Computer system analysis method and apparatus
A technology for the relationship between computers and objects, applied in the direction of platform integrity maintenance, etc., can solve problems such as slow engine
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
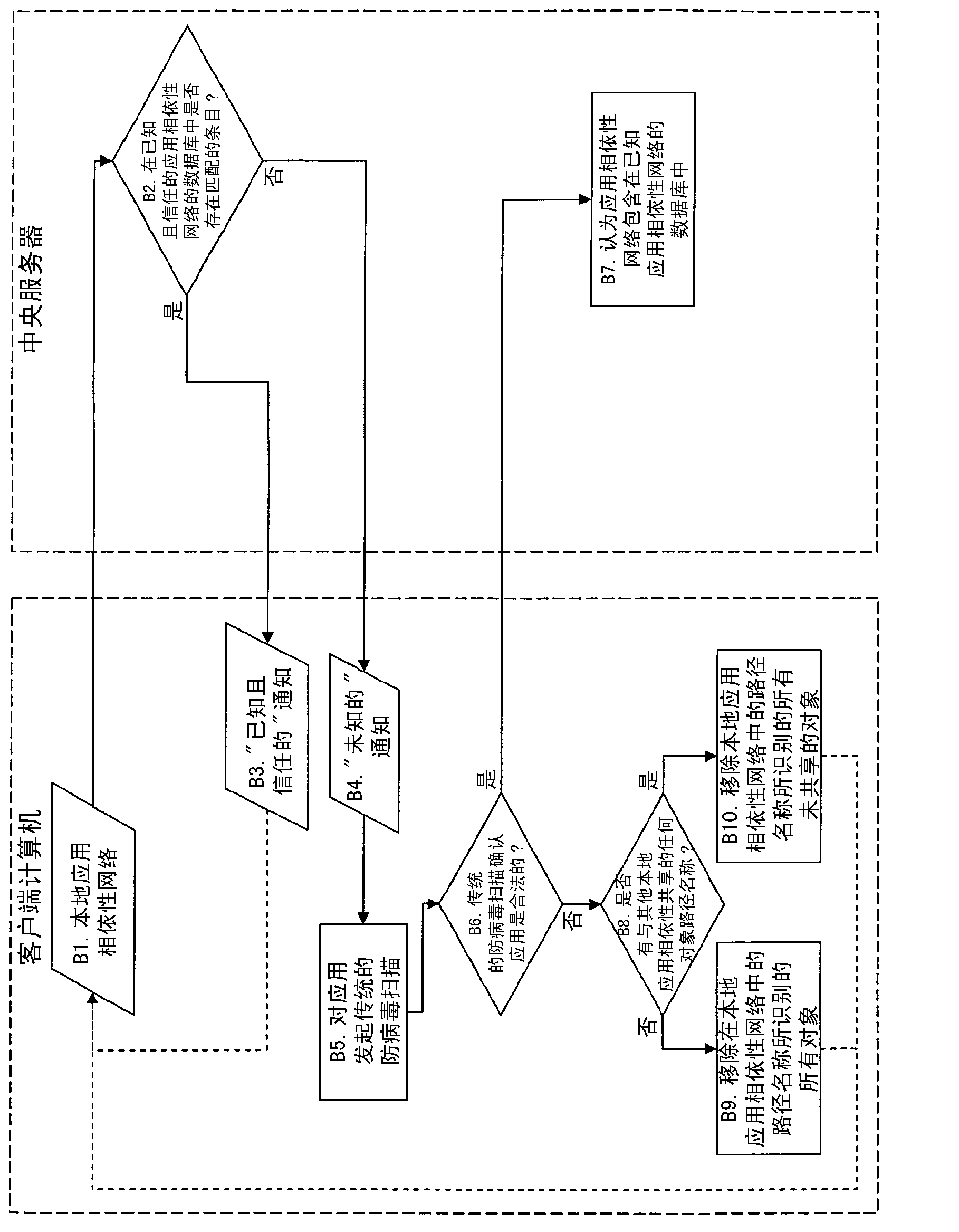
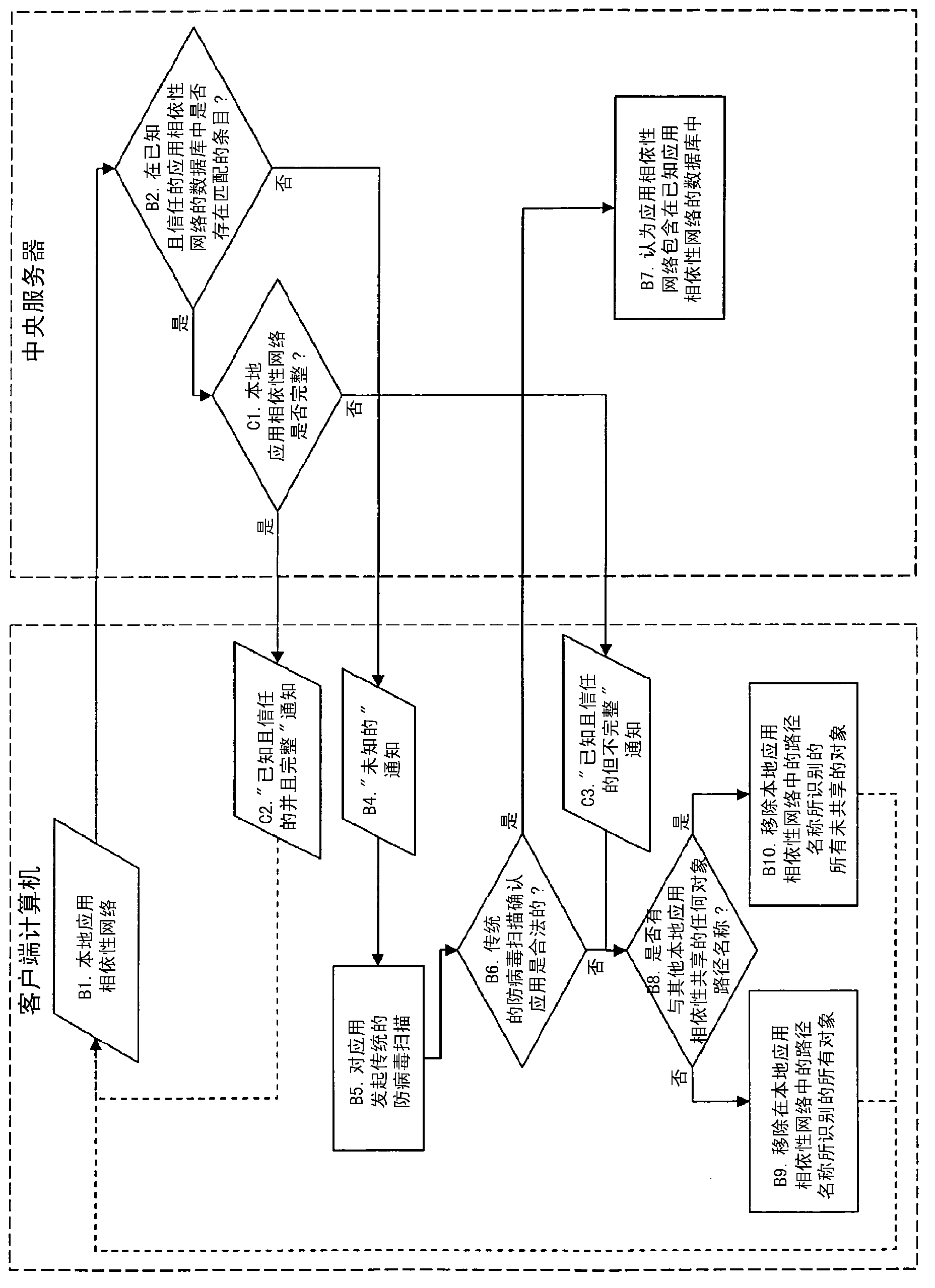
[0026] The malware scanning method described herein is given with respect to a computer system comprising one or more central servers and a plurality of client computers. Client computers communicate with the central server via the Internet. Those skilled in the art will readily recognize other computer system architectures that may employ this method.
