Method, device and system of verification of safety association between terminal equipment and user card
A technology for terminal equipment and verification terminals, which is applied in security devices, electrical components, wireless communication, etc., and can solve the problems of short PIN code key space, inability to perform user card authentication, and complex user card functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
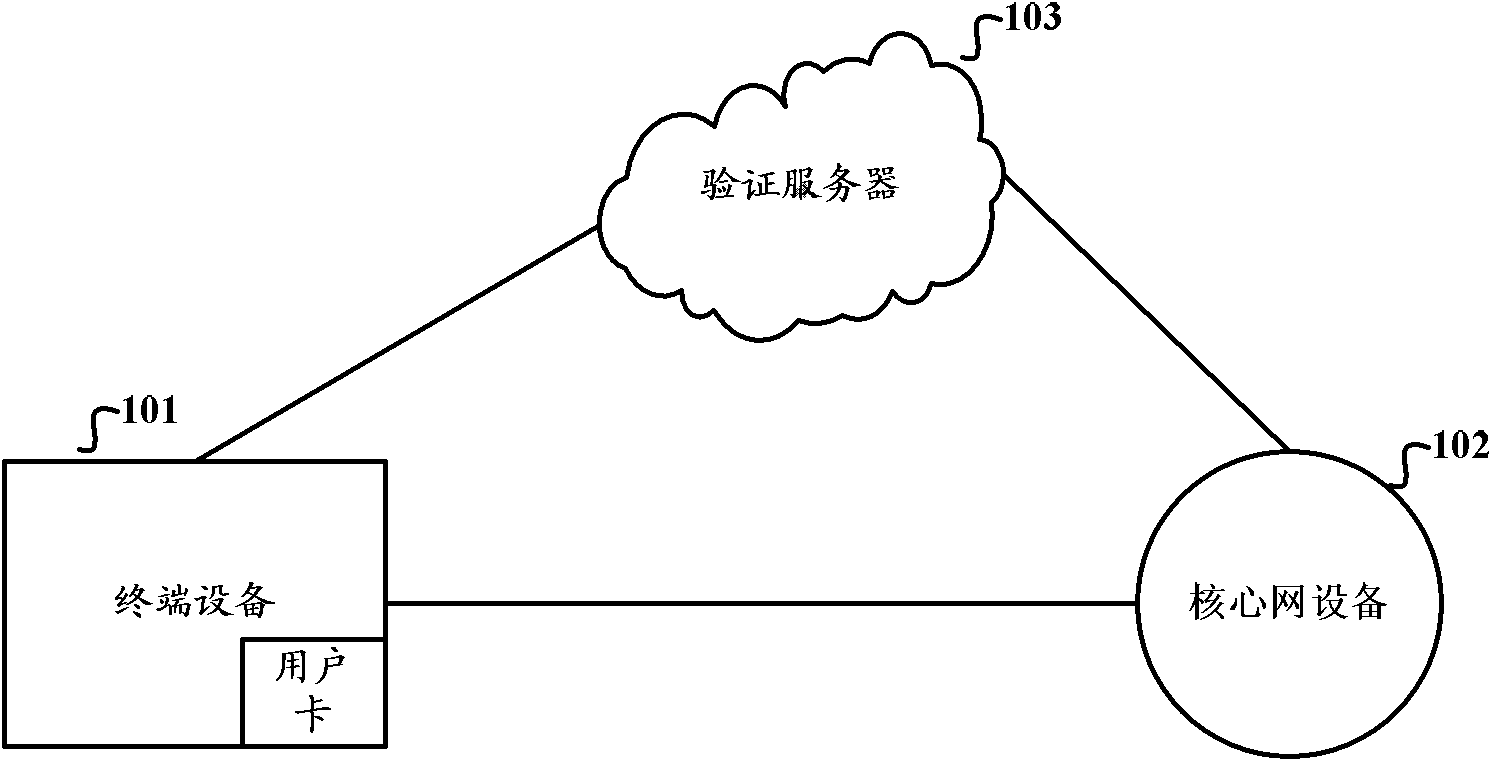
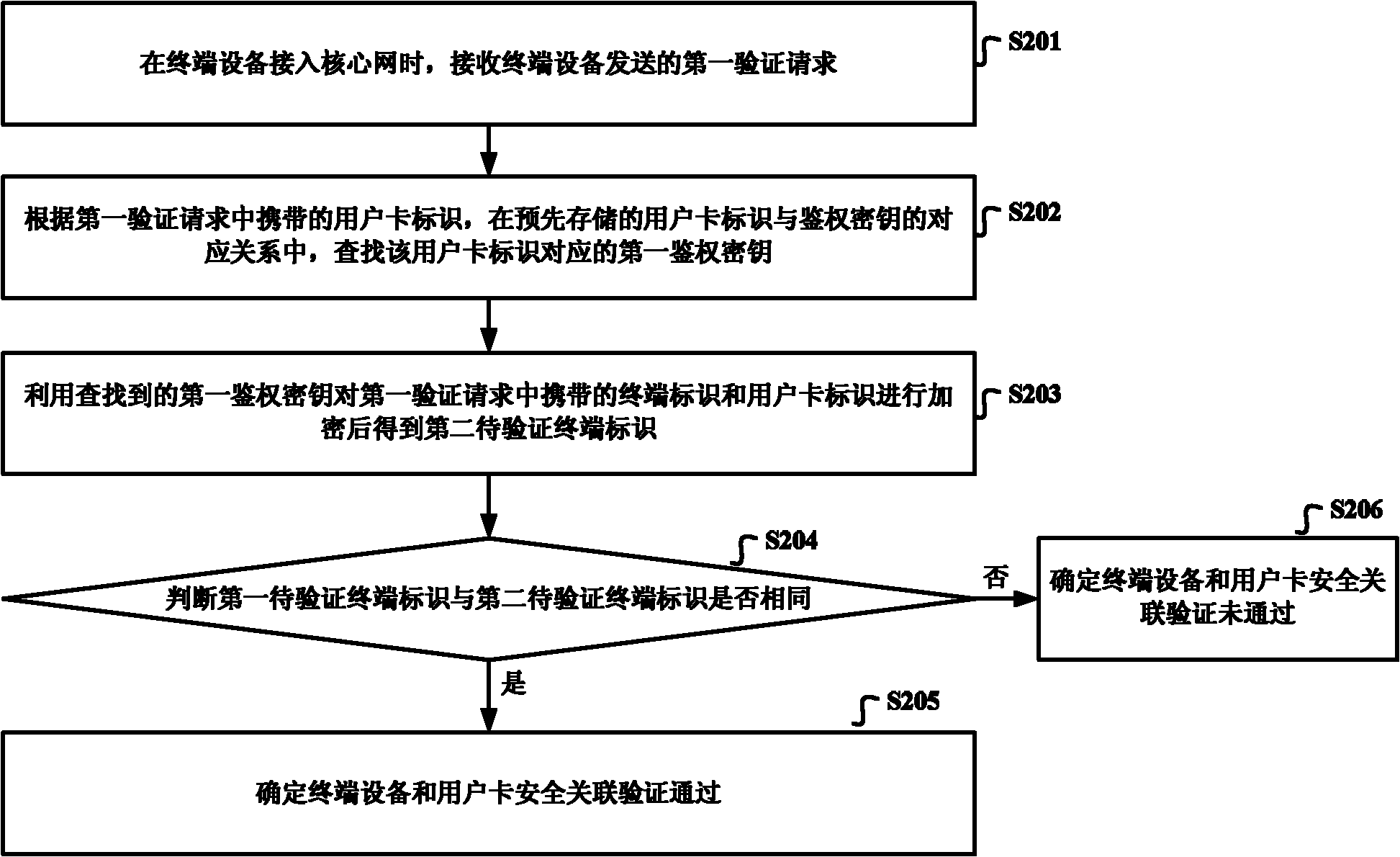
