Method for multi-way encryption and signing and zero knowledge certification
A zero-knowledge proof and multi-party technology, applied in the field of information security, can solve the problem that the asymmetric encryption system cannot guarantee multi-party encryption concisely
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
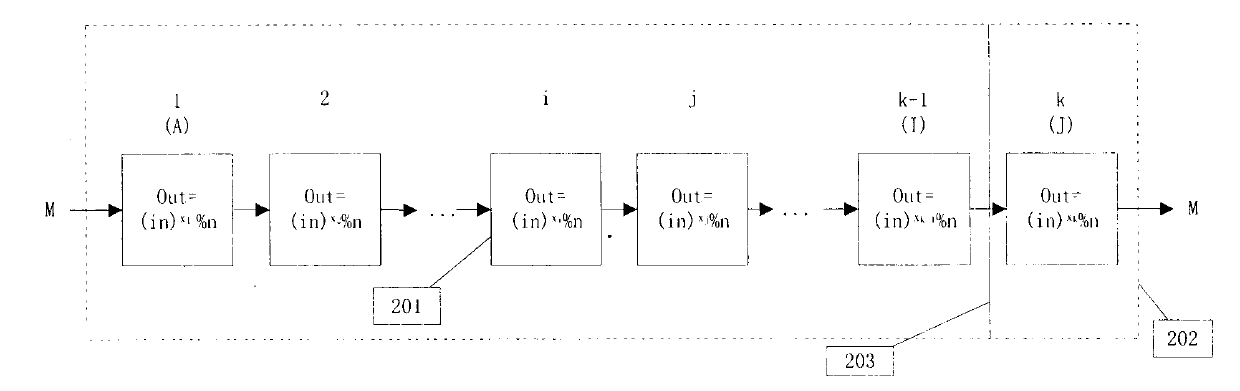
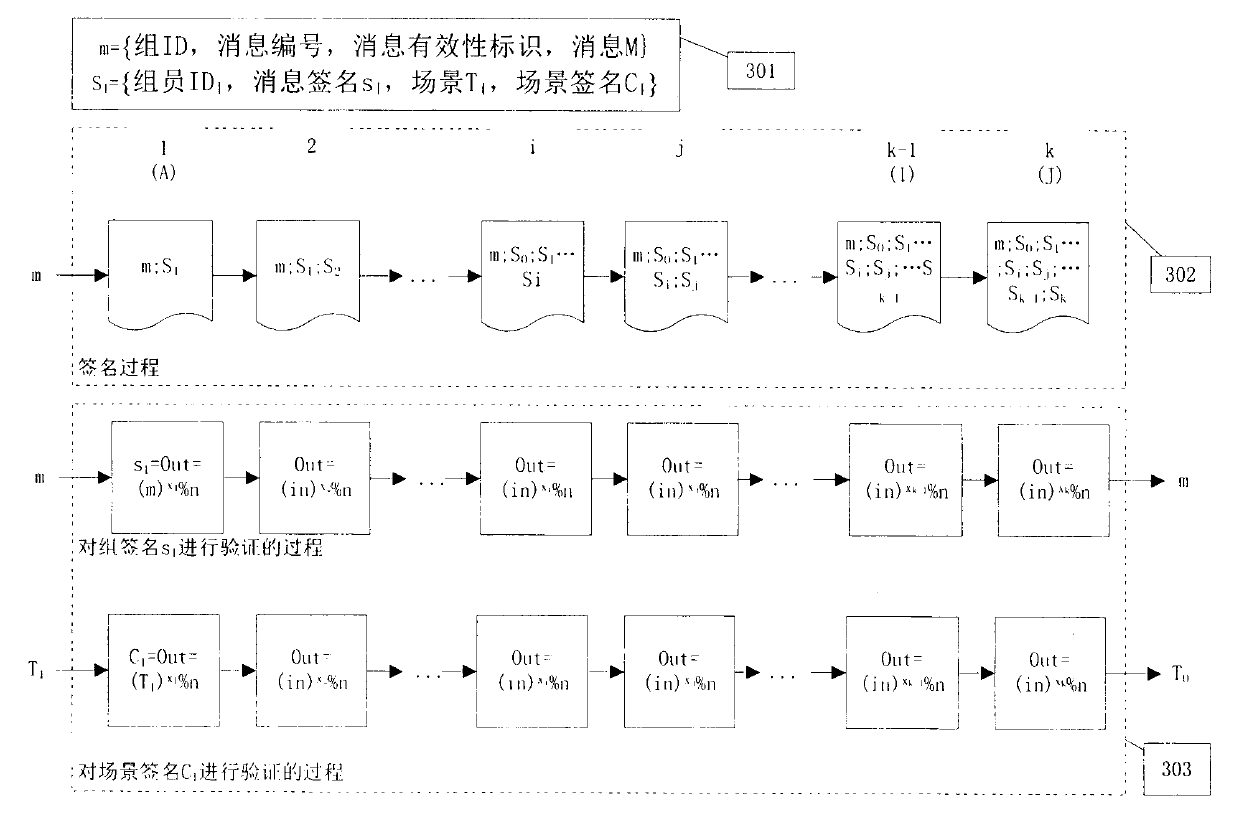
[0044] An implementation process is given here, but it does not mean that the solution of this application can only be implemented in this way. The ".eq." here means equality discrimination. The implementation process is as follows:
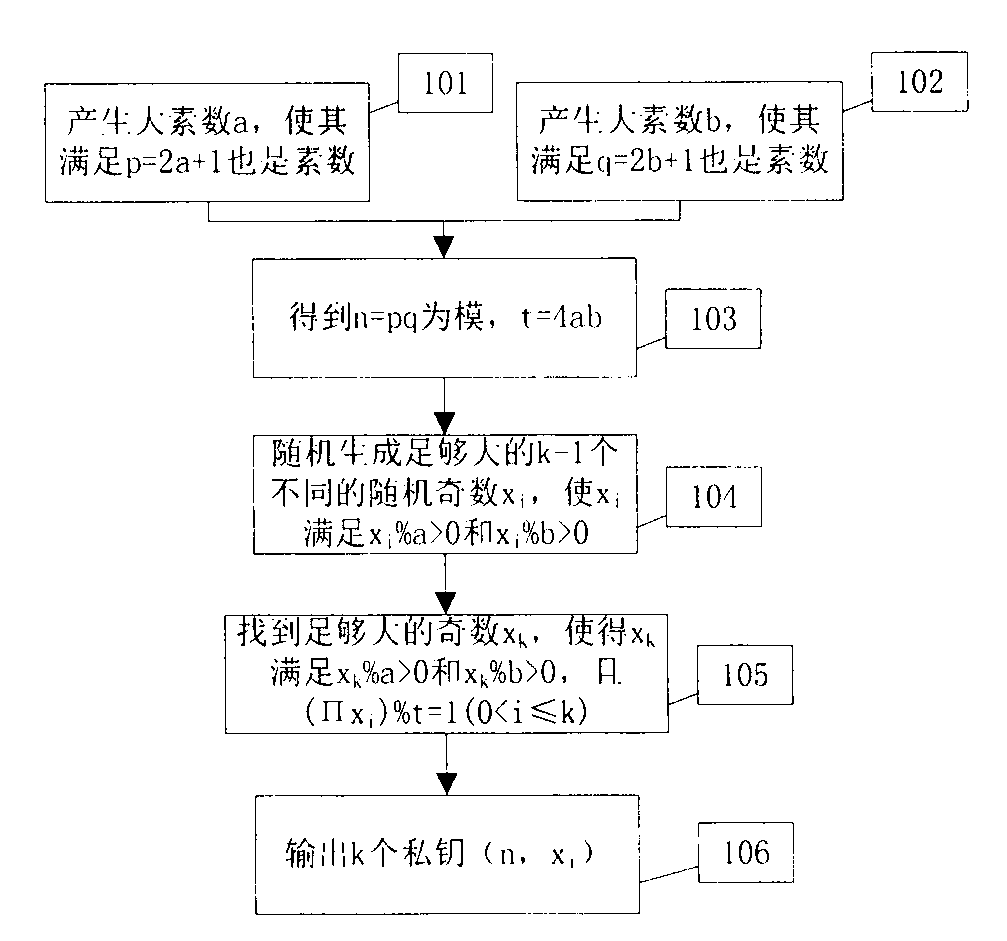
[0045] The process of generating a private key is as follows figure 1 Shown: Step 101, producing a large prime number a so that it satisfies p=2a+1 is also a prime number; Step 102, producing a large prime number b so that it satisfies q=2b+1 is also a prime number; Step 103, calculating n=pq and the Euler function t=4ab; 104 steps, randomly generate k-1 different random odd numbers x large enough i , so that x i meet x i %a > 0 and x i %b > 0; 105 steps, find a sufficiently large odd number x k , such that x k meet x k %a > 0 and x k %b>0 and (∏x i )%t=1(0i )(0
[0046] In the above steps, the three steps 101, 102, and 105 can all adopt the method similar to the RSA system, which will not be repeated here, and other methods can ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com