Method and device for processing file based on cloud security
A file processing and security technology, applied in the field of information security, can solve problems such as the inability to detect and kill malicious programs, and the widespread spread of malicious programs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
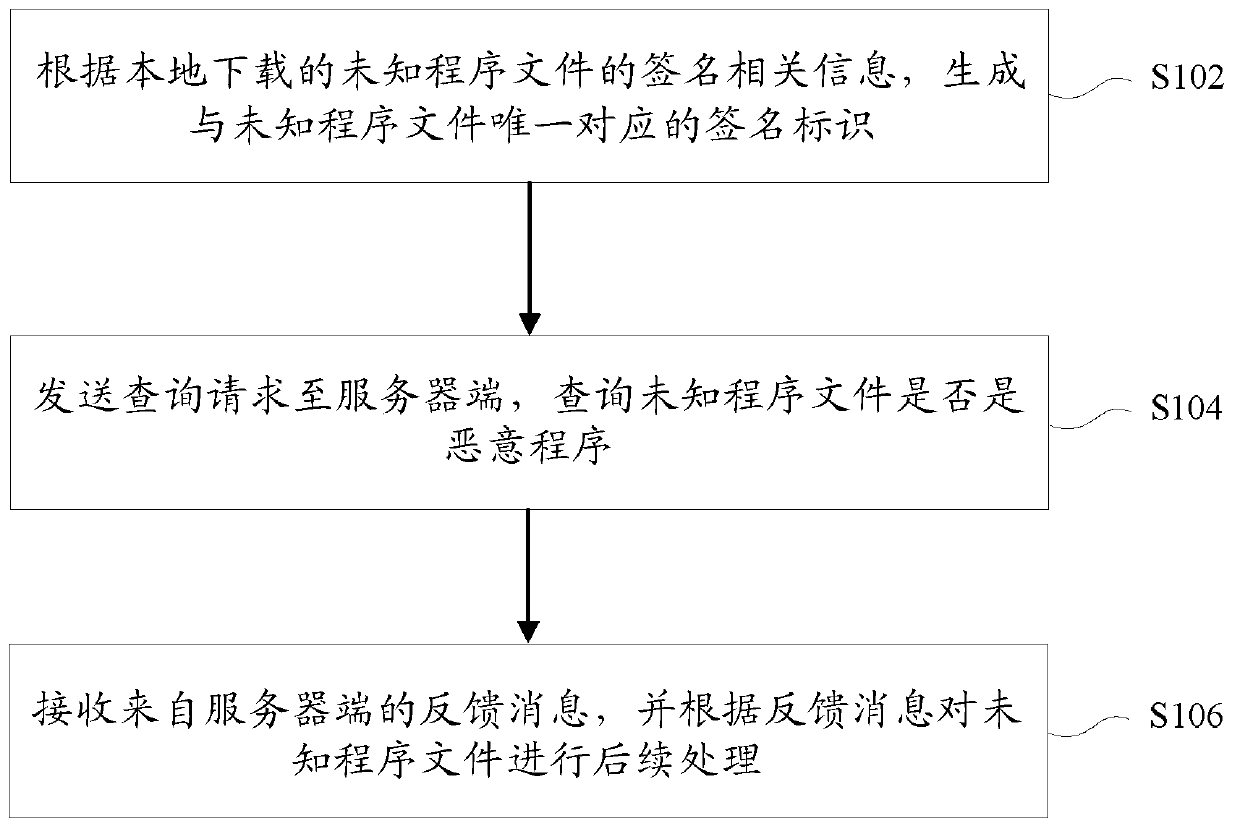
[0100] figure 1 Shows a flow chart of a file processing method based on cloud security according to an embodiment of the present invention. In this method, the client for processing local programs is improved, and the method specifically includes steps S102 to S106.
[0101] S102: Generate a signature identifier uniquely corresponding to the unknown program file according to the signature related information of the unknown program file downloaded locally.
[0102] S104: Send a query request to the server to query whether the unknown program file is a malicious program. Wherein, the query request carries the signature identifier of the unknown program file and some or all of the file characteristics of the unknown program file.
[0103] Among them, the file feature in this embodiment may include the MD5 value and SHA1 value of the file, or a feature value calculated by extracting part of the content from the file. It can also include the DLL (Dynamic Link Library) information that t...