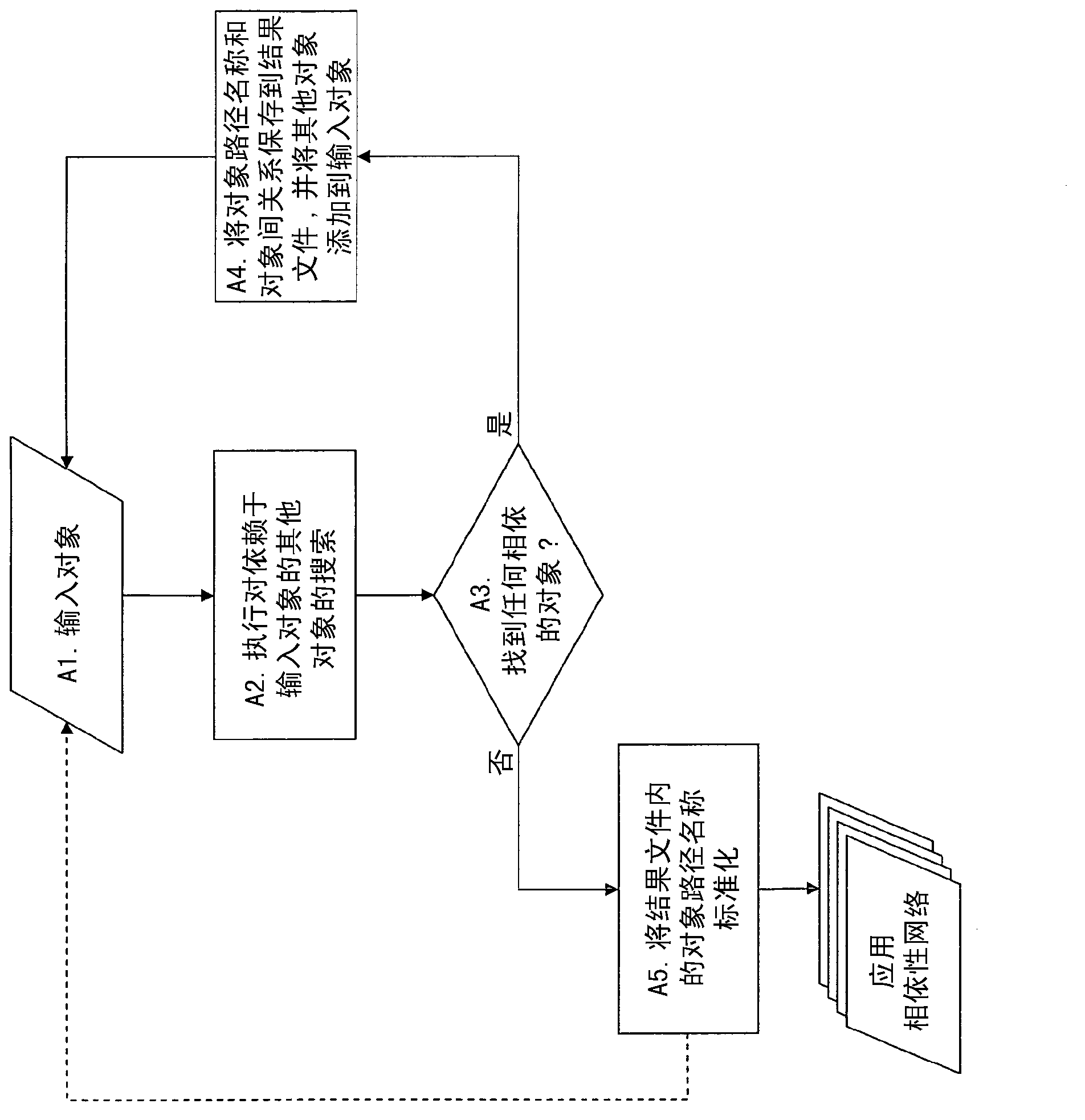
[0027] An application on a client computer typically includes: a set of related objects, including at least data files, directories, and registry information (the latter including the application's configuration and settings) - a desktop shortcut to the application executable; storing the application executable in directory where other apps and libraries live; the app registry points to the location of data files and other executables that the app needs to run. The set of related objects and their relationships can be thought of as the application's "dependency network".
[0028] It should be understood that regardless of ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com