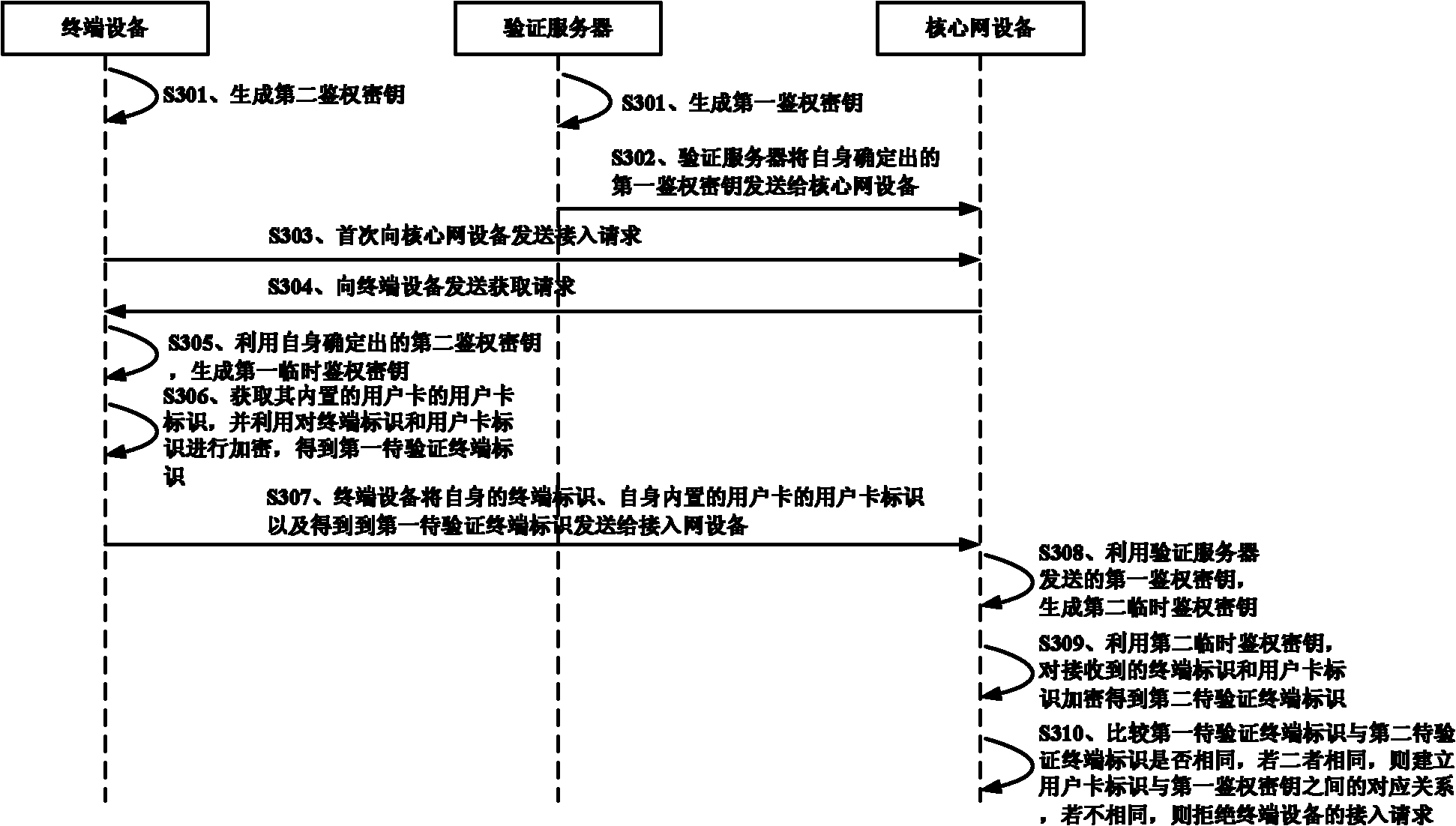
[0012] In the prior art, the method of verifying whether the user card and the terminal device are securely associated either needs to expand the function of the user card, or can only realize the one-way authentication of the user card by the terminal device, and the solutions in the prior art are all on the terminal side These solutions cannot inform the network side of the verification results of user cards and terminal devices. Therefore, they cannot meet the needs of the network side for anomaly detection of terminal devices in application scenarios such as the unattended Internet of Things.
[0013] In view of this, the embodiments of the present invention provide a method, device, and system for verifying the security association between a user card and a terminal device, so that the network side can judge and know the verification result of whether the user card and the terminal device are securely associated, and realize the security association between the user card an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com