Embodiment 2
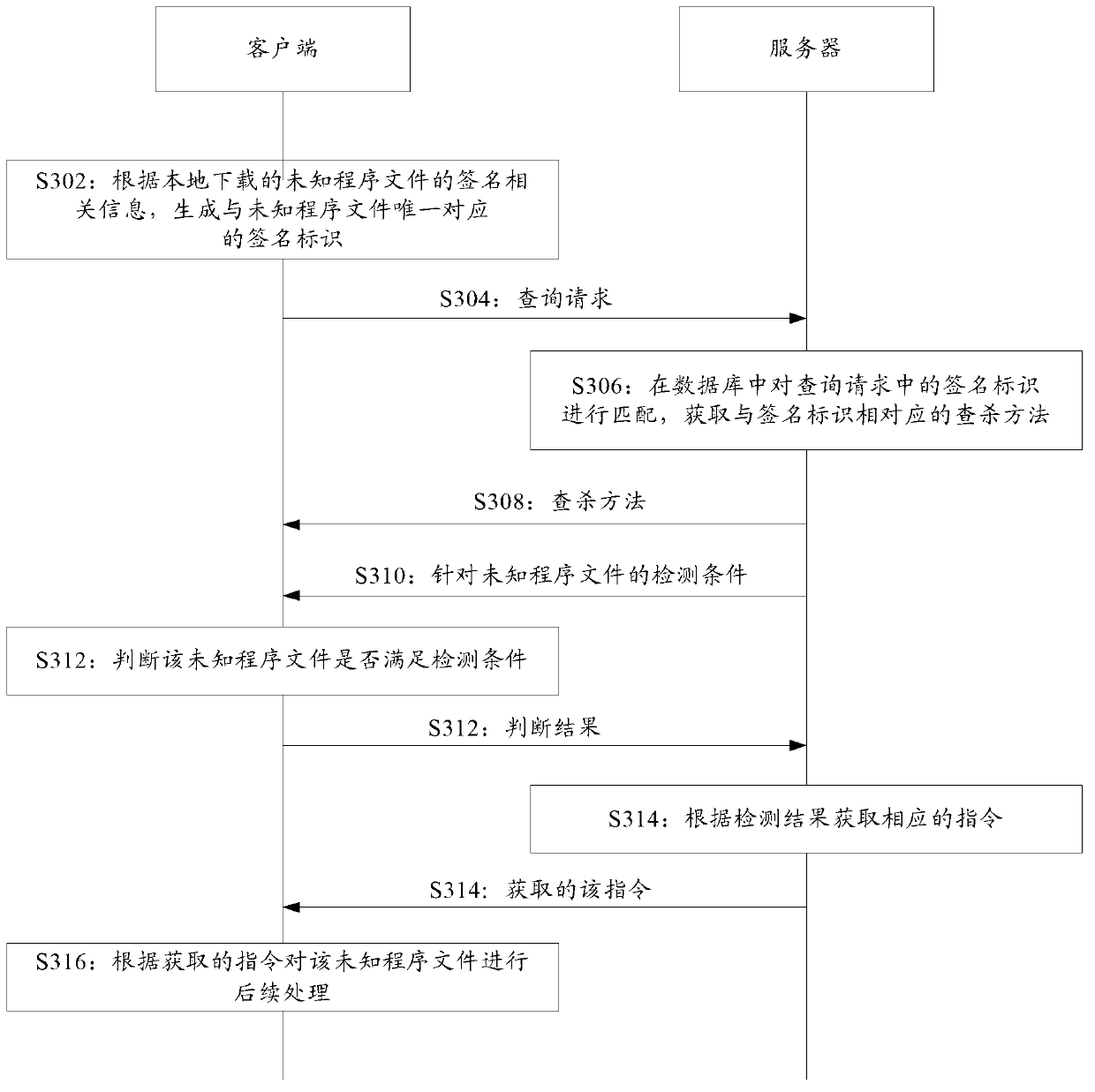
[0117] This embodiment is a specific application scenario of the first embodiment above. Through this embodiment, the method provided by the present invention can be explained more clearly and specifically.
[0118] image 3 Shows a flowchart of a file processing method based on cloud security according to an embodiment of the present invention. The method specifically includes steps S302 to S316.
[0119] S302: The client terminal generates a signature identifier uniquely corresponding to the unknown program file according to the signature related information of the unknown program file downloaded locally.
