Identity authentication and key agreement method suitable for electricity consumption information collection system
A technology of identity authentication and key negotiation, which is applied in the field of information security, can solve problems such as inapplicability, and achieve the effects of enhancing security, preventing illegal monitoring or interception, and strict identity authentication and key negotiation processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be described in further detail below in conjunction with the accompanying drawings.
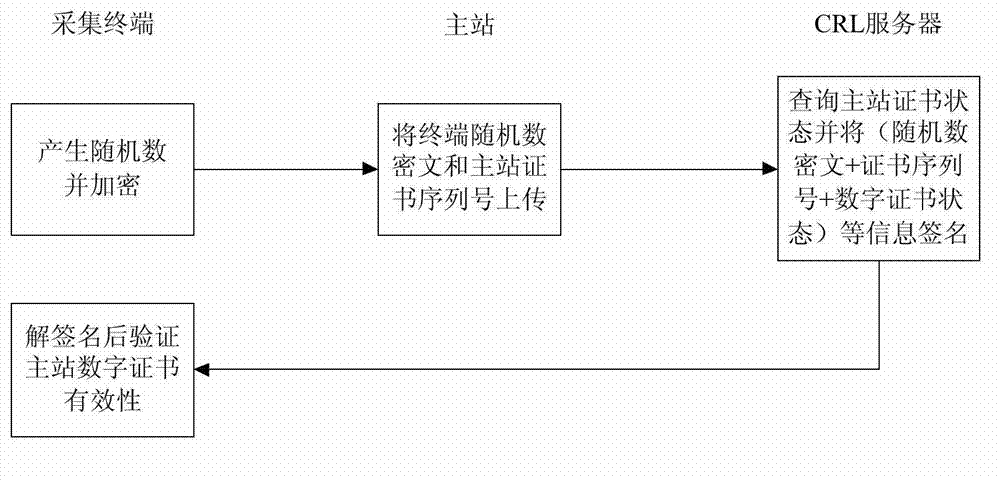
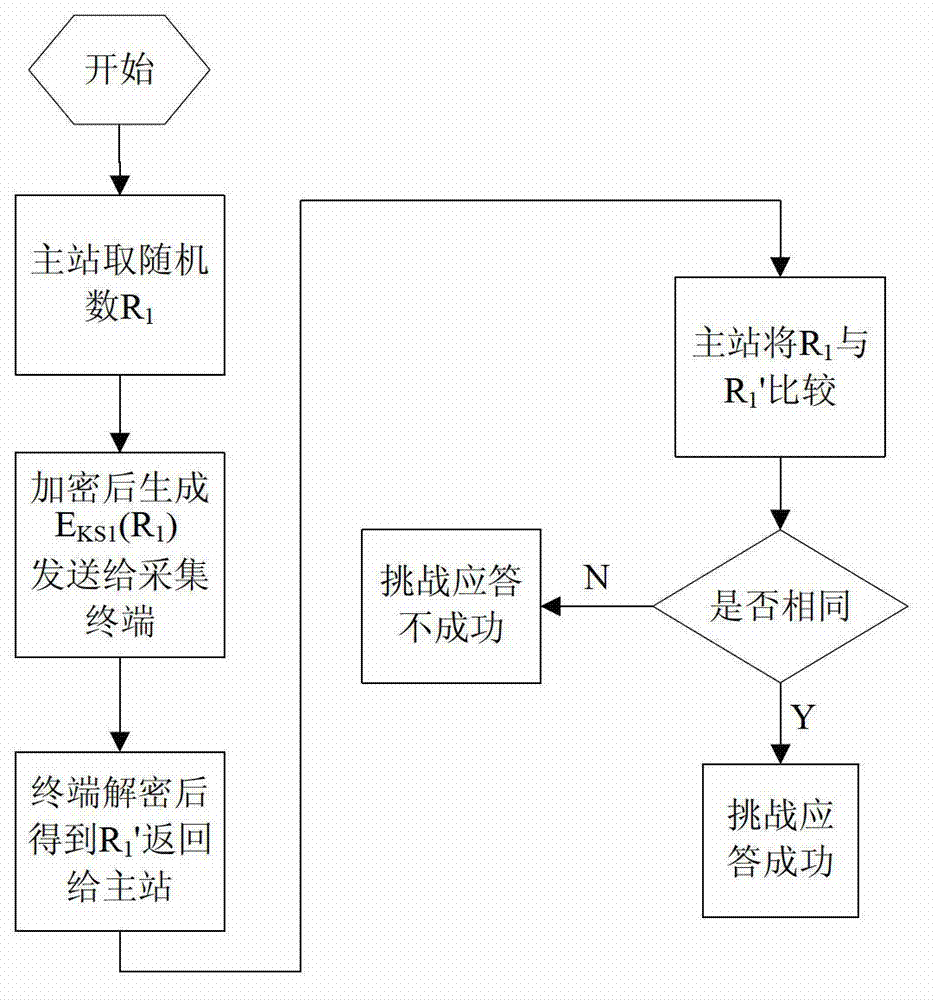
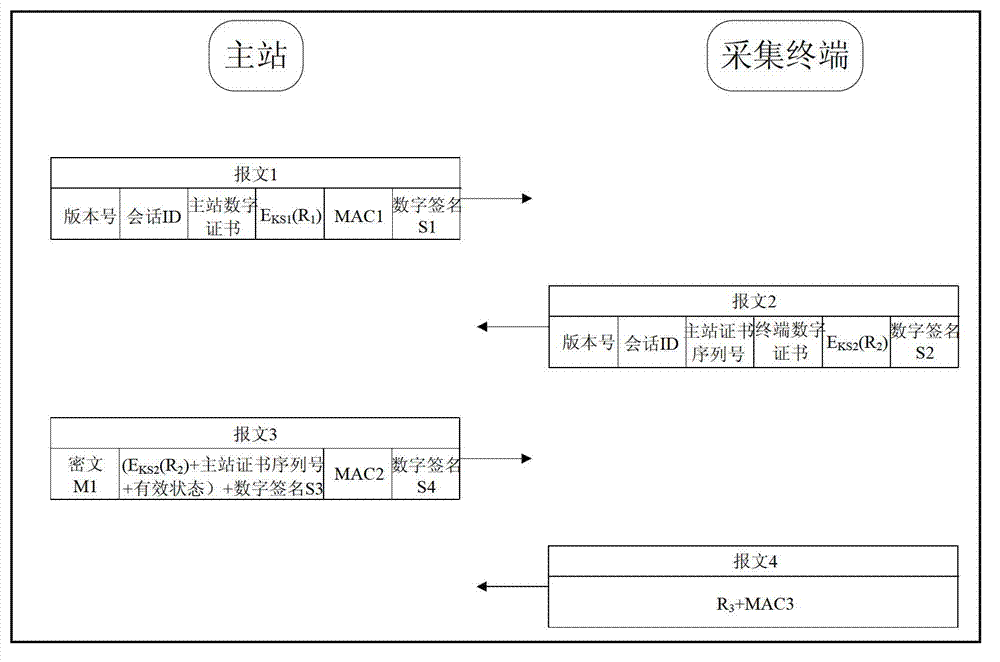
[0057] Such as figure 1 In this embodiment, the signature authentication mechanism for digital certificate validity query by an authority is as follows: a CRL certificate server is configured at the master station, and the CRL certificate server signs the digital certificate information query result of the master station or the collection terminal; the collection terminal Need to verify master digital certificate C M At the same time, a set of random numbers is first generated, encrypted and then sent to the master station. The master station uploads the random number ciphertext generated by the collection terminal and the serial number of the digital certificate of the master station to the CRL certificate server, and the CRL certificate server queries the serial number of the certificate. Corresponding digital certificate status, and sign the random number...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com