Entity impersonation attack penetration testing method aiming at aircraft communication addressing and reporting system (ACARS) data chain
A technology of data link and entity, which is applied in the field of aviation VHF data link security, and can solve problems such as national security impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
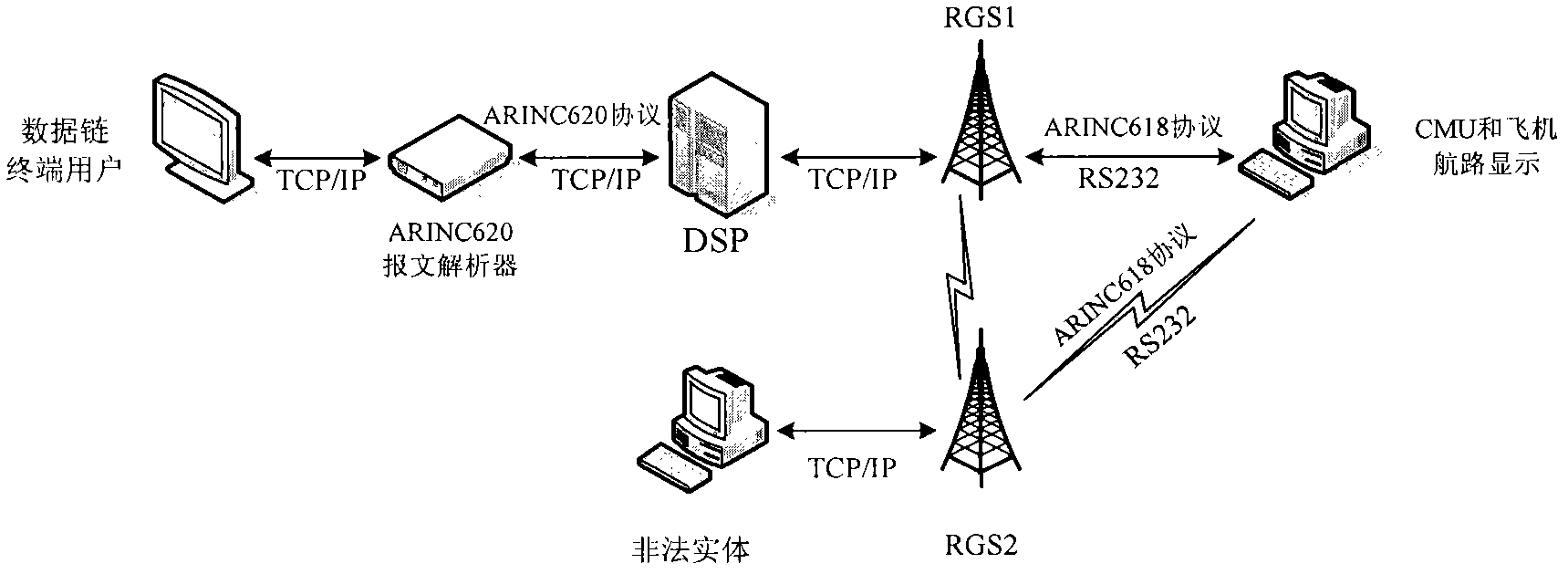
[0021] 1. According to figure 1 In the simulated system architecture, click the route management module on the onboard CMU to start, and the aircraft starts to fly.
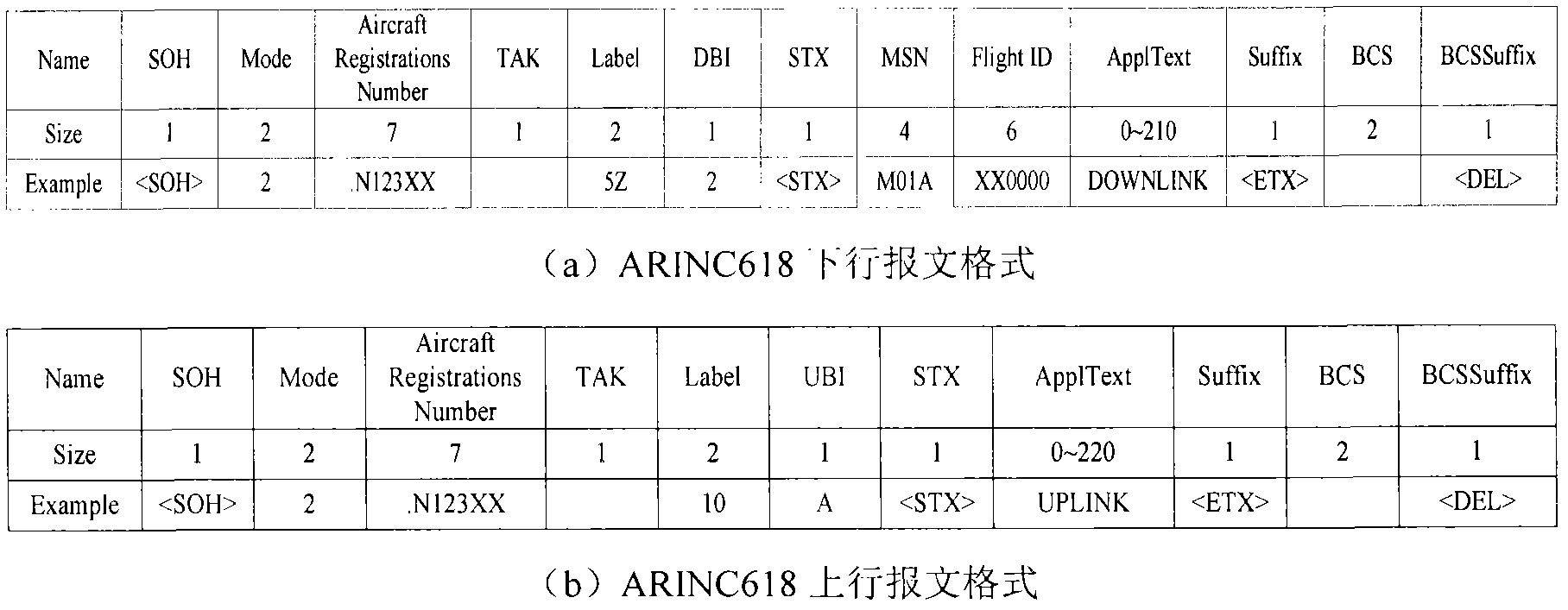
[0022] 2. Pretend to be a legal DSP on the attack end and send a message to the aircraft, click the entity disguise icon on the attack end, enter the content of the message in the pop-up interface, and enter the network statistics report request with the label (Label) S1.
[0023] 3. Click Send to start sending information to the aircraft by pretending to be a ground terminal.
[0024] 4. In the CMU module, it can be seen that the CMU has received the request normally and responded.
[0025] 5. The network statistics report has been intercepted on the attack side.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com