[0120] It should be noted that, in this embodiment, when the client executes the local program file, it will determine whether each program file is a locally known program file, so as to ensure the client's knowledge of the local program and also ensure the local program's safety. Among them, a program file list is stored in the client, and when the scanned program file is not...
Embodiment 3
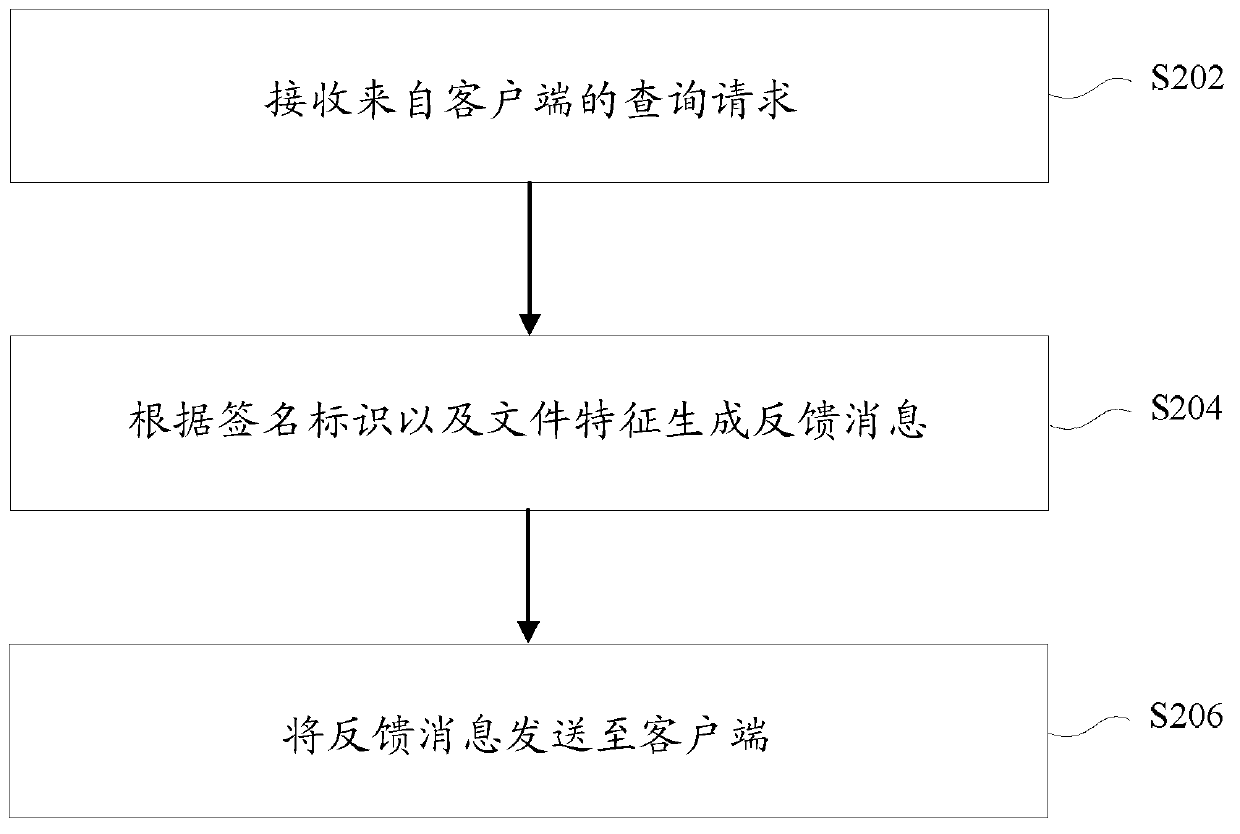
[0152] Figure 4 Shows a structural block diagram of a cloud security-based file processing device according to an embodiment of the present invention. The device is executed in the client's engine. The unknown 0 of the device’s safety includes:
[0153] The generating module 410 is configured to generate a signature identifier uniquely corresponding to the unknown program file according to the signature related information of the unknown program file downloaded locally;
[0154] The query module 420, coupled with the above-mentioned generating module 410, is configured to send a query request to the server to query whether the unknown program file is a malicious program, wherein the query request carries the signature of the unknown program file and part or all of the unknown program file Document characteristics;
[0155] The processing module 430 is coupled with the above-mentioned generating module 420 and is configured to receive feedback messages from the server, and perform ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com