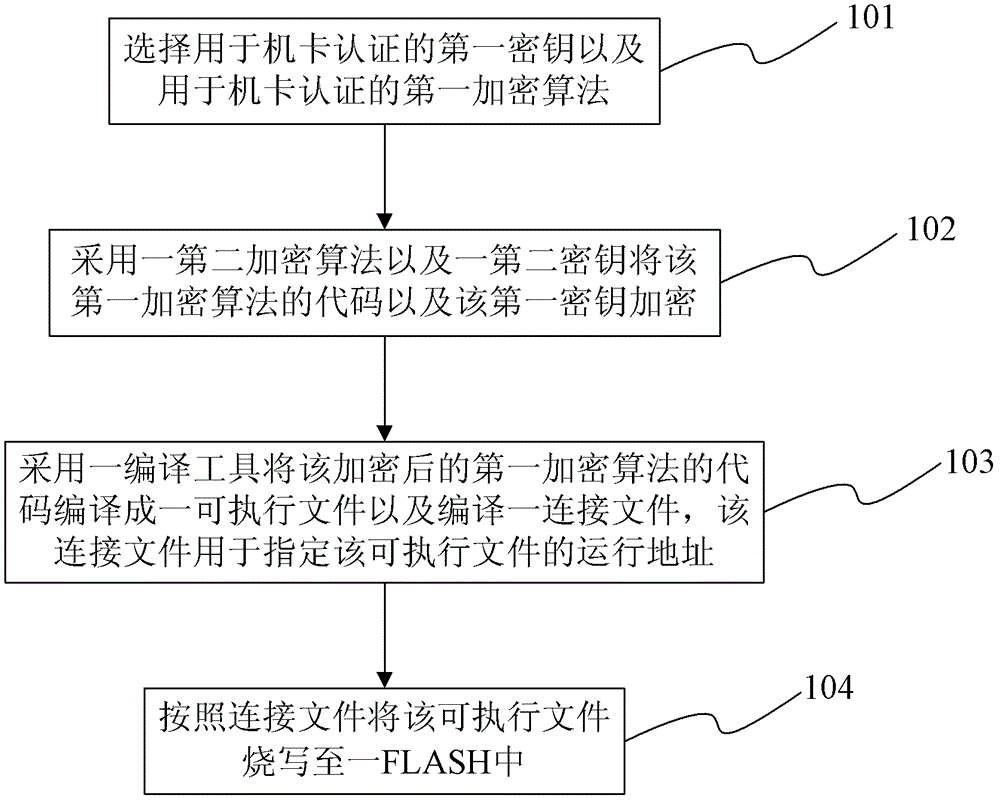
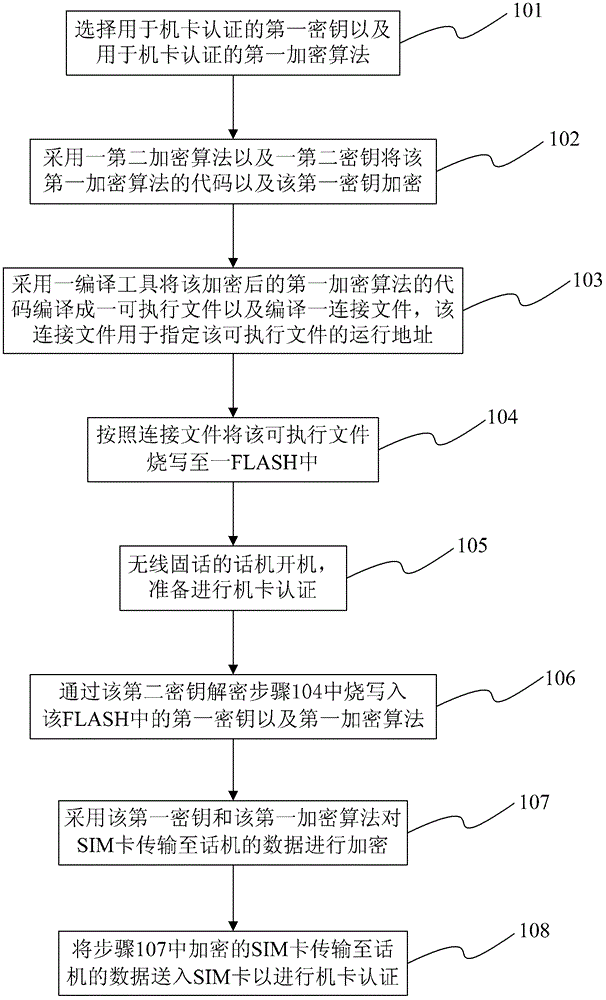
[0026] refer to figure 1 , introduces a key storage method of a wireless fixed phone of the present invention.
[0027] Step 101, selecting a first key for machine-card authentication and a first encryption algorithm for machine-card authentication, wherein the machine-card authentication is authentication between a wireless fixed phone phone and a SIM card. Wherein, the first encryption algorithm is a 3DES algorithm.
[0028] Step 102, encrypt the code of the first encryption algorithm and the first key by using a second encryption algorithm and a second key. Wherein, the second key is selected through the GPIO interface of an application processor of the wireless fixed phone. There are 4 groups of the second key, and the group is selected according to the configuration of the two GPI...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com